Today, we are going to combine what we learned from the Introduction to Cryptography article with our Java programming skills. If you are new to Java, check out Matthew's Learn Java: Part One for a quick beginner's lesson, or check out some of the Java tutorials directly on Oracle.

Today's digital cameras record not only the images themselves, but also the metadata behind the scenes, like camera settings, location, date, time, etc. But there's a lot more to say about a photograph. What's the subject? Is it night or day? Outside or inside? Person, place or thing?

Oh Data, You so Awesome! We are going to use Node.JS to gather us some data. Given nodes plethora of well abstracted network abilities and it's deep evened nature, it will make quick work of plugging into various data sources and gathering / making good use of said data.

Earlier in the week, Obama’s attorney general stated something that is quite alarming. “In this hour of danger, we simply cannot afford to wait until deadly plans are carried out, and we will not,” Eric Holder said during a speech at Northwestern University’s law school in Chicago. It's a very ambiguous statement. Why do people talk like this? Why can't they just talk straight to the point? Well, most of the time it's to hide something. Take a look at this video: What do you think of that! Th...

Ever wondered how other players can get so much awesome enchanted gear in such little time? Struggling to gain experience orbs and need an efficient way to do so with very few casualties? In this tutorial, we will be going over how to build a quick XP farm with a zombie spawner (though any spawner will do). Setup

As many of you Null Byters may know, I was planning on writing this article a week or two ago. Better late than never! So, let's get right to it then—choosing the right Linux distro for your needs.

I'm sure most everyone has some kind of fluorescent light source in their home; those long white tubes that emit a bright white light when turned on, or maybe a few of the CFL power-saver bulbs. These bulbs actually require very little "power" (i.e. a high voltage:almost no current ratio) to emit light. In fact, static electricity is enough to make them flicker. Inside these tubes is a gas, and when electricity flows through that gas, it gets "excited" and produces light.

Taking good care of our colon should be one of our capital concerns. Do you know that like the air we breathe, the colon additionally becomes polluted with toxins? Toxin accretion will appear for as continued as you continuously eat. These toxins become the account of a abatement in activity and added problems like constipation, gas, bloating, etc. So now, imagine how acceptable activity could be after these toxins!

In this article, I'll be showing you how to make a simple yet effective static electricity generator. Basically, this device allows you to carry a constant static charge on your body and discharge it on anything grounded or of opposite polarity. The electricity generated is around 8-10 kV, at a very low current. The shock is enough to startle your friends, just like a static shock from a trampoline or carpeted room. You'll need a little experience in soldering and circuit design to build the ...

Let's face it, the world we live in is far from the fairy-tale land we want it to be, where violence doesn't exist and weapons are not needed. Our foremost goal in life out there in the scary world is simply to survive. And if we need a few tools to accomplish this, we should use them, right?

Sometimes, paying for the whole Xbox LIVE service might seem like a waste of money. You're constantly experiencing lag, you've got people modding and cheating, kids are being loud and obnoxious over the mic, and your kill-to-death ratio is getting dumped on. Basically, the whole multiplayer experience just isn't cutting it anymore—you want to go back to the classic world of single player. Well, there's always downloadable content—simply known as DLC.

Welcome to Minecraft World! Check out our tutorials, post to the community corkboard, and come play on our free server!

Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server. Does your structure sometimes lack that "pizzazz" you seek? Well, this week's Saturday workshop is going to give you a few tips on how to upgrade your builds! This workshop will be centered around adding some extra aesthetics to your castle walls, towers, buildings and more.

If you saw my last tutorial on retiring early and wealthy, you now know how anyone can invest a small amount of money over the course of their life, and by exploiting compound interest, achieve an extremely comfortable and easy going retirement. In Part 2, we are going to dive into something a little more risky: Tax liens.

TCP/IP Client / Server Application Hello! Today's blog post will be about coding a very rudimentary Client and Server application duo, which will communicate by using TCP Sockets.

Scrabble Bingo of the Day: CABRESTA [n/pl.] A cabresta (also cabestro or cabresto) is simply a lasso, a rope formed with a running noose that's used on ranches and Western plains for catching horse and cattle. Cabresta comes from the Spanish word halter, which refers to the headgear used for leading or tying up livestock and other animals. But halter also used to mean to hang someone by roped noose, which could be how it became popular as a term for a noosed lasso.

Piezoelectric Energy In this article, I'll show you how to make a small, wallet-sized device that generates electricity from kinetic energy. The concept is simple: Piezoelectricity is the charge that is produced when certain solid materials (commonly ceramic and crystal) in response to mechanical stress. Piezoelectrics have many applications; in speakers, actuators, sensors, even fuses. For more information, click here.

Keyloggers are a must-have tool in your arsenal. Hardware keyloggers have the advantage of being undetectable through anti-virus or other protection programs. They also capture keystrokes before the OS even boots up, so they are pretty handy tools.

Another great Community Byte in the bag! This week was really cool, especially with programming going on twice a week. We transitioned to the new times very smoothly with no one left behind, from what I can tell.

Cheers to another completed Community Byte project! Things went well regarding timeliness and being friendly to the other coders and students. If you've got ideas for our next mission, or an idea for a tutorial, submit them to me. Friday, our mission was to take out HackThisSite, basic mission 5. This mission focused on JavaScript, again. This time there is a little bit more security in place.
Stan Parker StanDP~"Avid PC Enthusiast Since 1982..."

File recovery on Linux is a bit different than Windows. It requires different software than the Windows counterparts because every OS has their own file system. Windows uses NTFS, or FAT file systems, while on the other hand, Linux uses ext-based file systems. I personally use ext4 file system because it's the latest and greatest ext-journaling system and supports a large level of directory recursion and file sizes, but most installations still use ext2 or ext3. When files are deleted from a ...

BANSHIE n pl. -S banshee 62 points (12 points without the bingo)

Giveaway Tuesdays has officially ended! But don't sweat it, WonderHowTo has another World that's taken its place. Every Tuesday, Phone Snap! invites you to show off your cell phone photography skills.

CUCURBIT n pl. -S a gourd 64 points (14 points without the bingo)

UTILIDOR n pl. -S an insulated system of pipes for use in arctic regions 59 points (9 points without the bingo)

MIMESIS n pl. -MESISES or -MESES mimicry MIMETIC adj 61 points (11 points without the bingo)

PLASTRUM n pl. -S plastron 62 points (12 points without the bingo)

HEXEREI n pl. -S witchcraft 67 points (17 points without the bingo)

FOVEOLET n pl. -S a foveola 64 points (14 points without the bingo)

REAPHOOK n pl. -S an implement used in reaping 67 points (17 points without the bingo)

VERONICA n pl. -S a handkerchief bearing the image of Christ's face 63 points (13 points without the bingo)

Often times when staying at a hotel or anywhere for that matter, you'll whip out your laptop and check the local area for Wi-Fi. I know you've all been in my shoes when you find an unsecured network that appears to be public Wi-Fi belonging to the hotel or airport, and you connect to it. You connect fast and perfectly, only to find that when you open your browser, it says you don't have an account, and are filtered from accessing the web. This is because the owners of the network want to keep...

YANQUIS 68 points (18 points without the bingo) Definition: United States citizens [n/pl.]

FEAZING 70 points (20 points without the bingo) Definition: fazing; disturbing the composure of [present participle of feaze]

Giveaway Tuesdays has officially ended! But don't sweat it, WonderHowTo has another World that's taken its place. Every Tuesday, Phone Snap! invites you to show off your cell phone photography skills.

Like the recent XSS 0day exploit found in the Mac and Windows versions of Skype, a similar one has been found in the Skype app for iPhone. The vulnerability allows an attacker to send a message that contains malicious JavaScript code in the "Name" parameter. This code can steal your phonebook, crash the app, and potentially do a lot worse. The URI scheme is improperly identified for the web-kit browser. Instead of going to a blank browser page, it defaults to "file://". The code could steal a...

MACHZOR 73 points (23 points without the bingo) Definition: mahzor; a Jewish prayer book [n]

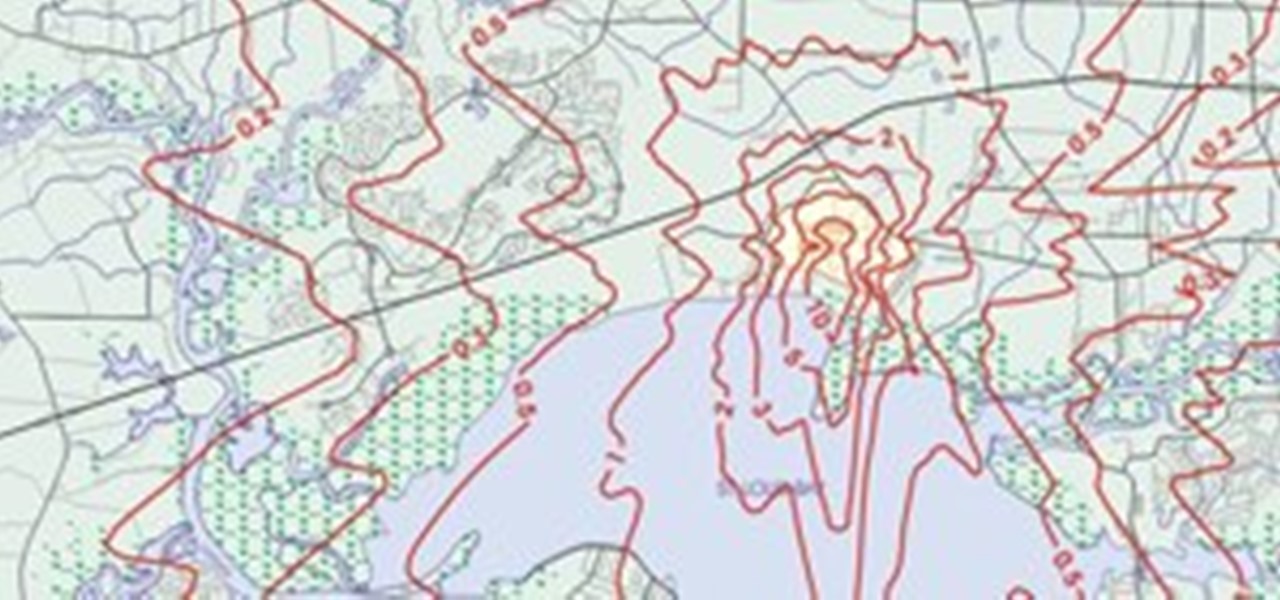
ISOPLETH 63 points (13 points without the bingo) Definition: a type of isogram [n]