
How To: Neutralize mean girls
Rumors, gossip, exclusion. Mean girls have a lot of weapons in their repertoire – here's how to combat all that nastiness.


Rumors, gossip, exclusion. Mean girls have a lot of weapons in their repertoire – here's how to combat all that nastiness.

Buying a digital camera doesn't mean your old prints, slides, or negatives are obsolete. You can easily convert them with a scanner to bring them into the 21st century. Watch this video to learn how to convert photos to digital.

Learn how to get your body bikini ready. Try these proven methods to get an awesome bathing suit bod.

FreshDV had the opportunity recently to speak with Jerome Courshon on the marketing and distribution of movies and films. Jerome offers a full course in the “Secrets of Distribution” . If you are a filmmaker of any kind you owe it to your crew, your cast and yourself to watch this segment. From contracts, residuals, and pitfalls to avoid Jerome covers the 101 basics of film distribution and helps prepare you for what you need to know once the ink dries on the DVDs. In Jerome’s words:

Learn how to do full situps with dumbbells and alternate cross punches. Presented by Real Jock Gay Fitness Health & Life.

Learn how to do single medicine ball on the shelf crunches. Presented by Real Jock Gay Fitness Health & Life.

Is your iPhone frozen and stuck on a single screen? Don't worry: In most cases, your iPhone isn't broen. A frozen iPhone seems to be a common problem and thanks to this youngster, fixable. Learn how to fix and turn a frozen iPhone back on with help from these steps.

Knots are very useful for all types of situations. The video will show you how to tie a double over hand knot. You basically tie a loose single knot and then pass one end around again and back through the loop to make it a double knot. This looks like a pretty strong knot so try your hand at it.

If you want to burn a single song or entire cd from your itunes library you will have to create a play list. This video will show you how to create a play list and add songs that you would like put on a cd. You will then see how to burn the songs and you will have created your very own personalized cd. It’s not very difficult and will just take a few minutes.

Behold, the quickest way to make a paper sword out of a single sheet of printer paper. In just under two minutes create this simple weapon. Once you've mastered the basics in this video, add your own twist to this fast, fun design.

Follow these guidelines to fold an origami church. This video provides clear guidelines on some of the more difficult folds. You only need a single piece of origami paper to complete this tutorial of an origami church.

Follow this example to fold an origami six pointed star. This video provides clear visual examples so that you will not need an instruction booklet. This six pointed star can be folded from a single piece of silver origami paper. The six pointed star is sometimes used as an ornament at Tanabata, the Japanese festival of stars.

View this instructional origami video to fold a single paper stiletto shoe. With these instructions, the art of paper folding becomes fairly simple. One can repeat these instructions to complete the pair of origami paper stilettos.

This video origami tutorial shows how to transform a single sheet of square paper into an eight point star. Follow along with the demonstrator as she folds up this origami project. Watch this instructional video and learn how to origami a folded 8 point star.

This video origami tutorial shows how to fold a star destroyer paper airplane out of a single sheet of square paper. Never bold another boring paper airplane again. Watch and follow along with this instructional video to learn how to fold an origami star destroyer paper airplane.

This video origami tutorial shows how to use the traditional Japanese art of paper folding to make shapes; in this case, a trash can. All you need is a single sheet of paper. Learn how to origami a trash can by watching this instructional video.

This video crocheting tutorial shows how to do the half double crochet stitch. The half double crochet stitch is larger than a single crochet stitch, but not as large as a double. Watch this instructional video and learn how to stitch the half double crochet.

A simple video tutorial showing you how to take a single card and make it disappear from both hands, then, if you wish, you can make it reappear in your hand.

Mika demonstrates easy devil stick tricks. You can do a single throw and a double hitting. You can also put the devil stick over your leg.

A professional Roulette trainer explains in detail and through live demonstrations the rules of the game, explaining the differences between single and double, money management, and percentages. You will get to understand possible mistakes.
Learn how to download without using google or any torrents! Single Fish works. But don't do anything illegal now.

A flower arrangement with just one type of flower? It may sound monotonous, but it's actually understated and quite elegant, not to mention incredibly easy.

Place the neodymium magnets on the track and place four or five ball bearings in a line touching one side of the magnets. When you are ready to fire it, nudge the single ball bearing so it slowing rolls toward the magnets.

Websites and web applications power the internet as we know it, representing a juicy target for any hacker or red team. TIDoS is a framework of modules brought together for their usefulness in hacking web apps, organized into a common sense workflow. With an impressive array of active and passive OSINT modules, TIDoS has the right instrument for any web app audit.

The newly-announced Moto G7 Play offers some of the same upgrades as its sibling, the Moto G7, but at a much lower price. The upgrades are pretty significant when compared to last year's Moto G6 Play, taking this phone from the "only if you're on a strict budget" category into a great value option.
Besides the Apple vs. Samsung competition, few battles are as vocal as the battle between the best Pixel and best iPhone. This year, it's the Pixel 3 XL and iPhone XS Max, two phones that are equipped with minor hardware updates from their predecessors, though both showcase significant OS-level improvements.
The battle between the Pixels and the iPhones has been heating up over the last few years, and this year's bout is the best one yet, with Google's Pixel 3 taking on Apple's iPhone XS.

On the surface, AppleCare+ seems like an expensive and gimmicky option to tack onto your already pricey iPhone 11, 11 Pro, or 11 Pro Max. Upon further inspection, however, you'll see that its seemingly expensive price tag is chump change compared to the fees you'll have to pay if you end up having to repair your premium device outside its one-year warranty.

Gmail conversations, Facebook private messages, and personal photos can all be viewed by a hacker who has backdoor access to a target's Mac. By livestreaming the desktop or exfiltrating screenshots, this information can be used for blackmail and targeted social engineering attacks to further compromise the mark.

An incorrectly scaled object in your HoloLens app can make or break your project, so it's important to get scaling in Unity down, such as working with uniform and non-uniform factors, before moving onto to other aspects of your app.

Let's face It ... Pennywise is going to be the Halloween costume to beat this year. It's terrifying, simple enough to pull off, and with the original movie's gargantuan box office gross and the hit status of the sequel, released in September, everyone and their pet dog will get your costume.

Food is both a necessity and a joy. Many people enjoy exploring, cooking, eating, and learning about foods from around the world. But the picture isn't always rosy. A new report from the Centers for Disease Control and Prevention (CDC), highlights the ways and whereabouts of food that make us sick.
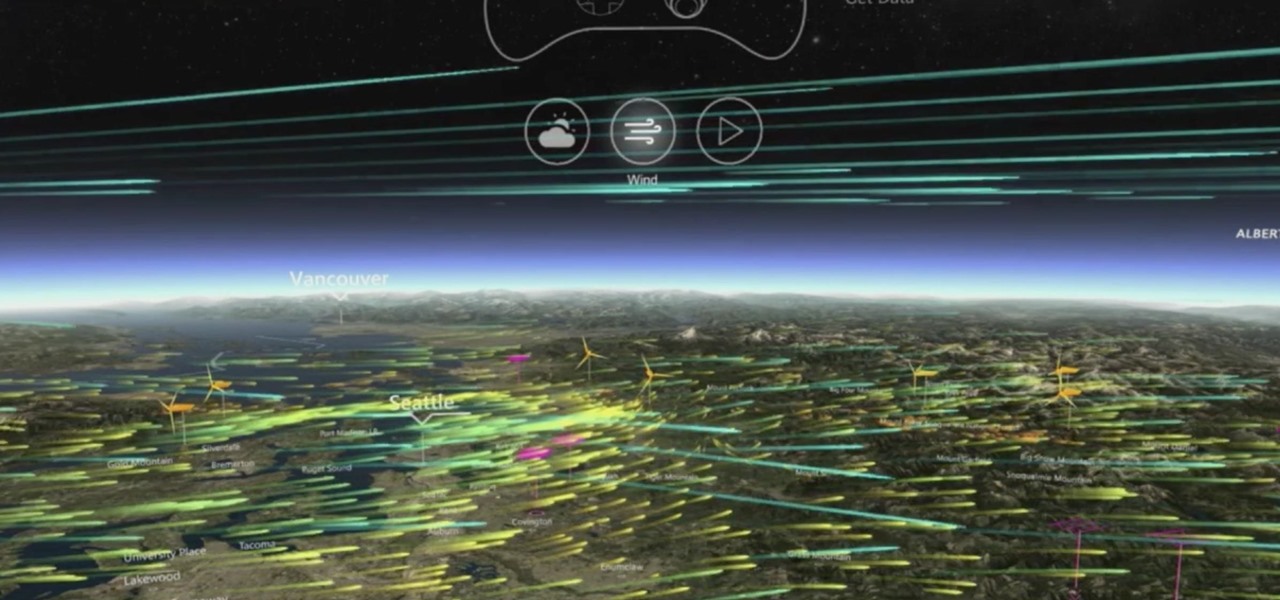
One thing that I got more and more excited about as we got closer and closer to the Microsoft Build 2017 developers conference was finally learning about the new Acer Windows Mixed Reality head-mounted displays (HMD). Brandon Bray, Principal Group Program Manager at Microsoft, had teased us a few weeks earlier at the Vision Summit event in Los Angeles, California, and said there would be a lot more information at Build. Fortunately for us, he was right.
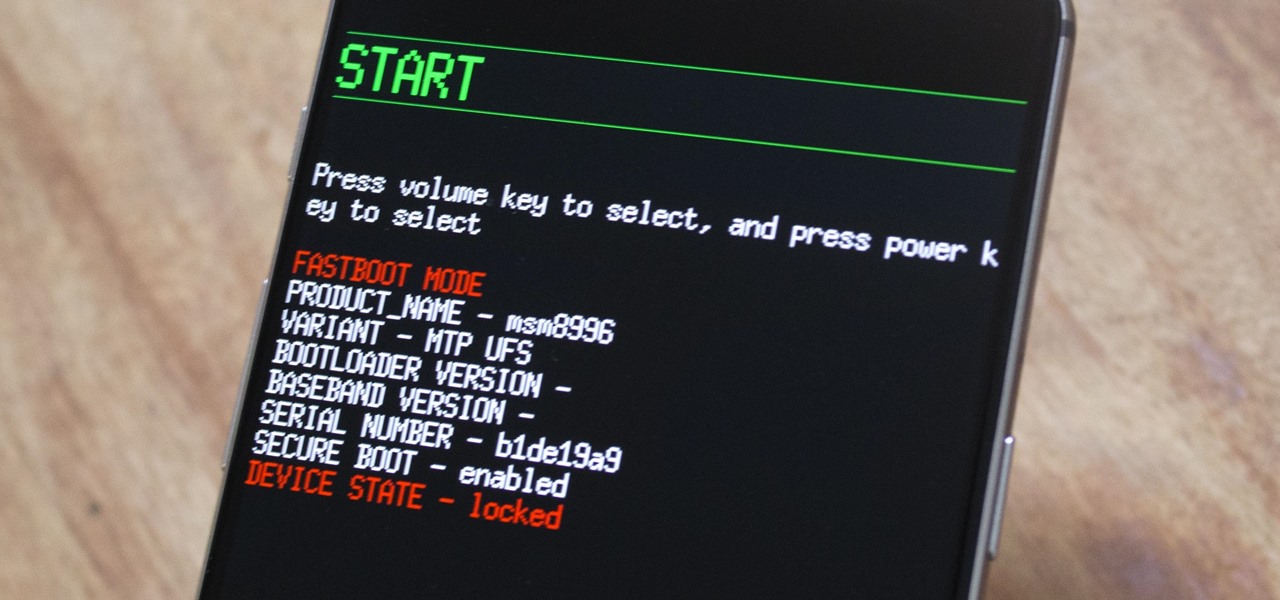
The OnePlus 3 and 3T are two of the most modder-friendly devices to be released in 2016. Not only that, but they're both extremely solid phones which happen to sport a very reasonable price tag. Among the things that make these devices such a joy for tinkerers is the fact that they have an unlockable bootloader, receive timely kernel source releases, and are actually quite easy to root.

Few summertime drinks are as sweet, tart, and refreshing as lemonade. It can cool off even the hottest day and help you relax poolside, on the beach, or just sitting around the house.

As exciting as it can be to crack open a beer, there's nothing fun about wandering around a party and asking other partygoers for a bottle opener.

Welcome to a tutorial on crypting technology. In this article, we will be discussing types of crypters, how they work and why they work. After defining these, we will then make our own basic crypter using the function I gave to you as a task to complete by yourself in the previous tutorial.

Over the past decade the Internet community has been witness to the rise of many new forms of online interaction. These new technologies have given rise to anonymous networks (like TOR), black markets within the deep web network (like the Silk Road), and even forms of digital currency, or more accurately crypto-currencies, such as Bitcoin. All of these technological advancements have contributed to securing users around the world and protecting their privacy. Therefore it is no surprise that ...

Welcome back, my tenderfoot hackers! In this series, we are exploring the myriad of ways to hack web applications. As you know, web applications are those apps that run the websites of everything from your next door neighbor, to the all-powerful financial institutions that run the world. Each of these applications is vulnerable to attack, but not all in the same way.

Welcome back, my aspiring hackers and those who want to catch my aspiring hackers! As most of you know, this series on digital forensics is inspired by the motivation to keep all of you all out of custody. The more you know about the techniques used by law enforcement and forensic investigators, the better you can evade them.