Need help figuring how to access the system volume information folder on an XP computer? This clip will teach you everything you'll need to know. It's easy! So easy, in fact, that this home-computing how-to from the folks at Britec can present a complete overview of the process in just over five minutes. For more information, including detailed, step-by-step instructions, take a look.

In this Computers & Programming video tutorial you will learn how to use Stock.Xchng to access free stock images. The site is at SXC. Go to this site and you will find a large number of stock images that are free to use. And every day new photos are being added. You can search for an image by category by clicking on the search box and scrolling down to find your category. You can also type in the search box to find a photo of your liking. The image also tells you what is the screen size, prin...

In order to access your wireless router settings in a Windows PC you need to use a command called ipconfig. The purpose of this command is to find out what your IP is. Go into the command console and use ipconfig to find out what it is but instead of noting down the IP address, we actually have to note down the default gateway values for the task at hand. Now all you need to do is open your web browser and insert the default gateway values from before into the address bar. By doing so you wil...
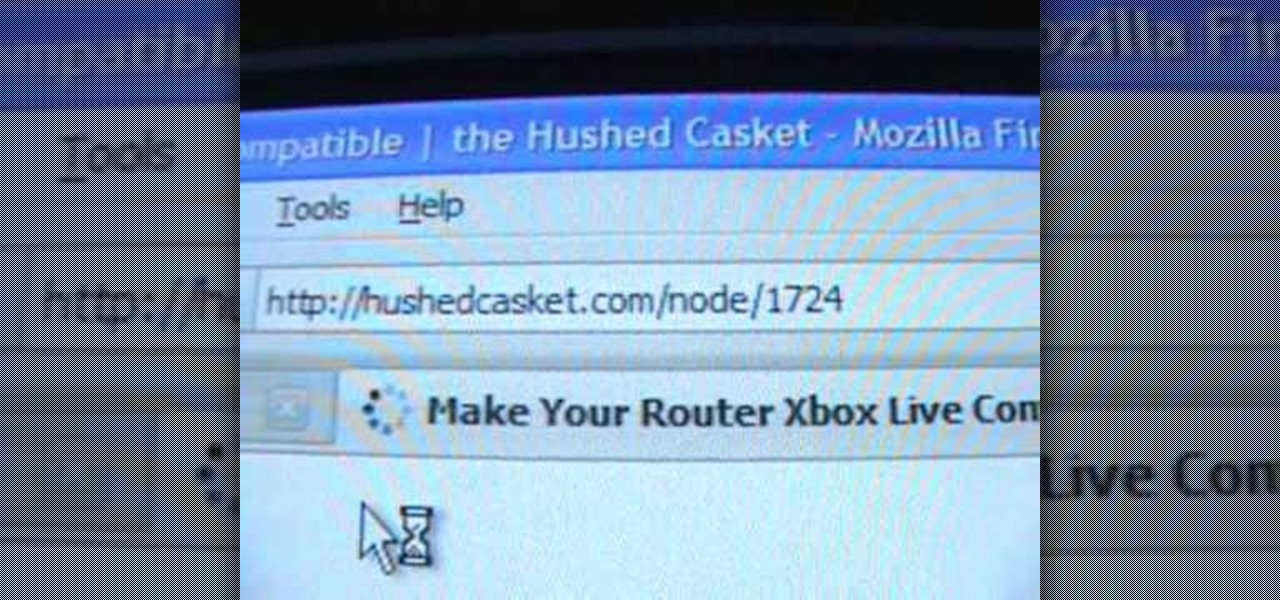
Open your internet browser, type in the address bar 192.168.1.1 and enter your user name and password to access. Look in the right and search for Port Forwarding / Port Triggering. Click on Add Custom Service. Type a name to the service, like XBox Live, now access HushedCasket and scroll down to see the ports you need to open. Go back to the setting and select UDP in Service Type. Put 88 in Starting Port and Ending Port. Go to your XBox and enter in System Settings, go down to Network Setting...

Removing a vehicle's tires and inspecting the brake rotors is possible with a few easy steps. First, remove all five lug nuts and remove the wheel from the vehicle. A power tool will easily remove the lug nuts. You now have access to the wheel so the next order of business is to lift off the wheel. Once the wheel is off the vehicle and safely set aside, return to the vehicle. You now have access to the brake pad. The final step in the process is to inspect the brake pad for thickness and abno...
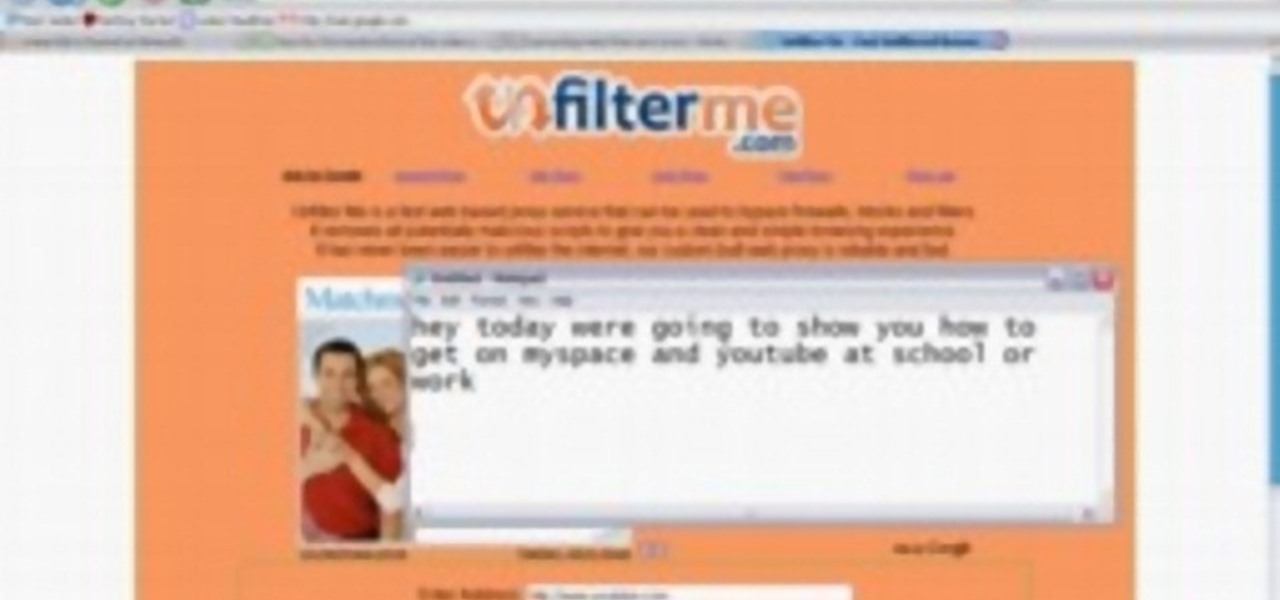
This video shows you how to easily access blocked website like MySpace or YouTube at school. The first thing you have to do is open the web browser and surf to Unfilter Me . Then, type your desired web site URL in the "Enter Address" field. Hit the "Start Browsing" button and wait for the site to load. Note that the URL in the address bar is different. This is the easiest way to access blocked websites at school. That's it! Good Luck!

This how-to video is about how to use command prompt to view the blocked websites at school. This step by step instruction will help one to open the blocked websites at school.

You can get an expensive ticket for driving with a busted tail light. But that's not all. Driving with a faulty brake light can be dangerous. Replacing the bulb is a simple task that takes only a few minutes.

Researching genealogy takes a little enterprise and the skills of a master sleuth.. Watch this video to learn how to research your genealogy and family tree.

You can't get the same gaming experience on your iPhone as you would on a PlayStation 5, Xbox Series X, or gaming computer. The processing power is less, the controls inadequate, and there are many on-screen distractions, all of which make mobile gaming less enjoyable. While you can't fix many of these issues, there is a way to prevent some problems, and that's thanks to Guided Access.

Now that more people are working from home on unsecured networks and personal devices, hackers are having a field day accessing everything from private browsing histories to personal banking information. A virtual private network (VPN) is the first and most important line of defense when it comes to protecting all of your devices from digital intrusions, but not all VPNs are created equal.

Third-party apps on your iPhone must ask for your permission to access your library in the Music app. Some will even want to get access to your Apple Music account. If you no longer use the apps, you shouldn't be letting them have access anymore. It's easy to hunt them down, and doing so might even show some apps you can't even remember giving any permissions to.

SEO is the name of the game. If you want your business or brand to succeed, ranking on the front page of Google is a boon. Getting to the front page of search engines takes work, but it's not impossible when you master SEO best practices.

Your Galaxy's lock screen already lets you know there's no SIM card installed if it's missing on your device, so there's really no need to have a persistent icon for it on the status bar. If you want to hide the pesky symbol and accompanying notification for good, there's a nifty app you need to check out right now.

Without admin privileges, installing additional software, or modifying the Windows 10 firewall, an attacker can alter a router and perform a variety of exploits. It's accomplished by forwarding requests from Kali through a backdoored Windows computer to the router gateway with simple SSH tunnels.

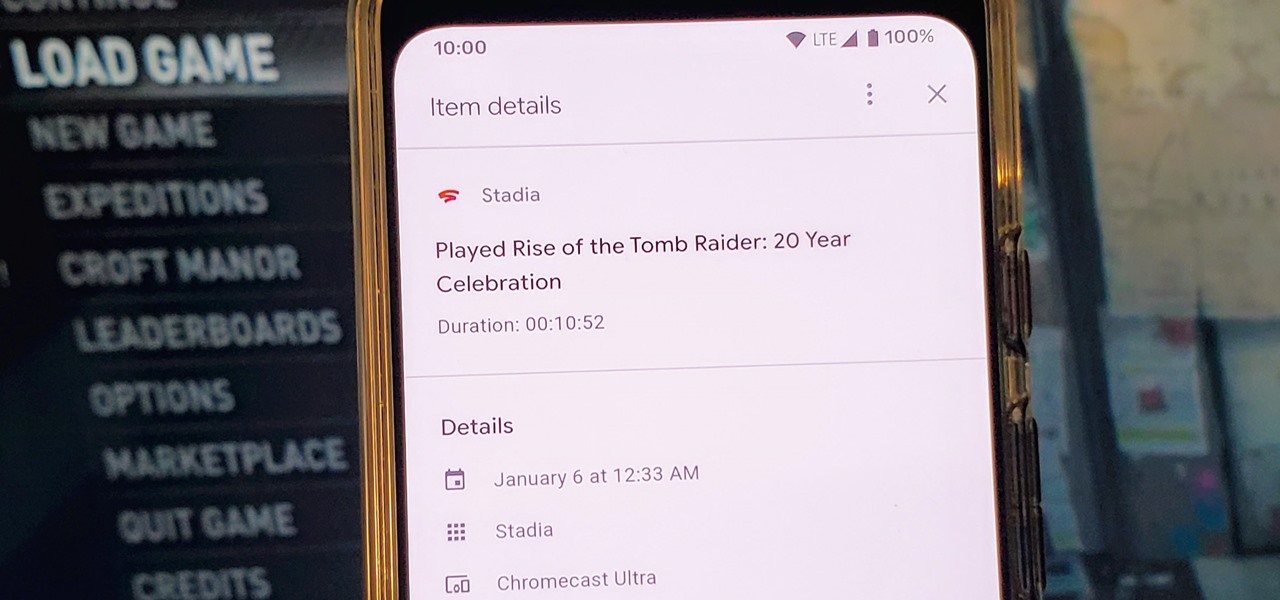
Since Stadia is an early access game streaming platform, Google is still working on bringing big things to the table. You can expect wireless Stadia controller support for many more devices, high-quality 4K gaming on all Chrome web browsers, and more Google Assistant features. They also managed to silently sneak in a way to keep track of your Stadia gaming sessions too, which is pretty handy.

As we predicted this time last year, Magic Leap is finally moving from consumer entertainment hype to making a firm commitment to enterprise customers.

While MacOS computers have been spared from some of the most famous malware attacks, there is no shortage of malicious programs written for them. To keep your computer safe from some of the most common types of malware, we'll check out two free tools. These tools can automatically detect ransomware encrypting your files and watch for unauthorized access to your microphone and camera.

Apple has seemingly always made it a priority to show how much it cares about user security and privacy — enough that it has a page dedicated to it, proclaiming that "privacy is a fundamental human right." It's true that there are few issues more important than user privacy when it comes to technology, and Apple only makes things better in iOS 13.

It's been proven that hackers can manipulate your screen with fake taps through specific exploits, so they can potentially hit the "Grant" button when you get a superuser request. This is the last thing you'd want to happen since the malicious app from that point forward has full system privileges. Luckily, using a fingerprint to lock your superuser requests can prevent this.

Android 10 goes all-in on gesture navigation. Unlike Android 9, all three buttons which made up the navigation bar are replaced with gestures, with the biggest change being the back button. The problem is this same gesture is already used within apps to access the side menu, so in Android Q, this has been changed.

Call Screen is one of best features on Pixel phones. With one button, you can screen calls using Google Assistant and avoid pesky spam callers. However, after the call, there is seemingly no way to access the transcripts for future review. Fortunately, there is a way, but it is tucked away.

On Thursday, Mojo Vision, a startup comprised of former engineers from Apple, Amazon, Google, and other Silicon Valley mainstays, emerged from stealth backed by $50 million in funding for a hands-free augmented reality platform that runs without smartphones, tablets, or other devices.

Perhaps you've thought about rooting your OnePlus 5, but thought again when you heard SafetyNet would prevent you from using apps like Google Pay, Pokémon GO, or Netflix. Those are valid struggles when you root using traditional methods. There are no such worries when using Magisk, as it masks the fact that your device has been modified.

If you're on iOS 11.4.1 or iOS 12 and go more than an hour without unlocking your iPhone, an "Unlock iPhone to Use Accessories" message will appear whenever you connect your iPhone to a computer or other device that tries to use the Lightning cable's data lines. This is to protect you, but it can be annoying if you have no reason to believe that law enforcement or criminals will have access to your iPhone.

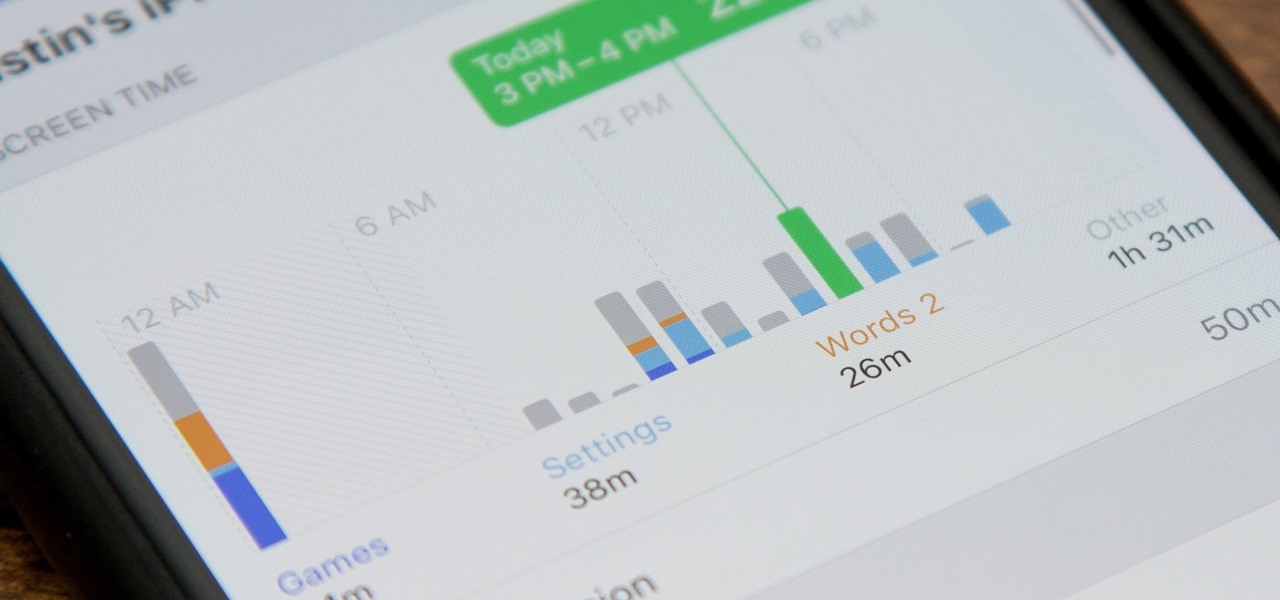
Apple's digital health initiative in iOS 12 includes Screen Time, a settings menu that shows you how much time you spend playing games, reading news, and whatever else it is you do. This menu also lets you schedule downtime away from your iPhone, set time limits for your apps, and more. While this is all great, it's hidden inside the Settings app — but there's a faster way to access this data.

Uber as a service is great, but using it requires you to hand over your location data to the company. What's worse is that you may be giving them precious access to your GPS even when don't have the Uber app open. This is both a major privacy issue and a drain on your battery. Fortunately, some of you can fix this.

HTC is entering the augmented reality market through the back door by giving developers access to the stereo front-facing cameras on the Vive and Vive Pro VR headsets.

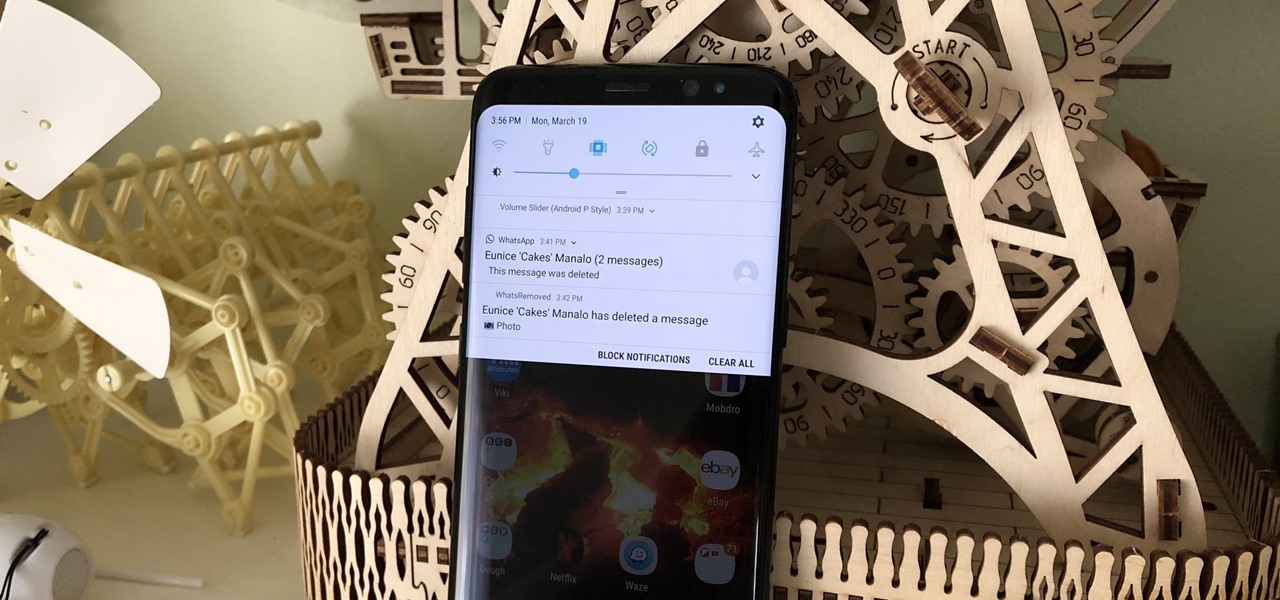
To help keep potential drama at bay, WhatsApp lets you delete questionable messages before the other person even sees them. If you're on the receiving end and you're curious about the deleted text, however, there's an Android app that lets you view erased messages.

Snap Inc.'s dedication to augmented reality has expanded the world lenses in Snapchat to our own Bitmojis. While it's great to see our characters interacting with real environments, we haven't seen them connect to other Bitmoji in AR space. That all changes with "3D Friendmojis," a lens from Snapchat that lets you stage scenes between your Bitmoji and a friend's.

Apple has tools built into iOS to help parents monitor the iPhone habits of their children. However, those same tools can be used by everyday iPhone owners to both hide apps they don't care about, as well as restrict features they don't need or that infringe on privacy. Whether you fit into one category or the other, all iPhone users can benefit from the "Restrictions" feature.

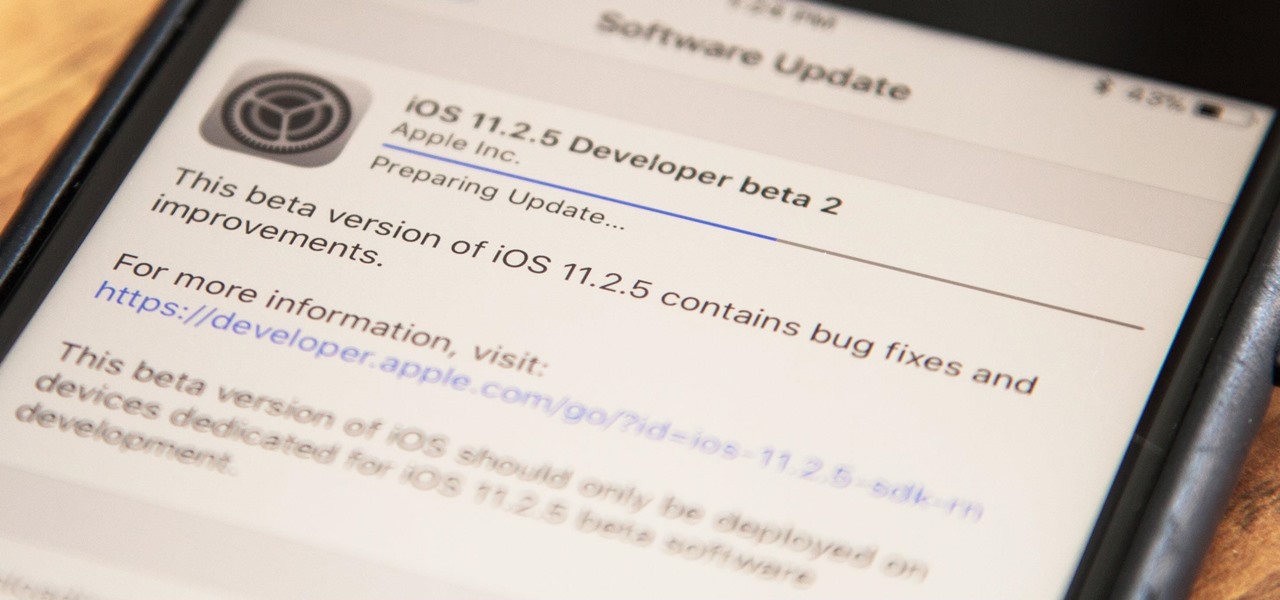
Apple has released the second beta for iOS version 11.2.5 for developers on Dec. 19. The update comes six days after the release of the first 11.2.5 beta which updated the Music app to include a persistent "play bar" at the bottom of the window, along with some bug fixes. Public beta testers received the update on Dec. 20.

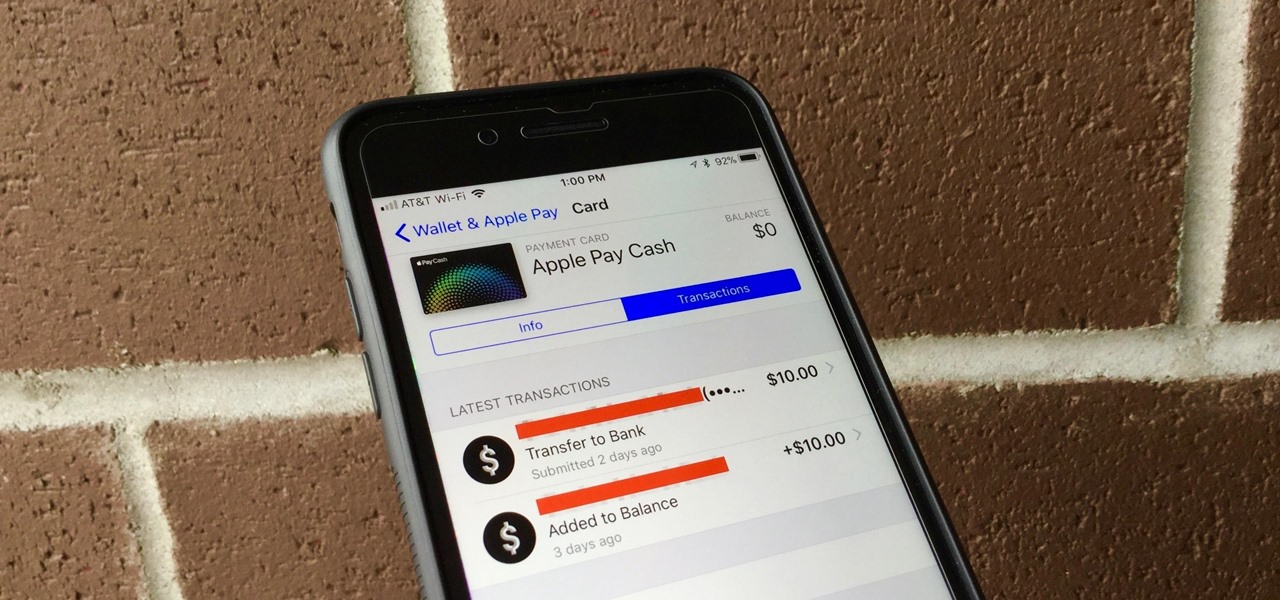
With Apple Pay Cash, sending and receiving money with fellow Apple users has never been easier. One big plus about Apple's new Apple Pay Cash card is that all of your transactions are available just a few taps away, so you can see all your person-to-person payments, balance additions, and bank transfers.

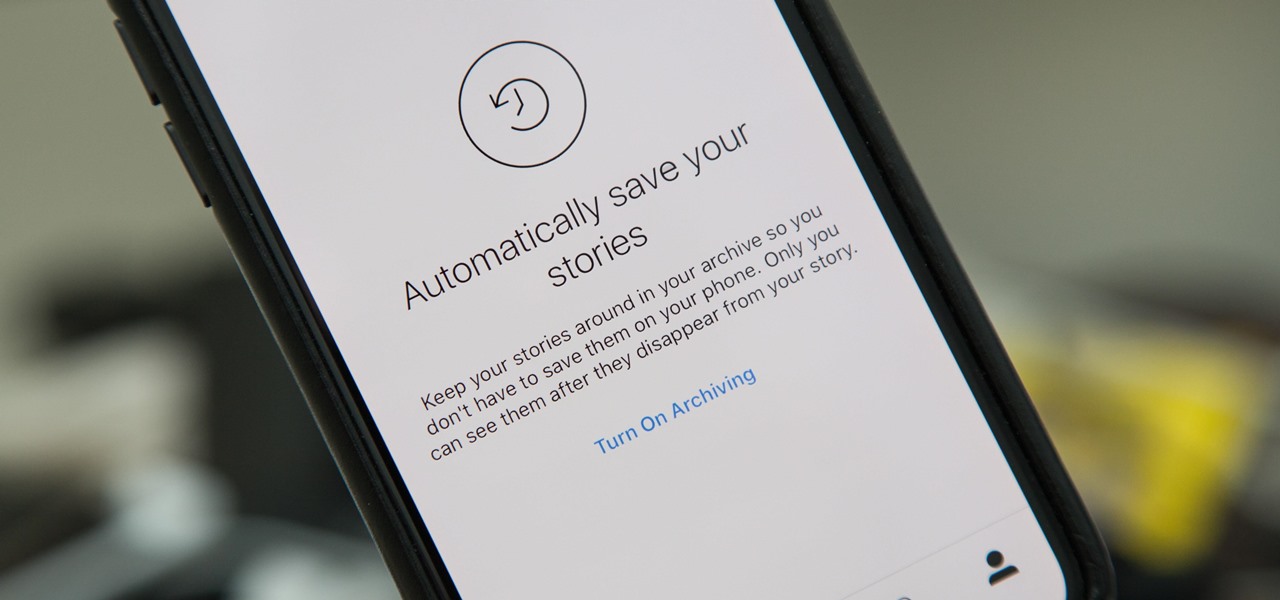
If you're familiar with Instagram Stories, you know that you can download your story to your iPhone or Android device for offline viewing. Those downloaded stories can easily get lost, and Instagram is finally doing something to keep that from happening with a new archive option for stories, similar to the regular posts archive.

There's a new macOS vulnerability that hackers within physical reach of your computer can use to gain root access to your system and accounts. Just by using "root" as the username and a blank password on a privilege escalation prompt, someone can install malware on your computer, access hidden files, reset your passwords, and more. Root access gives them the ability to do anything they want.

Introduced along with the iPhone X, Animoji are animated characters, mostly animals, that are rendered from the user's facial expressions using the device's TrueDepth camera system to track the user's facial movements.

Spotty cellular reception is a fact of life that we all have to deal with, especially when you're traveling. For those of us who rely on our smartphones for navigation, driving through areas with bad mobile data service can be a cause for major headaches.

I've possibly been really out of it for a long time not to have realized that Instagram has a bunch of hidden filters. Clarendon seems to be by number one filter for pics and videos, but maybe that's exactly what I've been doing wrong.

A recently confirmed polio outbreak in Syria is connected to low levels of vaccination, worsened by conflict. It is the first confirmed incidence of polio in Syria since 2014. Before 2013, the last case of polio in Syria was in 1999.

3D Touch is only available on the 6s and 7 series iPhones right now, and likely future models, so those with older devices are missing out on all the cool "Quick Actions" available for app and settings icons. But the new iOS 11 is finally bringing some of those helpful shortcuts to iPhones without 3D Touch built in.