
How To: Import HD video from a JVC Everio to a Mac via iLink
Let us help you install your JVC Everio software and hook up your JVC HD Everio video camera to your computer. Just select your operating system.


Let us help you install your JVC Everio software and hook up your JVC HD Everio video camera to your computer. Just select your operating system.

This tutorial for Devil May Cry 3 covers the basics of jump canceling and the overall advantages it will provide the player once mastered. The whole concept of a Jump Cancel (JC/JCing for short) is the cancellation of an aerial technique with a jump.

Check out this video tutorial to see how to use the BD Genie Safety Lancet blood sampler device. BD Genie Lancets are high quality, safety-engineered, single-use capillary blood sampling devices. They offer a permanently retractable blade or needle feature that minimizes the possibility of injury or reuse. BD offers a full range of blade depth and needle gauges for sufficient blood volume in multiple sample requirements. All Genie's can be used in conjunction with BD Microtainer Tubes.

Watch this video to learn how to play "Truly, Madly, Deeply" by Cascada on piano or keyboard. Right hand notes:

How to graft Lophophora The materials to be used:-
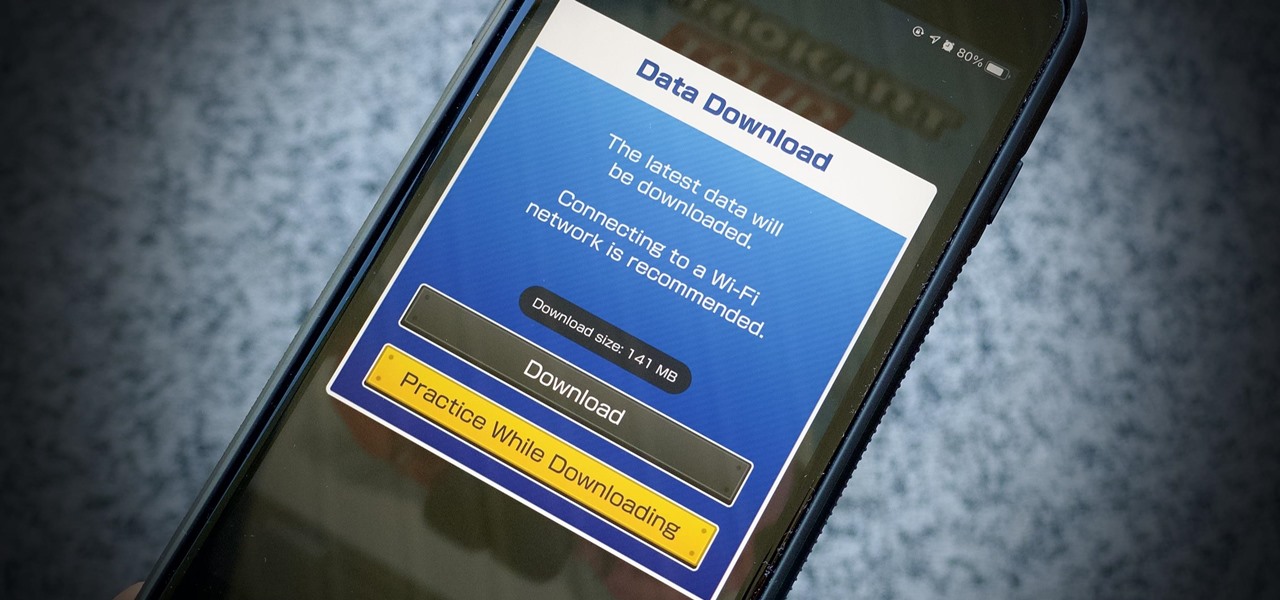
If you have a limited mobile data plan on your iPhone, you know how tricky it can be to stay within your given allotment. Large app installs and updates, 4K resolution videos, and photo backups can waste precious data resources in no time. And apps like Apple News, Facebook, Mail, and Netflix eat data like it's candy. But you can nip the problem in the bud by restricting data hogs from your cellular network.

While sheltering at home orders are lifting, companies are still conducting most business online. Case in point, hackers have been having a field day over the last few months. Securing your identity has always been important, but never as much as it is at this moment.

Keeping the books in order is one of the great challenges every business owner faces. Having a great product or service is one thing, but managing the minutia of invoicing can trip up a lot of small- and medium-sized businesses.

Mac users know why they love Apple. Of course, there are limitations. An entire universe of shortcuts is unavailable to the average user.

There's a lot of talk about 5G these days. You might even think your iPhone is 5G-ready, since, well, it says so right in the status bar. 5G E, right? Sorry to burst your bubble, but no iPhone is capable of connecting to 5G networks yet, no matter how much you pay for that 11 Pro.

Whether you're coding a simple app, trying to learn a new programming language, or building an entirely new operating system from scratch, being able to quickly and clearly organize your thoughts is absolutely paramount — even as an ethical hacker or penetration tester.

A stager is a small piece of software that's typically used by malware to hide what's happening in the early stages of infection and to download a larger payload later.

If you're using or need to use Zoom, the popular video teleconferencing service, you've almost certainly heard about "Zoombombing" by now. While Zoom has been adding security measures to address the problem, there are other things you can do to prevent or stop Zoombombers in their tracks so that your video meetings and chats go undisturbed and uninterrupted.

Without admin privileges, installing additional software, or modifying the Windows 10 firewall, an attacker can alter a router and perform a variety of exploits. It's accomplished by forwarding requests from Kali through a backdoored Windows computer to the router gateway with simple SSH tunnels.

SSH, or the secure shell, is a way of controlling a computer remotely from a command-line interface. While the information exchanged in the SSH session is encrypted, it's easy to spy on an SSH session if you have access to the computer that's being logged in to. Using a tool called SSHPry, we can spy on and inject commands into the SSH sessions of any other user logged in to on the same machine.
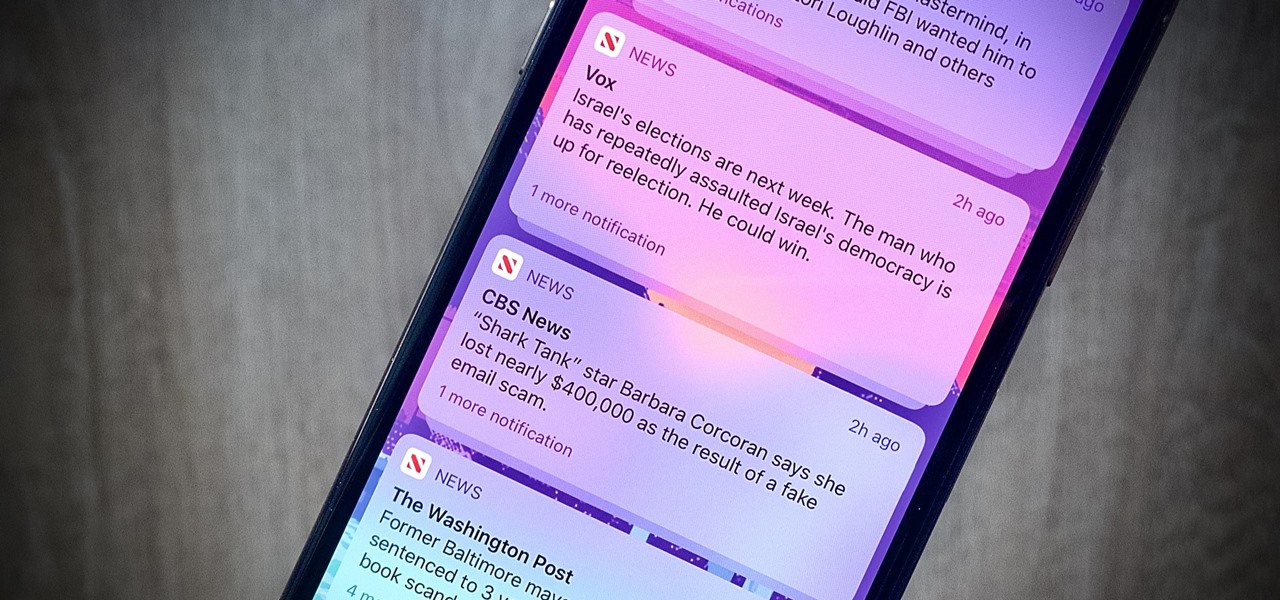
When left unmaintained, lock screen notifications can be an overwhelming, chaotic mess. Alerts coming in at a rapid pace can be hard to see because there are just too many of them, and your iPhone's screen sometimes can't even take it, falling asleep before you can read only a few notifications. If that sounds like you, there's an easy way to take back control of alerts — and your sanity.
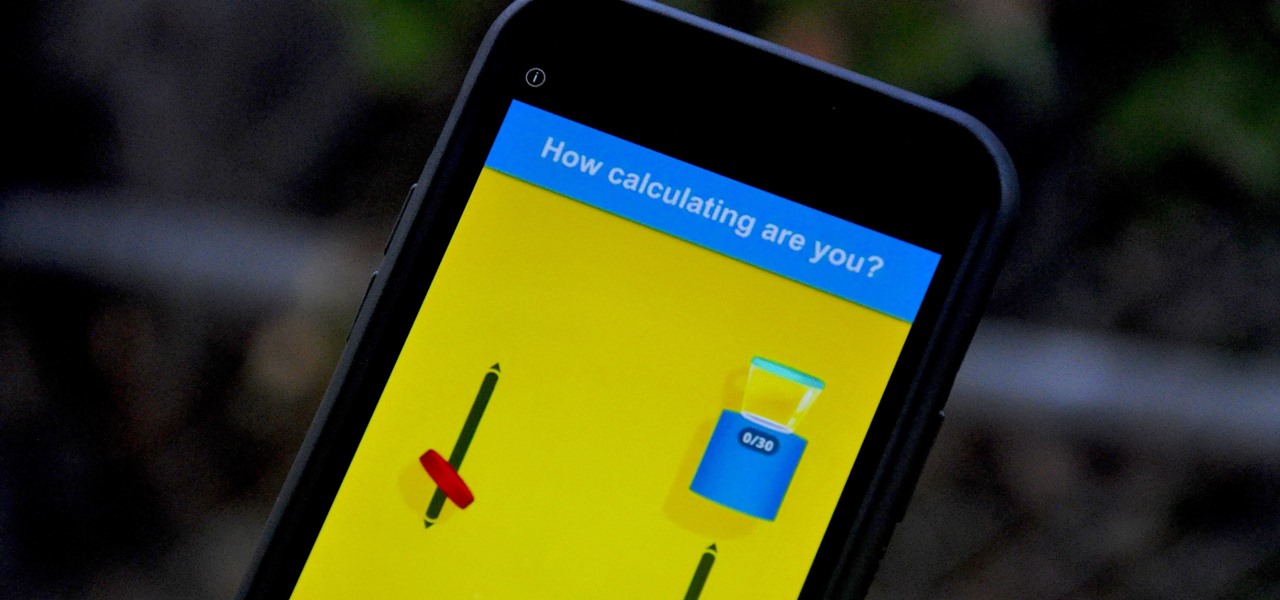
No one likes in-app advertisements, especially in mobile gaming, but they're necessary because they offer developers a way to make revenue without having to charge you to play. In some games, in-app purchases give you the chance to remove ads, but what can you do about apps that don't offer the option to kill ads?

The augmented reality team at USA Today closed out a prolific year of immersive storytelling with a hard-hitting companion piece exploring the controversial conflict in Afghanistan.

UnrealIRCd is an open-source IRC server that has been around since 1999 and is perhaps the most widely used one today. Version 3.2.8.1 was vulnerable to remote code execution due to a backdoor in the software. Today, we will be exploiting the vulnerability with Metasploit, examining the underlying code to understand it, and creating our own version of the exploit in Python.

Lenovo has done a great job preventing leaks of their new Moto RAZR. We've seen a few images here and there, but for the most part, we knew very little about the long-rumored phone. But with the announcement date just around the corner, an FCC filing has given us a look at the new RAZR from almost every angle.

The spatial computing world of Magic Leap is no longer limited to the rarefied tones of Sigur Rós and Sennheiser's Ambeo Augmented Audio app. Now, the entire music universe will be at your augmented reality fingertips.
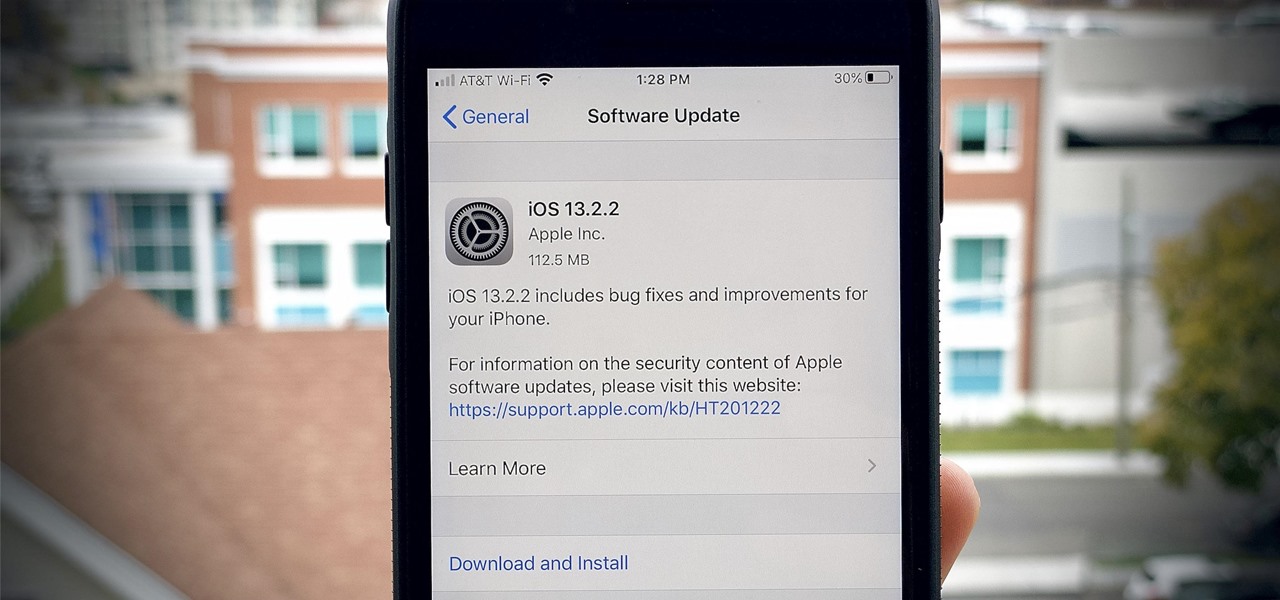
If you're a beta tester, you know Apple released iOS 13.3 this week, bringing with it stability for multitasking as well as minor changes throughout the OS. It seems Apple doesn't want the rest of us to go without this critical patch, as the company releases iOS 13.2.2 today, Thursday, Nov. 7.

One of the coolest things about Android is the massive development community behind it. These developers keep on cooking up new things even after official support has stopped for an older device. It breathes new life into somewhat forgotten devices, which is always great news. With Android 10 out, it's time to see what phones will get the custom ROM treatment.
Apps can collect a lot of data. Even if they don't have permission to access your GPS or camera, they can still read other sensors and learn a lot more than you'd think. Your gyroscope could be used as a keylogger. The light sensor could read your visited links. But if you're on Android 10, you don't need to worry about this.
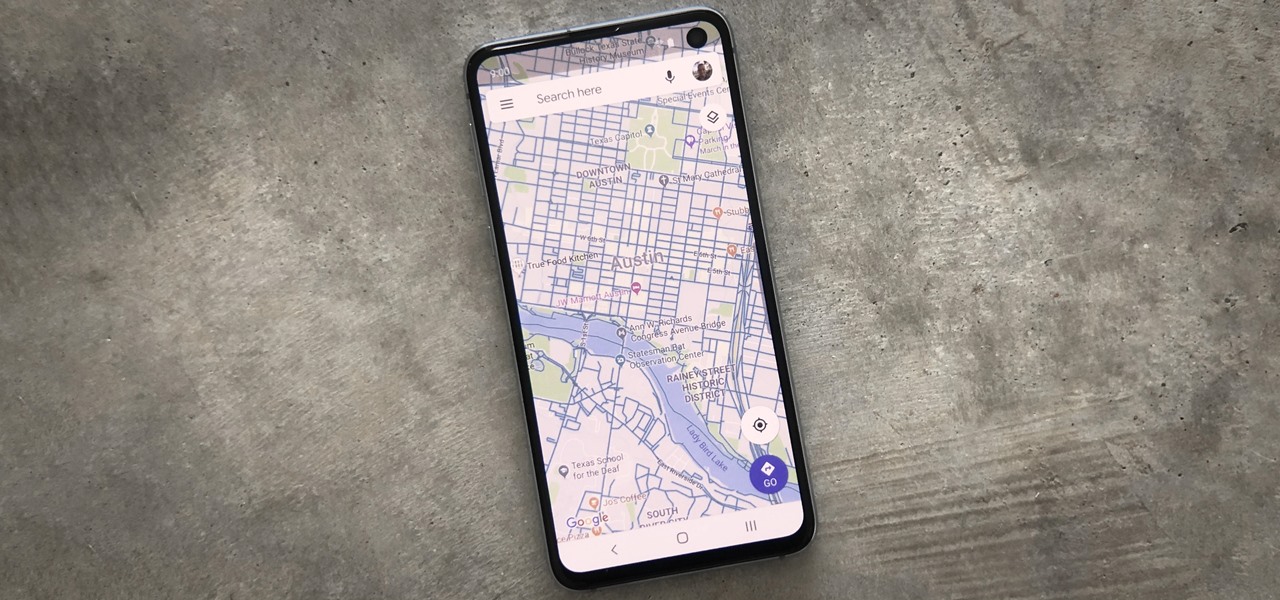
When you're going somewhere for the first time, it's nice to know what the destination will look like. Street View in Google Maps is the perfect tool for that, though it's always been a little awkward to access. But now, Google added a new overlay that will put Street View content literally one tap away at all times.

While Snapchat augmented reality often embraces pop stars like Drake and Ariana Grande, a couple of bands from the louder side of the music industry have found a home with Facebook.
With Android 10 "Q" right around the corner, now would be a great time to get accustomed to the new system-wide dark mode it's bringing with it. Dark themes not only allow for more comfortable viewing at night, but can also consume less battery at the same time. With a single button tap, you'll be able to enable this new dark theme for all compatible apps without having to jump through hoops.

Phone numbers often contain clues to the owner's identity and can bring up a lot of data during an OSINT investigation. Starting with a phone number, we can search through a large number of online databases with only a few clicks to discover information about a phone number. It can include the carrier, the owner's name and address, and even connected online accounts.

You already know that the best place to learn about the cutting edge of augmented reality is Next Reality, but the best event to meet the people and companies pushing the space forward is the annual Augmented Reality Expo (AWE), and we're giving away free tickets!

Popping a shell is often the main goal of a hacker, and it can be exciting when executed properly, but sometimes they do have their limitations. Metasploit's Meterpreter probably needs no introduction, but this powerful, dynamic payload can offer a leg up over normal shells. To prove it, we'll show how to take a normal command shell and elevate it to a Meterpreter session.

In the last few weeks, the Magic Leap ecosystem has ramped up activity with a number of new releases debuting just before the close of the year.

Portrait mode works with any dual-lens iPhone, as well as the single-lens iPhone XR, and lets you take impressive portraits with blurry, bokeh-filled backgrounds. Portrait selfies, on the other hand, are only available devices with Face ID. But that's only for Apple's Camera app itself — third-party apps like Messenger have "portrait" selfies for any iPhone — as well as any Android phone model.
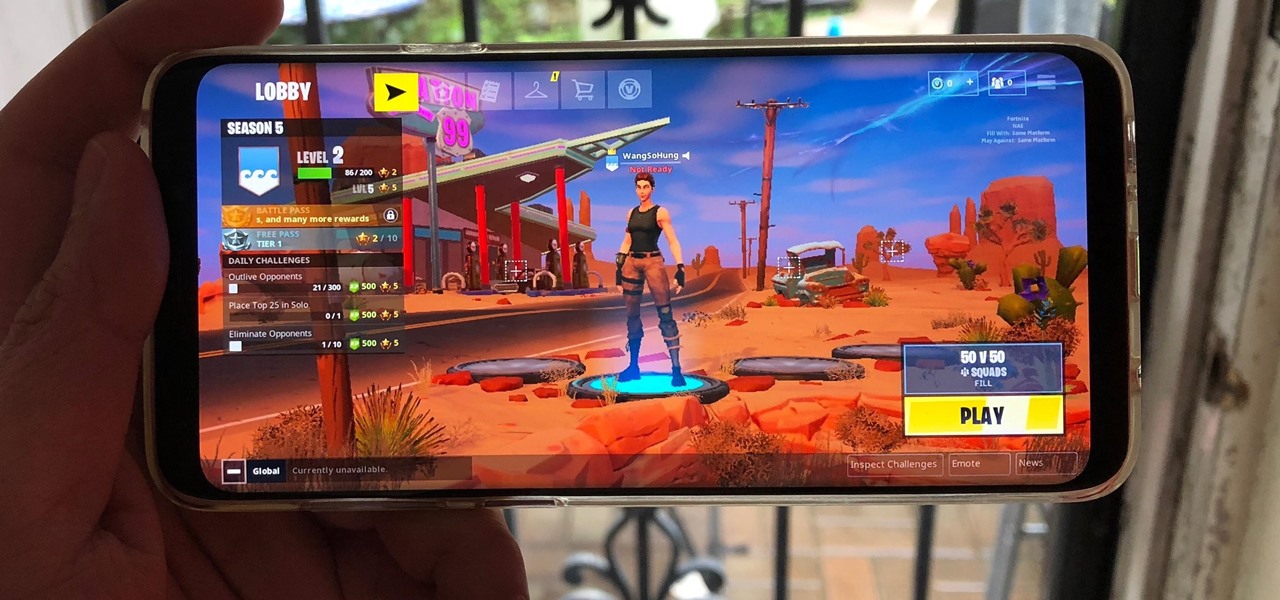
Fortnite's long awaited arrival on Android has ramped up excitement among gamers who are installing the beta version in astounding numbers. With so many midrange and budget devices running Android, however, it's important to stay on top of your device's performance to ensure smooth and uninterrupted gameplay.

As Android bug bounty hunters and penetration testers, we need a properly configured environment to work in when testing exploits and looking for vulnerabilities. This could mean a virtual Android operating system or a dedicated network for capturing requests and performing man-in-the-middle attacks.

Command injection is a technique used by hackers to execute system commands on a server, usually via a web application or some kind of GUI. This can happen when an application provides some sort of functionality to the user involving the use of system commands. When the input is not properly sanitized, commands not originally intended to be run are allowed to be executed.

While hackers have taken advantage of numerous vulnerabilities in Adobe's products to deliver payloads to Windows users via PDF files, a malicious PDF file can also wreak havoc on a Mac that's using the default Preview app. So think twice before double-clicking a PDF open on your MacBook — it might just be a Trojan with a rootkit inside.

Apple's lead marketing tool for the iPhone X, 3D Animoji that you control with your facial and head movements, are once again in the spotlight in a new commercial the company posted on its Korean YouTube account this week.

Realizing there's no voice to guide you while using your iPhone to navigate can be problematic, causing serious headaches from getting lost to unscheduled pit stops or worse. And while this problem can hit Apple Maps like other navigation apps out there, there are a number of fixes you can try to get navigation audio working again.

Apple has introduced a special edition iPhone 8 and 8 Plus to bring attention to the ongoing worldwide battle against AIDS. As the second iPhones to carry the (PRODUCT)RED name, these rare iPhones may quickly sell out when preorders open up on Tuesday, April 10, at 5:30 a.m. (PDT), so we'll go over some tips to help you secure a red iPhone before it's gone.

Android 9.0 Pie has officially rolled out, but for the time being, it's only available to Google's own Pixel phones and a select few others. Thankfully, you can get a taste of the Android Pie experience on any phone right now.