Welcome back, my tenderfoot hackers! In this series, we are exploring the myriad of ways to hack web applications. As you know, web applications are those apps that run the websites of everything from your next door neighbor, to the all-powerful financial institutions that run the world. Each of these applications is vulnerable to attack, but not all in the same way.

Welcome back, my rookie hackers! So many readers come to Null Byte to learn how to hack Wi-Fi networks (this is the most popular hacking area on Null Byte) that I thought I should write a "how-to" on selecting a good Wi-Fi hacking strategy.

Google I/O is like Christmas for Android enthusiasts. Every year, this conference showcases new and upcoming features for the world's leading mobile operating system, and this year's was no different. Shortly after announcing Android M, Google released a preview version of the upcoming firmware for Nexus devices.

In my last guide, I showed how you could crack the combination of any Master Lock combination padlock in 8 tries or less using my online calculator. Now, as promised, I'll be showing you how I devised the attack, which is based off the well-known technique that reduces the 64,000 possible combinations of a Master Lock down to just 100. Here, I will be drilling open a Master combo lock to show you how the insides work.

Welcome back, my aspiring hackers! Although this article may have been better placed first in this series, I doubt that anyone would have read it when just starting out studying Linux. Now, that you are well into your Linux studies and have some familiarity with how it operates, I'd like to take this moment to explain the philosophy around the Linux operating system.

When a stuffy nose hits, it feels like breathing clearly and easily may never come again. Allergies, colds, and even changes in weather can leave our sinuses blocked, with medicine seeming like the only option. But don't break out the medication just yet — relieving the pressure of a stuffy nose, a stuffy head, and stuffy ears can be as easy as touching a pressure point.

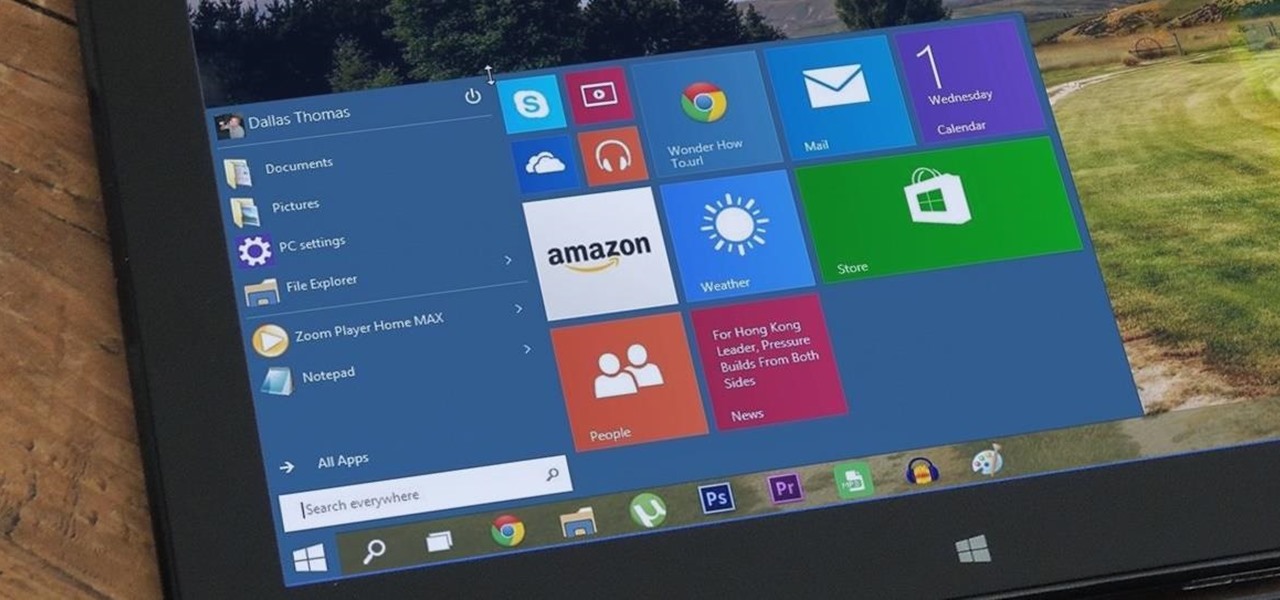
At a closed-door presentation on September 30th, 2014, Microsoft unveiled the latest iteration of its industry-leading operating system. Dubbed Windows 10 (seems as if Redmond isn't too fond of the "9" moniker), this new version brings along with it many UI optimizations and under-the-hood tweaks. With a particular focus on optimizing the interface for traditional mouse and keyboard computers, one of the most noticeable changes is the return of the Start Menu. While touch-optimized devices wi...

Welcome back, my budding hackers. So many of you are interested in hacking Wi-Fi that I have decided to revisit my Wi-Fi Hacking series with some updated and more in-depth material. I strongly suggest that you look at some of my earlier posts, such as "Getting Started with Terms and Technologies" and "Getting Started with the Aircrack-ng Suite of Wi-Fi Hacking Tools," before continuing here. If you're ready, you can also check out our updated 2017 buying guide here.

If you've already read the first part exploring what geniuses actually eat as opposed to what the rest of us are told to eat for brain health, you've noticed that there are some big discrepancies. Instead of favoring healthy, wholesome foods high in antioxidants, lots of high-achieving types tend to go for caffeine, sugar, and processed foods. One notable health habit practiced by many: eating breakfast.

As we near the one-year anniversary of its release (and the inevitable unveiling of its successor), the Samsung Galaxy Note 3 remains a device that packs quite a punch when it comes to hardware. It boasts a 2.3Ghz CPU and was the first mobile phone ever to house 3GBs of RAM. Suffice it to say, it can handle any software you throw at it with no discernible lag. Even Samsung's notoriously bloated TouchWiz ROM seems lightning fast.

MacBooks are built for creation and creativity. They're built to withstand our careers, our hobbies, and our everyday use. I use mine every day, and there's nothing I'd recommend more for computing needs.

You know what's awesome? You own a Nexus. That means, with Google's blessing, you have easier access and control over your device than other manufacturers allow. You can really dig in and do some interesting things if you root.

It's rare that a developer listens to the wishes of the masses, but that's exactly what CyanogenMod has done with their new CyanogenMod Installer, which automates the entire ROM installation process on your HTC One or other Android device. Previously, upgrading from the stock HTC One ROM to CyanogenMod required an unlocked bootloader, a custom recovery, the latest CM version, and Gapps. Let's be honest—unlocking the bootloader is a pain the ass, and probably the only reason stopping most peop...

Welcome back, my novice hackers! My recent tutorials have been focused upon ways to NOT get caught. Some people call this anti-forensics—the ability to not leave evidence that can be tracked to you or your hack by the system administrator or law enforcement.

War leaves a lot of stuff behind. Torn families, delegitimized institutions, mass graves, and unexploded ordinances litter the post occupation landscape. Whether or not you have driven the imperialist out, or are still in the phase of armed resistance, you will need the ability to safely diffuse bombs. My bomb defusing Silvia-bot can do it all. She can catch grasshoppers, cut wires, collect samples, tase enemies and even play chess! Materials

There are many ways to access the Google Assistant on your phone, but Android 12 adds another one for Google Pixel models that may be the best way yet.

Have you ever had a great meal at your local restaurant and wondered how to make it yourself? Or perhaps you've found yourself stumped at what to make for dinner based on the random provisions in your kitchen? Now, you can discover solutions to these food-based problems via Snapchat's computer vision wizardry.

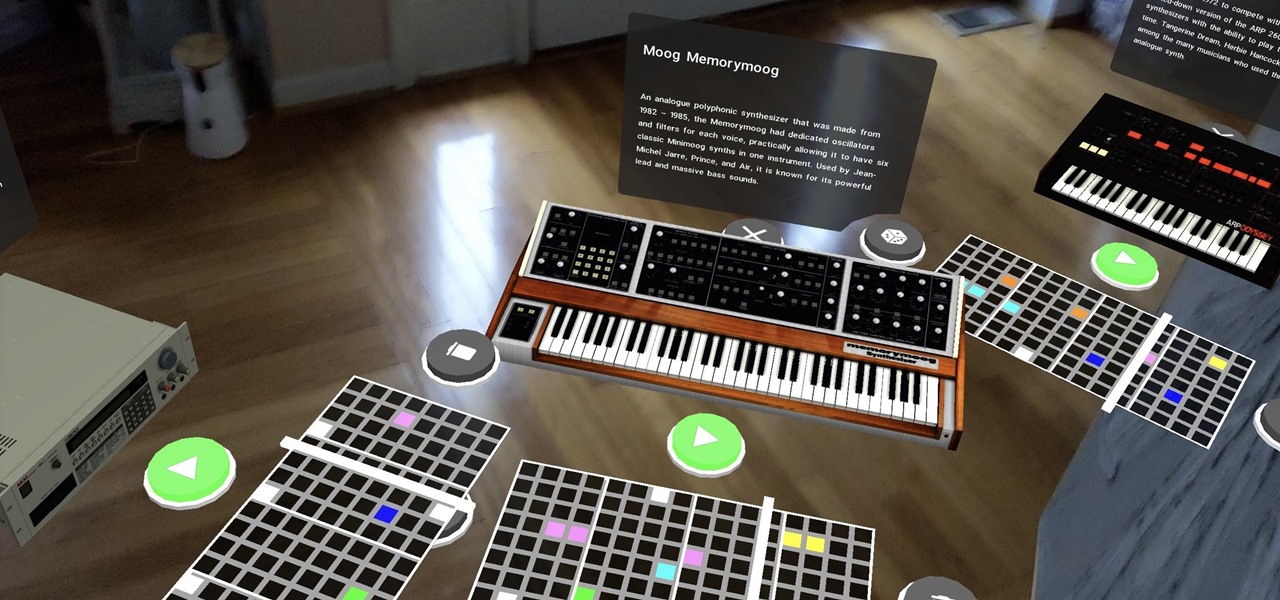
Museum curators typically frown upon visitors touching paintings, sculptures, and artifacts, but not when those exhibits are displayed in augmented reality.

If you use iCloud Photos, Apple's iCloud link feature is meant to make sharing multiple photos and videos faster and easier, but it's not as great as you might think. Luckily, there's a way to stop your iPhone from creating them automatically, as long as you're running iOS 13 or later.

We are now in the age of 5G. Carriers worldwide are upgrading their networks to the newest standard for mobile, which will dramatically improve your phone experience. How? By giving it download speeds and latency that surpass Wi-Fi. But before you upgrade, there are few things you should know first.

With protests springing up across America, there's a chance you may have your first interaction with law enforcement. Many demonstrators will have their phones in-hand to film the action, which, sadly, could prompt an officer to demand the device and any self-incriminating data it may contain. Before this happens, you should know there are tools at your disposal to protect your data in such situations.

Despite the fact that over 600,000 Snap Lens filters have been created since Lens Studio debuted in 2017, and Facebook is reporting that more than a billion users have interacted with its Spark AR filters across Facebook properties, social augmented reality filters get a bad rap in the AR industry.

You watched the live stream, pored over the specs, and are now super excited for the Google Pixel 4. But specs don't tell you everything. After using the Pixel 4 XL for over a week now, we've found several things you wouldn't know without getting your hands on the phone.

It is a great time to be a mobile gamer. Not only are there millions of mobile games on the Play Store and App Store, but thanks to some recent developments, we can also even play PC games. AMD recently released an app, which, among other things, lets you play your favorite PC games on your phone.

You can almost detect the collective breath-holding of the augmented reality industry as it waits for Apple's inevitable entry. A new Apple wearable built with augmented reality technology is likely the device that will finally make the smartphone take a backseat.

Giving up your Wi-Fi password can be giving up more control than you think. Because of the way Chromecast and other IoT devices communicate, anyone on the same Wi-Fi network as your device can often make it do whatever they want. With a script called "Cast All the Things," we can hijack a Chromecast to play nearly any kind of media with a single command in terminal.

If you've ever spent any serious time examining the Chinese tech startup world, you know that it moves fast — very fast. The tech startups hailing from Beijing and Shenzhen are moving so fast that they're now in serious competition with Silicon Valley.

After months of waiting, it looks like HMD has finally answered the call. Nokia's parent company is finally releasing a true flagship phone — one that isn't just an enhanced version of a previous phone and actually brings something new to the table. That phone is the Nokia 9 PureView.

With just a few taps, an Android phone can be weaponized into a covert hacking device capable of running tools such as Nmap, Nikto, and Netcat — all without rooting the device.

Rooting usually means sacrifice. With most root methods, you lose access to apps like Netflix and Android Pay when SafetyNet gets tripped. More importantly, you lose the ability to accept OTA updates, forcing you to manually flash new Android versions. But there's a way around all of this if you root the right way.

Net neutrality is dead and your internet service providers can collect all the data they want. While VPNs are a great way to protect some of that privacy, they're not perfect. There is another option, though, called Noisy, which was created by Itay Hury. It floods your ISP with so much random HTTP/DNS noise that your data is useless to anyone even if they do get it.

Leaked databases get passed around the internet and no one seems to notice. We've become desensitized to the data breaches that occur on a daily basis because it happens so frequently. Join me as I illustrate why reusing passwords across multiple websites is a truly awful practice — and compromise hundreds of social media accounts in the process.

Don't think because your MacBook is using FileVault disk encryption your device is secure or immune to hackers. Here's how to find out if that FileVault password is strong enough to withstand an attack from a motivated attacker.

Developed by Open Whisper Systems, Signal is a free, open-source encrypted communications app for both mobile and desktop devices that allows users to make voice calls, send instant messages, and even make video calls securely. However, a vulnerability was recently discovered for the desktop version that can be turned into a USB Rubber Ducky payload to steal signal messages with a single click.

Google's Pixel phones claimed the top spot in our ranking of the best phones for rooting, but they do have one drawback from a modder's perspective: Because of their A/B partition layout for seamless updates, the devices don't have official support for Magisk. Thankfully, though, developer goodwin has stepped in with a fix, so we can now get Magisk working on the Pixel and Pixel XL.

Architects are natural candidates to be early adopters of mixed reality. Their trade consists of not only designing buildings and spaces, but also presenting those designs to clients, who then decide that their vision is worth spending thousands (if not millions or billions) of dollars to build in reality.

Being part of the wild frontier is amazing. It doesn't take much to blow minds of first time mixed reality users — merely placing a canned hologram in the room is enough. However, once that childlike wonder fades, we need to add more substance to create lasting impressions.

Typing on a mobile device has come a long way since the days of flip phones. Today, there are awesome keyboard apps like Gboard, which integrates Google search features and makes typing a breeze. But the whole experience still stands to improve if you take some time to learn a few useful tips.

With tools such as Reaver becoming less viable options for pen-testers as ISPs replace vulnerable routers, there become fewer certainties about which tools will work against a particular target. If you don't have time to crack the WPA password or it's unusually strong, it can be hard to figure out your next step. Luckily, nearly all systems have one common vulnerability you can count on — users!