
News: Nokia 9 PureView Leaks & Rumors
Update February 25: The Nokia 9 PureView was announced at Mobile World Congress! Read all of the official specs and details at our full rundown of Nokia's latest flagship.


Update February 25: The Nokia 9 PureView was announced at Mobile World Congress! Read all of the official specs and details at our full rundown of Nokia's latest flagship.

After finding and monitoring nearby wireless access points and devices connected to them, hackers can use this information to bypass some types of security, like the kind used for Wi-Fi hotspots in coffee shops, hotels, and in flights high above the ground. By swapping their MAC address for that of someone already connected, a hacker can bypass the MAC filter and connect freely.

With Nokia's relaunch, the iconic company attempted to reimagine the budget phone market. The series of phones they introduced last year challenged the idea that good phones can't be cheap. This year, Nokia introduced the Nokia 7 Plus, a phone which offers perhaps the best balance of specs, software, and price.

Continuing our series on building a dynamic user interface for the HoloLens, this guide will show how to rotate the objects that we already created and moved and scaled in previous lessons.

When your iPhone is being sluggish, one thing you can do to get performance back up to snuff is clear the device's random access memory. It's not a publicized feature from Apple, but it's there nonetheless. And while it's easy enough to utilize on iPhones with Home buttons, the iPhone X is a little trickier.

Samsung hopes to make a splash with the new Galaxy Note 9 to make up for the underwhelming sales of its signature Galaxy S9 series. This flagship is a radical departure from its predecessors — it's now optimized for gaming and paired with the most advanced S Pen stylus to date. Here's everything you need to know.

Recently, iPhone users have been bragging that they can set Live Photos as their lock screen wallpaper. While this is a great way to spice up a boring lock screen, Android users shouldn't feel left out in the cold. The highly customizable and feature-rich OS has a few tricks up its sleeve too, and it's really easy to set any GIF as your Android's home screen and/or lock screen background.

Millions of travelers pass through airports each day without understanding how powerful and insecure a boarding pass can be. Anyone can scan the boarding pass barcode with a mobile app, allowing access to frequent-flyer accounts and even a passenger's temporary airline account. In this guide, we will explore how hackers scan and decode the information contained in a boarding pass barcode and why.

Format strings are a handy way for programmers to whip up a string from several variables. They are designed to save the programmer time and allow their code to look much cleaner. Unbeknownst to some programmers, format strings can also be used by an attacker to compromise their entire program. In this guide, we are going to look at just how we can use a format string to exploit a running program.

The reveal of Magic Leap One: Creator Edition brought with it some insight into the path the device took from prototype to "final" design.

Any internet user will need to download files eventually, and most simply have faith that what they are downloading is trustworthy. This doesn't give much clarity into the contents of the file, but if the file's author published the original checksum, comparing it to the SHA-256 hash of the downloaded file can ensure nothing was tampered with.

An attacker with shell access to a Linux server can manipulate, or perhaps even ruin, anything they have access to. While many more subtle attacks could provide significant value to a hacker, most attacks also leave traces. These traces, of course, can also be manipulated and avoided through methods such as shell scripting.
Root, TWRP, Xposed, Magisk, custom ROMs — before you can have any of these, the first thing you should do is unlock your bootloader. Thankfully, the Pixel 2 and Pixel 2 XL are some of the most modder-friendly phones out there, so you only need to send a single fastboot command to unlock the bootloader.

Steganography is the art of hiding information in plain sight, and in this tutorial, I'll show you how to use Steghide — a very simple command line tool to do just that. In addition, I'll go over a bit of conceptual background to help you understand what's going on behind the scenes. This is a tool that's simple, configurable, and only takes a few seconds to hide information in many file types.

When it comes to streaming services, Google Play Music is one of the best options for both Android and iOS. Perhaps its single greatest feature is the fact that you can upload as many as 50,000 of your own songs to Google's servers, then stream your library to any device without ever paying a dime.

The default tool for payload generation is MSFvenom, a Metasploit standalone payload generator as well as encoder. This tool is an incredibly powerful tool for payload generation, but it can be difficult and requires a bit of reading for newer users.

Wonder Woman has always been a Halloween and cosplay staple. It's a costume that's both dependable and stylish — just like the Amazon who wears it. This year's reprise with Gal Gadot offers a fresh take on the old standby, with more muted colors, a tougher demeanor, and a decided lack of stars or stripes. Tahnee Harrison from CineFix's DIY Costume Squad has come up with a compromise between the old and new costumes. It's got the cut, styling, and details of Gal Gadot's 2017 costume, but the b...

Some of us woke up at the KRACK of dawn to begin reading about the latest serious vulnerability that impacts the vast majority of users on Wi-Fi. If you weren't one of those early readers, I'm talking about the Key Reinstallation Attack, which affects nearly all Wi-Fi devices.

Code execution in Microsoft Word is easier than ever, thanks to recent research done by Etienne Stalmans and Saif El-Sherei. Executing code in MS Word can be complicated, in some cases requiring the use of Macros or memory corruption. Fortunately, Microsoft has a built in a feature that we can abuse to have the same effect. The best part, it does so without raising any User Account Control security warnings. Let's look at how it's done.

There's no denying that there are some seriously useful new features in iOS 11 for iPhone. But there's also no denying that Apple got a few things wrong with the latest iOS update, as well as left a few important features out.

Apple has something big in store for consumers in 2017 to mark the 10th anniversary of the iPhone. One major surprise is that Apple has decided to forgo on releasing a 7S in favor of a redesigned iPhone 8 and 8 Plus. To further commemorate its 10-year milestone, the Cupertino-based company has released the very exclusive iPhone X, garnering much excitement in the process.

Apple has finally given us a decent file manager in iOS 11. The new "Files" app replaces the not-very-old iCloud Drive app that appeared in iOS 9, but you can still access your iCloud Drive files in the new Files app, as well as files from third-party cloud services. A nice improvement, right?

On the airplane, in the middle of cold and flu season, your seatmate is spewing, despite the clutch of tissues in their lap. Your proximity to an infectious person probably leaves you daydreaming (or is it a nightmare?) of pandemics and estimating how likely it is that this seatmate's viral or bacterial effusions will circulate throughout the plane and infect everyone on board.

Cross-compilation allows you to develop for one platform (like Kali) and compile to run on a different platform (such as Windows). For developers, it means that they can work on their platform of choice and compile their code for their target platform. For hackers, it means we can compile exploit code for Windows from Kali.

In my previous article, I discussed installing and configuring OpenVAS on Kali Linux. Now it's time to start using OpenVAS with the Greenbone Security Assistant to audit networks for security issues. This can be extremely helpful when you are looking for vulnerabilities or misconfigurations in a large number of hosts.

Word games fit perfectly with the on-the-go nature of mobile gaming. They're easy to pick up whenever you feel like exercising your brain, but they're also fairly easy to put down when you need to get back to the real world.
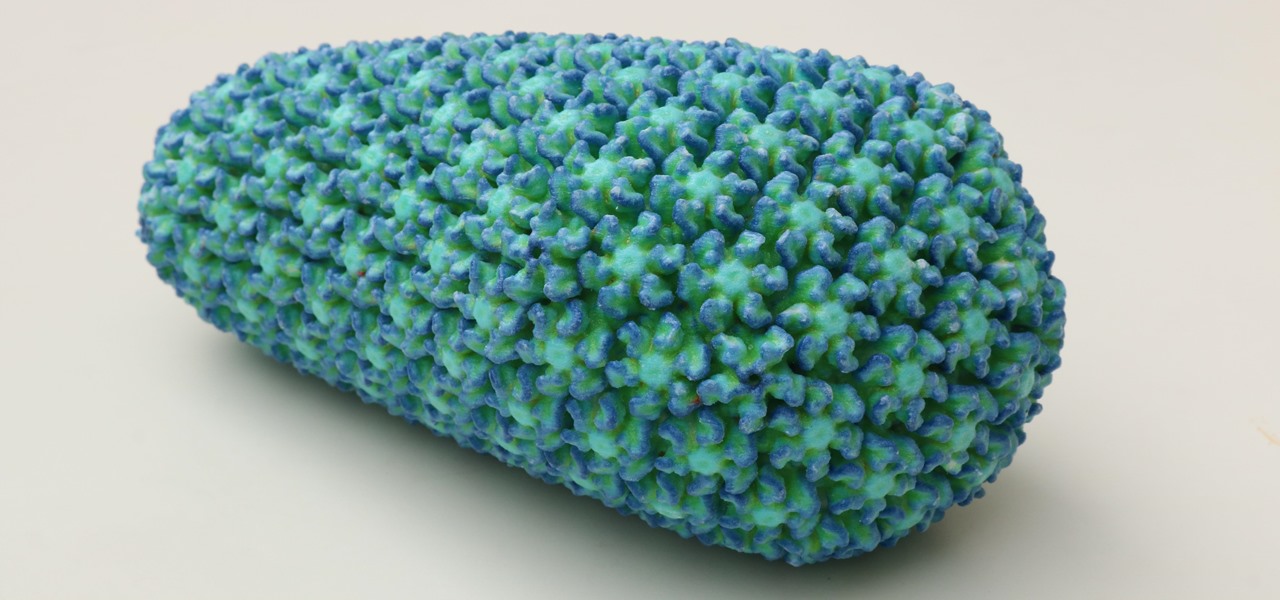
While some researchers look for drugs to treat HIV, other scientists delve deep into the virus itself for answers on how it causes infections.

The Operative Framework is a powerful Python-based open-source intelligence (OSINT) tool that can be used to find domains registered by the same email address, as well as many other investigative functions. This reconnaissance tool provides insight about your target through examining relationships in the domains they own.

Type 1 diabetes is an attack on the body by the immune system — the body produces antibodies that attack insulin-secreting cells in the pancreas. Doctors often diagnose this type of diabetes in childhood and early adulthood. The trigger that causes the body to attack itself has been elusive; but many research studies have suggested viruses could be the root. The latest links that viruses that live in our intestines may yield clues as to which children might develop type 1 diabetes.

Keystroke injection attacks are popular because they exploit the trust computers have in human interface devices (HIDs). One of the most popular and easily accessible keystroke injection tools is the USB Rubber Ducky from Hack5, which has a huge range of uses beyond simple HID attacks. The USB Rubber Ducky can be used to attack any unlocked computer in seconds or to automate processes and save time.

The release of Unity 5.6 brought with it several great enhancements. One of those enhancements is the new Video Player component. This addition allows for adding videos to your scenes quickly and with plenty of flexibility. Whether you are looking to simply add a video to a plane, or get creative and build a world layered with videos on 3D objects, Unity 5.6 has your back.

Think of the coolest, most unique way to create art that you can. Got it? Now think about creating that art out of living things.

The Samsung Galaxy Note 8 (or Galaxy Note8, depending on how you like it) is one phone which couldn't possibly have bigger shoes to fill. Samsung's latest flagship has officially been announced, so it's time to decide whether not it's capable of filing the void left by the failed Note 7. From the revealed specifications and details, the Note 8 is turning out to be one device worth pre-ordering.

It's official — the newest version of Google's mobile operating system is called Android 8.0 Oreo, and it's in the process of rolling out to many different devices. Oreo has plenty of changes in store, ranging from revamped looks to under-the-hood improvements, so there's tons of cool new stuff to explore.

While its direct-selling model echoes brands like Avon and Tupperware, Indonesia's MindStores gives the approach a modern twist—with augmented reality.

Bitcoin continues to make chaotic waves in the finance industry, with one bitcoin currently worth about $1,250 as of this writing. What's great about bitcoin is that you don't need to shell out rent money to get in the game, because bitcoins can be bought in increments—basically, whatever you can afford.
Long before Apple and Android became household names, Nokia dominated the mobile industry. The Finnish company was one of the first to develop smartphones, and their classic N95 with 2G "high-speed" internet connectivity was declared the "best smartphone ever" by some in 2007. Outside of the US, before the iPhone became all the rage, owning a Nokia phone was a status symbol akin to wearing a Rolex or Omega watch.

Not only has there been difficulty finding consensus on a name for driverless, autonomous, self-driving, or automated vehicles, there is also the issue of what we actually mean when we say a vehicle is self-driving, automated, and so on.

To shine light on the future of the relationship between humans and viruses, a team of researchers from the University of Oxford looked into the dim and distant past.

A terrifying antibiotic-resistant superbug, one thought to only infect hospital patients, has made its debut in the real world. For the first time ever, the superbug carbapenem-resistant Enterobacteriaceae (CRE) infected six people who hadn't been in or around a hospital in at least a year, and researchers aren't sure how they got infected.