In the past few weeks, the internet has been abuzz with nightmarish horror stories of Comcast's questionable decision-making and downright terrible customer service. The central theme of many of these disputes with the nation's largest cable provider is that without evidence, the conglomerate will refuse to acknowledge its mistake and place the burden of proof on the customer.
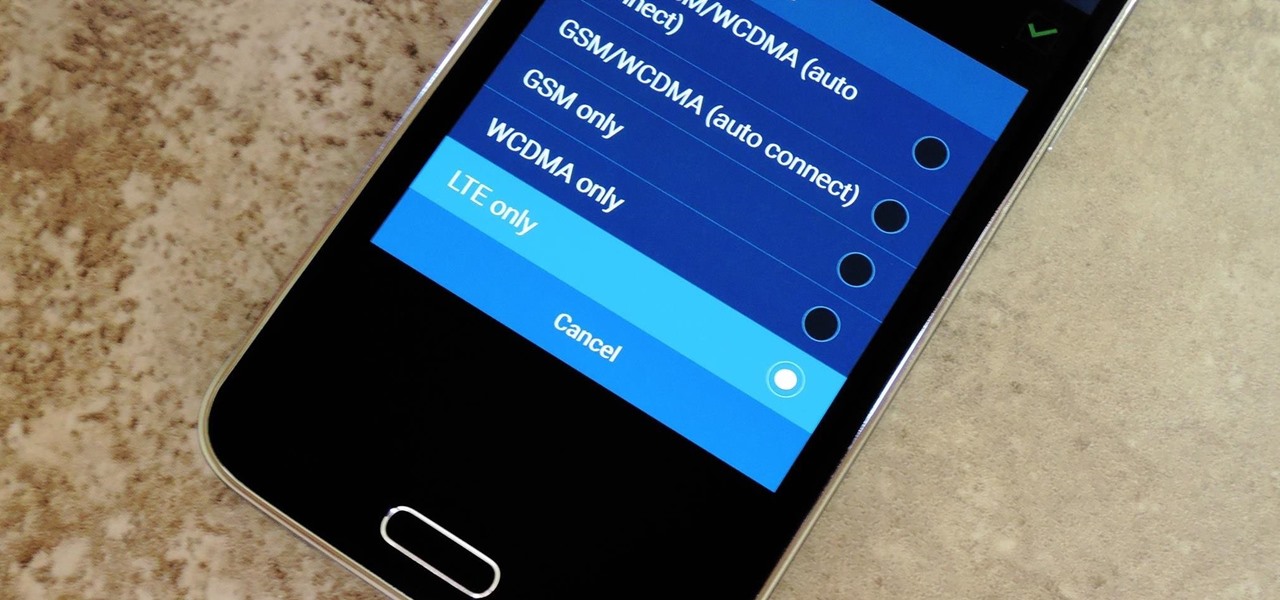
Even with the highest-tiered data plan available, there are times that your phone or your carrier might downgrade your connection to 3G or even lower. This usually occurs when you've made a phone call, or you've switched cell towers while traveling.

Apps that save your passwords have been around for quite a long while. But apps that complete the entire login process automatically? Now that's a different story.

Developing an imperceptible lie is difficult, especially when you're lying right to someone's face. Thanks to smartphones, getting people to trust you is now easier than ever. You can craft a lie in seconds and hit send, all without ever seeing their untrusting faces.

Stock Android has come with lock screen widget support for a couple of years now, ever since the days of the first Ice Cream Sandwich build. But for some reason, Samsung decided to remove this feature in the Galaxy S5.

Want to learn how to make Peppa Pig with Play-Doh? Here is our attempt on showcasing a tutorial on how to make Peppa Pig with Play-Doh.

A friend of mine has a crazy amount of Reddit karma and gold, and yesterday he let me in on his secret. This person, who will remain unnamed for obvious reasons, created a Python script called Reddit Karma Crawler that finds rising posts before they get too popular.

The new iOS 8 was just unveiled, and it looks pretty awesome. Apple showed off some of the enhancements and new features we can expect to receive in the fall at WWDC, and while not the huge facelift we saw with iOS 7, it does showcase what Apple does best—refinement. Continuity

Welcome back, my aspiring hackers! In previous tutorials, I have shown you how to scan the globe for vulnerable servers and write simple scripts in BASH and Perl to perform other reconnaissance tasks. In a very recent guide, I taught how to scan vulnerable servers for Heartbleed.

Whether it's bad timing, or some trying-to-be-funny photobomber, it sucks having a photo ruined by someone or something getting in the way. While you can always retake the photo, it's simply impossible to capture the moment you intended, no matter how much restaging you do. But with an HTC One, there's no need to retake anything, as we have access to built-in features that will remove those photo intruders.

Transparent status bars and new lock screens weren't the only new additions that came with the Galaxy S3 KitKat update. Along with better battery life and a smoother user experience, we got a new toggles design and recent apps menu. Of course, Samsung's infinite wisdom left these two aesthetic features hidden away. Luckily, with root, you can easily enable them with just a few quick edits.

Let's say you're watching a video and everything's going great, but you feel the need to raise the volume a tiny bit. You hit the volume button on your Nexus 5, and all of a sudden, a giant volume slider appears that obscures half of your video for 3 seconds.

Figuring out someone's password, pattern, or PIN isn't very difficult—simply watching over their shoulder or following the oil marks left across their screen is enough to figure them out and bypass whatever lock screen security they have.

If you lend someone your phone, even if it's just for a second, there's a chance they can enter an app and see something you'd rather they didn't. Whether it's a personal email or a private photo, there are plenty of reasons why you'd want to keep snoops out of certain apps.

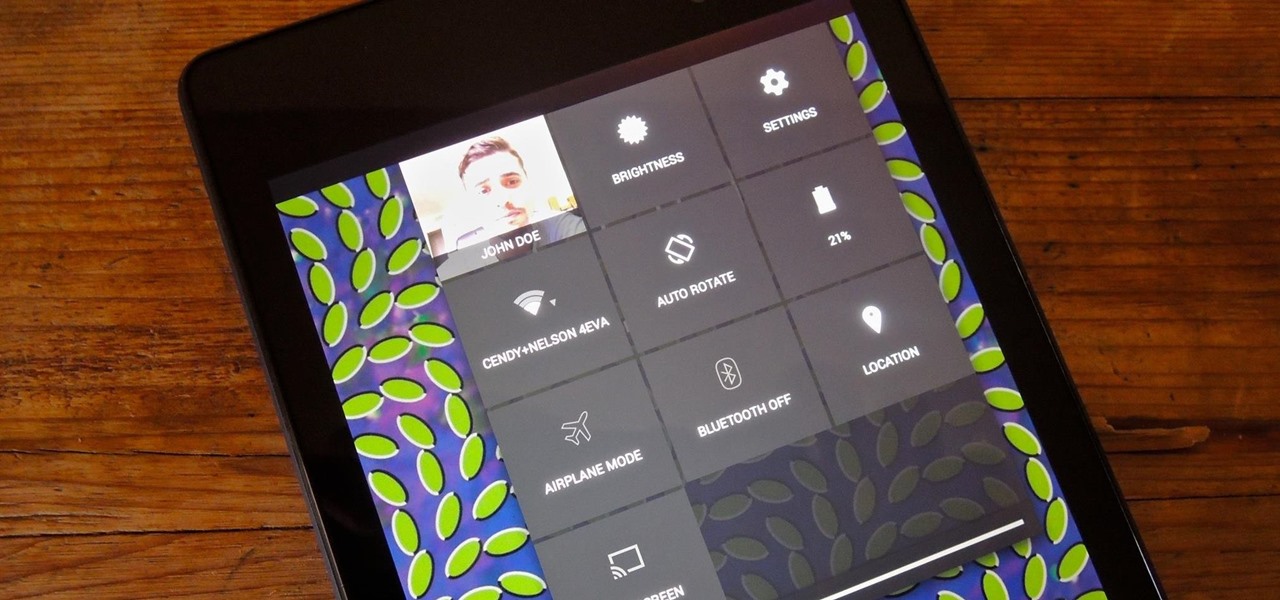
Accessing notifications and quick settings from the lock screen just makes things move quicker and more efficiently, unless of course we're using a secure lock screen. It makes sense that if we have face, pattern, or pin security enabled, we may not want notifications accessible, but really, that should be something we decide for ourselves—and now we can.

Notifications, while certainly helpful, can at times be overbearing. There are banners plastered every which way on your smartphone for almost every application. While many of the notifications can simply be swept away or turned off, the same can't be said of persistent notifications.

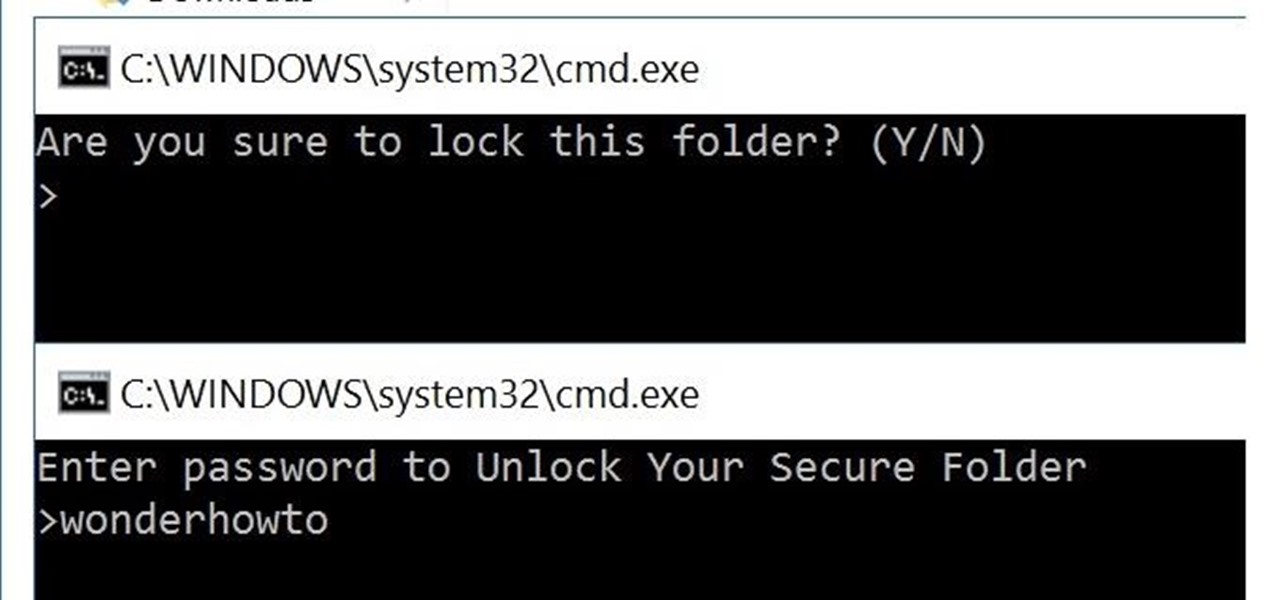
You can easily lock any folder on your Windows computer with a simple Notepad hack. By creating a batch file, you can hide a folder and require a password be entered before it becomes visible and accessible. This is a great tool for locking sensitive information, like pictures, financial statements, and a lot more.

A great aspect of using Android is having the ability to change and tweak aspects of the user experience to your liking. You can easily change things like home screens, widgets, and icons on your Nexus 7 tablet, but also core system settings if you want, like volume settings. Most stock systems come standard with a "15 step" volume control. That means simply that you have 15 levels from mute to the loudest volume settings. Whether your an audiophile or just someone who wants a little more con...

Welcome back, my hacker apprentices! Although there is a multitude of different hacker types, the one target they all share is the database. I often refer to the database as the hacker's Holy Grail, or the ultimate prize for an effective hack.

One of the best features on the new Moto X is Touchless Control, which lets you verbally ask the device questions or perform tasks without ever touching or turning on the display, a feature that would do quite nicely on the Nexus 7, if it could handle it.

What is your Samsung Galaxy Note 2 running? More than likely, you're still rocking Jelly Bean 4.1.2, which is already pretty outdated. My grandma uses 4.1.2.

Welcome back, my tenderfoot hackers! This is the third installment of my series on basic Linux skills that every hacker should know. Although some hacking tools are available for Windows and Mac, every real hacker uses Linux—for good reason.

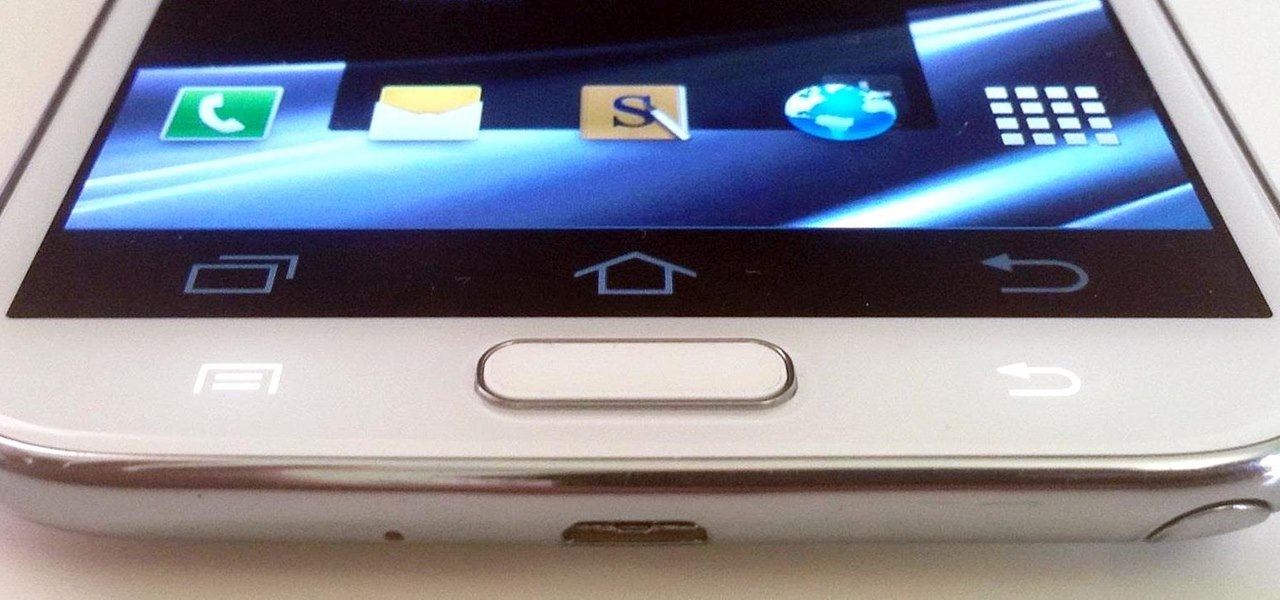
There may only be a few hardware buttons on your Samsung Galaxy Note 2, but when they're not working, your phone might as well be a doorstop. A few years back, I was texting while walking to class and a student on a bicycle crashed into me. My phone was flung thirty feet—straight into a puddle. I picked it up and checked for damage, but everything seemed okay. The biker apologized profusely, but nothing was wrong, so I told him not to worry about it and proceeded to class.

Welcome back, my newbie hackers! We've already saved the world from nuclear annihilation and covered our tracks afterwards, but the world is still threatened by a malicious, megalomaniacal dictator with missiles and nuclear weapons.

You know that moment when you finally figure out something, but you figured it out years after you really needed it? Don't you freaking hate that?!

These days, we increasingly have more and more devices in our everyday possession. While a notebook computer, a tablet, and a smartphone may seem like overkill, they do work to make our lives easier and even help reduce clutter in certain ways.

We've all had to write an essay or research paper at some point, and undoubtedly the hardest part about it is always the citation, right? If you ask me, it's a huge pain in the arse. Even more so if you're gathering your facts from a huge variety of sources.

Whether you're at work or in class, there are times when using your phone is unacceptable, regardless of that subtle yet sudden twitch in your arm that arises every time you hear the vibration of a text message.

Welcome back, my tenderfoot hackers! So many of you responded positively to my post about using the keylogger, as well as my post regarding turning on the webcam, that I decided that you might enjoy another similar hack. In this article, we will enable the audio recording capability on the remote system of your roommate.

Being politically correct on social media sites is super boring. I've had my fair share of rage tweets and angry Facebook posts with some colorful wording, but sometimes using and F-bomb just gets the point across better. Now that Facebook is pushing out their new Graph Search, it might be time to clean up your profile. FaceWash is a web app that searches your Facebook profile for common bad words. You will need to give the app permission to access all of your wall posts (or course). Once acc...

At first glance, the iOS home screen looks nearly identical to the original release back in 2007. Though those experienced with the evolving iterations of iOS will tell you that the features have changed. Furthermore, with the App Store continuing to explode with (lets face it) better options than the stock software, these included applications are only causing clutter across the springboard.

With presidential voting going down on Tuesday, November 6th, voters are beginning to anchor down on their choice for president. But with the way the media works, this may be difficult for some people because the news sites they listen to give conflicting and sporadic information on the candidates.

Did you buy your new iPhone 5 without a contract? We'll, if you bought it from Apple, AT&T or Verizon, you can have it unlocked pretty easily. Why Have It Unlocked?

Taking screen captures is a standard feature on iPhones and newer Android smartphones, but for some reason it's not very intuitive. Screenshots allow you to share your phone's screen with your friends, document technical problems for customer support, and even make how-to guides easier to follow. So, it's definitely worth remembering. Here's how you do it.

At the recent DefCon conference in Las Vegas, researchers opened many of the top commercially available gun safes with simple tools like a straw or a paper clip, and in one case, just by shaking it a bit. The investigation began after the researchers, Toby Bluzmanis, Marc Tobias and Matt Fiddler, learned that certain Stack-On safes, issued to some law enforcement officials to secure their firearms at home, could be opened simply by jiggling the doorknob.

Hello! My latest interest is screenwriting. I would like to share a few hints I find quite useful. I am a newbie, so the following post will not be taken from the treasury of many years of experience. Just plain facts,.. Thanks for reading! Step 1: In the Beginning

Control is important. Mankind inherently wants to control its environment, which is why we have things like indoor plumbing, electric lights, air conditioning, and more. Likewise, Minecraft has redstone, which is a way for users to control their environment and manipulate it to suit their needs.

Camping is wonderful isn't it? You get to go out into the wild, build a fire, pitch a tent, and tell ghost stories. My favorite part about camping isn't any of those things, though. No, the best part about camping in my opinion is the food. Whether it be planking freshly caught fish, roasting hot dogs, melting s'mores, or cooking hobo dinners, the food is always the most memorable part of camping to me because you get to eat stuff outside of the norm.

A preposition links together nouns, pronouns and phrases to other words in a sentence. This language tutorial, you will learn how to use prepositions in biblical Greek (Koine). This is a perfect lesson for the scholar looking to study the ancient language of Greece. Watch this how to video and you will be speaking the biblical Greek language in no time.

In this language tutorial, you will learn to use the present passive indicative in biblical Greek (Koine). This is a perfect lesson for those who wish to study this ancient language. Listen and repeat the words in this language tutorial and you will be speaking biblical Greek in no time.