Last time in how to train you python, we covered the basics of variables and output. While we were covering variables, we talked briefly about strings. "String" is just a fancier way of saying "Word". A string is simply a set of characters encased in quotations, this lets python know that it is a word. Sometimes when we do things with strings we'll need to change them in order to do something. Python is case sensitive, for example "Null-Byte" is not the same as "null-byte". This is where mani...

Android has a brand new mobile payments system, and it's rolling out to most devices as we speak. Android Pay, as it's called, will replace the existing Google Wallet app as an update, and it brings some awesome new functionality such as tokenization and the ability to tap-and-pay by simply unlocking your phone.

Computer system authentication is critical to keeping systems safe from unwanted users, intruders, and abusers. Basically, authentication is the process of the potential user proving they are an authorized user.

In my opinion, spices are the key to a successful kitchen. With a healthy array of spices and spice mixes, you have the foundation for nearly any dish that you want to make; the culinary world is your oyster. With a depleted cupboard of spices, however, nearly every recipe looks intimidating and unattainable.

Everyone's favorite Android modding tool is finally available for the Galaxy S6 and S6 Edge. Thanks to some hard work by Wanam and a few other developers, we can now install the Xposed Framework on Samsung's latest mid-sized flagship phones.

Your average Android phone or tablet comes with quite a few apps already installed—even before you turn the device on for the first time. These pre-installed apps are certainly helpful when it comes to getting your feet wet with Android, but in many cases, they're not always the best apps available for accomplishing the tasks that they perform. Additionally, many third-party apps can add lots of cool functionality to your device, so you might say that sticking with only the pre-installed apps...

If your Android device wasn't manufactured by Samsung, chances are it uses on-screen navigation buttons. Colloquially referred to as "Soft keys," these have become commonplace due to their flexibility, as well as the fact that manufacturers don't have to include extra hardware buttons with a propensity to fail.

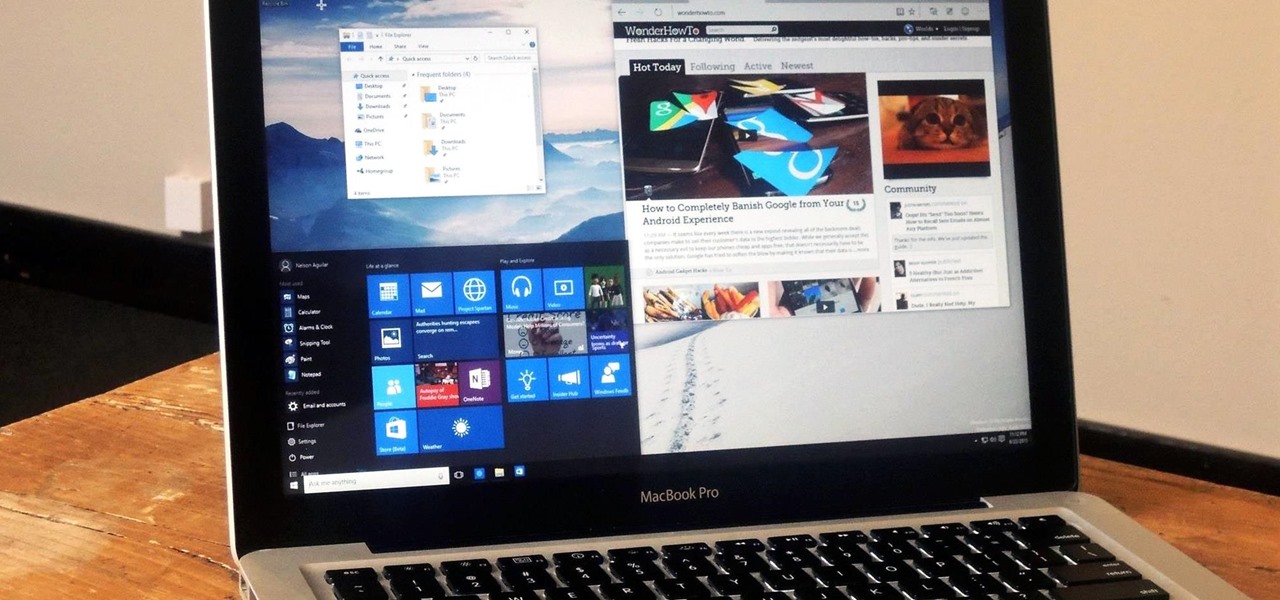
While Windows 10 is still a few weeks away from a public release, that doesn't mean you can't enjoy its brand new features right now. Anyone with an Insider Preview account can install Windows 10 on their computer. And that doesn't just go for those that own a Windows PC—Mac users can get their hands on Windows 10 as well.

We're all familiar with the sinking feeling that happens when you cruise through a recipe, only to arrive at an instruction that calls for a tool you don't have. Some of the best food hacks (and my personal favorites) exist to combat that problem. Why spend money on a kitchen tool—or worse, avoid a recipe altogether—when you could find a new way to achieve the same result?

If you're a Mac user with an Android phone, some apps on your computer aren't very useful, such as Messages, which is meant to work and sync with iOS devices. But now, thanks to MDRS, LLC, using the Messages app on your Mac with an Android phone is now possible and easily achievable. Plus, we've got 50 promo codes to give away for a free year of service!

If your iPhone is rebooting or your Messages app is constantly crashing, you might be the victim of an iOS exploit or just a buggy software update. While one problem sounds worse than the other, they both can get annoying real quick when you can't send any messages or even read new ones.

Summer is right around the corner, which means it's time to switch from perfect hot coffee to perfect cold coffee. A nice icy glass of cold coffee is wildly refreshing and just plain delicious. In my opinion, it's the key to enjoying any sunny day (warning: if you don't already drink cold coffee, you may find yourself drinking four or five glasses a day very quickly).

Reddit is one of the internet's greatest sources of funny and interesting videos. Its user base is extremely active, and a system of upvotes and downvotes ensures that the best content always rises to the top.

Welcome back, my novice hackers! As we saw in my first tutorial on Facebook hacking, it is not a simple task. However, with the right skills and tools, as well as persistence and ingenuity, nothing is beyond our capabilities.

The Nexus Player is one of the most robust set-top streaming devices on the market. This is mainly due to the fact that the base software it runs is a direct fork of Android, which is a very powerful operating system itself.

Sling TV, the new over-the-top TV streaming service from DISH Network, is the first to offer live programing for cord cutters. Available for $20 a month with no contract, Sling TV is the easiest way to end the reliance on cable and satellite subscriptions for getting your content as it airs.

Welcome back, my hacker novitiates! Eluding and evading antivirus software and intrusion detection systems is one of the most critical tasks of the hacker. As soon as a new exploit is developed and discovered, the AV and IDS developers build a signature for the attack, which is then likely to be detected and prevented.

Soup can be one of the most finicky dishes to make. While seemingly innocuous at first, the texture of this meal can change in an instant. For example, adding too many vegetables can result in soup that's too watery, such as tomatoes, which contain a lot of liquid.

While most people build collections of things with intrinsic value such as coins, stamps, or rare post cards, I collect wine corks—the natural ones, not the plastic kind. Corks are a natural product harvested from the cork oak tree. It takes the better part of 10 to 12 years before a tree can have its bark manually removed for the production of cork. Thankfully, no tree is harmed in the process and in 12 years, the tree bark can be harvested yet again.

One of the golden rules to cooking a Thanksgiving turkey is to place it on a roasting rack before it goes into the oven. Missing this step and cooking it directly on the pan will burn the bottom of the bird, resulting in overcooked, dry meat.

When it comes to subscription-based music streaming services, the conversation doesn't go much further than Spotify and Google Play Music (previously called "All Access"). Both services are essentially the same aside from slightly different catalogues and social options, and they both run ten bucks a month for unlimited music streaming and offline track saving (although Spotify does have a free, ad-supported service).

With all of the different websites we use in our day-to-day lives, keeping track of our numerous login credentials can start to become a hassle. This has created a market for password managers that aim to centralize these account credentials and generally streamline the process of logging into our favorite sites.

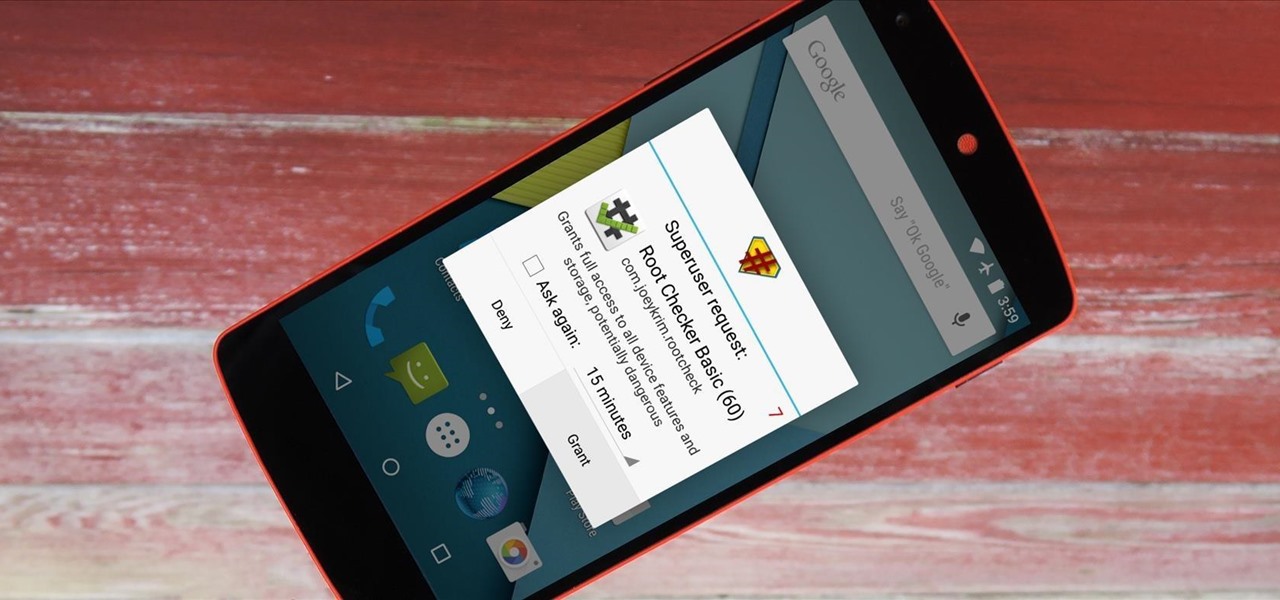
It didn't take long at all for developer Chainfire to sort out a root method for the new Android 5.0 Lollipop. After handling a few issues with changes to the SELinux kernel module, Chainfire pushed out an update to his popular SuperSU root app.

If you pay close attention, you might notice that the screen on your Android begins to flicker or pulsate when you lower the brightness past a certain point. This is a result of the AMOLED technology Samsung, among other manufacturers, use in their displays, and the way that these types of screens operate.

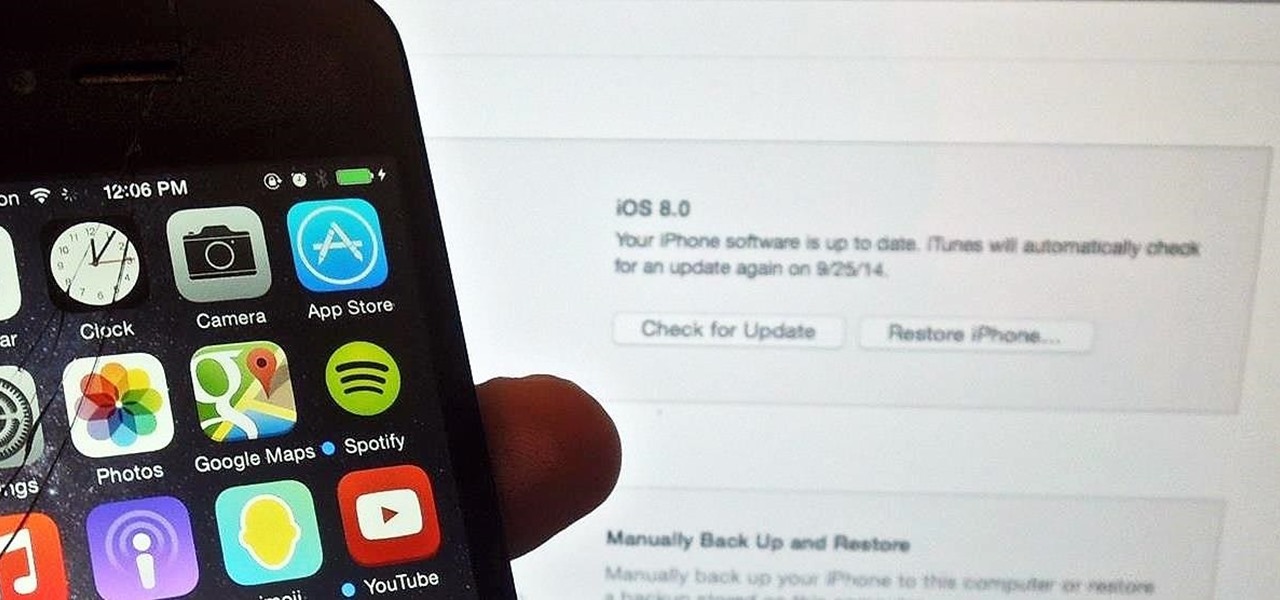
There are a lot of great new features in iOS 8, but not everyone is enjoying them. Some of you may just genuinely prefer iOS 7 over iOS 8, and some of you may be experiencing lag on older devices like the iPhone 4S, however minimal it may be. Whatever the reason, if you don't want iOS 8 on your iPad, iPhone, or iPod touch, there's still time to downgrade back to iOS 7.1.2.

iPad, iPhone, and iPod touch owners: it's that time again. iOS 8 has been released to the public, and those who have been eager to update since Apple's WWDC announcement won't have to wait any longer. Since iOS 8 promises to pack a bunch of new, really great features, it's time to present your options for getting on the latest and greatest for your Apple device.

Pushbullet is one of those apps that helps separate Android from its competition. By pushing the boundaries of cross-platform data syncing and file sharing, the service truly demonstrates how flexible and robust the world's leading mobile operating system can be.

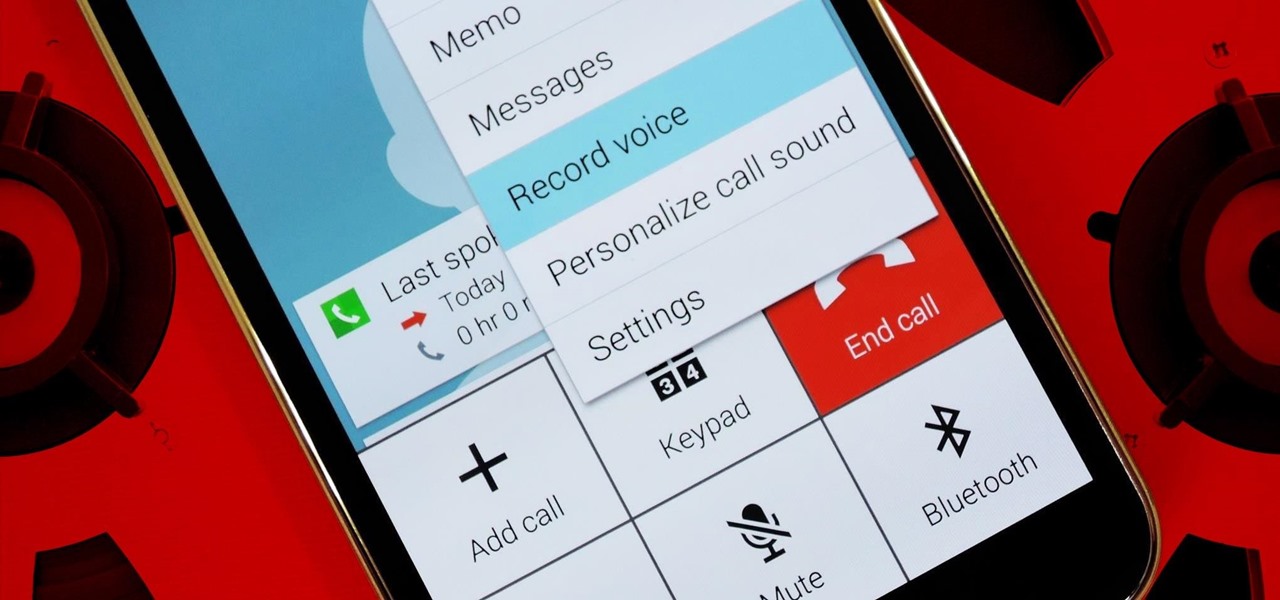
Before your carrier got its grubby little hands on your Galaxy S5, there was less bloatware installed and more functionality offered by the Samsung flagship device. Case in point: the GS5 that Samsung designed was capable of recording phone calls, yet the one that you own probably isn't.

How many times do you misplace your phone? Once a day? Twice? As much as you may hate losing your phone, it always seems to happen, and finding it isn't very easy if you left it on silent mode.

Welcome back, my rookie hackers! I recently began a series on using Metasploit, and my goal with it is to teach you the very basics the incredibly powerful hacking tool has to offer while progressively moving on to the more advanced features.

Update: August 1, 2014 Earlier today, President Obama signed into law the Unlocking Consumer Choice and Wireless Competition Act, making the act of unlocking your unsubsidized cell phone 100% legal.

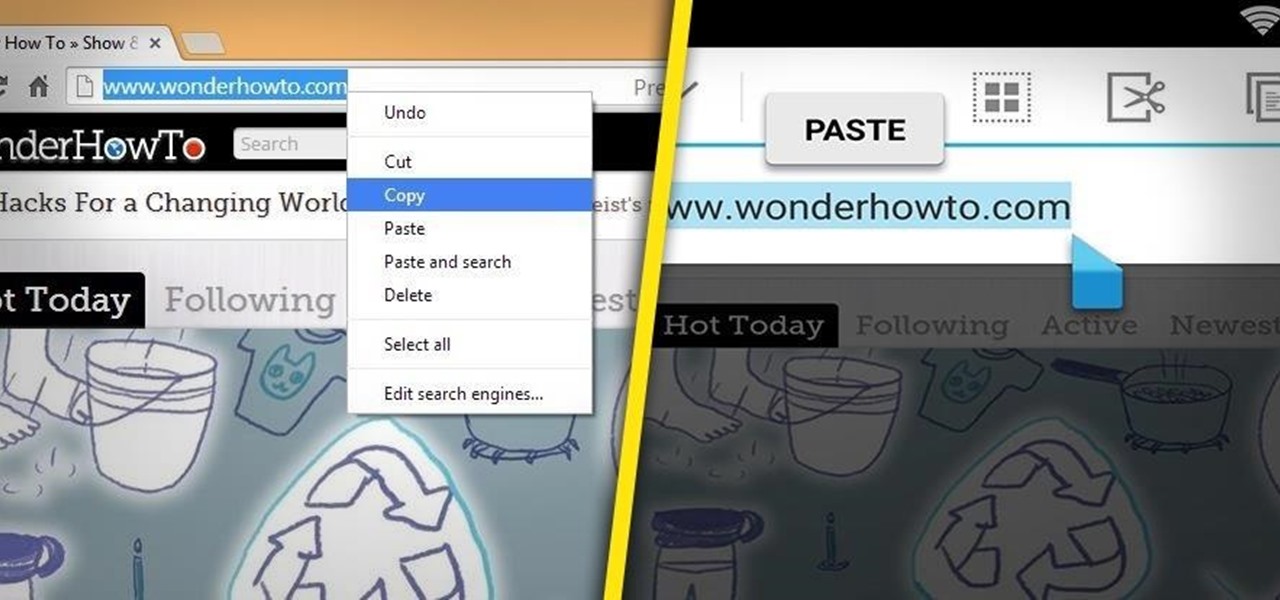
Do you take your notes on a word processor while browsing the web? Well, stop. There's an easier, less RAM hungry way to take notes by turning the tab of your web browser into a notepad. Whether it's an email address, a line of code, a new how-to, or an idea you don't want to lose, you can easily jot it down without slowing down.

Welcome back, my novice hackers! It has become clear from some of your questions that quite a few of you are unfamiliar with the hexadecimal system, or simply, hex. The hexadecimal system is used throughout computing and if you have never studied this Base16 numering system, it may appear relatively opaque.

Welcome back, my novice hackers! I have tried to emphasize throughout this "Hack Like a Pro" series that good reconnaissance is critical to effective hacking. As you have seen in many of these hacks, the techniques that we use are VERY specific to the:

Midway through 2013, a popular custom ROM called Paranoid Android introduced their multitasking feature "Halo." Bubble-style notifications inspired by Facebook chat heads pop up near the top of the screen, and you simply tap on them to bring up the app in a floating window.

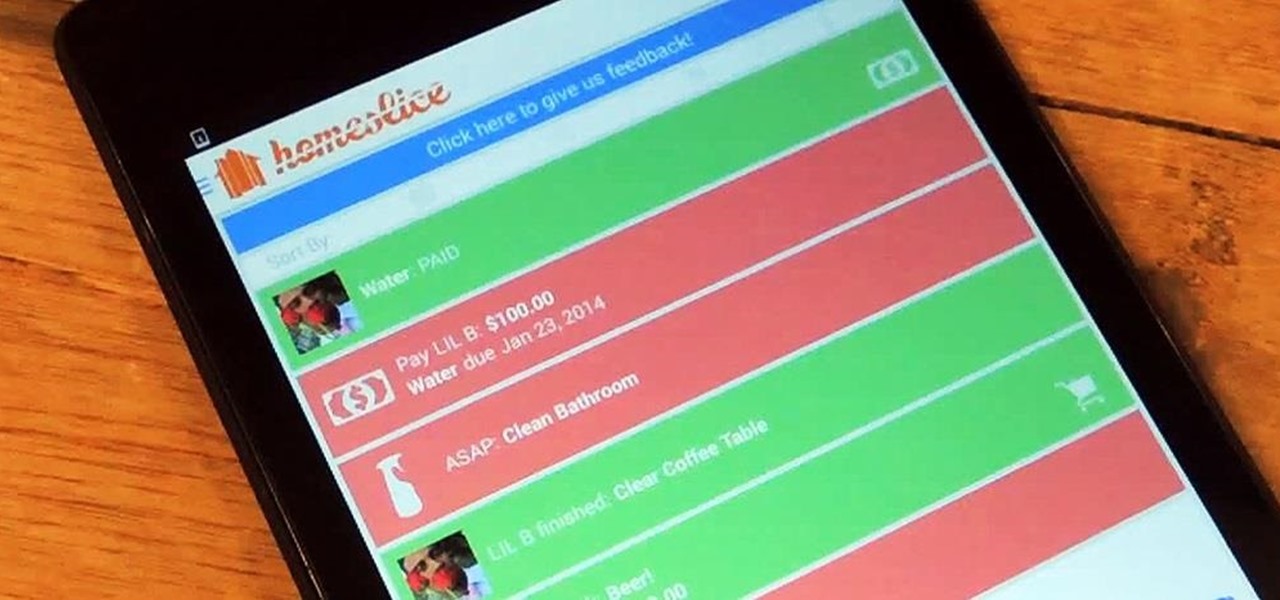
We've all heard our fair share of roommate horror stories, or have some of our own, because we never truly know who someone is until we've lived with them. Cohabitation issues generally revolve around things like bills, chores, cleaning, and groceries. Approaching a roommate, especially an adult one, to remind them to do their chores can be an anxiety-ridden and daunting task. After all, we're roommates, not parents!

Welcome back, my budding hackers! I've written several listener guides on creating a malicious PDF or malicious Word document that would carry in it a payload with the Meterpreter, or reverse shell enabling you to own the system. One of the hurdles to using these techniques is the antivirus (AV) software on the target system. For instance, if you try to email a malicious PDF or Word doc, it's likely that the victim system will alert the victim that it contains a virus or other malware.

One of the biggest problems in data security is authentication of data and its source. How can Alice be certain that the executable in her inbox is from the venerable Bob, and not from the not-so-venerable Oscar? Clearly Alice wants to know because if this file is actually sent to her by Oscar, the file might not be a game, but a trojan that can do anything on her computer such as sift through her email and passwords, upload her honeymoon pictures, or even turn on microphones and webcams. Thi...

Welcome back, my fledgling hackers! It's been awhile since we did a Metasploit tutorial, and several of you have pleaded with me for more. I couldn't be happier to oblige, as it's my favorite tool. For the next several weeks, I'll intersperse some new guides that'll help expand your Metasploit skills and keep you abreast of new developments in Metasploit, so look for them in the near future.

Welcome back, my fledgling hackers! Nearly every commercial enterprise worth hacking has an intrusion detection system (IDS). These network intrusion detection systems are designed to detect any malicious activity on the network. That means you!