The road can sometimes resemble a battle field. Tailgaters, horn-honkers, and jerks who cut you off are enough to drive any driver batty. Here's how to keep your cool behind the wheel and stay calm during moments in which you'd like to explode.

These hearty bugs are here simply to elicit screams and revulsion – or so it seems. Apparently they can survive nuclear waste, but that doesn't mean they impossible to get rid of. Deal with them pronto with this video on how to get rid of those pesky bugs.

Who said the eighties were dead? Well, they might be, but that doesn't mean you can't still rock the hairstyles. Take your hair to new heights by ratting it, which is simply another way of saying backcombing.

CC, which stands for "carbon copy", is a familiar phrase in email, but can also be used in business letters and legal documents. This can be especially useful for letters you want to spend up a company or organizational chain, letting each recipient know exactly who else received the same document.

The Google Chrome OS has been making a lot of waves for its convenience. In this video, the convenience is further highlighted, as we are shown how to install the Google Chrome OS on a Flash drive. Now you can take the entire OS with you wherever you'd like to go.

Thanks to Apple's awesome user interface, it is extraordinarily easy to set your default printer. Instead of guessing which printer your document printed to, be certain of where it is every time.

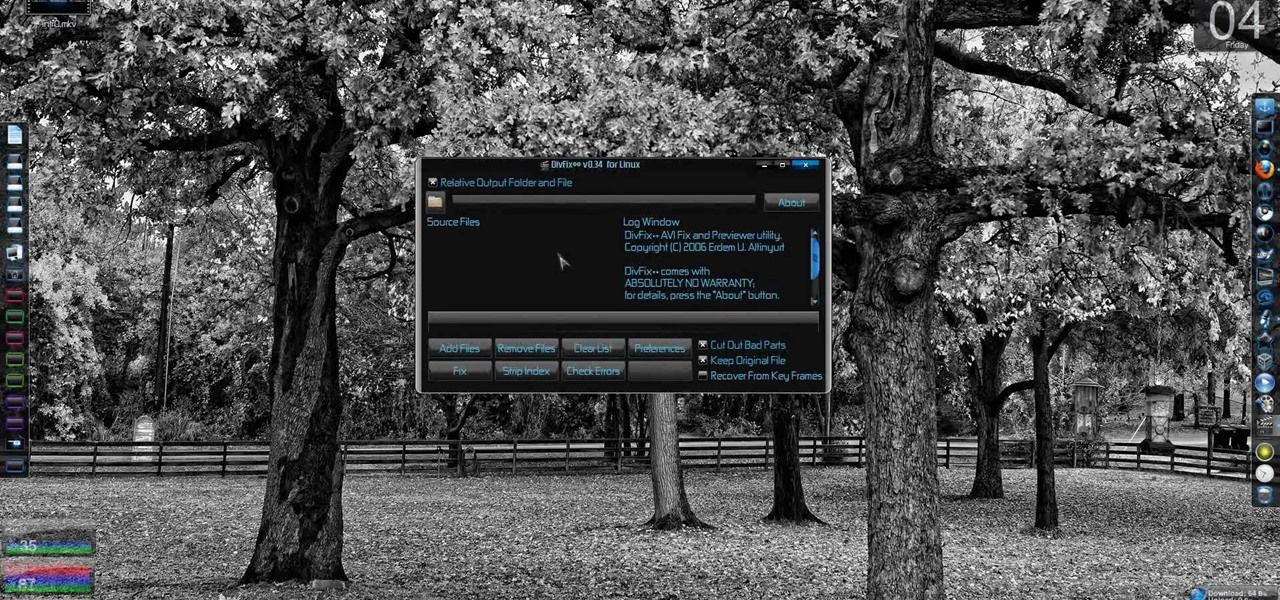
Broken AVI video files are your worst nightmare. Nobody wants to watch a video and find out it's corrupted and not working anymore. But there could be a solution on Linux. This computer operating system could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to fix broken AVI files with DivFix++ on Ubuntu Linux.

While drywall is an inexpensive building material, it's not the sturdiest. Luckily, repairing the inevitable holes is a quick and easy process.

Whether you work at a clothing store or simply want to get your mom off your back, fold those tees in a flash.

Whether you're on a job interview or a first date, follow these simple steps to give the impression that you're quite intelligent – even if you're quite average.

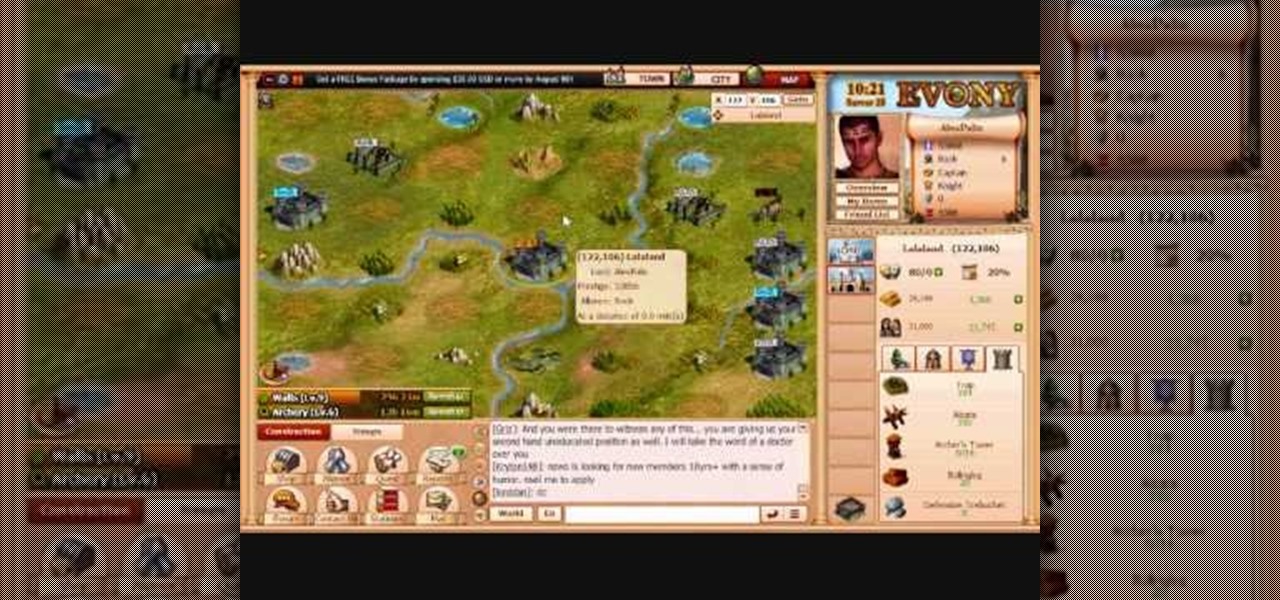
Learn everything you could possibly want to know about the internet, multiplayer game Evony with help from alexstewart2. Watch this video tutorial to learn how to farm rose, lion, cross, and nation medals in Evony.

Watch this video tutorial to learn how to make your own all-natural face masks. Tired of spending a lot of money on facial products that don’t even work? Try on some masks made from items you already own—they’re all natural and good enough to eat!

Watch this video tutorial to learn how to build a shelter in the forest. If you get stuck in the woods, you'll need to know how to protect yourself from the elements.

Brian Brushwood and Scam School give you another way to score free booze at the bar. Memorize a few configs and you'll hold the key to another unbeatable game and loads of free drinks!

If you’re still living in the Ice Age—that is, with a non-defrosting freezer—you’ll need these ancient skills. Learn how to defrost your freezer.

Learn how to play "Teenage Dirtbag" by Wheatus, an acoustic guitar tutorial. Follow along with this demonstration, tabs and lyrics here:

Outdoor Bum teaches you how to package your favorite Chinese or Indian food for dinner at the hut.

A small light tap is one of the easiest and most basic embellishments, and is a nice way for the follower to mark and express the double-time ('quick, quick') - or the 'and' count in between the beats - while the leader is leading a step on the whole beat ('slow'). A tap can be done in the middle of virtually any step - back, side, forward, ocho.

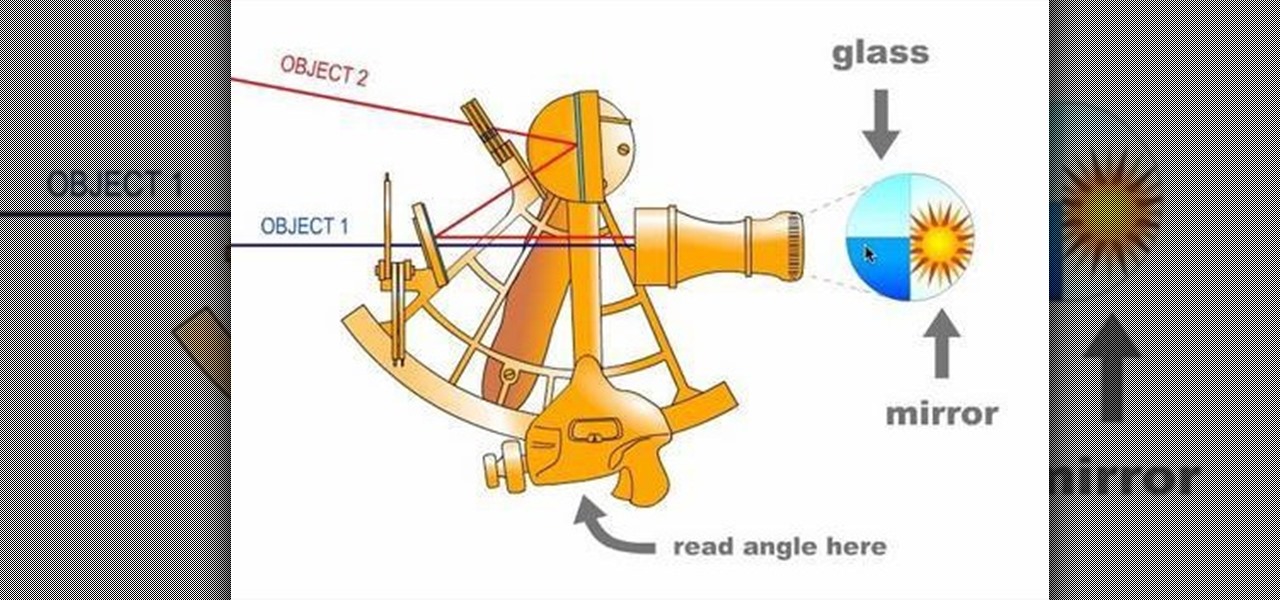
Learn how to find south, your latitude, and your longitude with only a few household items and some know-how, just by watching this science video tutorial. However, if using the homemade quadrant cited, the precision of your findings will be rather low. Don't worry, you'll be within a few hundred miles though.

Ready to try and sew-in your own weave? It's a big decision. As with everything that concerns our hair, we struggle with the pros and cons and often dwell on what could go wrong. Pixie cut. Perm or not? New shade (of pink, purple, or blue). These are all major decisions because ... well, it's our hair, and hair is such a big part of our style. To get a weave or not calls for careful consideration, and to sew one in yourself, that's an even bigger internal debate.

A CNC router machine is probably the most useful tool a hobbyist can own, but the price for a CNC machine on the market is way more than the average hobbyist is willing to spend. You can build your own CNC with very basic tools, little knowledge of machinery, mechanics, or electronics, but be warned, these machines are inherently dangerous, so wear the proper protection and use common sense. At the very least, read the instructions and precautions on every tool you use.

A CNC router machine is probably the most useful tool a hobbyist can own, but the price for a CNC machine on the market is way more than the average hobbyist is willing to spend. You can build your own CNC with very basic tools, little knowledge of machinery, mechanics, or electronics, but be warned, these machines are inherently dangerous, so wear the proper protection and use common sense. At the very least, read the instructions and precautions on every tool you use.

Want a new way to solve the OLL (Orientation of the Last Layer) on a Rubik's Cube? Well, go no further, this video tutorial will show you how to use the 2-Look OLL method to solve the Rubik's Cube.

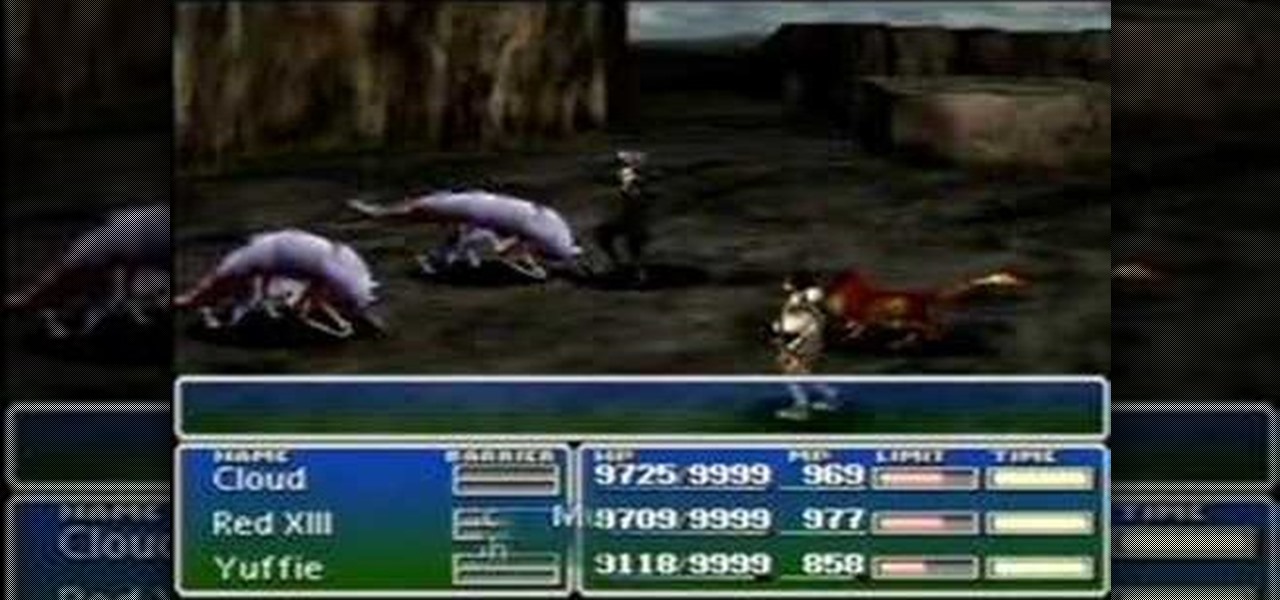
In Final Fantasy VII, it's possible to max out vitality without any store-related progress needed if your strength stat has already been maxed. Take a look at this video and learn how to max out vitality simply by targeting an enemy called "spiral".

Making a PCB is very simple; it does not consume a lot of time and the results look professional. After watching this step-by-step how-to video, you will be able to make your own PCB in your workshop using just a few inexpensive materials.

It's just a fact that hairy legs on women are not the most attractive. From razors to lasers, hairy legs can be a thing of the past. Hairy legs are some of the hardest parts to deal with because they're so visible all the time. Whether you want to rid yourself of prickly leg hair or just simply hide it, there are always solutions for your hairy legs. Shaving is of course the most common way of removing leg hair. It's relatively quick and easy, and once it's built into your routine you don't e...

Learn how to do neutral grip pull ups. Presented by Real Jock Gay Fitness Health & Life. Benefits

Learn how to do alternate hand kiss wide grip pull ups. Presented by Real Jock Gay Fitness Health & Life.

Learn how to do seated alternate cable rows on a stability ball. Presented by Real Jock Gay Fitness Health & Life.

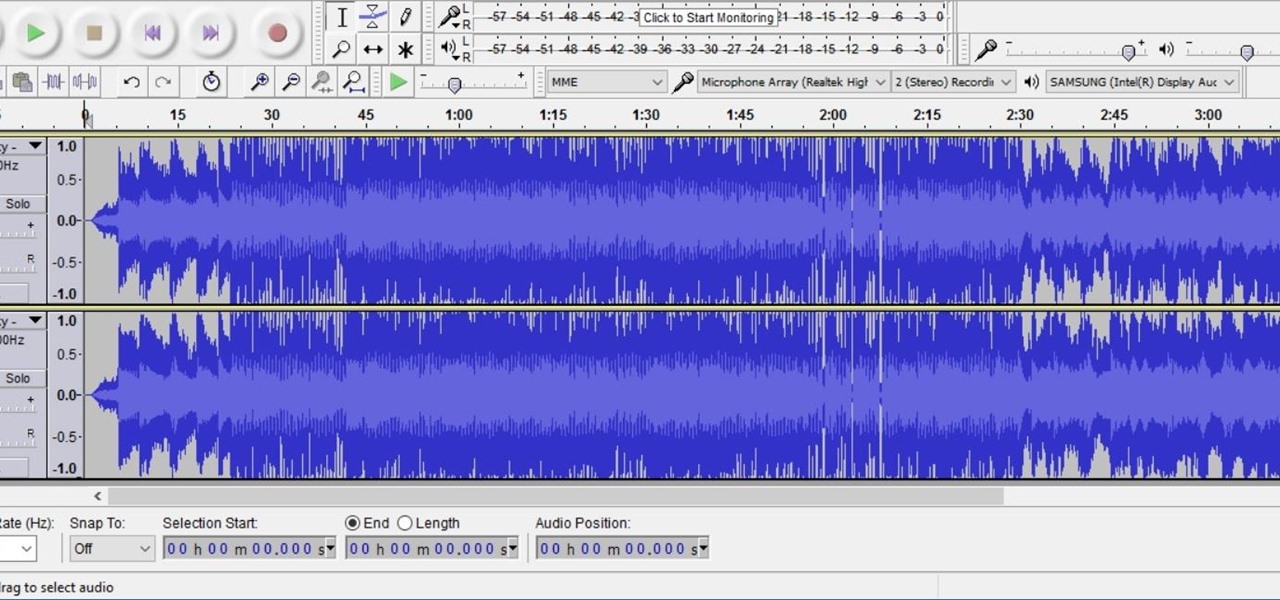
Need to remove the vocals from a song? Audacity just might be the answer. It's one of the few free audio editing programs out there with many, many features, making it simple to create a track for karaoke or simply to listen to an instrumental version.

To keep your young tree healthy through the winter there are several maintenance tips to keep in mind. You need to protect them from mice and voles gnawing around the base of the tree because they can easily girdle the bark and cause a tree to die. A simple way to prevent this is to use a plastic wrap. Simply put it around the base of the tree about an inch or so below the soil line and wrap it around the tree all the way up. This will prevent the little mice teeth from gnawing on the bark. A...

It's exciting to get that reverse shell or execute a payload, but sometimes these things don't work as expected when there are certain defenses in play. One way to get around that issue is by obfuscating the payload, and encoding it using different techniques will usually bring varying degrees of success. Graffiti can make that happen.

Unlike some of the popular app lockers out there, a nifty app fittingly named App Hider completely erases apps, files, and their associated footprints from your smartphone. Think of App Hider as a micro-OS within your smartphone's system. This miniature ecosystem can operate copied apps independently, thus giving it an unprecedented layer of privacy and freedom within your handset.

For years, Apple's Notes app has been a reliable way to jot down important ideas, tasks, plans, and more. While there are apps on the market that advertise themselves as being more feature-filled than the stock iOS option, Apple is now giving them a run for their money. Here are 14 new features and changes you'll see with Notes in iOS 13.

NetBIOS is a service that allows for communication over a network and is often used to join a domain and legacy applications. It is an older technology but still used in some environments today. Since it is an unsecured protocol, it can often be a good starting point when attacking a network. Scanning for NetBIOS shares with NBTScan and the Nmap Scripting Engine is a good way to begin.

With the number of web applications out there today, it comes as no surprise that there are just as many vulnerabilities waiting for hackers to discover. Finding those vulnerabilities can be a difficult task, but there are plenty of tools available to make the process easier. While it won't help find any zero-days, web scanners such as Uniscan will detect common vulnerabilities.

Users are often the weakest link when probing for vulnerabilities, and it's no surprise they can be easily fooled. One way to do this is called clickjacking. This type of attack tricks the victim into clicking something they didn't mean to click, something under the attacker's control. Burp Suite contains a useful tool called Clickbandit to generate a clickjacking attack automatically.

Excessive cell phone use was issue that Apple decided to tackle with iOS 12. Starting with the iPhone's 2018 update, a new "Screen Time" feature give you the ability to set App Limits to encourage more balanced usage, and there's another setting that gives you control over when certain apps can be accessed.

Web application vulnerabilities are one of the most crucial points of consideration in any penetration test or security evaluation. While some security areas require a home network or computer for testing, creating a test website to learn web app security requires a slightly different approach. For a safe environment to learn about web app hacking, the OWASP Juice Shop can help.

It always helps to be prepared for the worst. This applies to our phones now more than ever, as we depend on them to be our record keepers for text messages from friends, family, and coworkers. If you ever lose or severely damage your phone, having a backup of your precious texts gives you the peace of mind of knowing that you can always get them back.