If you live with pets, you know where their tongue has been, yet you let them kiss and lick you all they want without even thinking twice about it. I've heard people say that a dog's mouth is very clean, and that their saliva, delivered by licking, can help heal wounds, but is that really true?
With any continuously active software, it can start to become fairly complex after a few years of updates. New features and revisions both get layered into a thick mesh of menu systems and controls that even pro users can get bewildered by. If you are new to a certain application after it has been around for many years, it can be downright intimidating to know where to begin.

When it comes to modifying Android, the single, most powerful tool available is TWRP custom recovery. It's even more capable than simple root access when it comes to changing the look and feel of your software, and you can even use TWRP to root your device in a few simple steps.

I've been an Android user almost as long as the operating system has existed, so when I received my first iPhone in April, I felt like I was in a foreign land. Sure, it runs most of the apps I'm used to, and the phone itself feels about the same in my hand as any similarly-sized device, but everything else is just different.

I'm an Android user. Over the course of the past seven years, I've owned ten different smartphones—all of them powered by Android. This isn't due to some blind trust in Google or some unfounded hate for Apple, either, because I've always made sure to get my hands on each iPhone iteration along the way to see what it had to offer.

Welcome back, everybody. In the previous article, we covered the ideas and concepts of well-known ports and trust exploitation in order to evade a firewall. Today, we'll be building the shell, the part that receives commands, executes them, and sends the output back to the attacker.
Hey everyone. Only found the site a few days ago but really loving it. Been

Welcome to the final tutorial of the series on standard C. This article will cover the linked list abstract data type (ADT). There will be a lot of abstraction to try to deliver the understanding in the most basic way for easiest interpretation of what they are and how they work, then we will get into the guts of it and learn the technical code underneath. For those who have yet to grasp the concept of pointers, it's advisable that you do that first before approaching this. Having learned thi...

Greetings my fellow aspiring hackers, It's still Christmas and we have a lot of things and hugs and kisses and ... to share ( you know the things that you do ). I have never done this before but I just felt to encourage you on the quest for knowledge, security and defence, skills and a whole lot more that comes out as a result of pursuing hacking. What we mean by hacking on this forum is White hat Hacking and OTW has great articles on it and I don't need to explain myself on that one.

This year, Google released two Nexus phones to glowing reviews, and as we've grown to expect, the Android community wasted no time in coming up with a root method for both. In fact, legendary root developer Chainfire even devised an entirely new "systemless" method for rooting that should make updating a bit less complicated, along with a few other benefits.

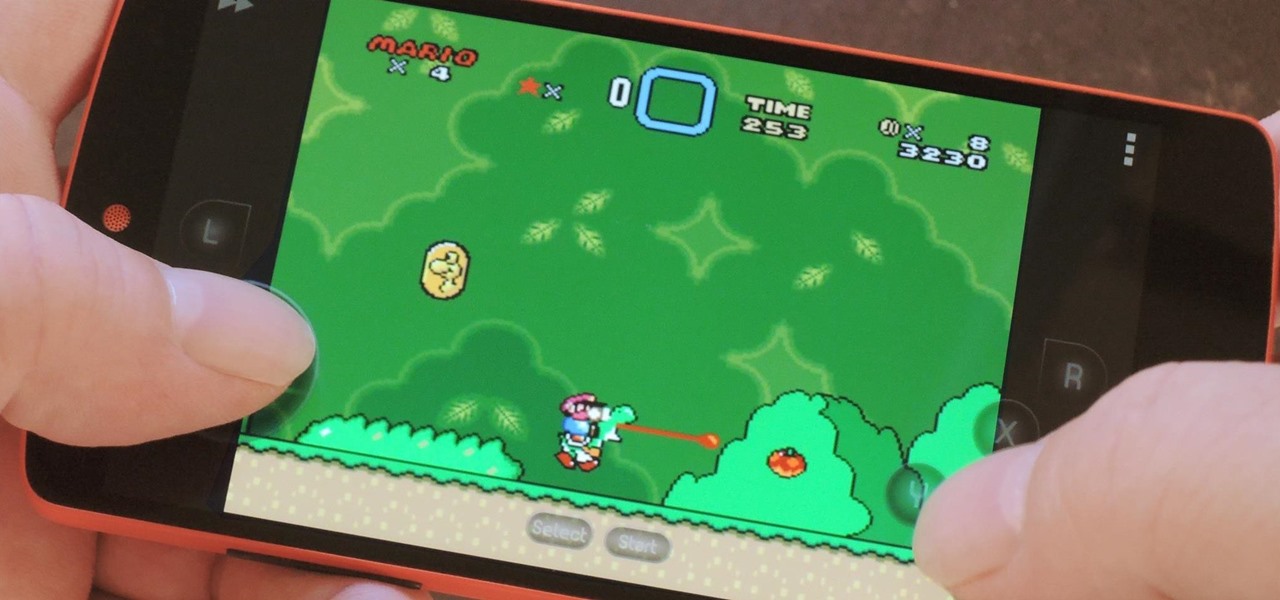
Smartphone games are getting pretty good these days, but they still can't beat the retro appeal of a good emulator. I mean, who wouldn't want to have their all-time favorite console and arcade games tucked neatly in their front pocket? Classics ranging from Super Mario Bros. to Pokémon can all be played at a silky-smooth frame rate on today's devices if you can just find a good emulator to run them on.

We are most certainly not machines. We all need some downtime every once in a while to set our sanity scales back in balance, which in turn, makes us more productive workers. This is a premise that several forward-thinking employers fully understand, but these types of companies are few and far between in corporate America.

As we're all aware, recon is vital to a successful hack. We need to know everything we can about the target in order to perform the best possible attack. Port scanning is a basic recon concept that is introduced very early in learning proper reconnoissance. The issue with port scanning is that is makes a lot of noise. Every connection to every port will be logged. This is where stealth scanning comes in. Also known as SYN or half-open scanning, stealth port scanning is a bit quieter, and is l...

There are over 1.6 million apps on the Google Play Store, which makes it the largest collection of mobile apps on the planet. However, a large portion of this total is occupied by apps with overlapping functions—think social media, news, weather, music players, and various other categories where developers compete against one another to garner the largest user base.

I have a personal rule when it comes to an app's interface: If it doesn't follow Android's design guidelines, it was probably written with Apple's iOS in mind first and foremost.

This is a short explanation and tutorial on how to grab saved passwords from Google Chrome, ideally from a meterpreter session. The idea behind this is to understand how saved passwords work and how to keep them safe. Let's have some fun :D Understanding Google Chrome Saved Passwords

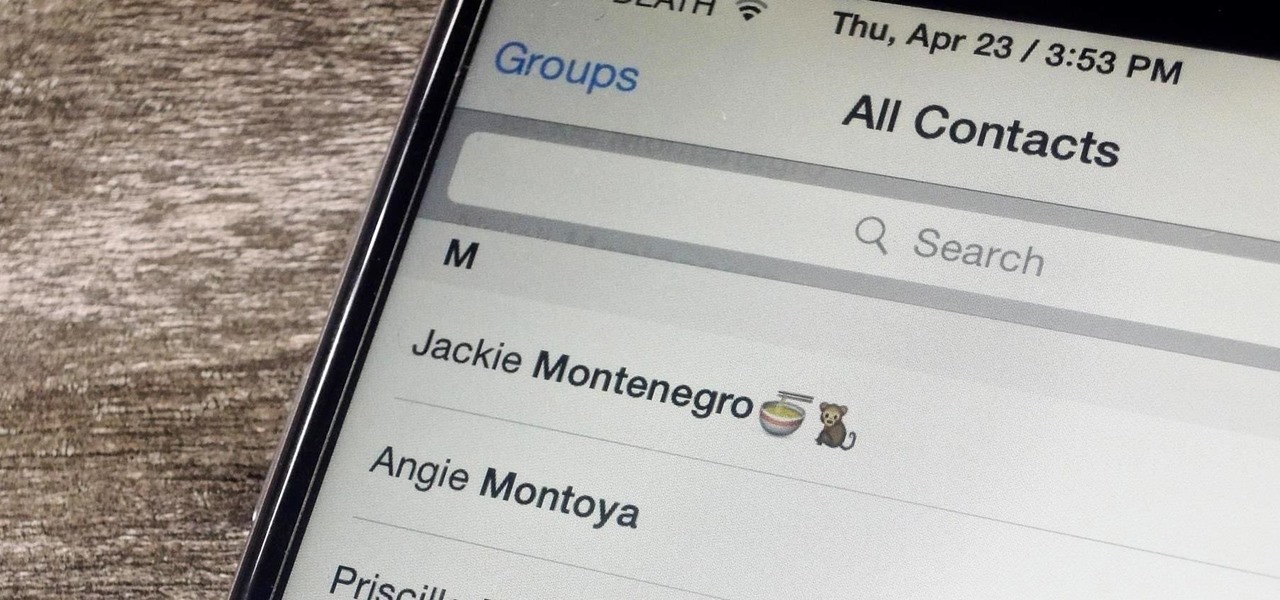
Organizing contacts is a bitch, especially on the iPhone. Some contacts will have multiple entries, you can only delete contacts one by one, and certain types of contacts can't be deleted at all. If that isn't enough to make you pull your hair out, then I don't know what will.

While the Apple Watch does have up to 18 hours of battery life each day on a full charge, your results will vary depending on how often you use it and what you're actually doing with it.

Welcome back, my tenderfoot hackers! As hackers, we often are required to get past antivirus (AV) software or other security measures. To do so effectively, we need to have some understanding of how AV software works. In this tutorial, we will take a cursory view of how AV software works so that you can better strategize on how to evade detection by it.

In this simple tutorial you will be shown step-by-step how to write local shellcode for use on 64-Bit Linux systems. Shellcode is simple code, usually written in assembly that is used as payload in exploits such as buffer overflow attacks. Payloads are the arrow head of an exploit: though the rest of the arrow is important for the delivery of the attack, the arrow head deals the killing blow. In reality, payloads are slightly less exciting yet far more interesting and intelligent than medieva...

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

In order to make your food taste good, your favorite restaurant is most likely using way more salt than you think they are (among other pro secrets). Which is why when you ask just about any professional cook what the biggest problem with most home-cooked meals are, they almost always answer that they're "undersalted" or "underseasoned." (In cooking lingo, to "season" food means to salt it.)

My years in the restaurant business have taught me many things. Some of those things are best left unsaid and other things require a PhD in vulgarity, but the one thing I learned that I keep coming back to night after night is that you do not have to spend a lot of money to drink excellent wine. This is especially true of champagne...I'm sorry, sparkling wines.

Sometimes it's hard to remember that lasagna, pizza, cannoli, and other dishes are actually Italian in origin; they're so much a part of the American culinary landscape at this point. Wherever they come from, Americans of all kinds love to eat 'em. This guy was released from a North Korean prison, and after two years, the first thing he wanted to eat was fast-food pizza.

We've already seen the visual changes that Android 5.0 Lollipop has brought to the table, but Google spent just as much time altering things under the hood. Awesome new functionality and hardware capabilities have been added left and right, and with the OS already out now, it's high time we had a look at some of these tweaks.

The release of iOS version 8.1.1 brought some much needed bug fixes to Apple's mobile operating system, but with it came a patch for Pangu's jailbreak method, which worked on iOS 8.0 to iOS 8.1 using a Mac or Windows computer. Luckily, it didn't take very long for a new team of developers to come up with a method for jailbreaking iOS 8.1.1 devices, and much like its predecessor, the process is a cinch.

I am an English major physically allergic to all algebraic formulas, so you're unlikely to get any help from me when it comes to solving any expressions. But in the glorious technological age we live in, there are plenty of apps that actually make math and problem solving fun, even a little bit addictive.

It seems like every day now that we see a new headline on a cyber security breach. These headlines usually involve millions of records being stolen from some large financial institution or retailer. What doesn't reach the headlines are the many individual breaches that happen millions of times a day, all over the world.

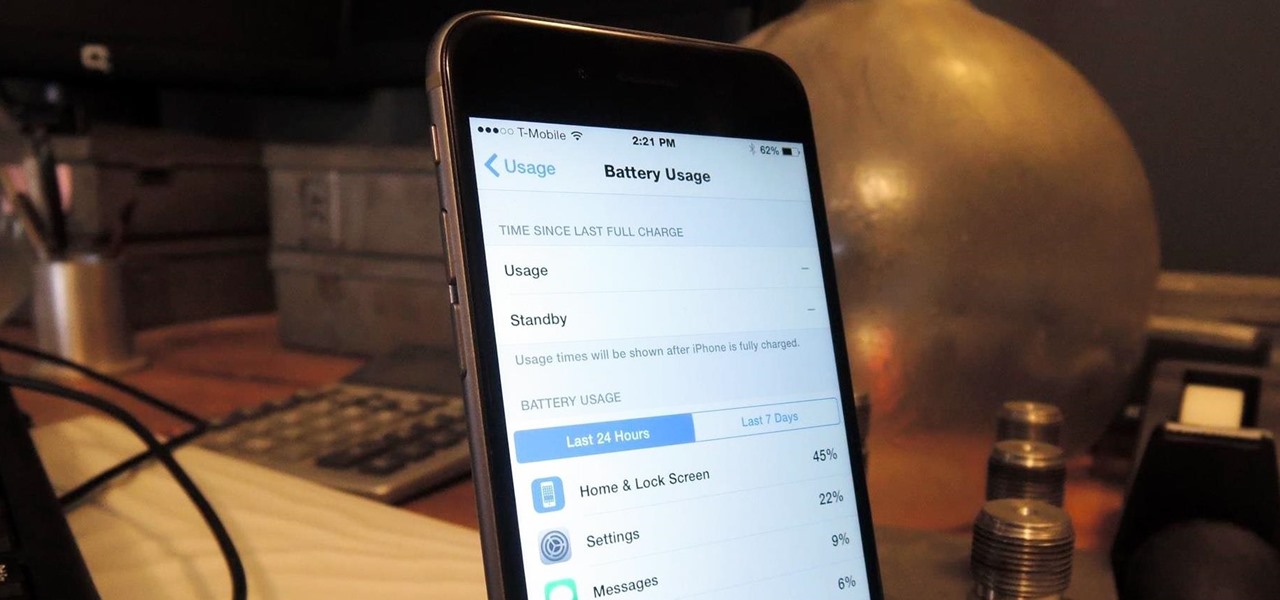
The new iPhone 6 and 6 Plus are supposed to last a lot longer in your pocket with improved battery life, but that doesn't mean that iOS 8 will be that friendly on your older iPhone model. All of those awesome new features could be killing your battery, but with some simple tweaking, your battery life concerns will be a mere afterthought.

French toast is one of those things that everybody kind of knows how to make, but few people know how to do really well. And while the dish originally does hail from France (its original name, pain perdu, means lost or wasted bread), it has become a beloved American breakfast dish.

Aluminum foil is one of those things that every cook, experienced or just starting out, has in their kitchen. And while we may think we know how useful this handy material can be, there are hundreds of ways we could be utilizing tinfoil to make our lives a whole lot easier.

Welcome back, my novice hackers! Reconnaissance is one of the most important preparatory steps to hacking. As I have emphasized many times before here on Null Byte, you must know the operating system, the ports, the services, the applications, and sometimes even the language of the target to be effective. If you haven't taken the time to gather this info, then you are likely wasting your time.

If you've ever owned an HTC device or anything in the Nexus line, odds are, you have typed the word "fastboot" into your command line at one time or another. That said, odds are, you have only just barely scratched the surface of what this handy little Android tool can do. Let's take a deeper look.

The beauty of a grilled cheese sandwich is that even a mediocre one still tastes pretty good (I find the same is true with pizza). However, chefs and cooking pros have come up with some great tricks that will turn a regular grilled cheese sandwich into something sublime.

Go to a chain supermarket, and chances are you'll see one type of garlic—maybe two or three if you're lucky. However, there's a mouthwatering slew of Allium sativum out there, far beyond those papery white bulbs most of us encounter at the nearest Stop 'n' Shop.

People who know that I am a professional hacker often ask me what they can do to make their computers and personal information safe from people like me. The answer, of course, is that nothing will make you completely safe, but there are a number of measures any computer user can take to reduce the chances of being a victim of a hacker.

For the novice cook, fungi can be weird because, well, they're fungi. However, if you've been afraid to get acquainted with mushrooms, you've been missing out. Vegetarians love mushrooms and with good reason.

Welcome back, my neophyte hackers! I have already done a few tutorials on password cracking, including ones for Linux and Windows, WEP and WPA2, and even online passwords using THC Hydra. Now, I thought it might be worthwhile to begin a series on password cracking in general. Password cracking is both an art and a science, and I hope to show you the many ways and subtleties involved.

The microwave oven is a monumental technological achievement that's saved college students and single people from starvation for decades. Almost 97% of all American households have one, which makes it the most-owned kitchen appliance in US homes right after the refrigerator.

Foodies and big-time chefs like Thomas Keller go crazy for fleur de sel. This finishing salt appears in fancy eateries and cookbooks the world over, and in the early 2000s, it was not uncommon to see diners in a high-end restaurant sprinkle a pinch of fleur de sel on their plates from their own personal stash.