Samsung has just announced the Galaxy Note 10 and 10+. These are the latest and greatest from the largest smartphone OEM in the world. Plenty of numbers and specs have been thrown your way to showcase how good the Galaxy Note 10 is, but we wanted to simplify all this for you and key in on the most important things.

Who's ready to let future Facebook augmented reality smartglasses read their brain? Well, ready or not, the tech giant is making progress in the area of brain control interfaces (BCI) by funding research.
The OnePlus 7 Pro comes with a new Zen Mode feature to help increase your concentration and reduce distractions. It takes things a step further than Google's Digital Wellbeing by disabling your device and stopping sounds. But even if you don't have a OnePlus, you can now get this distraction-free feature on any phone.

If you find yourself with a roommate hogging limited data bandwidth with video games or discover a neighbor has invited themselves into your Wi-Fi network, you can easily take back control of your internet access. Evil Limiter does this by letting you control the bit rate of any device on the same network as you, allowing you to slow or even stop data transfer speeds for them completely.

For many, the stock version of Android is often considered the epitome of what the operating system should look and feel like by default. It's clean and clear of unwanted extra apps that come pre-installed with the system, provides a fluid and fast user experience, and runs on just about any device that has an unlocked bootloader to install a custom ROM with the stock version ready to go.

After showing off a prototype of the Grordbattle multiplayer first-person shooter at the Game Developer Conference, Magic Leap has added a new Shared World feature in version 0.95.0 of the Lumin OS update released this week.

What if you could easily visualize which access point every Wi-Fi device nearby is connected to in a matter of seconds? While programs like Airodump-ng can intercept this wireless information, making it easy for hackers to use and understand is another challenge. Fortunately, a tool called Airgraph-ng can visualize the relationships between Wi-Fi devices from only a few seconds of wireless observation.

After years of waiting, Microsoft has finally updated its industry-leading augmented reality device, the HoloLens.

When it comes to resistance to the elements, Samsung seems to believe in the old saying "if it ain't broke, don't fix it." They've carried over the IP68 rating under IEC 60529 that was first found on the S8 all the way to their tenth-anniversary flagship, the Galaxy S10. While this certainly sounds great on paper, it's natural to want to dig a little deeper and find out what the rating means.

We're still weeks away from a probably HoloLens 2 release, but Microsoft's immersive computing team is still hard at work on other aspects of its "mixed reality" ecosystem.

Smartphones and other Wi-Fi enabled devices send radio signals called probe frames to locate nearby wireless networks, which makes them easy to track by listening for their unique MAC address. To show how this kind of tracking works, we can program a NodeMCU in Arduino to sniff the air for packets from any device we want to track, turning on an LED when it's detected nearby.

The latest version in Epson's Moverio line of smartglasses looks to offer a headworn window into the world that prioritizes versatility as well as mobility.

Time to play — Fortnite is now officially available on Android. However, the game won't be available across the Android ecosystem right away. Fortnite Battle Royale launches on Samsung devices first. That means if you have a Galaxy S7, S8, S9, Note 8, Tab 3, or Tab 4, you can download the game right now.

Using Netcat to backdoor a macOS device has its short-comings. If the compromised Mac goes to sleep, the Netcat background process will occasionally fail to terminate correctly; This leaves Netcat running infinitely in the background and the attacker with no new way into the device. As an alternative, we'll use the lesser-known Tcl shell which can handle abrupt backdoor disconnections.

Note-taking apps are a dime a dozen on the Play Store. However, due to their inability to sync across devices, many can't compete with Google Keep. Mozilla decided to throw their hat in the ring with Notes by Firefox, and unlike others, their notes app syncs easily with one of the most popular browsers, plus it's encrypted.

A team of academics from three different universities and two private companies have just discovered a new vulnerability that affects almost every Android device since 2012. The vulnerability is known as RAMpage, and it could be used to gain complete control over the device.

The spirit of Google's Tango augmented reality platform lives on at Vivo, a China-based company that has developed its own 3D sensor for mobile devices.

We've shown you the best augmented reality headsets, and now it's time to show you the rest. These are the AR headsets you've probably never heard of or even seen. The AR headsets that, in some cases, have a shot at the big time, and may one day reach widespread adoption, and, in other cases, are unwieldily contraptions that look like something out of a weird science fiction movie.

If you cover a particular area in tech long enough, you develop certain pet peeves, and one of mine happens to be devices that attempt to keep us wed to the Google Glass style of augmented reality. And while I remain mostly uninterested in such devices, one of these products recently earned my admiration and might work for you, too, under the right circumstances. It's called the Golden-i Infinity.

While Huawei smartphones haven't always been the best choice when it comes to custom ROMs, one thing that has always been accessible is the ability to unlock the bootloader. An unlocked bootloader is the first step into the magical world of rooting, but after May 24, Huawei will stop offering this service.

Google's Pixel smartphone had a decent head start as one of the first devices to offer ARCore, but that early exclusivity has been frustrating for some Android device owners. Some of that frustration was relieved when Google added more Android devices to the ARCore list in February.

Last week, we told you about Microsoft's Alex Kipman and his nomination for the annual European Inventor Award, presented by the European Patent Office (EPO). And while that's big news in and of itself, it turns out we overlooked a very important detail buried in the EPO's video presentation. What was it? Only one of the most sought-after data points related to the HoloLens since its launch: how many have been sold.

It's always a pleasure when your activity syncs across all of your devices. Herein lies another reason to use Samsung Internet — the app natively syncs with your open tabs on desktop Firefox. Anything you do on your computer can be easily accessible from your smartphone.

Now that we've had a chance to jump into the Lumin SDK documentation at Magic Leap's Creator Portal, we now have much more detail about how the device will function and utilize software than any single piece of content released by Magic Leap to date.

Setting up a new Android phone can be a pain. Although Google has some automated features, it does not restore everything. When it comes to transferring certain types of data like files and SMS logs, it's even trickier. By following our steps, you can be sure that you all your data will follow you to your new device.

If you installed Android 9.0 Pie, you might have enjoyed trying out some of the new features in the latest version of Google's OS. However, change isn't always a good thing, so you might be wishing you could downgrade back to Oreo right about now. Good news — you can.

It seems like each day new rumors and leaks come out for Huawei's upcoming P series devices. Everything from its name change to its specs has been leaked, sometimes with contradicting rumors. One of the biggest leaks is the inclusion of triple rear cameras, a first for smartphones.

No smartphone is immune to software issues, even one as advanced as the Galaxy S9 and S9+. Bugs can be caused by a multitude of issues, such as third-party apps that just refuse to play well with your device's OS. Thankfully, there's a simple way for you to check if your S9's bugs are due to uncooperative apps.

With Nokia's relaunch, the iconic company attempted to reimagine the budget phone market. The series of phones they introduced last year challenged the idea that good phones can't be cheap. This year, Nokia introduced the Nokia 7 Plus, a phone which offers perhaps the best balance of specs, software, and price.

Ever since Google CEO Sundar Pichai took the helms of the world's most valuable brand, he has made it his mission to bring smartphones to lower-income communities. Born in India, Mr. Pichai has created several programs to address the needs of the Indian market, particularly the lower income families.

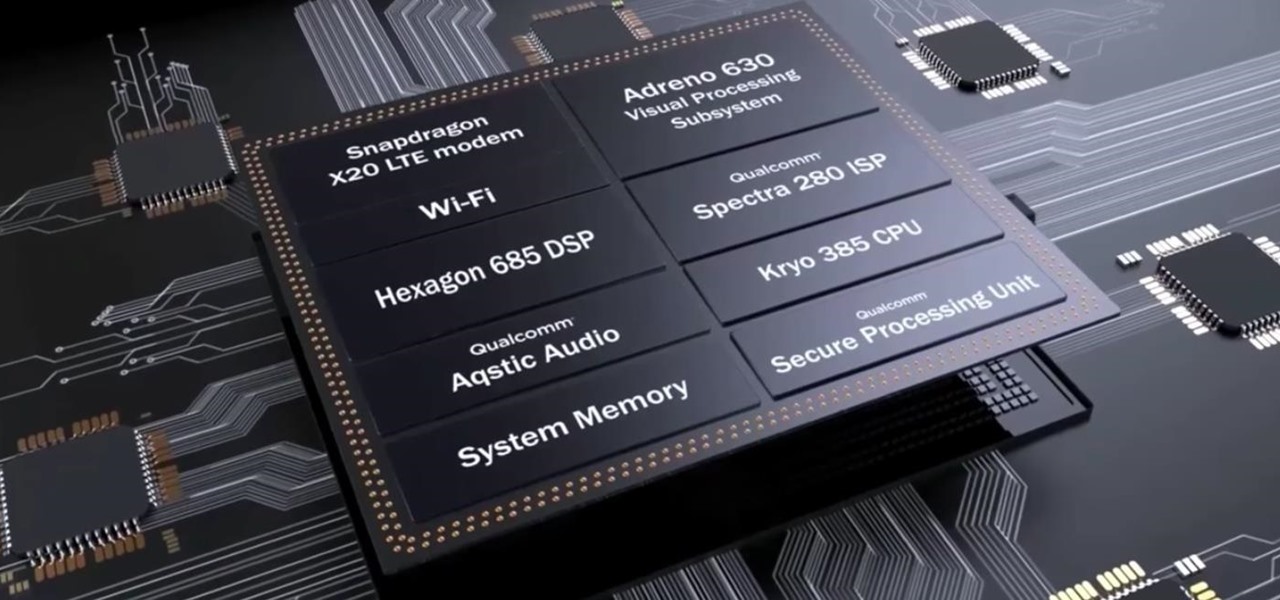
After the success of the Snapdragon 835, Qualcomm now has its eyes set towards the future with the arrival of its next-generation SoC, the Snapdragon 845. Debuting alongside the Samsung Galaxy S9, the 845 is now set to take over the market for flagship Android phones in 2018.

The day has finally arrived — Samsung has unveiled the Galaxy S9 and S9+. Apart from minor upgrades, the two might not appear to be much different from last year's S8 and S8+, but that's not necessarily a bad thing. One feature that hasn't changed is the Galaxy's IP68 water-resistance rating. That's a great score, but it begs the question — what does that number really mean?

A very low-key update to the ARCore developer's site has expanded the universe of officially-supported devices for Google's augmented reality toolkit to include the Samsung Galaxy S7, S8+, and Note 8 handsets.

Security-minded users can reduce the risk of phishing by enabling Advanced Protection on important Google accounts, requiring a U2F security token to log in. Using these keys isn't intuitive on most popular smartphone platforms, and you can find yourself locked out if you don't plan ahead. You'll need to learn and practice using U2F keys on your device before enabling this layer of security.

The first developer preview build of Android P (Android 9.0) is right around the corner, but less than 1% of Android phones are running Oreo. The fragmentation on Android (the number of devices on different versions of the operating system) is staggering, and a problem that has plagued the operating system since it first debuted in 2008 — despite Google's best efforts to fix it.

One thing that makes Apple great is the connectivity between its products. Many tasks you do on an iPhone can be switched over to a Mac or iPad quickly and easily. The Notes app is no exception to this advantage, but you need to make sure you're set up so that your notes sync properly on each device you have.

Coming into this year's Consumer Electronics Show (CES), the common sentiment among observers was that this was expected to be the big year for augmented reality.

Koadic allows hackers to monitor and control exploited Windows systems remotely. The tool facilitates remote access to Windows devices via the Windows Script Host, working with practically every version of Windows. Koadic is capable of sitting entirely in memory to evade detection and is able to cryptographically secure its own web command-and-control communications.

BlackBerry's focus on secure software and their new partnership with manufacturer TCL are two of the biggest factors in their recent resurgence. Last year, the company announced two new devices — the KEYone and the BlackBerry Motion. The KEYone has been available for a while, but after months of waiting, BlackBerry announced the Motion will hit US shores in a few days.

Whether you're watching Netflix on your Android tablet, smart TV, or computer, the process for changing how subtitles and closed captioning appear is the same. Plus, when you customize the font, size, color, and the background, all devices connected to your Netflix profile will update — except for iOS and tvOS devices. A different process is necessary for an iPad, iPhone, iPod touch, or Apple TV.