These days, we increasingly have more and more devices in our everyday possession. While a notebook computer, a tablet, and a smartphone may seem like overkill, they do work to make our lives easier and even help reduce clutter in certain ways.

A flat soda tastes awful. It's almost as bad as drinking a room temperature milkshake. Of course, you can always opt to buy single-serving cans or 20 ounce bottles, but that's always going to be more expensive than 2-liters.

Whether you like it or not, certain songs get stuck in your head. You might be driving to work or school when suddenly Cher's 1998 lead single "Believe" plays on the radio.

YouTube is the third most popular website in the world, after Google and Facebook. Millions of subscriptions happen each day on YouTube, with over 800 million unique users visiting each month. In that timespan, roughly 4 billion hours of video are watched, with 72 hours of video uploaded every single minute.

The vast majority of people involved in Steampunk are interested in history but, like with science, there's something about history that we don't talk about very often: The holes.

Time-lapse videos are a recent phenomenon to the mainstream audience—in movies, on television shows, and even in commercial ads. These sped-up and blurred images are a microcosm of many of our lives in which we're constantly in a hurry to get somewhere. We like everything fast: our work, our coffee, and our news.

While one second may not seem like much, it's the perfect amount of time to encapsulate your day. Photographs are just that, instant snapshots of your day that can send you flying back to that exact moment of time. A couple of months back I visited New York, but I don't recall what I ate, what I wore, or even what I felt. Whenever I look at this picture though, it all comes flooding back to me. I remember that it was a Friday. I remember I ate a brownie, because after I got off the bus I was ...

In this project, you'll learn step by step how to modify a microwave oven transformer into a high-current device that can pump out 800 amps of electrical current, which is enough amperage to melt metal. If you liked the Metal Melter you saw in my previous project, here's how you can make your own!

Like most new things, the Start Screen in Windows 8 has its adorers and detractors, but either way you slice it—it's here to stay. I'm still getting used to the Start Screen, so I'm not sure if it's a love or hate feeling yet, but I do know one thing—I want my own background!

This may seem like an odd subject, because what do Steampunks and iPhones even have to do with each other? Actually, more than you might think!

Sometimes you just want to kill a whole bunch of things at once, or to paraphrase Samuel L. Jackson in Jackie Brown, sometimes you absolutely, positively got to kill every mob in the room. Well, the automatic machine gun is the way to do it; accept no substitutes!

A travelator, also known as a moving walkway or moving sidewalk, seems like a tricky thing to build in Minecraft, especially when it's zigzagging, but there are really simple autowalks out there (like this one).

Chopsticks are very easily reusable, yet they always get thrown away. You use them when you get Chinese takeout, then toss them out without even a backwards glance.

As I said before in my earlier post on how to make a two-tone doorbell, sound is more than just music. Note blocks can create a wide variety of notes and sounds, and those can be used for more than just making a stirring rendition of "Still Alive" from Portal.

Have you ever felt like you wanted to totally annihilate someone in Minecraft with a machine gun? Yeah, me, too. Thankfully, you can!

Hello! This post is not about craft, it's about cyber bullying. If you ever had such an experience, that an unknown hacker was bullying you for no reason at all, please follow my words. Thank you! Step 1: Let All the People You Know That Your Are Being Harassed.

Omniscience is not required to make some really cool shit happen. Yes, it took a while, but we can make fuel from the Sun! Solar panels are basically our answer to God. And now that we can make solar electricity, finding the most efficient way to harvest it is tricky.

The introduction of smartphones has been what some may see as a step backwards in technology regarding batteries. The first cell phone that I had would last 3-4 days on a single charge; however, the lack of functions minimized the use that is saw.

Home cooks know firsthand what it takes to make delicious and amazing food for friends and family. One of the most effective ingredients to making foods as delicious as possible is herbs.

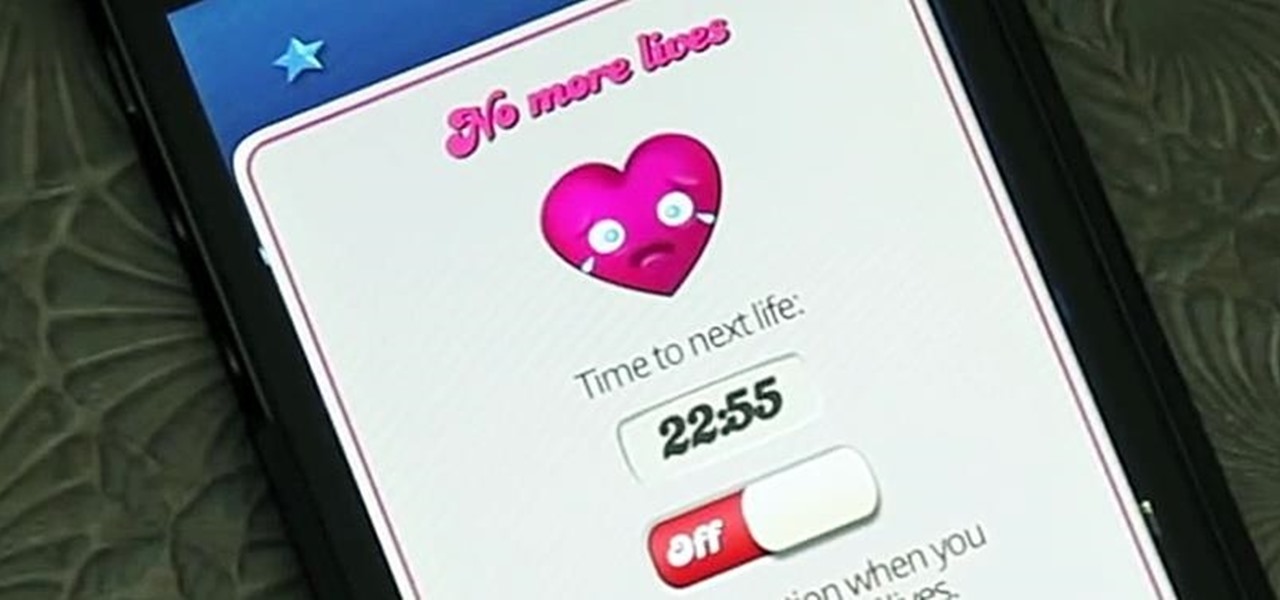
I hate waiting to play, and I hate bugging my Facebook friends even more. But that's what Candy Crush Saga makes you do if you want to get new lives and levels faster.

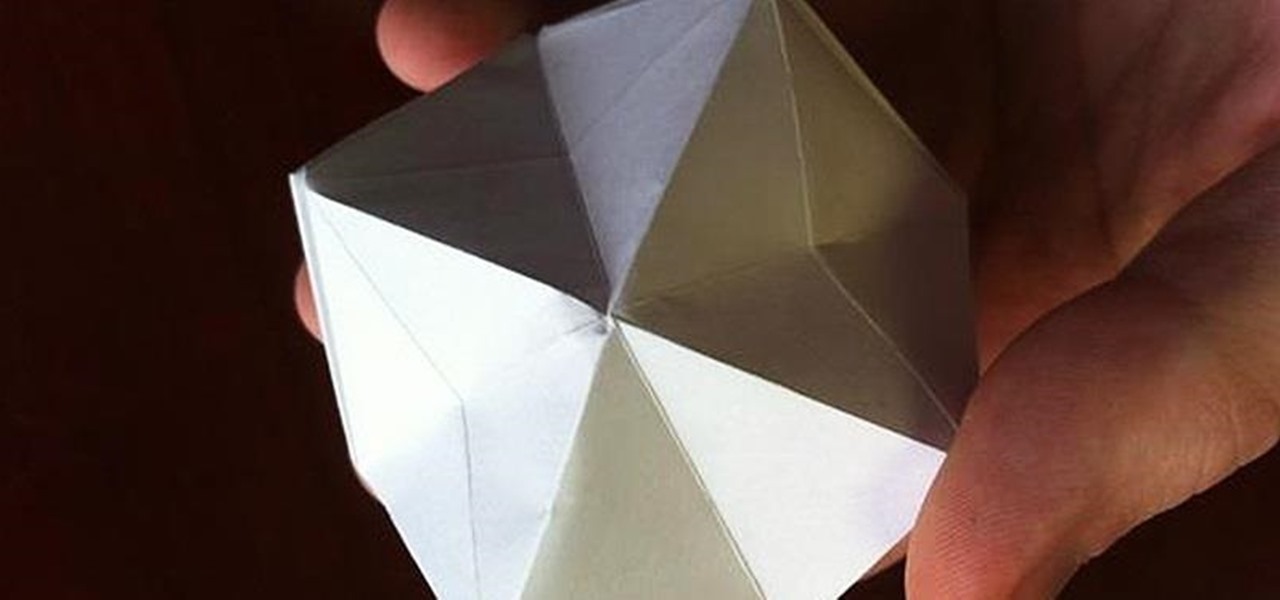
One of the most popular and basic origami geometric shapes is the "water bomb," which is a simple inflated cube. With a few extra folds and only a minor shift in approach, a more complex geometric shape can be achieved.

This is a lengthy, detailed series on iPhone development, for which you'll need an Intel-based Mac computer, running Mac OS X 10.5 (Leopard) or higher. Then, before you actually get started developing for the iPhone, you'll need to register as a developer with Apple. Then, you'll need to download Xcode and the iPhone SDK. Once you have all this, you can start developing iPhone applications!

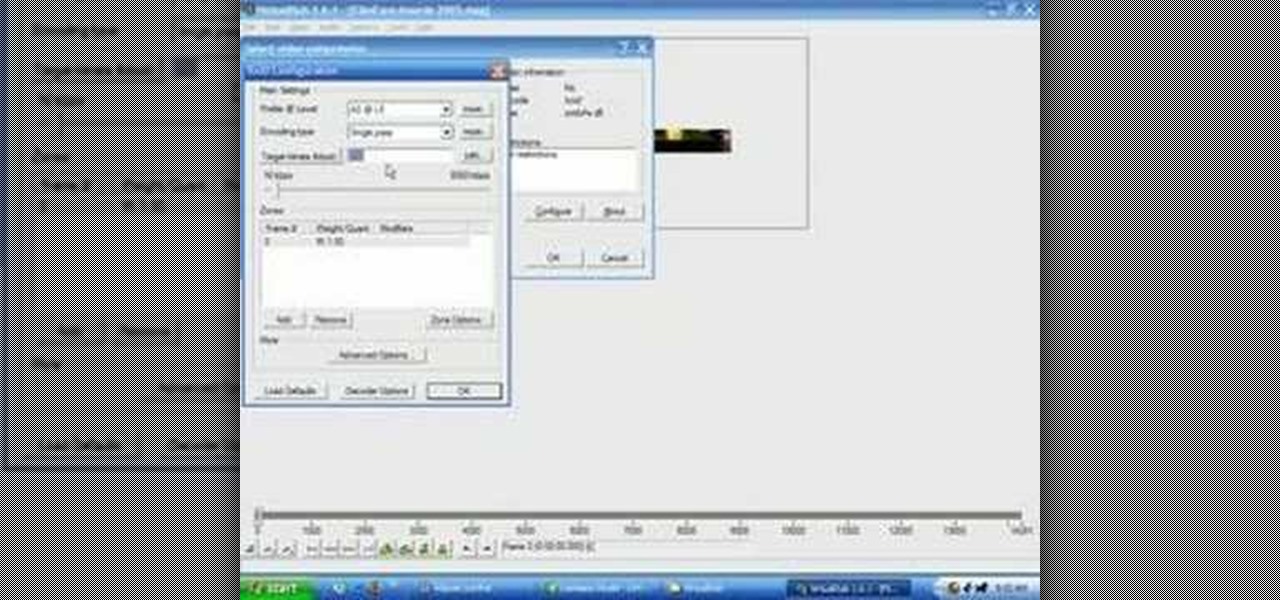
This quick video will show you how to compress a video file. To compress a video file you will need software called Virtual Dub. Open Virtual Dub and open a video file you want to compress. Click on Video Compression Choose the video codec named Xvid, and click on Configure. Select AS@L5 and Single Pass. Click on the target button, select 300kb. Go to Audio Compression. Select MPEG layer 320kb stereo sound. Save as an AVI. When it's finished the file will be on your desktop.

Whenever you need to type out a fraction on your iPhone, whether in a message, word document, presentation, math problem, recipe, or wherever else you need it, it's easy to use numbers and slashes. But there's a way to make fractions look more professional and easier to read straight from your keyboard.

This week, Google showed off some wild new and innovative AR experiences that showcase the WebXR protocol for browser-based AR content, while 8th Wall applied its own web-based AR platform in service of Captain Morgan.

People fundamentally distrust magicians. And they should. The illusions they proffer are just that, illusions meant to astound rather than tangible interactions and results that have weight and meaning in our real world. Our lizard brains know this, and, no matter what the outstanding feat of "magic" presented, we nevertheless hold fast to our survival-based grip on the truth: we just saw simply "can't be real."

Navigating and editing text is an essential part of any operating system, and with iOS 13, Apple has made some significant changes. Some things remain the same when working with text, but there are many updates to moving the cursor, scrolling, and selecting, cutting, copying, pasting, undoing, and redoing text.

The Windows 10 desktop and microphone can be livestreamed without using Remote Desktop Protocol (RDP) software and without opening any ports on the target computer. A hacker with low user privileges can monitor and exfiltrate a target's every move and private conversation in real time no matter where they are. Hackers are watching and listening, and there are few ways to protect yourself.

With an inconspicuous Android phone and USB flash drive, an attacker can compromise a Windows 10 computer in less than 15 seconds. Once a root shell has been established, long-term persistence to the backdoor can be configured with just two simple commands — all while bypassing antivirus software and Windows Defender.

The easiest way around a security policy is to find users who don't follow it. The Have I Been Pwned database identifies accounts with information breached by major third parties like Yahoo and LinkedIn. With Maltego, hackers can locate breached accounts created using company email addresses, potentially giving attackers access to a company account if the employee reuses a compromised password.

Identifying vulnerable devices and services on a target router can be difficult without leaving logs and other traces of an active attacker on the network. However, there is a way to covertly decrypt and view Wi-Fi activity without ever connecting to the wireless network.

It's easy to have your password stolen. Important people like executives, government workers, journalists, and activists face sophisticated phishing attacks to compromise their online accounts, often targeting Google account credentials. To reduce this risk, Google created the Advanced Protection Program, which uses U2F security keys to control account access and make stolen passwords worthless.

There's no doubt Kali has established itself as the most popular penetration distribution available. However, just because it's the fan favorite of beginners and security researchers doesn't make it right for everyone. Manjaro Linux is a beginner-friendly Arch-based distribution which can be easily weaponized with the Black Arch expansion, creating a friendlier first-time Arch experience.

While there aren't as many ways to customize your iPhone like there is on Android, there are still a lot of apps out there that can help streamline and enhance your experience beyond Apple's own default options — and we've hand-picked over 100 essentials.

Surveillance is always a useful tool in a hacker's arsenal, whether deployed offensively or defensively. Watching targets yourself isn't always practical, and traditional surveillance camera systems can be costly, lacking in capabilities, or both. Today, we will use motionEyeOS running on a Raspberry Pi Zero to create a small, concealable Wi-Fi connected spy camera that is both affordable and easily concealed.

It's universally known that broccoli, kale, Brussels sprouts, cauliflower, and all cruciferous vegetables (also known as brassicas) are good for you—but you probably don't know exactly how good they really are.

Whisking liquids seems somehow quaint, especially since there are good, cheap devices out there like immersion blenders and hand mixers that can whip cream, turn egg whites into meringue, and mix batters for you.

If you've beaten Year 1 - The Sorcerer's Stone of LEGO Harry Potter: Years 1-4 on the Xbox 360, then get ready for the LEGO-ized version of J. K. Rowling's second masterpiece, Year 2 - The Chamber of Secrets. Get every single achievement, every single collectible… everything you can imagine. All the videos and levels are listed below.

Watch a 41 part series on Spore's Space Stage. How will you create the universe? With Spore you can nurture your creature through five stages of evolution: Cell, Creature, Tribe, Civilization, and Space. Or if you prefer, spend as much time as you like making creatures, vehicles, buildings and spaceships with Spore’s unique Creator tools.