This video is about a particular pool or snooker game shot technique called "Shooting or Going around the Angles." The presenter, with a alias name of 'Forcefollow', first describes a particular 9-ball pool game situation that would require this technique, using a computer generated picture image to show an overhead view of the pool table, with the pool balls in question placed at certain locations within the table and showing the various angle trajectories paths of the desired ball to be str...

This crochet how-to video is a quick demonstration on color stranding using single crochet. Watch as our host shows you how to practice color stranding on his single crochet hat.

Get a new perspective on computing with an HP Tablet PC. HP's Tablet PCs are well-equipped personal notebooks, with a significant twist. The display turns around one hundred and eighty degrees, transforming your notebook into a flat tablet touchscreen PC.

There's a tool on your iPhone that can help you with your overall emotional well-being, one that can help you be more aware of your emotions throughout the day and build resilience against the stressors in your life.

One of my favorite perks of this job is the opportunity to try out all the big flagship phones each year. Whether it's rating their suitability for a particular use-case or just entering their specs into our comparison tool, we have to get our hands on all major phones released in the US. We pride ourselves on being fair in our reviews and roundups, but that doesn't mean we don't have preferences.

The newly-announced Moto G7 Play offers some of the same upgrades as its sibling, the Moto G7, but at a much lower price. The upgrades are pretty significant when compared to last year's Moto G6 Play, taking this phone from the "only if you're on a strict budget" category into a great value option.

Ever since the announcement of the Razer Phone, a wave of gaming smartphones started to hit the market. With ASUS being such a big name in gaming, it made sense for them to throw their hat in the ring. The result is the ROG Phone. And with this first try, ASUS has topped the rest, creating a gaming phone others should try to emulate.

Besides the Apple vs. Samsung competition, few battles are as vocal as the battle between the best Pixel and best iPhone. This year, it's the Pixel 3 XL and iPhone XS Max, two phones that are equipped with minor hardware updates from their predecessors, though both showcase significant OS-level improvements.

The battle between the Pixels and the iPhones has been heating up over the last few years, and this year's bout is the best one yet, with Google's Pixel 3 taking on Apple's iPhone XS.

Gmail conversations, Facebook private messages, and personal photos can all be viewed by a hacker who has backdoor access to a target's Mac. By livestreaming the desktop or exfiltrating screenshots, this information can be used for blackmail and targeted social engineering attacks to further compromise the mark.

When hacking Wi-Fi networks, having the right wireless adapter is essential. But hunting online for one can be a frustrating experience. To see how the handful of Kali-compatible adapters on the market measure up, I ran a series of tests to benchmark and compare their range, signal strength, and ability to enter monitor mode and perform packet injection. This should help you determine which adapter is right for your own hacking needs.

Let's face It ... Pennywise is going to be the Halloween costume to beat this year. It's terrifying, simple enough to pull off, and with the original movie's gargantuan box office gross and the hit status of the sequel, released in September, everyone and their pet dog will get your costume.

Food is both a necessity and a joy. Many people enjoy exploring, cooking, eating, and learning about foods from around the world. But the picture isn't always rosy. A new report from the Centers for Disease Control and Prevention (CDC), highlights the ways and whereabouts of food that make us sick.

Social engineering makes headlines because human behavior is often the weakest link of even well-defended targets. Automated social engineering tools can help reclusive hackers touch these techniques, but the study of how to hack human interactions in person is often ignored. Today, we will examine how to use subtle, hard to detect persuasion techniques to compromise a human target.

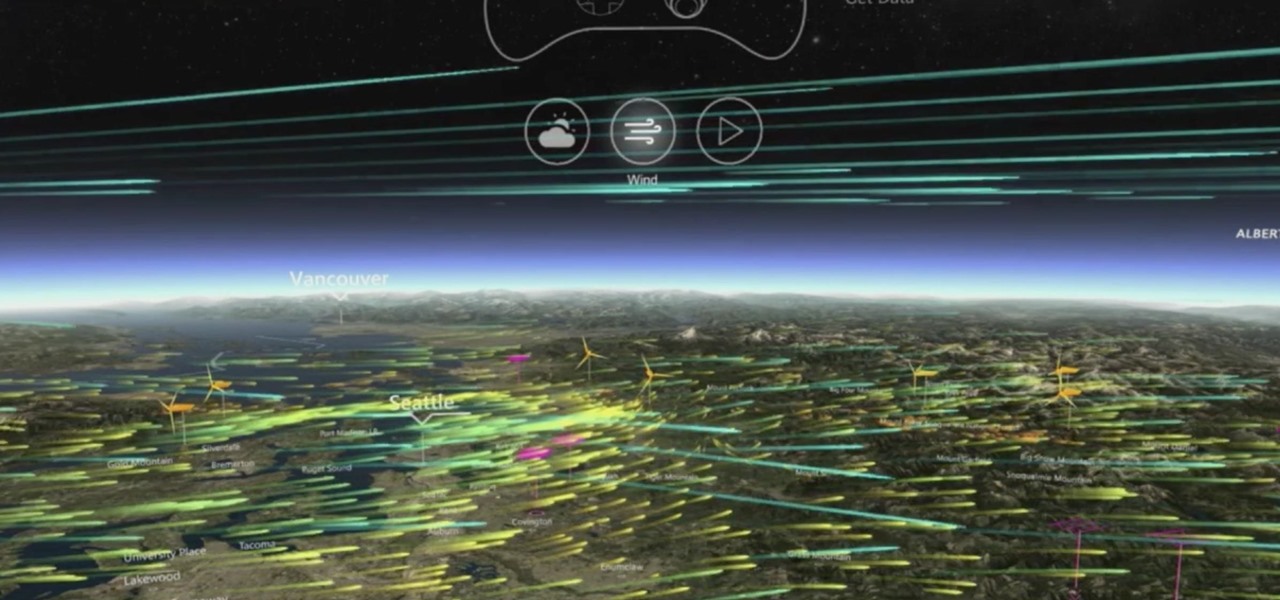
One thing that I got more and more excited about as we got closer and closer to the Microsoft Build 2017 developers conference was finally learning about the new Acer Windows Mixed Reality head-mounted displays (HMD). Brandon Bray, Principal Group Program Manager at Microsoft, had teased us a few weeks earlier at the Vision Summit event in Los Angeles, California, and said there would be a lot more information at Build. Fortunately for us, he was right.

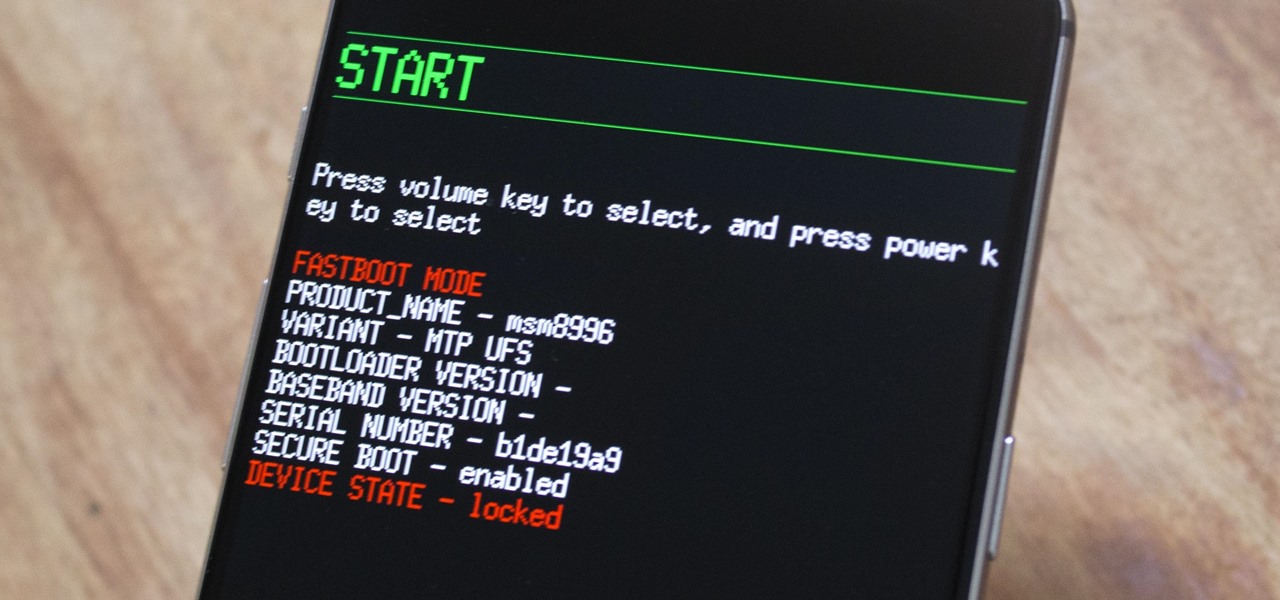
The OnePlus 3 and 3T are two of the most modder-friendly devices to be released in 2016. Not only that, but they're both extremely solid phones which happen to sport a very reasonable price tag. Among the things that make these devices such a joy for tinkerers is the fact that they have an unlockable bootloader, receive timely kernel source releases, and are actually quite easy to root.

Beginners luck is a phrase I have always hated. But really, beginners luck comes down to not letting your experience in something get in the way of the idea.

As exciting as it can be to crack open a beer, there's nothing fun about wandering around a party and asking other partygoers for a bottle opener.

Over the past decade the Internet community has been witness to the rise of many new forms of online interaction. These new technologies have given rise to anonymous networks (like TOR), black markets within the deep web network (like the Silk Road), and even forms of digital currency, or more accurately crypto-currencies, such as Bitcoin. All of these technological advancements have contributed to securing users around the world and protecting their privacy. Therefore it is no surprise that ...

Welcome back, my tenderfoot hackers! In this series, we are exploring the myriad of ways to hack web applications. As you know, web applications are those apps that run the websites of everything from your next door neighbor, to the all-powerful financial institutions that run the world. Each of these applications is vulnerable to attack, but not all in the same way.

Welcome back, my aspiring hackers and those who want to catch my aspiring hackers! As most of you know, this series on digital forensics is inspired by the motivation to keep all of you all out of custody. The more you know about the techniques used by law enforcement and forensic investigators, the better you can evade them.

Welcome back, my novice hackers! This next subject might seem a bit obscure, but I promise you, this lesson will benefit you significantly either as a hacker or system admin. This tutorial will cover what is usually referred to as a regular expression, or regex for short.

TouchDevelop is a browser-based programming tool that allows anyone to build your own Windows 8 apps directly from any touchscreen device, including iPad, iPhone, Windows Phone, Android, PC and Macs. Once the script is created and the app proves to work, it can be placed in the Windows Store for free or purchase.

In order to play the game Risk, begin by setting up. Name a banker. Players choose a color. The number of players determines the number of armies. Remove the jokers from the country card packs. Shuffle the cards. Deal them face down. Players may not get an equal number.

Wouldn't it be nice if you could insert the current date with a single keystroke, like shown in the video? And if it would work in any application? Well, this is possible with PhraseExpress. This video tutorial shows you how to insert the current time or date stamp by pressing a hotkey. This works in every Windows program.

Pixel Perfect is the "perfect" show to help you with your Photoshop skills. Be amazed and learn as master digital artist Bert Monroy takes a stylus and a digital pad and treats it as Monet and Picasso do with oil and canvas. Learn the tips and tricks you need to whip those digital pictures into shape with Adobe Photoshop and Illustrator. In this episode, Ben shows you how to bizarrely merge photos in Photoshop.

Pixel Perfect is the "perfect" show to help you with your Photoshop skills. Be amazed and learn as master digital artist Bert Monroy takes a stylus and a digital pad and treats it as Monet and Picasso do with oil and canvas. Learn the tips and tricks you need to whip those digital pictures into shape with Adobe Photoshop and Illustrator. In this episode, Ben shows you how to create a Times Square billboard in Photoshop.

Watch this instructional knitting video to hang a rag hem on your knitting machine. Add weights to the inside of the knitted hem to keep your knit work straight. You will need a single pronged tool or a three pronged tool. If you knit with a knitting machine, this is an essential trick for getting started with larger projects.

Sandy from Afloral.com shows you how to make a flower corsage with this floral arrangement tutorial. Learn how to create a single, double, and triple flower corsage. These corsages are perfect for a wedding, prom, or any formal event. Watch this how to video and you will be making your own flower corsages in no time.

In this floral arrangement tutorial, Sandy from Afloral shows you how to create a boutonniere. Learn how to create a single, double and triple flower versions of the boutonniere. Watch this how to video and you can create your own boutonniere at home.

Confused by all the crocheting abbreviations? Then watch this how to video tutorial to learn common symbols and abbreviations used for crochet. Get your double, single, and triple crochets symbols down.

In Texas Throw 'Em 2, Chris ups the ante by cutting multiple carrots with a single card.

This video shows one how to paint a cherry blossom in the Sumi-e technique of painting in ink with a single brush.

Watch this Japanese ink painting demonstration to learn the technique used to draw bamboo with sumi-e ink. Create bamboo using straight strokes. Five leaves are drawn with one single brush of ink.

The double paradiddle is a fun rudiment that is based on the single paradiddle. It is a 12 note pattern that is often used in a 12/8 feel, or in beats and fills with a triplet feel. This triplet feel makes it perfect for Jazz, Latin and other world styles.

Carrie Leshin MS, Speech Pathologist tells you that if a child is not saying single words by the age of 18 months, at least 50 words, a parent should start being concerned.

This video demonstrates how to make a parrot from a single piece of paper. Set to some jazzy music, the demo seem to go by quicker than the published 10 minutes. The resulting 3D creation will sit on your finger like a live parrot only without the mess.

When is a knot not a knot? When it's a grip. The knot outlined in this video isn't a knot per se but a way to wrap objects to increase their grip and also to store extra paracord. Specifically, this video demonstrates how to County Comm Micro Widgy Bar, which is a miniature pry bar. It’s made from hardened D9 steel and is around 3? in overall length.

This dish is perfect for dinner for two. You need two beef tenderloin fillets with the silver skin cut off, ½ package of phyllo dough, 8 oz of mushrooms, 1½ cup green onions, 2 tbsps of olive oil, 1 tbsp of butter, ¼ cup of parsley, and 2-3 tsps of lemon juice, salt and pepper, Hollandaise sauce. Pan fry the beef for a minute or two on each side if you like it more well done. For the mushroom filling, use fresh mushrooms. Chop up the mushrooms finely. Chop up green onions. Use a little bit of...