Without much notice, Spotify launched Desktop Open Beta a few weeks ago, a program that allows anyone to download, test out, and provide feedback on the latest beta version of their desktop application for Mac and Windows.
Trust can be a touchy subject in general, and is often required when sharing personal information—especially so when handing our phones over to others. You may not have a ton of secret or nefarious information on your device, but that doesn't mean you want your mom or snoopy coworker having easy access to your messages or Facebook app.

The Galaxy S5's camera is amongst the most capable smartphone shooters on the market. With a 16-megapixel sensor that is capable of recording 1080p video at 120 frames per second, the stat sheet was officially stuffed when Samsung brought this device to market.
If you pay close attention, you might notice that the screen on your Android begins to flicker or pulsate when you lower the brightness past a certain point. This is a result of the AMOLED technology Samsung, among other manufacturers, use in their displays, and the way that these types of screens operate.

With hundreds of pictures accumulating on my device, it's a daunting task to devote time to sorting through which are worth keeping and which I should discard. Not all of the images on my device are winners, so the losers not only take up space, they make it difficult to find the good ones as I wade through the crap.
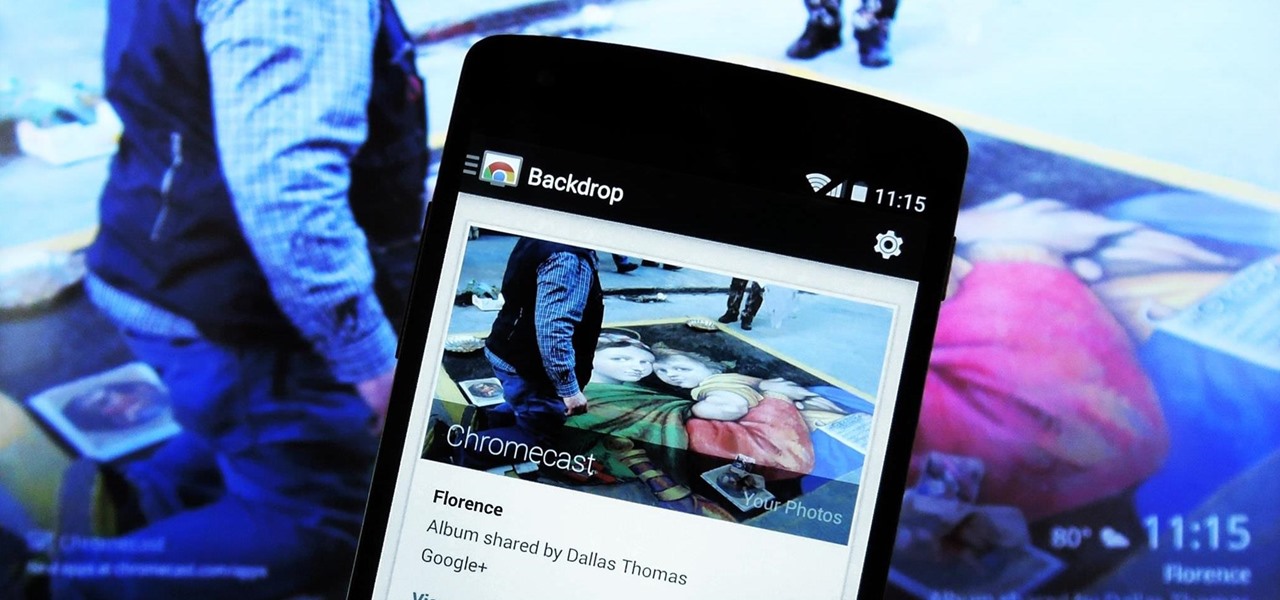
It's been a long-awaited feature since being announced at Google I/O in June, but Backdrop for Chromecast has finally started rolling out. With an update to the Chromecast app for Android and iOS, users will be able to personalize the background images that appear when Chromecast is idle.

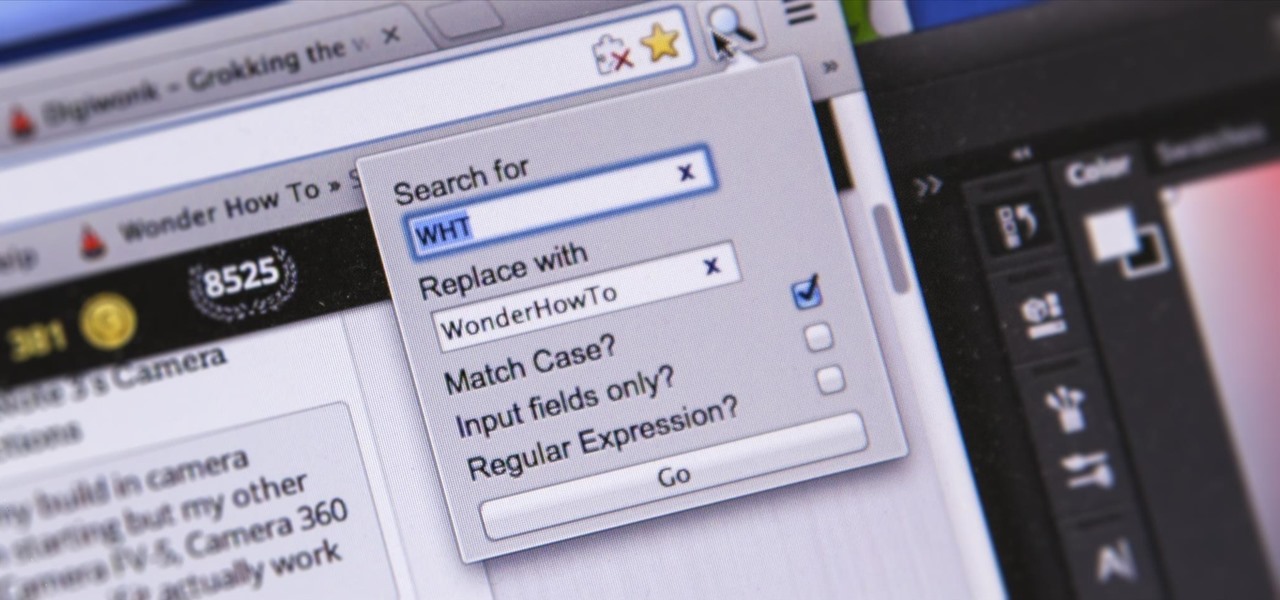
I'm sure you've been there—halfway through typing something out, you realize that one word you've been using more than any other has been misspelled. Perhaps it's a single word, acronym, or line of code that you find yourself typing quite often at work, but this one requires complicated hand gymnastics that you'd simply rather not perform over and over again.

Coffee! It's so amazing that J.S. Bach wrote a comic opera about caffeine addiction. Meanwhile, more than half of Americans 18 years or older start their day with a cup of the hot stuff. Most of us take coffee for granted, but it's a bean that can surprise you. Read on to understand more about coffee and how to take advantage of all that it offers.

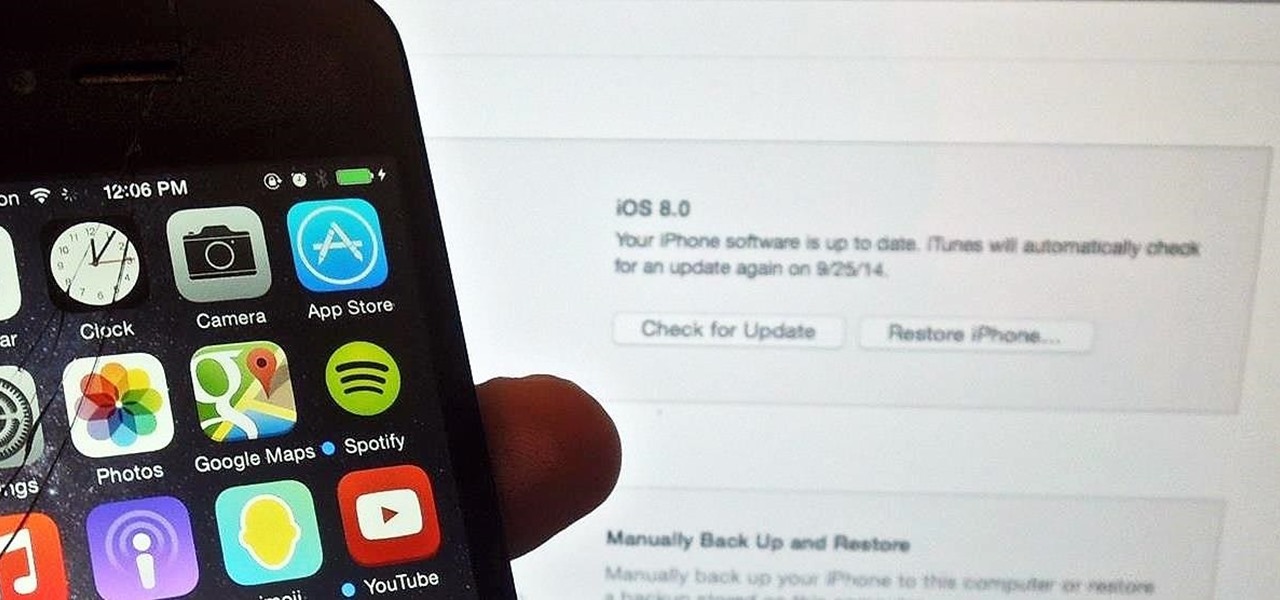
There are a lot of great new features in iOS 8, but not everyone is enjoying them. Some of you may just genuinely prefer iOS 7 over iOS 8, and some of you may be experiencing lag on older devices like the iPhone 4S, however minimal it may be. Whatever the reason, if you don't want iOS 8 on your iPad, iPhone, or iPod touch, there's still time to downgrade back to iOS 7.1.2.

iPad, iPhone, and iPod touch owners: it's that time again. iOS 8 has been released to the public, and those who have been eager to update since Apple's WWDC announcement won't have to wait any longer. Since iOS 8 promises to pack a bunch of new, really great features, it's time to present your options for getting on the latest and greatest for your Apple device.

Pushbullet is one of those apps that helps separate Android from its competition. By pushing the boundaries of cross-platform data syncing and file sharing, the service truly demonstrates how flexible and robust the world's leading mobile operating system can be.

How many times have you witnessed a beautiful moment that you would have loved to capture on film, only to watch it slip away as you struggled to unlock your phone and open your camera app?

In the past few weeks, the internet has been abuzz with nightmarish horror stories of Comcast's questionable decision-making and downright terrible customer service. The central theme of many of these disputes with the nation's largest cable provider is that without evidence, the conglomerate will refuse to acknowledge its mistake and place the burden of proof on the customer.

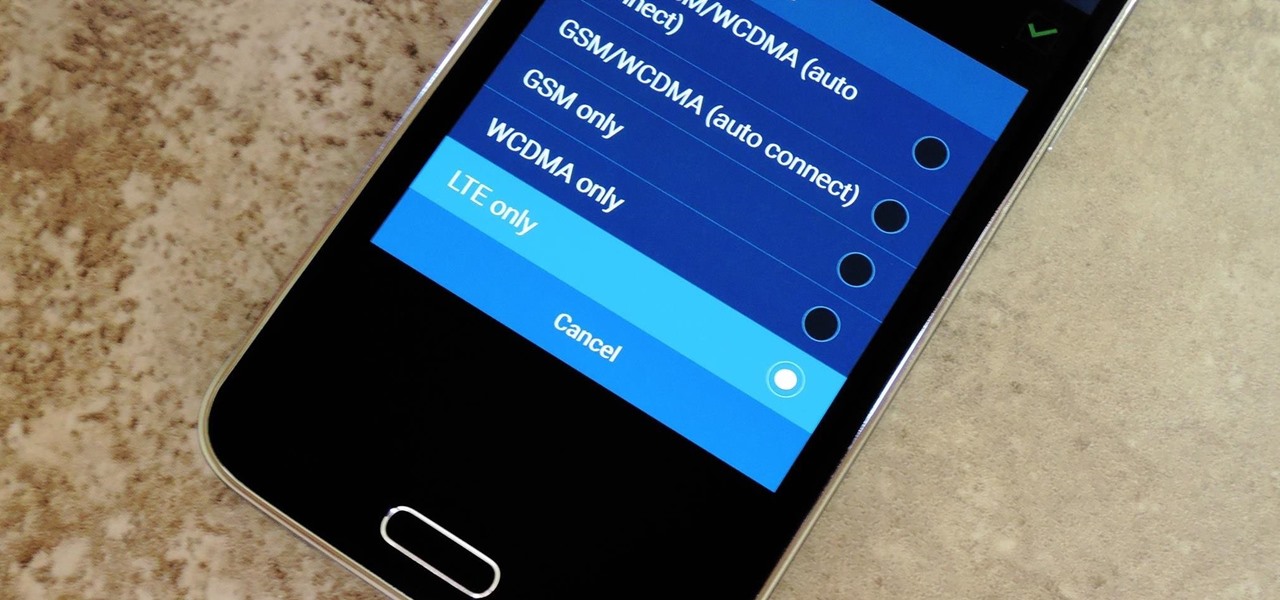
Even with the highest-tiered data plan available, there are times that your phone or your carrier might downgrade your connection to 3G or even lower. This usually occurs when you've made a phone call, or you've switched cell towers while traveling.

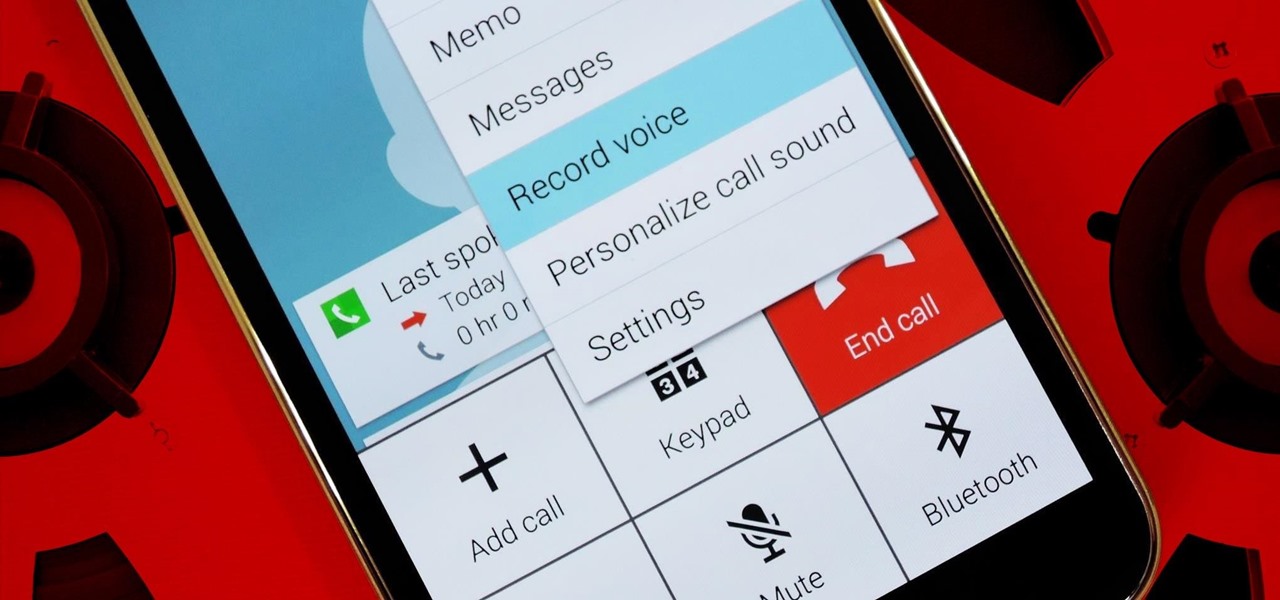
Before your carrier got its grubby little hands on your Galaxy S5, there was less bloatware installed and more functionality offered by the Samsung flagship device. Case in point: the GS5 that Samsung designed was capable of recording phone calls, yet the one that you own probably isn't.

Apps that save your passwords have been around for quite a long while. But apps that complete the entire login process automatically? Now that's a different story.

How many times do you misplace your phone? Once a day? Twice? As much as you may hate losing your phone, it always seems to happen, and finding it isn't very easy if you left it on silent mode.

Welcome back, my rookie hackers! I recently began a series on using Metasploit, and my goal with it is to teach you the very basics the incredibly powerful hacking tool has to offer while progressively moving on to the more advanced features.

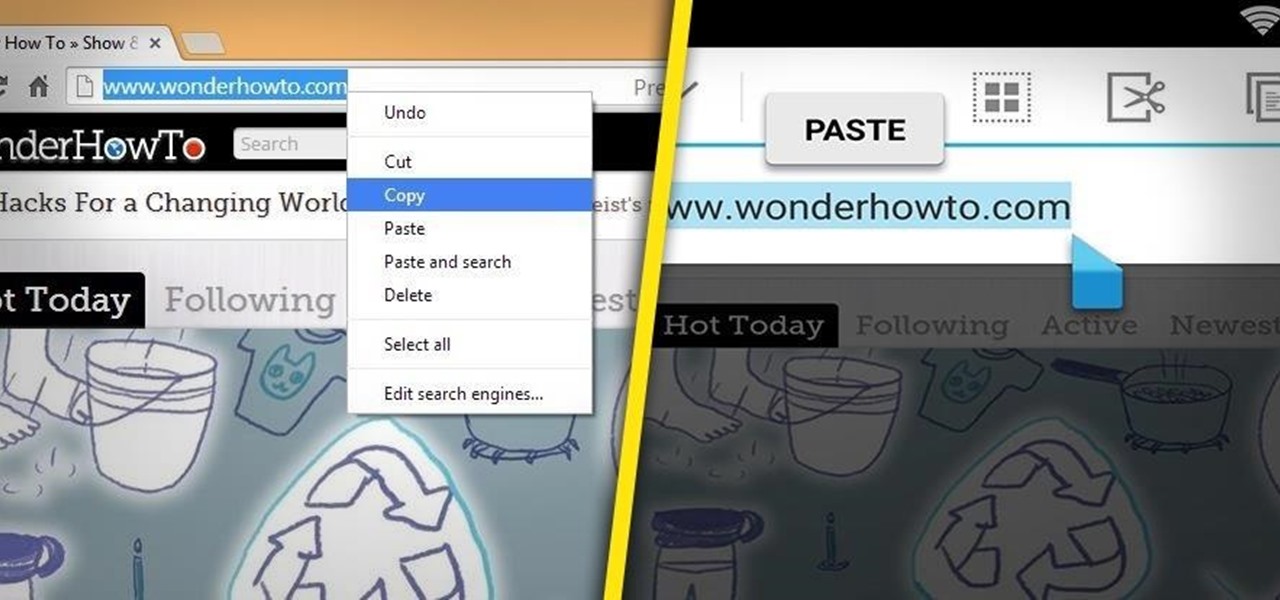
Do you take your notes on a word processor while browsing the web? Well, stop. There's an easier, less RAM hungry way to take notes by turning the tab of your web browser into a notepad. Whether it's an email address, a line of code, a new how-to, or an idea you don't want to lose, you can easily jot it down without slowing down.

Stock Android has come with lock screen widget support for a couple of years now, ever since the days of the first Ice Cream Sandwich build. But for some reason, Samsung decided to remove this feature in the Galaxy S5.

Want to learn how to make Peppa Pig with Play-Doh? Here is our attempt on showcasing a tutorial on how to make Peppa Pig with Play-Doh.

Welcome back, my novice hackers! It has become clear from some of your questions that quite a few of you are unfamiliar with the hexadecimal system, or simply, hex. The hexadecimal system is used throughout computing and if you have never studied this Base16 numering system, it may appear relatively opaque.

To-do list and reminder apps are a dime a dozen on Google Play, so trying to find the right one for you could take hours as you sift through hundreds of similar apps and widgets. Well, search no more, as we've found one of the most well-designed and easy-to-use reminder apps out there.

Your beloved Samsung Galaxy S3 is nearing the end of its life cycle. Sure, it can do most of what newer devices can, especially if you were lucky enough to receive the KitKat update, but your diminishing battery and scratched up screen have seen better days.

Whether it's bad timing, or some trying-to-be-funny photobomber, it sucks having a photo ruined by someone or something getting in the way. While you can always retake the photo, it's simply impossible to capture the moment you intended, no matter how much restaging you do. But with an HTC One, there's no need to retake anything, as we have access to built-in features that will remove those photo intruders.

Transparent status bars and new lock screens weren't the only new additions that came with the Galaxy S3 KitKat update. Along with better battery life and a smoother user experience, we got a new toggles design and recent apps menu. Of course, Samsung's infinite wisdom left these two aesthetic features hidden away. Luckily, with root, you can easily enable them with just a few quick edits.

Let's say you're watching a video and everything's going great, but you feel the need to raise the volume a tiny bit. You hit the volume button on your Nexus 5, and all of a sudden, a giant volume slider appears that obscures half of your video for 3 seconds.

Figuring out someone's password, pattern, or PIN isn't very difficult—simply watching over their shoulder or following the oil marks left across their screen is enough to figure them out and bypass whatever lock screen security they have.

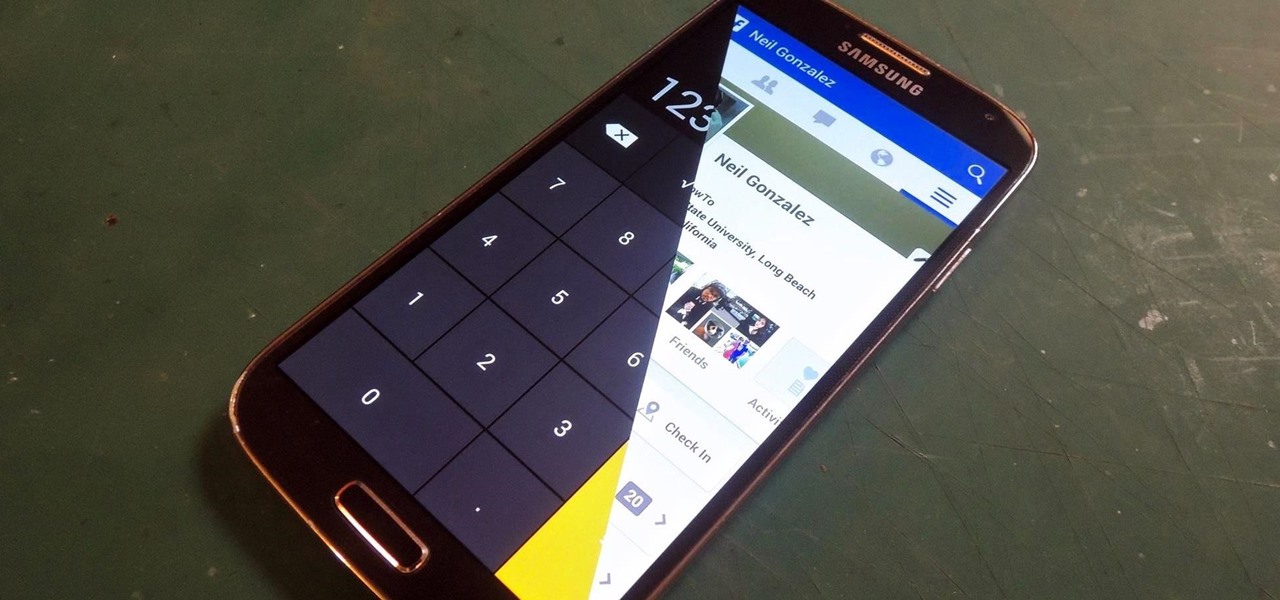
If you lend someone your phone, even if it's just for a second, there's a chance they can enter an app and see something you'd rather they didn't. Whether it's a personal email or a private photo, there are plenty of reasons why you'd want to keep snoops out of certain apps.

Accessing notifications and quick settings from the lock screen just makes things move quicker and more efficiently, unless of course we're using a secure lock screen. It makes sense that if we have face, pattern, or pin security enabled, we may not want notifications accessible, but really, that should be something we decide for ourselves—and now we can.

Notifications, while certainly helpful, can at times be overbearing. There are banners plastered every which way on your smartphone for almost every application. While many of the notifications can simply be swept away or turned off, the same can't be said of persistent notifications.

Welcome back, my novice hackers! I have tried to emphasize throughout this "Hack Like a Pro" series that good reconnaissance is critical to effective hacking. As you have seen in many of these hacks, the techniques that we use are VERY specific to the:

Midway through 2013, a popular custom ROM called Paranoid Android introduced their multitasking feature "Halo." Bubble-style notifications inspired by Facebook chat heads pop up near the top of the screen, and you simply tap on them to bring up the app in a floating window.

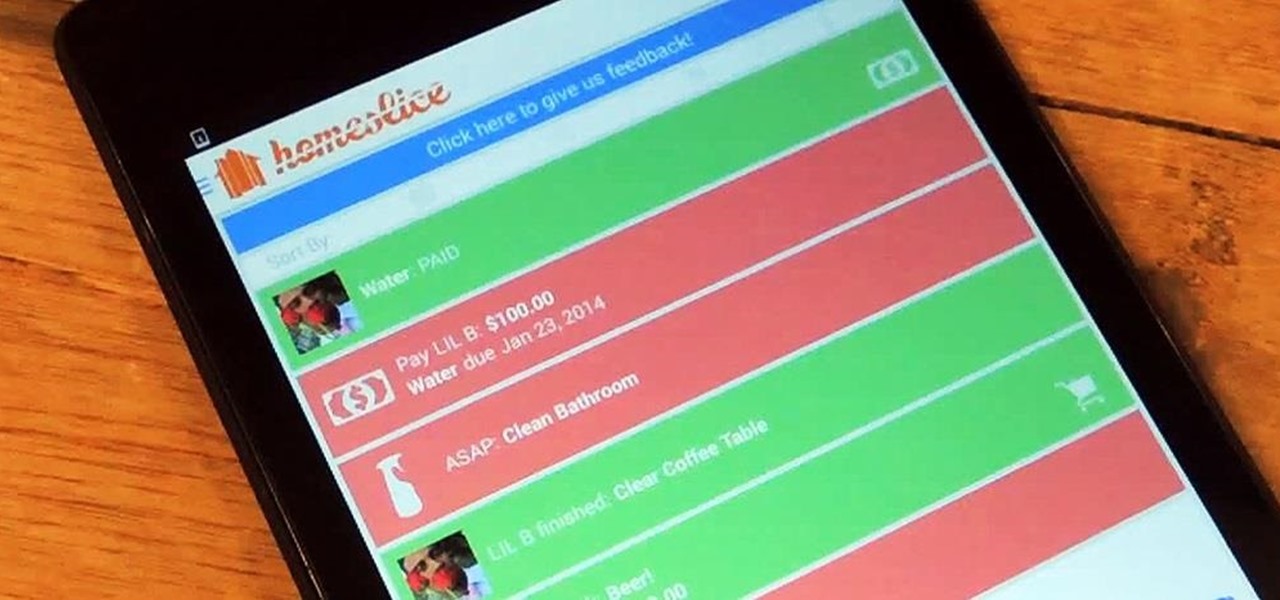
We've all heard our fair share of roommate horror stories, or have some of our own, because we never truly know who someone is until we've lived with them. Cohabitation issues generally revolve around things like bills, chores, cleaning, and groceries. Approaching a roommate, especially an adult one, to remind them to do their chores can be an anxiety-ridden and daunting task. After all, we're roommates, not parents!

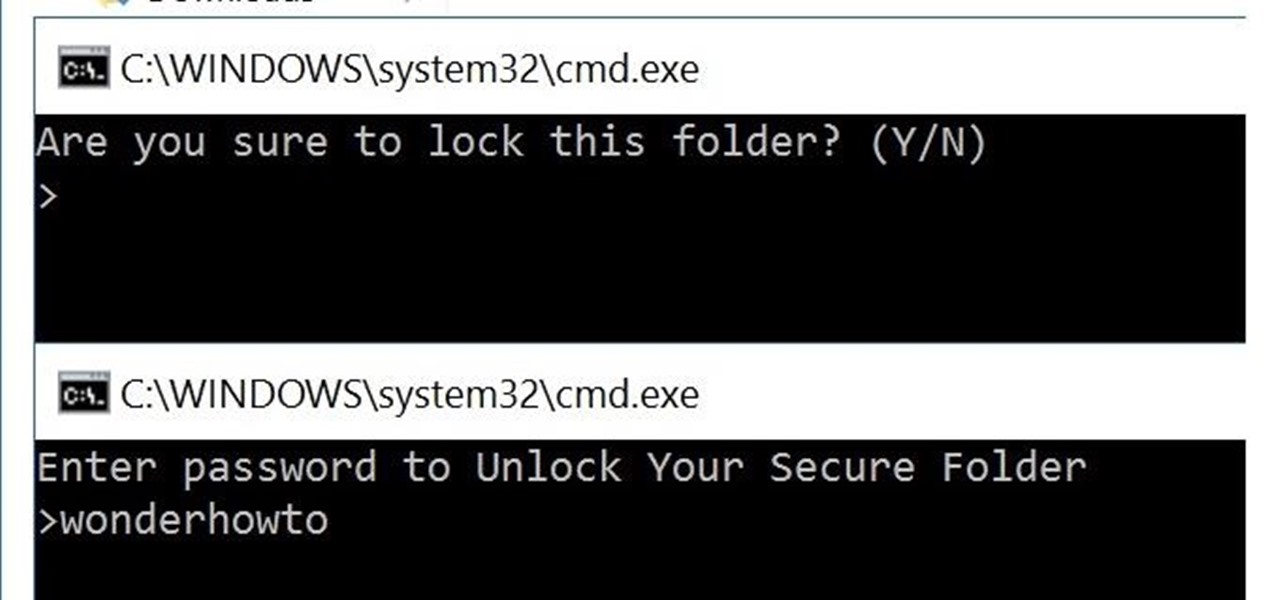
You can easily lock any folder on your Windows computer with a simple Notepad hack. By creating a batch file, you can hide a folder and require a password be entered before it becomes visible and accessible. This is a great tool for locking sensitive information, like pictures, financial statements, and a lot more.

Welcome back, my budding hackers! I've written several listener guides on creating a malicious PDF or malicious Word document that would carry in it a payload with the Meterpreter, or reverse shell enabling you to own the system. One of the hurdles to using these techniques is the antivirus (AV) software on the target system. For instance, if you try to email a malicious PDF or Word doc, it's likely that the victim system will alert the victim that it contains a virus or other malware.

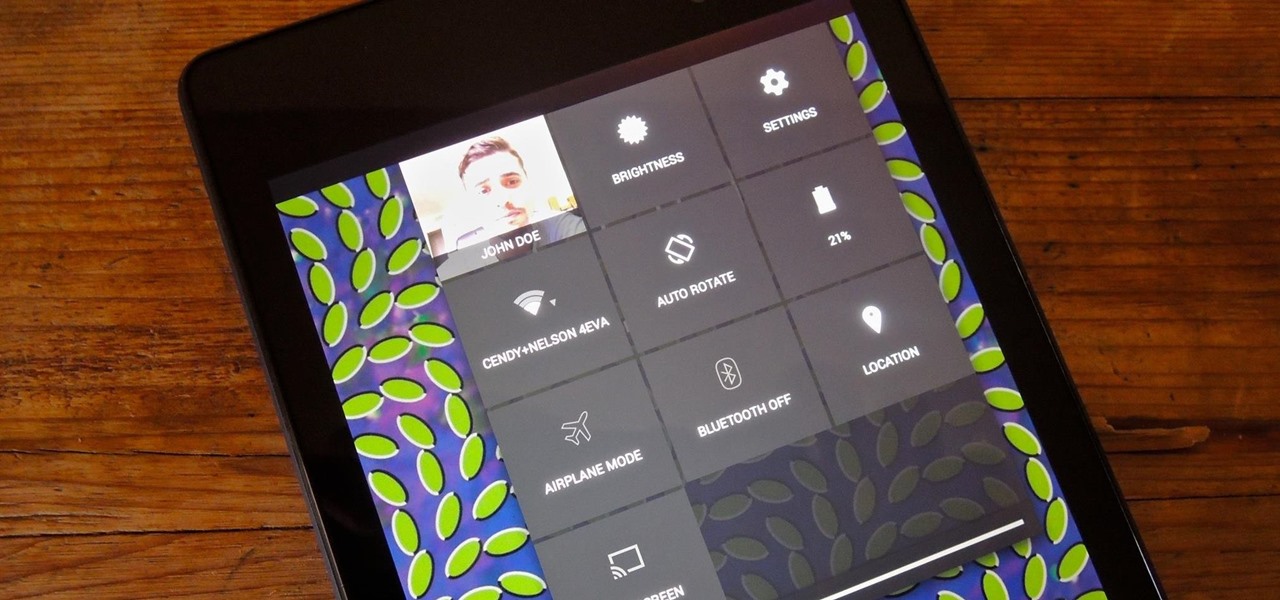
A great aspect of using Android is having the ability to change and tweak aspects of the user experience to your liking. You can easily change things like home screens, widgets, and icons on your Nexus 7 tablet, but also core system settings if you want, like volume settings. Most stock systems come standard with a "15 step" volume control. That means simply that you have 15 levels from mute to the loudest volume settings. Whether your an audiophile or just someone who wants a little more con...

Welcome back, my fledgling hackers! It's been awhile since we did a Metasploit tutorial, and several of you have pleaded with me for more. I couldn't be happier to oblige, as it's my favorite tool. For the next several weeks, I'll intersperse some new guides that'll help expand your Metasploit skills and keep you abreast of new developments in Metasploit, so look for them in the near future.

Welcome back, my fledgling hackers! Nearly every commercial enterprise worth hacking has an intrusion detection system (IDS). These network intrusion detection systems are designed to detect any malicious activity on the network. That means you!

Welcome back, my nascent hackers! Earlier, I wrote a guide on finding operating system and application vulnerabilities in Microsoft's own security bulletins/vulnerability database. In this tutorial, I will demonstrate another invaluable resource for finding vulnerabilities and exploits by using the SecurityFocus database.