This video crocheting tutorial demonstrates how to do single crochet stitches for Japanese amigurumi shapes. This pattern will make a ball shape, useful for amigurumi yarn toys. Learn how to stitch a single crochet for ball shapes by watching this instructional video.

The ability to stay connected online regardless of your environment is incredibly valuable. Being able to access the internet during a blackout, check your messages while camping, or get in contact with emergency services while you're out in the middle of nowhere can be the difference between a brief inconvenience and prolonged suffering. The DuoTurbo 4G LTE Mobile Hotspot with Complimentary 9 GB Data can give you that easy, constant connectivity, and right now it's on sale for $152.99 — 10% ...

Almost 20% of the US population (about 60 million Americans) live in rural areas where mobile reception is weak or nonexistent. In times of crisis, these Americans can't rely on the internet to communicate with loved ones or receive new information. This is why being able to interact offline is so important.

If you have friends who aren't privacy-conscious, you've surely heard the old "What do I have to hide?" excuse. Despite the fact that billions of people are using the internet each day, many of them don't know the dangers that can find them. And many don't know the tools to combat them.

Apple's latest updates to its operating systems add another security feature to its Find My service, so you have an even better chance at locating your lost iPhone, iPad, or Mac should it ever happen. As long as you have the option enabled, you can leverage other Apple users' devices to find yours on the map.

With just one line of Ruby code embedded into a fake PDF, a hacker can remotely control any Mac computer from anywhere in the world. Creating the command is the easy part, but getting the target to open the code is where a hacker will need to get creative.

Having a dropped call can be incredibly frustrating, especially when you look down and see that your iPhone has full reception. While there's any number of issues that can cause this, one common and often overlooked issue is your iPhone failing to switch cell towers as appropriately needed.

Using Netcat to backdoor a macOS device has its short-comings. If the compromised Mac goes to sleep, the Netcat background process will occasionally fail to terminate correctly; This leaves Netcat running infinitely in the background and the attacker with no new way into the device. As an alternative, we'll use the lesser-known Tcl shell which can handle abrupt backdoor disconnections.

Electronic warfare tactics work by jamming, disrupting, or disabling the technology a target uses to perform a critical function, and IoT devices are especially vulnerable to attacks. Wireless security cameras like the Nest Cam are frequently used to secure critical locations, but a hacker can surgically disable a webcam or other Wi-Fi connected device without disturbing the rest of the network.

The misconception that macOS is more secure than the Windows operating system is far from the truth. With just one small command, a hacker can completely take over a MacBook and control it remotely.

Several recent research studies have pointed to the importance of the microbes that live in our gut to many aspects of our health. A recent finding shows how bacteria that penetrate the mucus lining of the colon could play a significant role in diabetes.

The Cloud Security Alliance (CSA), a leading IT trade association, has published its first report on risks and recommendations for connected-vehicle security, ahead of when driverless cars are about to see volume production in the near future.

If imitation truly is the sincerest form of flattery, then Snapchat must be blushing profusely as Instagram continues to shamelessly copy its features and dig into its wallet. Instagram has also managed to copy some of the security aspects — or lack thereof — of one of Snapchat's hottest characteristics.

If you're one who likes to tinker with Android, TWRP is the first thing you should install. It replaces your phone's stock recovery mode interface and adds over a dozen advanced features to your device—most notably, the ability to flash ZIPs that can modify practically every aspect of your operating system. It's certainly one of the most powerful tools available for Android, and there's simply nothing capable of replacing it.

In the world of analog synthesizers, hitting a key, twisting a knob, or sliding a fader makes a beautiful musical (or not so musical) sound and can be an amazing and downright satisfying experience. Now it's about to get even more satisfying, if you add Microsoft's HoloLens into the mix as a means to twist those knobs virtually instead.

Windows 10 has so many new features that we couldn't even cover them all with one article. From keyboard shortcuts to revamped search functions and all-new window gestures, Microsoft definitely piled on the fresh functionality in the latest version of their operating system.

With a slab-style touchscreen device, butt dialing is always going to be a problem. While you're moving about, your phone can unlock itself and give your most recent contact a ring, leading to an awkward one-sided conversation where the other person gets to eavesdrop on everything you're doing or saying at that moment.

Over the past decade the Internet community has been witness to the rise of many new forms of online interaction. These new technologies have given rise to anonymous networks (like TOR), black markets within the deep web network (like the Silk Road), and even forms of digital currency, or more accurately crypto-currencies, such as Bitcoin. All of these technological advancements have contributed to securing users around the world and protecting their privacy. Therefore it is no surprise that ...

What type of person are you in group settings? Are you the social butterfly, eager to get to know everyone and interested in the people more than the setting? Or are you a wallflower, afraid to catch anyone's eye out of fear?

It seems like every day now that we see a new headline on a cyber security breach. These headlines usually involve millions of records being stolen from some large financial institution or retailer. What doesn't reach the headlines are the many individual breaches that happen millions of times a day, all over the world.

One of the most common complaints that people have about the Nexus 4 would have to be its intermittently poor Wi-Fi performance, a problem that for many, persists through the installation of updates and even custom ROMs.

It used to be easy to hack tethering—root your device and install a third-party or modded tethering app. But snuck in amongst the changes in Android 4.3, a new data-monitoring service of sorts made its debut. There used to be a time when your data connection was yours. You paid for it, so you were free to use it for whatever you wanted. Unfortunately, those days are long gone.

Welcome back, my aspiring hackers and those who want to catch my aspiring hackers! As most of you know, this series on digital forensics is inspired by the motivation to keep all of you all out of custody. The more you know about the techniques used by law enforcement and forensic investigators, the better you can evade them.

HTC claims to have improved the One M8's battery life by 40% over its predecessor, but there is always room for improvement.

Whenever a new version of a phone comes out, there's always that one cool feature you wish you had on yours. For me, that's Group Play.

Welcome back, my novice hackers! This next subject might seem a bit obscure, but I promise you, this lesson will benefit you significantly either as a hacker or system admin. This tutorial will cover what is usually referred to as a regular expression, or regex for short.

Welcome back, my fledgling hackers! One of the first issues any hacker has to address is reconnaissance. Before we even begin to hack, we need to know quite a bit about the target systems. We should know their IP address, what ports are open, what services are running, and what operating system the target is using. Only after gathering this information can we begin to plan our attack. Most hackers spend far more time doing reconnaissance than exploiting.

These days, we increasingly have more and more devices in our everyday possession. While a notebook computer, a tablet, and a smartphone may seem like overkill, they do work to make our lives easier and even help reduce clutter in certain ways.

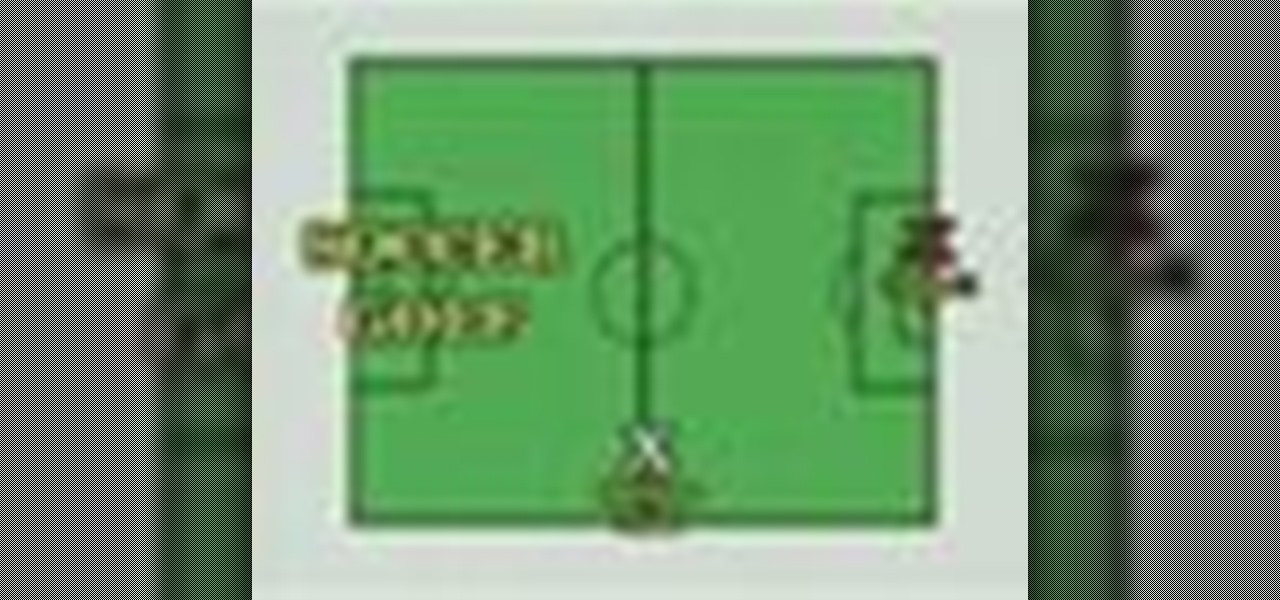
Try to get your ball in the hole in as few shots as possible - just like regular golf but with a soccer ball. The second video is a 2 player variation on soccer golf, only now the goal is to best your opponents score. The third video is a variation where the goal is to complete the course as fast you can (speed soccer golf).

Learn how to create custom fiberglass Single Sub enclosures and get professional results. Easy to follow step by step methods for your car audio install. Creating subwoofer boxes from fiberglass is a stronger and lighter alternative to using wood and just as easy if you get the right materials and watch this tutorial.

Learning and incorporating decorative borders on crochet projects can be a headache when they start to scrunch up. This crochet how-to video is a tutorial on how to do single stitch borders around a project without scrunching or messing up corners. Watch and let Mike show you how to work the needle so that you don't get any bunching around the edges.

Improve you crocheting skills by learning different ribbing techniques. This how to video is a tutorial that will show you how to crochet a single crochet ribbing. Watch and learn how to create decorative ribbing.

Watch this video to learn how to make a single crochet stitch.

Today is the anniversary of George Harrison's death nine years ago in 2001, and we thought a commemorative music lesson was in order. And instead of the usual Beatles fare, we thought we'd show you something a little less known, but just as good— "Handle with Care" by the Traveling Wilburys. Many still aren't familiar with the Traveling Wilburys, despite the superstar musicians involved, but that doesn't change the fact that these guys were awesome!

Exercise is a very important for everyone on a daily basis. Our society has evolved into a life of work, work and work. The majority of these jobs are sitting at a desk in some sort of cubicle. Humans are not built for this purpose; we are made to be active every single day. Thus, we must incorporate exercise in one way or another during our 14-16 hours of wake time. And this instructional video will show you a great exercise— how to do an abs crunch on an exercise ball.

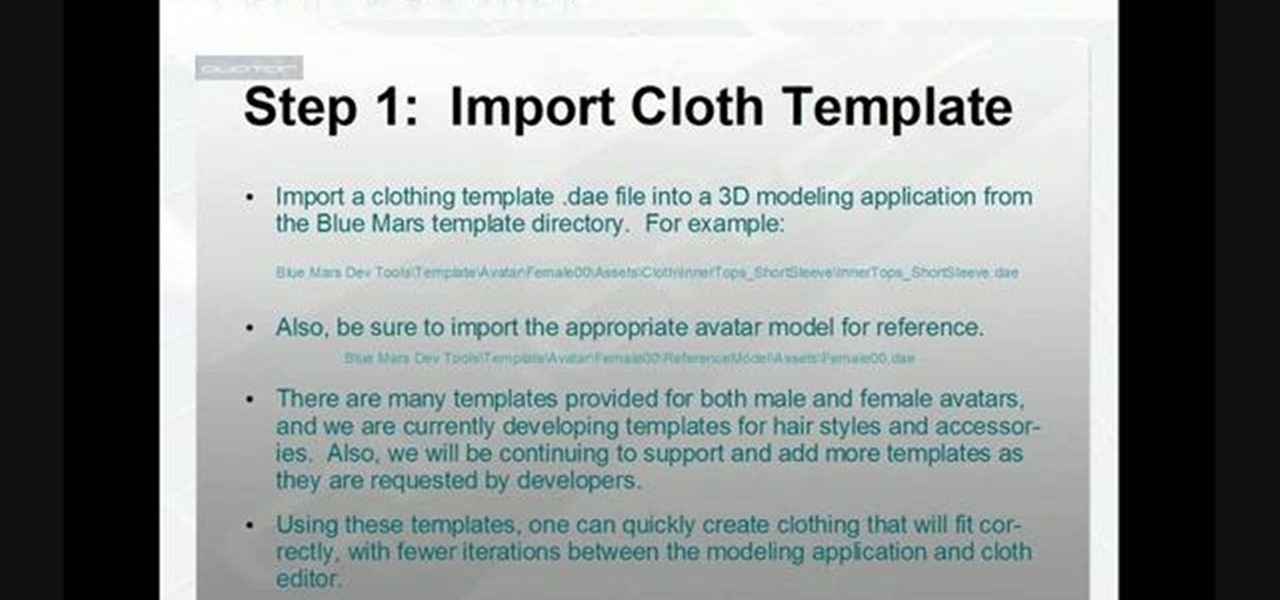
Create and animate your own piece of clothing! This tutorial series shows you how to properly create and texture a single item of clothing. Once it's created, you can then attach it to an object and animate it realiistically for your Audodesk project.

We don't know about you, but we're wondering how the hell Katy Perry even has time to work out these days with the countless number of promotional appearances, hostess jobs, planning a wedding, and singing gigs she's doing on a daily basis. But, after looking at a few recent pictures of the singer's fit and curvy body, she must be doing something to keep all that in shape.

If it's not hurting, it's not working. At least this saying is true when it comes to exercise. While low-intensity workouts like walking or doing standard crunches are good for your body, if you're looking to lose weight and tone up quickly, you must commit to doing some killer exercises.

No pain no gain, ladies and gents. If you want a fabulous body, trying to take the easy way out by trying those hokey "As Seen On TV" exercise machines or just by starving yourself is going to get you nowhere fast. Neither serve to encourage long term weight loss results, and while you may lose weight, most of that weight is going to be loss of muscle mass because you're not exercising.

This is one of those dance moves that requires a little bit of practice, but the payoff is a phenomenol increase in the way you handle ladies when dancing at the club. Whether you're single or part of a couple, checking allows you to do two important things: 1. Control the movement and flow of the dancing for both you and your partner, and 2. Open up space for your girl to freestyle a bit.