Greetings dear null byters, today we start a new series, we will start to attack users using social networking that are popular such as Facebook, Skype, and much more, and in part 1 of the series will engage users of Skype.
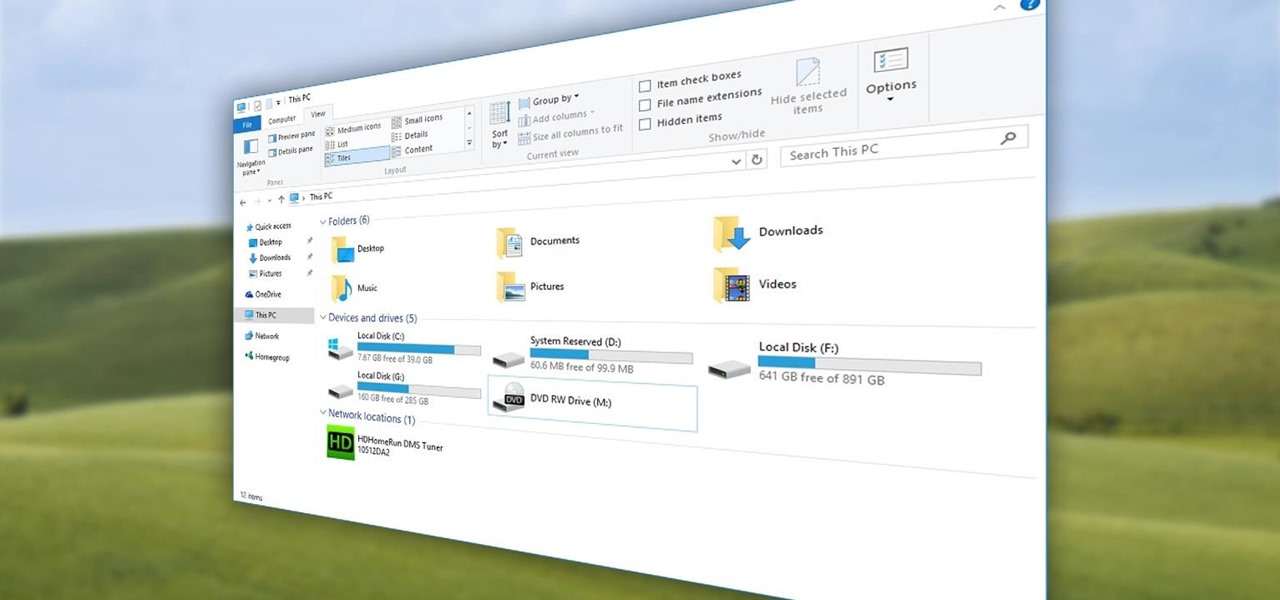
Quite a few things have changed with Windows 10, but one of the more central features that has received a makeover is the old Windows Explorer program, which has been renamed to File Explorer in this version.
If you are among those lucky ones who got a chance to pickup the Yu Yureka from Amazon and looking for a detailed guide on how to root your yureka, then I doubt that there is any better place than this. You might have visited some XDA threads for the same but those are generally brief explanations and you might miss something or the other. Moreover, in most of them, ported Clockworkmod recovery has been used which is less stable and lacks features. So keeping your worries aside, look nowhere ...

Welcome back, my tenderfoot hackers! Hacker newbies have an inordinate fixation on password cracking. They believe that cracking the password is the only way to gain access to the target account and its privileges. If what we really want is access to a system or other resources, sometimes we can get it without a password. Good examples of this are replay attacks and MitM attacks. Neither requires us to have passwords to have access to the user's resources.
If you've ever flashed a custom ROM on any of your devices, one of your main motivations for doing so was likely the set of neat tweaks and extra options that come with something like CyanogenMod. Another deciding factor was probably the fact that most custom ROMs offer a much cleaner interface than manufacturer skins.
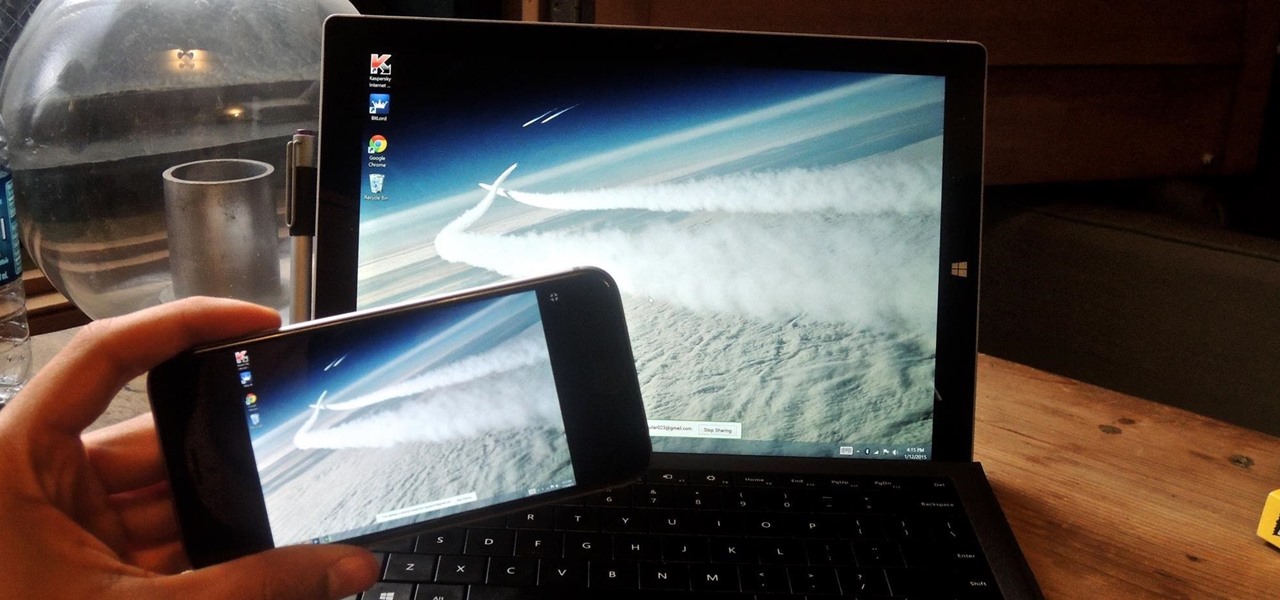
Google's Chrome Remote Desktop, which allows for remote access to your personal computer from your smartphone, has been out for almost a year now. Sadly, it's only been available for Android devices—until now. So, if you got an iPhone (or other iOS device), you can now access and control your computer directly from your smartphone or tablet just like with Android.

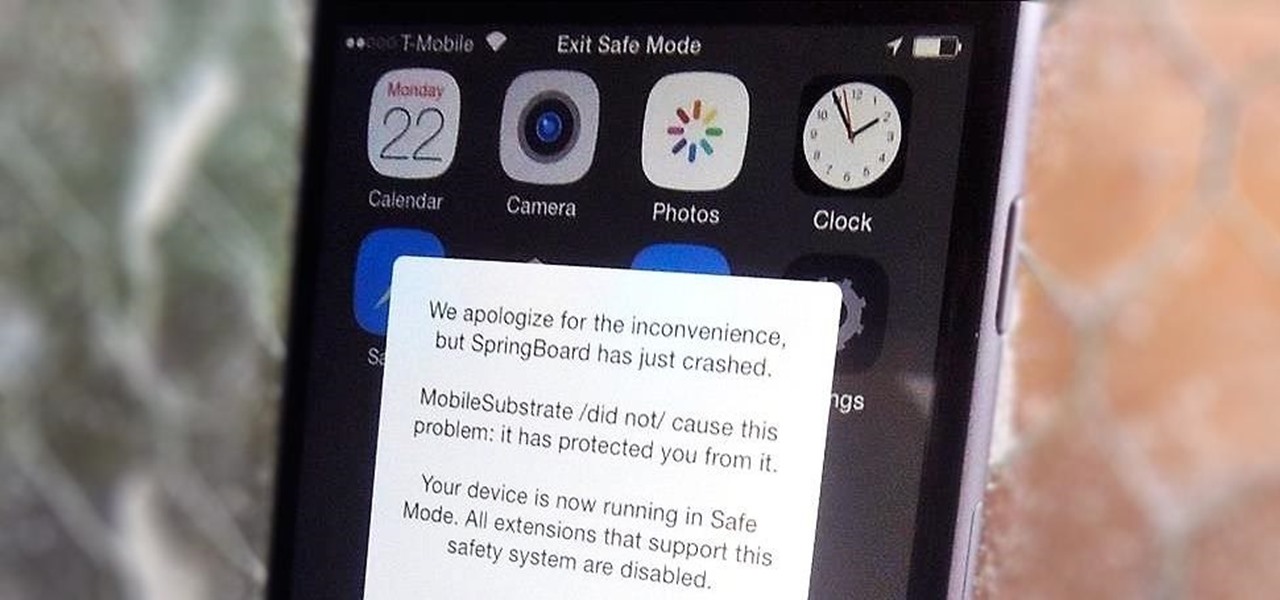
Installing tweaks or themes onto your jailbroken iOS device is a pretty fun and exciting experience, but if you do it for long enough, you're bound to come across a bug that will cause your operating system to crash.

Google's latest Nexus device is big, bold, and beautiful—and now it's got root. Thanks to some quick work by legendary Android developer Chainfire, the Nexus 6 already had a clear-cut root method before most stores even had it in stock.

Lending someone your phone to make a call is always an awkward situation, as you closely monitor them to make sure they stick to a phone call rather than wandering off into private applications like your photo or messaging apps. You don't necessarily want to eavesdrop on their conversation, but trusting people with your phone is difficult, especially if you have some risqué or embarrassing pictures stored on it.

Airports are terrible germ-infested purgatories where people sit around for hours without Wi-Fi while they anxiously await to get wherever they really want to go. Unfortunately, there isn't much we can do about waiting, but this little Wi-Fi hack could help make the waiting a little less boring.

This video will show you how to protect others from accessing saved password on Google Chrome. Saving account passwords in browsers are useful for time saving as well as threatening for malicious activity. This is dangerous for security. So you must protect your accounts detail from others to secure your browsing. Watch the video and follow all the steps carefully.

The newer Graph Search in Facebook can help you find friends in specific cities, photos of a particular subject, restaurants that your friends liked, and a whole lot more. One thing it can't help you with just yet is searching public posts on Facebook, which you could do in the previous search version. Actually, some users do have the option to search public posts with Graph Search, but it's very limited and doesn't include me. If you're like me and don't have access yet, there is a workaroun...

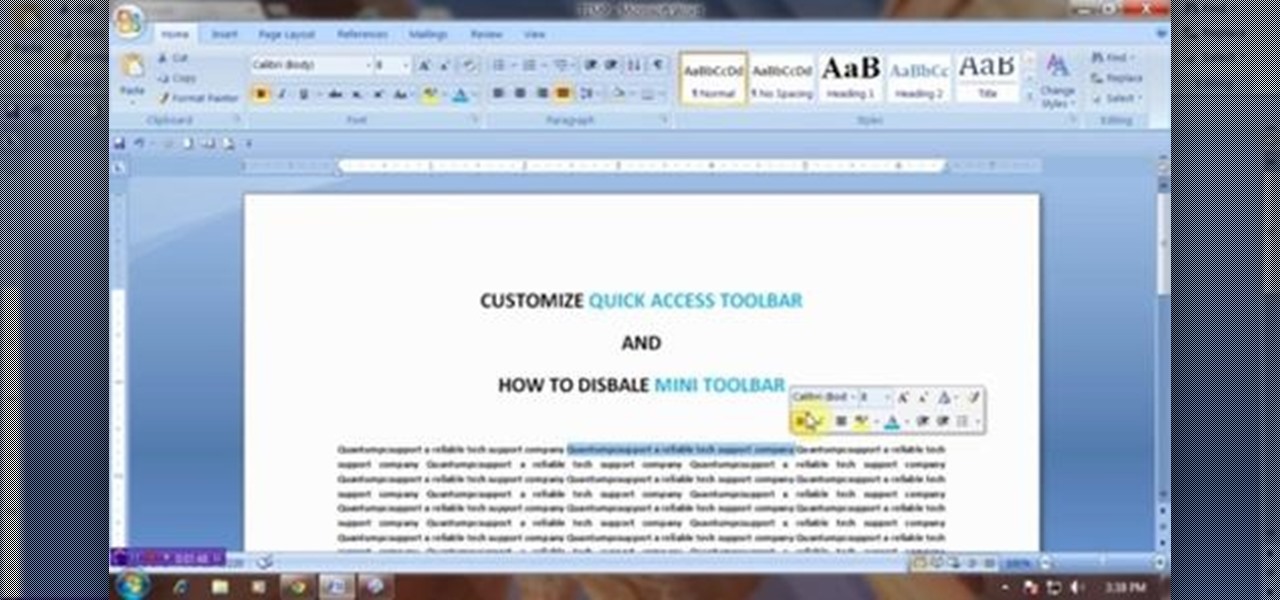
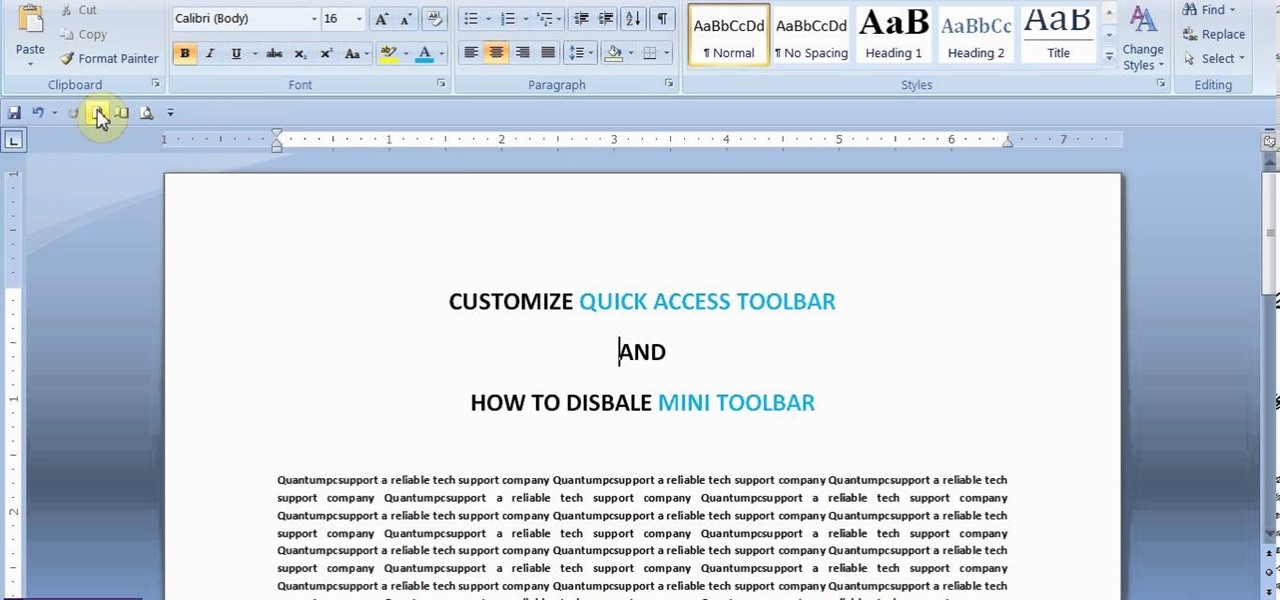
This video will show you how to customize quick access toolbar and delete mini toolbar in MS Word 2007. These 2 things are very useful. Watch the video and follow all the steps to employ it yourself.

With popular remote desktop app LogMeIn recently ending its free service, lots of Android users have begun looking for alternatives. There are some good ones out there like TeamViewer and Microsoft Remote Desktop, but today, Google released an app that makes a pretty good contender.

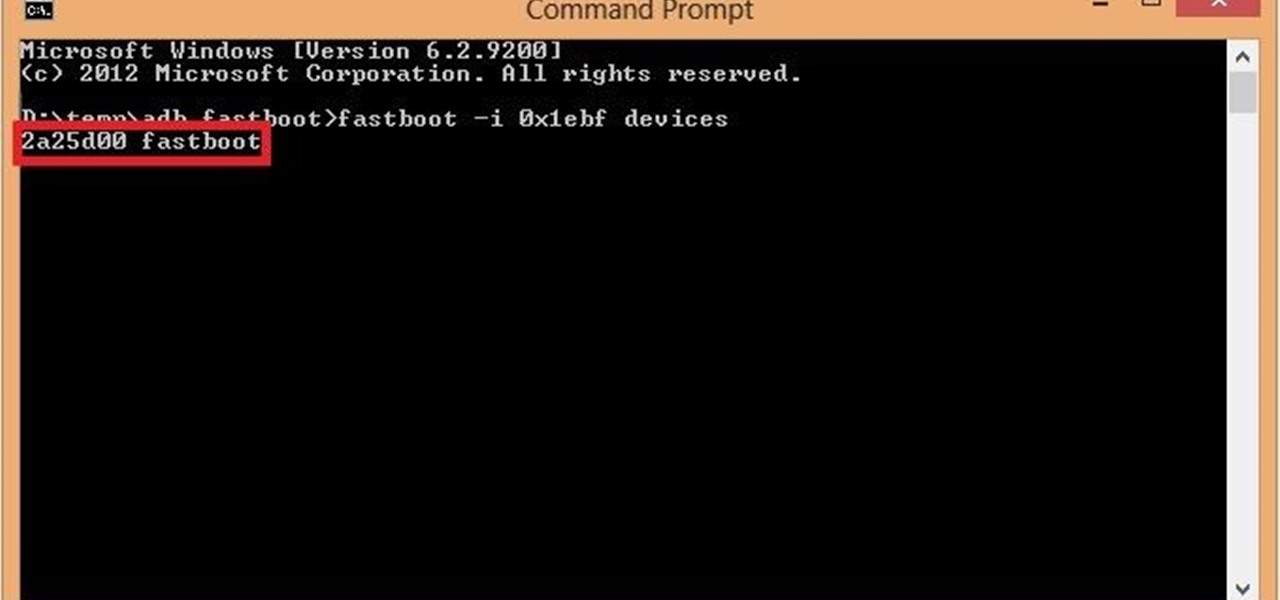
Getting into fastboot or recovery mode on your Android device is nothing new, especially if you're a softModder. Accessing the bootloader menu is the genesis to a lot of mods, and if you're like me and constantly tweak your device, you probably get irritated every time you have to shutdown, then use the power button and volume rockers to access the special menus.

In a world where more features are king, sometimes it's a good thing to breathe, take a step backwards and keep it simple. With home launchers, this isn't often the case, as developers add a galore of features to their apps in order to be at the top of the game.

Ways to Blocking a Website on a PC Open the “Control Panel” by click “My Computer” on your PC

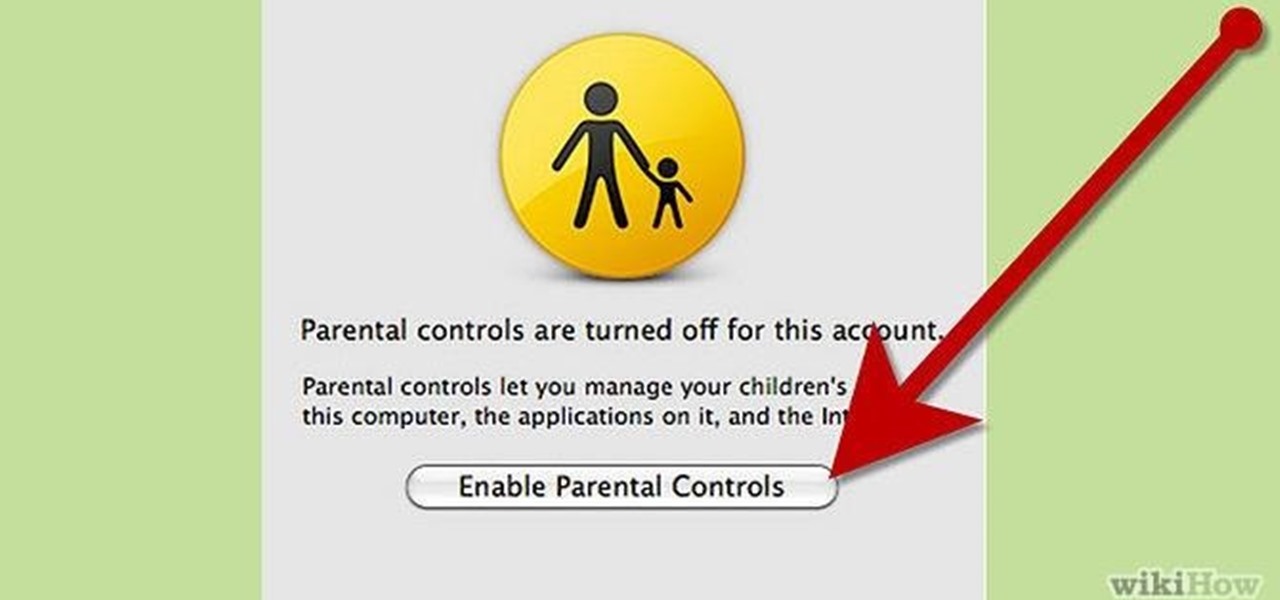
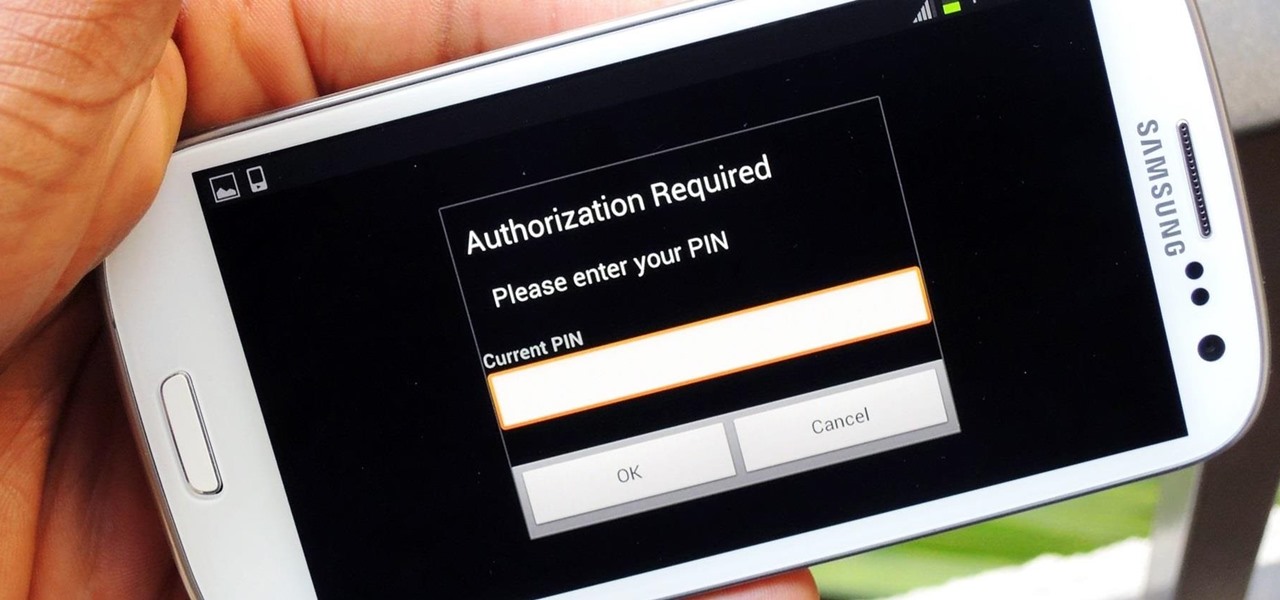
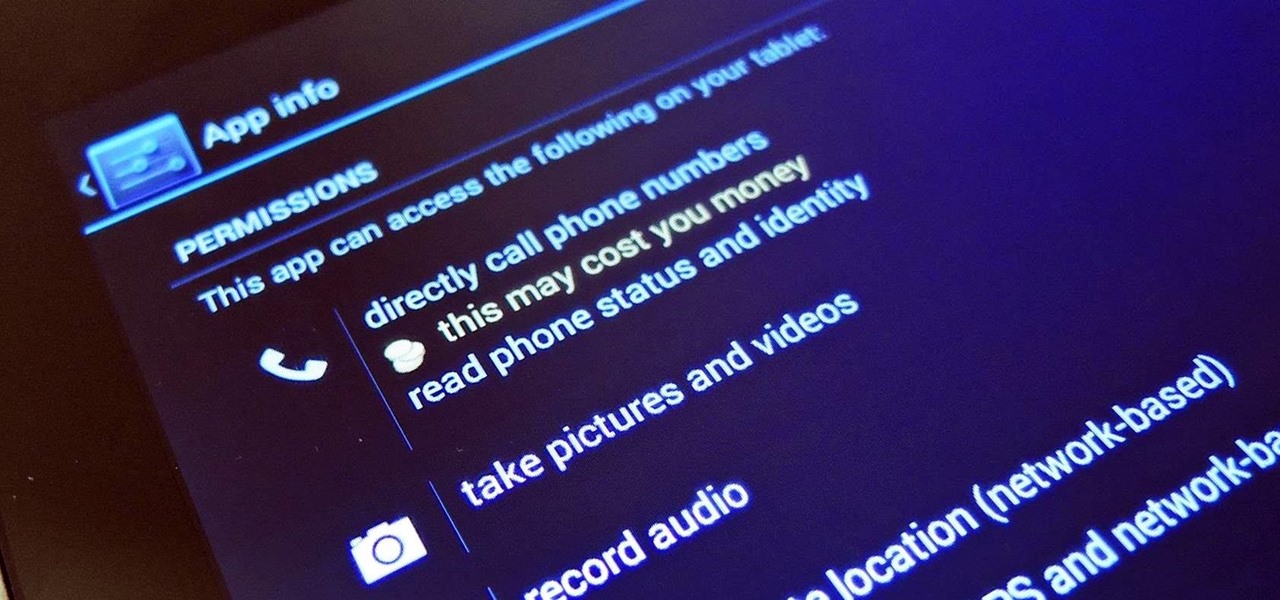
Normally, "restricted access" is something you despise. No one likes to be told they can't do something, especially when it comes to the Internet. Unfortunately, having web access at all times can not only eat away at your wallet, but make your day less productive overall, so some sort of moderation is needed.

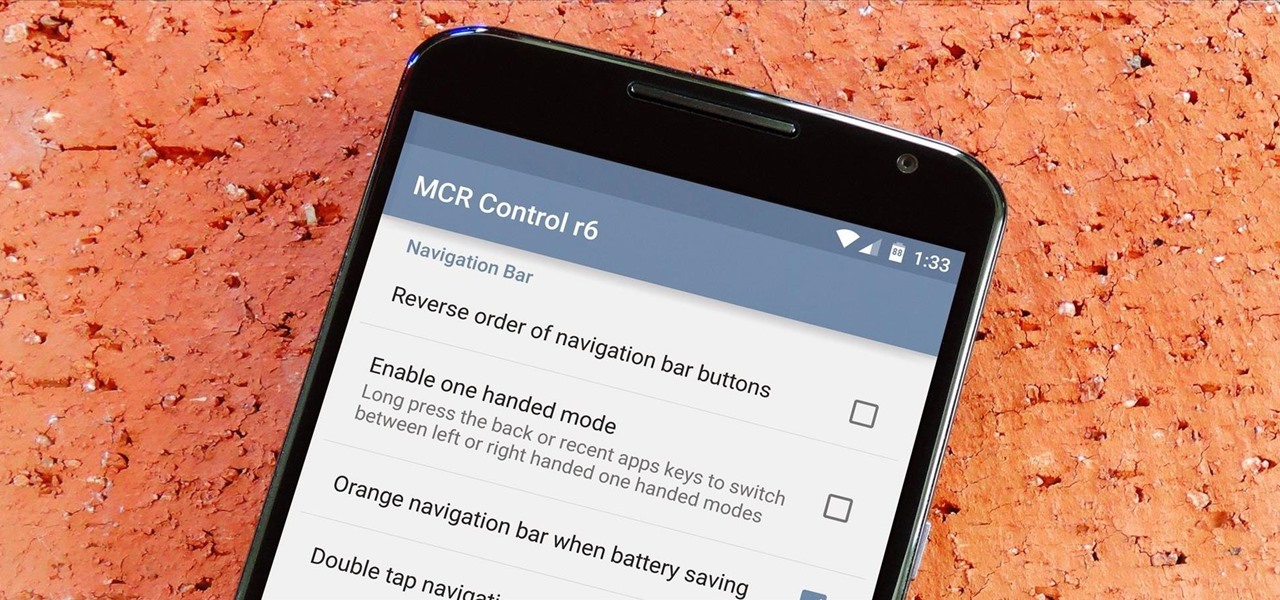
As things begin to clutter on your device, navigating through it can become much more difficult than when you first got it. The sheer number of added apps and mods that build up after time take its toll not only on the quickness and memory of your device, but also on your efficiency to access everything easily.

The dryer’s idler pulley provides tension to the dryer’s drum belt so the belt won’t slip when the drum is turning. It can become faulty over time due to increased friction. If your dryer is making a squeaking or squealing nose then the idler is probably faulty. Replacing this pulley is a simple project. Repair your noisy dryer with this step-by-step tutorial!

Privacy has been a heated topic in recent months, with everyone now up in arms over unauthorized leaks and exposures. And guess what—tablet and smartphone users are just as vulnerable.

Welcome back, my neophyte hackers! As part of my series on Wi-Fi hacking, I want to next look at denial-of-service (DoS) attacks, and DoSing a wireless access point (AP). There are a variety of ways to do this, but in this tutorial we'll be sending repeated deauthentication frames to the AP with aircrack-ng's aireplay. Remember, hacking wireless networks isn't all just cracking Wi-Fi passwords! Our Problem Scenario

Welcome back, my greenhorn hackers! Now that we're familiar with the technologies, terminology, and the aircrack-ng suite, we can finally start hacking Wi-Fi. Our first task will be to creating an evil twin access point. Many new hackers are anxious to crack Wi-Fi passwords to gain some free bandwidth (don't worry, we'll get to that), but there are so many other Wi-Fi hacks that are far more powerful and put so much more at risk than a bit of bandwidth.

This video will show you how to customize Quick Access Toolbar in MS Work. You could add, delete commands and can set the placement of the bar.

Ditching Sense (HTC's stock Android Launcher) is a great way to breathe new stock-like life into your HTC One smartphone without rooting, but even that has its limitations. If you really want the full Google experience, albeit with some extras, CyanogenMod has always been the go-to ROM. In effect, this will give you an experience similar to the Google Nexus or the new HTC One Google Edition.

International, T-Mobile, and Verizon customers all share something in common—their carriers provide unlocked Wi-Fi tethering for free. Of course, you still pay for the data used, but they don't charge you extra simply for using your Samsung Galaxy S4 as a wireless hotspot.

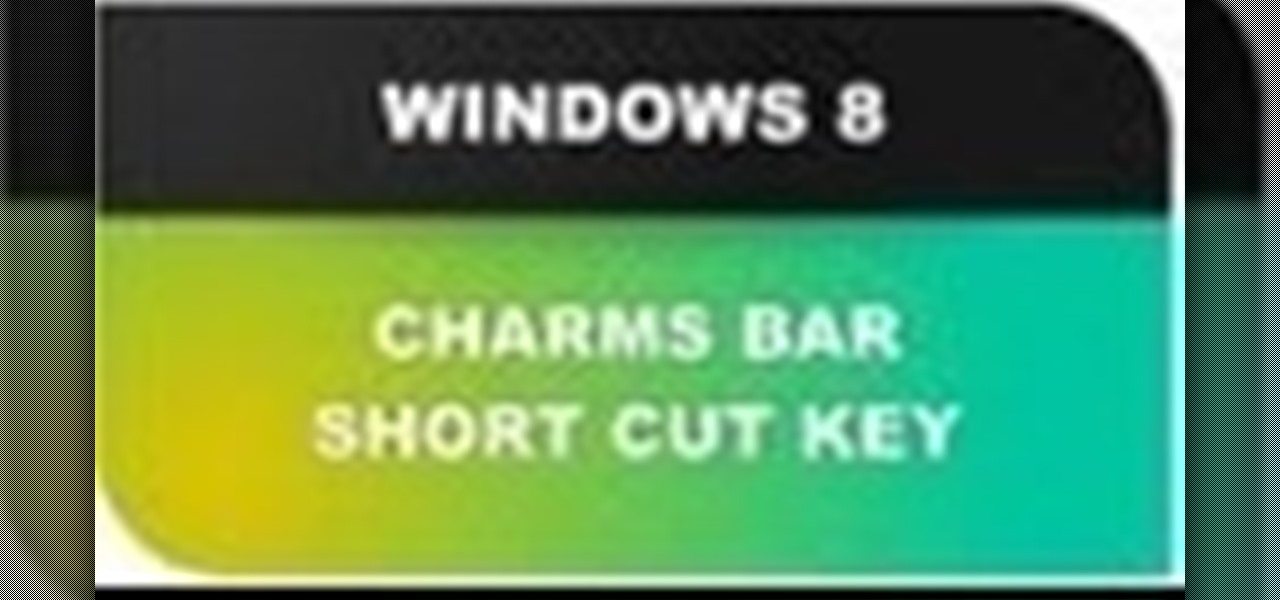
In this Windows 8 Tutorial you will learn how to use the shortcut key for accessing the charms bar in Windows 8. There are a few benefits to this for one the charm bar remains in place even if you don't have your cursor over it also you save yourself time by not having to go all the way to the upper right hand corner of your screen every-time you want to access the windows 8 charms bar.

Having access to your computer from your cell phone is an extremely useful feature. Whether you need to edit documents or send files that are on your home desktop, or you simply want to watch movies you have saved on your computer, access is key.

I know what you're thinking—taking a screenshot is super simple. While that is partly true, taking of a screenshot of the Start Screen in Windows 8 is little bit tricky, unless you're on your Surface.

Spit, or speed, is a fun, fast-paced card game that will have your heart racing nearly as fast as your hands.

Each & Every One of You (EEOOY) is a mock TV show pilot that teaches ordinary people how to make contemporary installation art. If these words strike fear into your heart or make you cringe with memories of seeing contemporary art and wondering what the hell it was all about, this show is for you!

You've got style. You've got class. You've got... No reason to still be wearing a clip-on. Show off your suave side with a perfectly knotted tie. Watch this video to learn how to tie a bow tie.

Learn how to do tube assisted dumbbell curls. Presented by Real Jock Gay Fitness Health & Life. Benefits

Step 1: from the original six step position, kick your left leg to the right side as if you were going to 3step.

WPA-secured wireless networks, or WiFI Protected Access, is a form of internet security that secures your wireless LAN from being accessed by unauthorized users. Safer than WEP, or wireless equivalent privacy, WPA still has weaknesses that are prone to cracking - IF, that is, you know what you're doing.

If you'd like to have access to all your files at home without the hassle of spending money on expensive file hosting services or installing foreign software on your computer that could potentially harm it? Well Google has the answer for you, taking over the world one more computer at a time! In this video you will learn how to use your Gmail account and a Gmail Drive shell Extension to gain access to your files from any computer regardless of location!

In this tutorial, we learn how to open & utilize the trunk area of a 2010 Prius. To access the cargo area, open the rear hatch by pressing on the release above the license plate. To keep items out of sight, there is a sliding cover that you can pull back and hook into slots. To open, pull towards you slightly, then reel it in. There is additional space under the floor which can be accessed by twisting the locks and removing from the vehicle. Underneath this, there is a cargo bin, and undernea...

Google is the biggest and best search engine on Earth, and if you are a webmaster and want your website to be a big success it would really behoove you to know as much about how it works as possible. The Google Webmasters series of videos and website were created to teach webmasters, SEO professionals, and others how Google works by answering their questions and giving them insights into how they can best integrate and utilize Google's functionality to improve their business. This video will ...

Vince shows viewers hot to access the Chuck Norris trick on Google. First, you need to open your web browser and go to Google. In the Google search bar type in 'Find Chuck Norris' and click 'I'm feeling lucky'. Make sure you do not click enter but the 'I'm feeling lucky' button to the right. You will get a funny message that says 'Google will not search for Chuck Norris because it knows you don't find Chuck Norris, he finds you'! The suggestions should read 'Run before he finds you' and 'Try ...

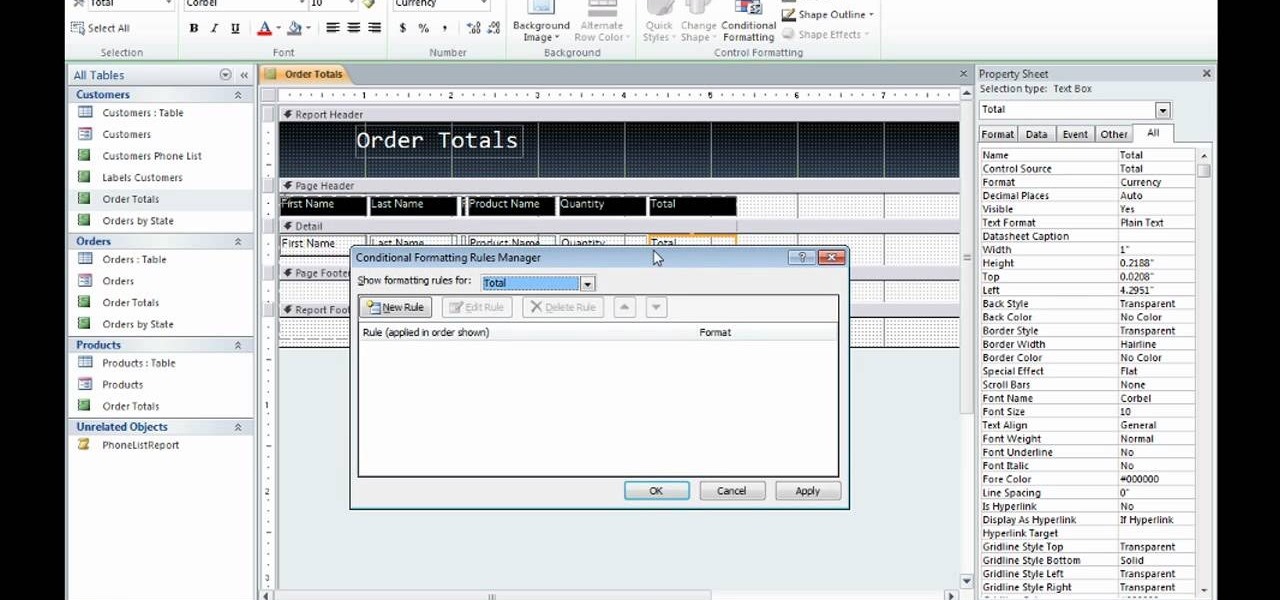
lyndapodcast teaches you how to apply conditional formatting withing Microsoft Access 2010. You click View - Design View. Click the Total tab and you'll notice some highlighted options above. Click Format and then Conditional Formatting. This where you will create rules. Click the new rule button. Now you will see the conditions with drop-down menus. Type in the numbers you want and then select the formatting you want when the rule is true. The preview below will show you how the numbers will...