Calling all crochet-loving beginners! In this two part video tutorial, learn how to make the single crochet stitch and the first row of a sampler scarf, as well as the second row of a sampler scarf. Steps are gone over step-by-step for those of you who are beginners. Good luck with your start!

In this tutorial, we learn how to crochet a round shell Catherine's Wheel left-handed. For the first round you will start by doing four single crochets after the slip stitch. After this, do seven double crochets, then a single crochet followed by seven more double crochets. Make two more chain stitches, then a single crochet and three double crochets. After this, start the next row which will be a chain stitch, then three double crochets. Next, you will do seven double crochets, followed by a...

Learn how to focus on a single mix when on the decks. While DJing might appear simple to the untrained eye, truly mastering the turntables requires as much time and dedication as mastering any other instrument. Fortunately, the internet is awash in free video DJing lessons like this one, which make the learning process easier than it's ever been. For more information, including detailed, step-by-step instructions, take a look.

Donna teaches how to do a front-post, back-post crochet stitch. First of all you'll need yarn and a hook. Start with a single crochet. Donna uses white to create the single crochet and to create a heart, goes over the single line with pink to create a double crochet. To create the double line, go around and through. from front to back, through the single post. Always have the yarn going through the same side. The basic method using the pink, is to make the design in a "V" shape. Using this me...

The Cheshire Cat isn't like other famous cartoon cats: he's brilliantly purple and hot pink, ever smiling and entirely unnatural. However, he makes for a perfect Halloween costume, with his bright, neon appearance and mysterious nature.

As was mentioned by the great OTW last week, TOR, aka The Onion Router, has had its integrity attacked by the NSA. In an attempt to reduce the anonymity granted by the service, the NSA has opened a great many nodes of their own. The purpose is presumably to trace the origin of a communication by compromising some entrance and exit nodes. Once both are compromised, it is much easier to correlate traffic with a particular individual.

OK, you've got yourself a single phase induction electric motor, but you don't know how to start it. Check out this simple how-to to discover a few methods of starting this motor up. You'll need to know this unless you want to burn out your motor!

Use a 2D image of clouds to generate realistic video footage of 3D cloud motion. In this tutorial from All Bets Are Off, Aharon Rabinowitz demonstrates how to create this effect using a single 2D image of clouds and a few simple clicks.

In this free video exercise lesson, you'll learn how to do a single-arm standing tricep extension exercise weight lifting routine. With weight lifting, as with any physical fitness system, a basic mastery of proper technique is essential for both maximizing the effectiveness of your workouts and avoiding accidental injury. For more information, and to get started using this weight lifting exercise yourself, watch this handy home-fitness how-to.

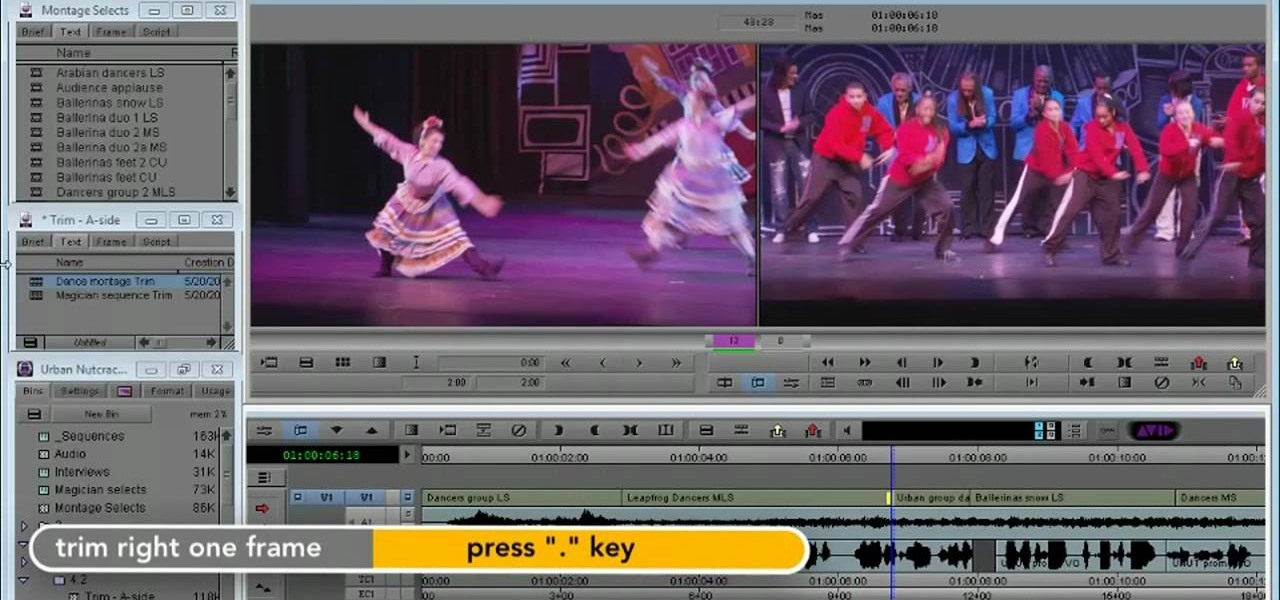
This clip presents instructions on how to do A-side single-roller trims within Avid Media Composer 5. Whether you're new to Avid's popular non-linear editor (also known as "The Avid") or are a seasoned digital video professional just looking to better acquaint yourself with Media Composer 5, you're sure to enjoy this free software tutorial. For detailed instructions, and to get started using Avid 5 yourself, take a look.

This crochet how to video is a demonstration of how to make a stuffed ball shape using single crochet in the style of amigurumi.

Are you new to crocheting? Watch this video tutorial to learn how to do a basic single crochet stitch. You will need some yarn and a size J crochet hook.

Are you new to crocheting? Watch this video tutorial to learn how to do a chainless single crochet foundation. You will need some yarn and a crochet needle.

In this tutorial, learn how to beat the media hype and go back to an old fashioned single blade razor. If you use a single blade razor, you will actually get a smoother, closer shave then the fancy multi-blade models, contrary to popular belief.

Most of us use a multi-blade pivot head razor, in the hope that we will get a closer shave. But did you know that you can get a close, comfortable shave with a good wet lather and single blade safety razor. This two part hair removal tutorial teaches you how to make the transition to shaving with a single-bladed razor. This is much cheaper way to shave. It may seem scary at first, but with a bit of practice you will be getting a close shave with a single blade razor.

Want to learn how to crochet? Then watch this how to video to learn some of the basics of crocheting. Once you have mastered the basic single chain stitch you can try the single crochet stitch. The single crochet stitch is very simple to do, just follow along with the video.

When we are building programs that communicate over a network, how can we keep our data private? The last thing we want is some other lousy hacker sniffing our packets, so how do we stop them? The easy answer: encryption. However, this is a very wide-ranging answer. Today we're going to look specifically at how to encrypt data in Python with dynamically generated encryption keys using what is known as the Diffie-Hellman key exchange.

One of the biggest problems in data security is authentication of data and its source. How can Alice be certain that the executable in her inbox is from the venerable Bob, and not from the not-so-venerable Oscar? Clearly Alice wants to know because if this file is actually sent to her by Oscar, the file might not be a game, but a trojan that can do anything on her computer such as sift through her email and passwords, upload her honeymoon pictures, or even turn on microphones and webcams. Thi...

In this tutorial, Paul Pacult tells you everything you need to know about selecting and drinking a fantastic scotch. Scotch is a drink best enjoyed slowly and for this reason you will want to make sure you choose a tasty option. Follow along and learn the ins and outs of single malts so that you can sit back and enjoy this truly masculine beverage.

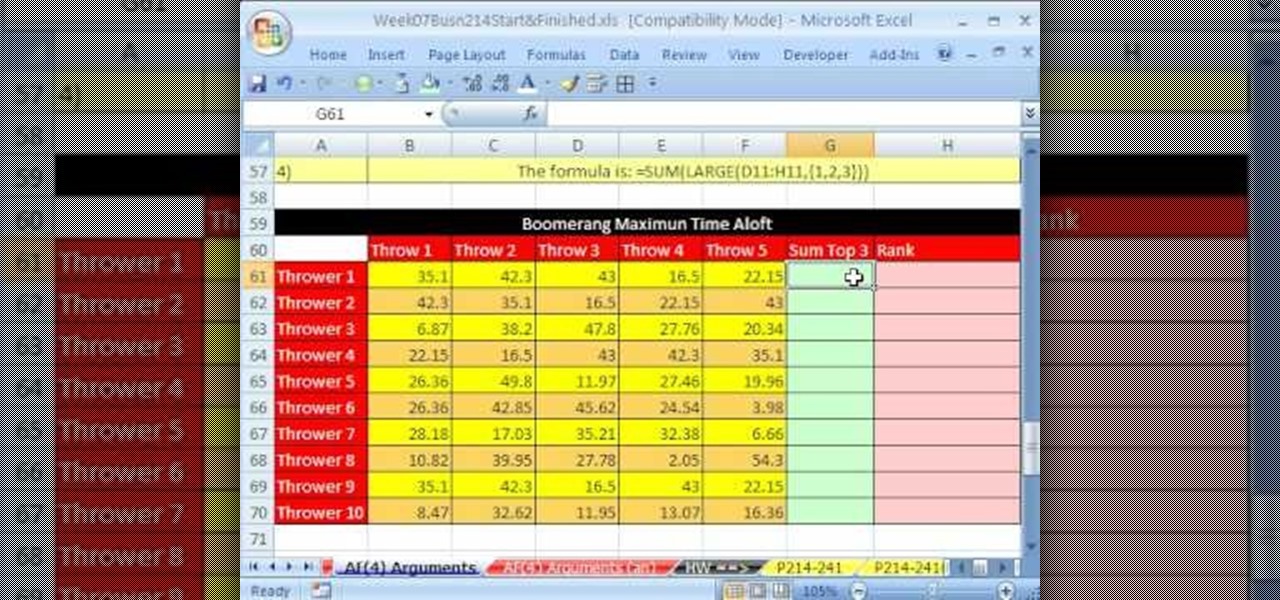
Whether you're interested in learning Microsoft Excel from the bottom up or just looking to pick up a few tips and tricks, you've come to the right place. In this tutorial from everyone's favorite digital spreadsheet guru, ExcelIsFun, the 39th installment in his "Highline Excel Class" series of free video Excel lessons, you'll learn how if an array or range is put into a function argument that is expecting a single value, the function becomes an array and delivers an array of values instead o...

This tutorial shows you how to make a chain stitch, and how to single crochet (sc) in both the chain base and an amigurumi round.

This is a view of how to get into a single scull rowing craft unassisted. This is brought to you by the Cork Boat Club in Ireland. It shows you how to Good tutorial for beginners. It shows you how to maintain balance, hold the rigger and lower yourself into the scull boat without falling into the river.

RC Concepcion, Host of Layers TV, goes over a couple of tips on how to setup a single page publication with multiple text boxes and a clipping mask. This 3 minute Illustrator tutorial is set to get you up to speed with the basics as quick as possible. So watch and learn how to create a single page with multiple text boxes and clipping masks in this Illustrator how-to.

Crochet personal homemade gifts for everyone. This how to video shows you how to crochet a baby beanie cap with the single crochet stitch. This crocheted baby beanie is sure to be the hit of the baby shower.

Supernova is coming! Prepare yourself. This video will show you how to beat Mission 19: Supernova in the StarCraft 2 single-player campaign mode. It's a great walkthrough with expert commentary throughout. SPOILER ALERT: This video contains relevant cinematics, so if you want just gameplay skip it.

Does shattering the sky sound good to you, or possibly like something that you should prevent? Mission 23 of StarCraft 2 campaign mode offers you the chance to do it. This video will walk you through it with expert commentary.

Single crochet stitches sound easy, but when many are knitted together into a pattern you get a very thick and heat-resistant surface. That's the idea behind this simple beginner-level crochet project for crafting a granny-style potholder out of a single crochet stitch.

A crochet single rib stitch is essentially a fancy way of saying a crochet stitch with an undulating up and down pattern. A "rib," or elevated stitch, runs across the finished piece vertically, forming an interesting pattern that can be used to accentuate scarves and mittens.

Check out this Make / Craft Magazine tutorial on plying yarn in weaving and textiles.

Ever wanted to learn how to pick a lock? Well, there's no better time than now to start learning the craft of so many locksmiths out there... lock picking. Just watch this video tutorial to see how to pick single-pin locks.

This tutorial video will teach you ho to slave with a single bladed razor. This razor will help you get a classic shave and do it with a single bladed razor.

Straightforward ab work with modifications for beginners and experts are shown in this pilates how-to video. Practice doing single leg lifts and changes with this pilates core workout. These pilates single leg lifts are sure to help tone and strengthen your abdominals in now time.

Improve you skills by learning the basics of crocheting with your left hand. This how to video is a tutorial that will show you how to crochet a left handed single crochet stitch. Crochet several rows of the single crochet to create larger yarn projects.

In this how to video, learn to play the slide pedal technique on the bass drum. This tutorial is for intermediate drummers.

This episode of Take Zer0 discusses the differences between the multi-camera format used in television, and the single-camera setup most often used in film production. Since it's likely that indie filmmakers have access to only one camera, we will explain and offer examples of how to efficiently shoot multiple takes with one camera to convey a single action.

Traps can serve a number of functions in your Terraria world. Watch this video to learn how to build traps that work well in both single player and multiplayer Terraria. As they say, there's more than one way to trap a mob.

Extreme crochet is when you bring multiple strands of yarn together and treat it like one big strand. You will definitely need a size P hook to be able to work with this much yarn. Here is how to use single crochet stitches when making something with extreme crochet.

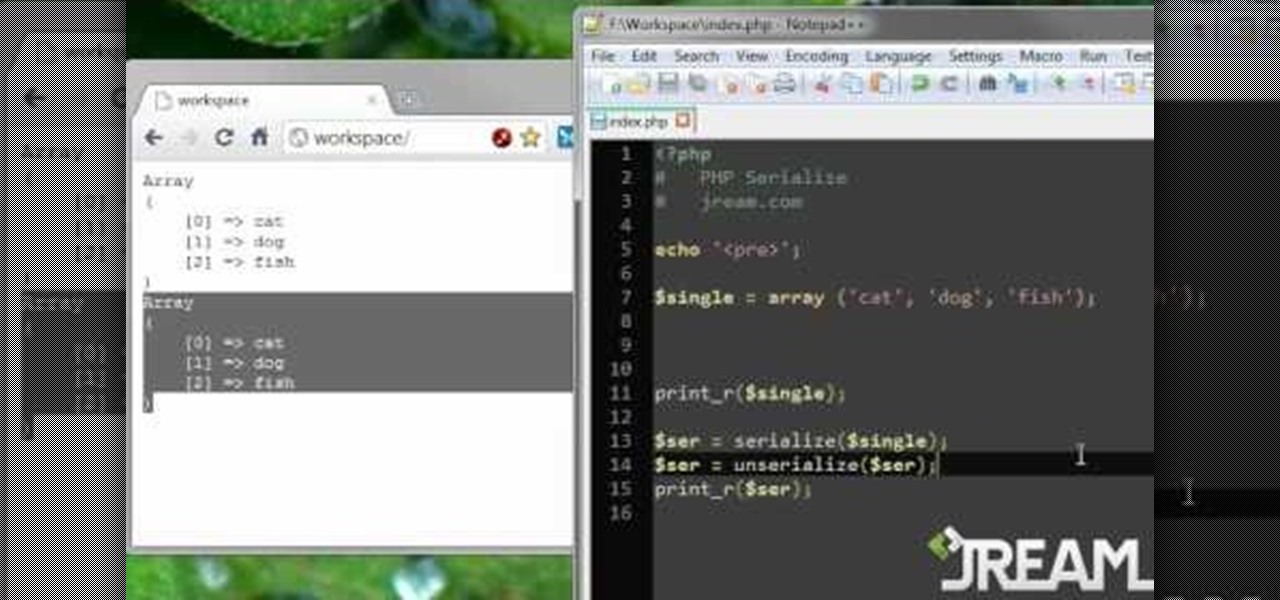
Learn to serialize your data and convert multidimensional arrays into a single string by following along with this informative video from JREAMdesign. Serializing your data essentially compacts it from an expanded array into a string series of values, a very handy PHP feature indeed.

Single player survival is the mode in Minecraft where you will have to worry about zombies and monsters, and your first night can be the scariest. This tutorial gives you some useful tips and tricks on how to get through that difficult first night.

The single stitch is a very simple stitch, easy for beginners to master, which can be used to join two granny squares together. This is a useful technique for joining any two crochet pieces together of any size or shape, not just granny squares!