In the not-so-distant past, cloud computing was thought of primarily in terms of online storage platforms. Now, however, massive cloud infrastructures are used by virtually every major business to reach clients, manage data, and deliver services.

Fake news was one of the main driving factors for Google News taking its current form. It offers verified sources to ensure more accuracy in your news feed to help control the spread of false information. Something you may not know, however, is that you can view your favorite Google News topics from your home screen with a single tap.

We are now in the age of 5G. Carriers worldwide are upgrading their networks to the newest standard for mobile, which will dramatically improve your phone experience. How? By giving it download speeds and latency that surpass Wi-Fi. But before you upgrade, there are few things you should know first.

Working from home is going to be a reality for more people than ever. With Twitter CEO Jack Dorsey announcing that his employees will be working remotely for an extended period of time (and even permanently, in some cases), the workforce is rapidly changing. More companies are certain to follow suit.

In 2018, Niantic unveiled its in-development augmented reality cloud platform for smartphones, the Niantic Real World Platform. A demo showed Pikachu and Eevee cavorting in a courtyard, darting in front of and behind potted plants and people's legs as they walked through the scene. This would be the future of Pokémon GO.

From booting into Fastboot mode with a single command to installing mods without root access, there's no shortage of reasons to use ADB. The catch, though, you had to be tied to a computer with a USB connection. However, a new feature in Android 11 finally allows you to run ADB commands over Wi-Fi instead of being tethered.

After many years of rumors, the second-generation iPhone SE is here. At $399, it is the most inexpensive iPhone Apple has sold since the original iPhone SE came out. And while the new SE comes with Apple's typical five-watt power adapter, the smartphone supports fast charging — you just need to get a fast charger separately.

It's exciting to get that reverse shell or execute a payload, but sometimes these things don't work as expected when there are certain defenses in play. One way to get around that issue is by obfuscating the payload, and encoding it using different techniques will usually bring varying degrees of success. Graffiti can make that happen.

Hacking web applications can sometimes be challenging due to the sheer amount of moving parts they possess. At the core of these apps are HTTP requests and parameters, but these things are often concealed from the user, due to security reasons, convenience, or both. However, a tool called Arjun can be used to discover hidden HTTP parameters in web apps.

Determining the antivirus and firewall software installed on a Windows computer is crucial to an attacker preparing to create a targeted stager or payload. With covert deep packet inspection, that information is easily identified.

Hey, you, still stuck at home? Cheer up, today is the first day of spring. Yes, really. And since you're probably locked in on TV, we're guessing you need a break from some of the less than sunshiney news reports rolling in. Well, no worries, because there's actually some good news to report.

With the Galaxy S20, Samsung has officially removed the Bixby button from its flagships. While it was a controversial key, in its later days, it did give us the ability to launch an app or custom action at the press of a button. There's still a way to do something like that, but now, you'll have to use the power button instead.

The biggest new feature in Android 10 is the system-wide dark mode. Both Samsung and Google phones have it, so third-party support is everywhere. The only problem is OnePlus forgot to include a way to quickly toggle dark mode on and off.

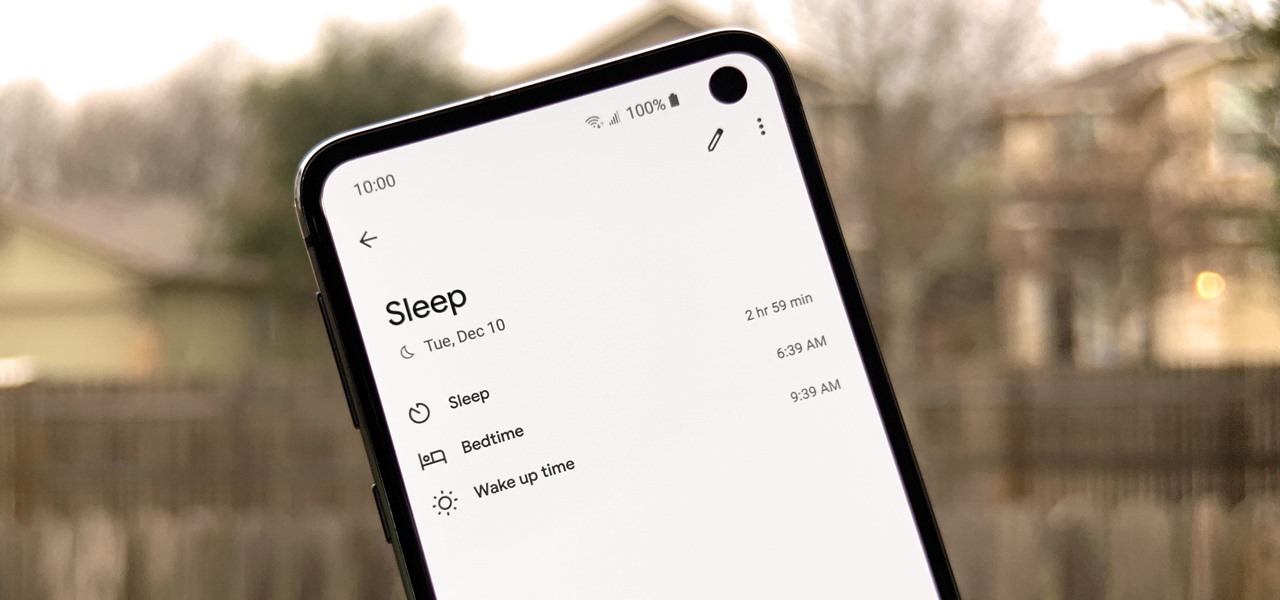
When trying to get fit, something that can easily be overlooked is your overall sleep quality. Your body needs sleep to recharge and it helps to maintain a healthy lifestyle, there's no denying it. Luckily, Google Fit can help you track your sleeping habits without having to jump through any hoops along the way.

For anyone interested in using cheap, Wi-Fi-connected microcontrollers like the ESP8266, the Arduino programming language can be a barrier to entry. Based on C++, Arduino requires knowledge of more computer science than languages like Python. Fortunately for beginners, setting up MicroPython on an ESP8266 allows anyone to write Python on affordable microcontrollers in a matter of minutes.

There are many password-cracking tools out there, but one of the mainstays has always been John the Ripper. It's a powerful piece of software that can be configured and used in many different ways. Metasploit actually contains a little-known module version of JTR that can be used to quickly crack weak passwords, so let's explore it in an attempt to save precious time and effort.

Whether you love Motion Sense or think it's a gimmick, one thing we can agree on is that its functionality is limited. It's currently limited to switching tracks on a playlist, snoozing alarms, silencing calls, lowering the volume of alerts, and checking notifications. But a new mod will help you do so much more with it.

If you want to carry a variety of network adapters without looking suspicious, a perfect solution is accessing them through Airserv-ng. Tucked away in the Aircrack-ng suite, this tool allows a hacker to plug any number of network adapters into a Raspberry Pi and access them over a Wi-Fi or Ethernet connection.

At Next Reality we mostly focus on augmented reality, but that doesn't mean we're not also absolutely obsessed with virtual reality, too. If the thing that's been keeping you from diving into the deep end of VR has been clunky tethered headsets or the expensive but necessary gaming PCs, then it's time for you to try the Oculus Quest, which is currently available to buy here for less than most gaming systems on the market.

Android phones have supported keyboards and mice for a long time, and you've even been able to use physical keyboards with iPhone and iPad models. But iOS 13 and iPadOS 13 finally include official mouse support. That means you can use a wireless or wired mouse and keyboard with your iPhone or iPad, though, a futuristic peripheral that combines the two may be even better.

The streaming content vision from Magic Leap recently underwent a quiet but major update, courtesy of AT&T.

Before smartglasses makers can dream of taking smartglasses to mainstream consumers, they must first determine the right mix of form, function, and price that will drive customers to buy into what they're hoping to sell.

My autistic son loves music. One afternoon, when he was nine, I downloaded GarageBand to his iPhone to help with the boredom of a long wait at a doctor's office. Instead of pacing or escalating into a meltdown, he spent the entire hour and a half practicing, learning, and composing. When we finally left that day, the rest of us exhausted and irritated, he shared his first composition with a big smile.

Ever since the introduction of Google's SafetyNet feature, it's been an ongoing battle with apps trying to detect root access. For a while, there was a lot of back and forth between Magisk and certain apps. Pokémon GO was a high profile example of an app aggressively checking for anything related to root. Luckily, Magisk has made great strides to keep apps from detecting root for good.

Microsoft.com is one of the most extensive domains on the internet with thousands of registered subdomains. Windows 10 will ping these subdomains hundreds of times an hour, making it challenging to firewall and monitor all of the requests made by the operating system. An attacker can use these subdomains to serve payloads to evade network firewalls.

In this era of smartphones, we all know very well how easily we can get addicted to our devices. Spending hours each day doing the endless scroll through Facebook and other social media sites just because we feel like we'll miss something if we don't. Both Google and Apple are aware of this and are trying to help control smartphone addition in their own way for Android and iOS.

For the first time, you can officially use a computer mouse with your iPhone, thanks to Apple's new Accessibility settings in iOS 13. It works for all types of Bluetooth mice, so if you have one, it'll already work. Plus, those with wireless receivers and even wired mice are supported by using a USB to Lightning adapter.

By using almost any packet-crafting tool, a hacker can perform denial-of-service (DoS) attacks. With the power to create just about any packet with any characteristics, a hacker can easily find one that will take down a host or network. Nmap and Hping are effective packet manipulation tools, but there's also Scapy, which is almost infinitely customizable.

Apple's Gatekeeper security software for macOS (Mac OS X) is vulnerable to remote attacks up to version 10.14.5. An attacker that's anywhere in the world can exploit MacBooks and other Mac computers by sharing a single ZIP file.

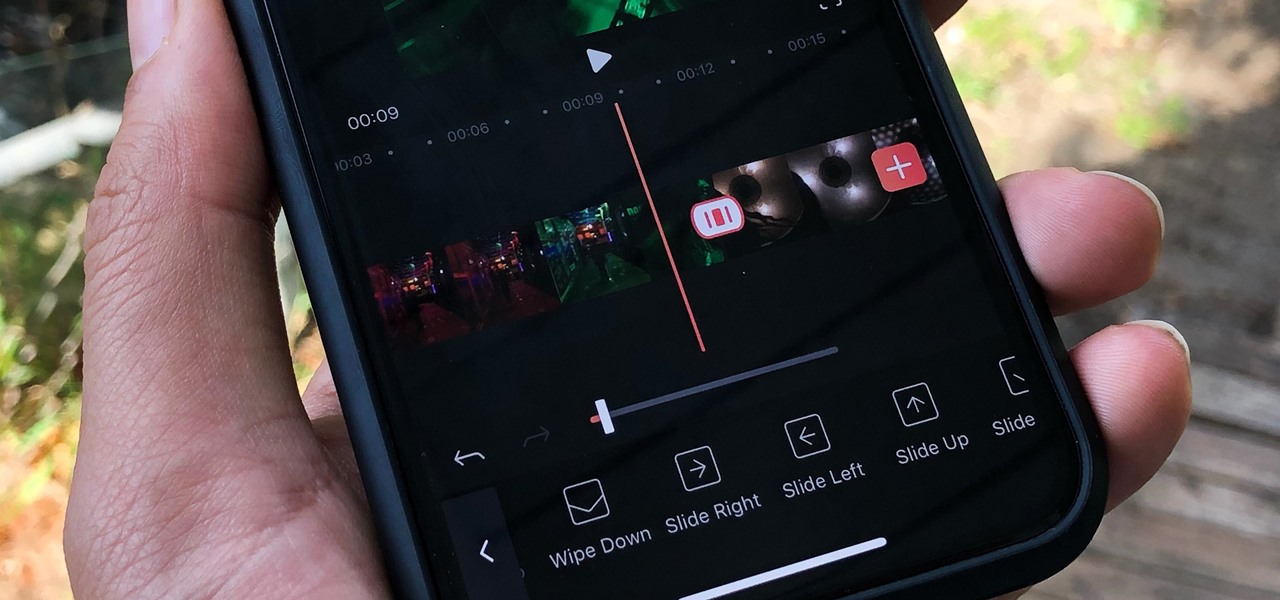
An edited video with lots of different clips needs great transitions to be successful. Transitions support your story and message, and without any, there's always a chance that your audience might lose track of what's going on and when. When editing in Enlight Videoleap for iOS, you can easily add cut, dissolve, iris, wipe, slide, and fade transitions to your video clips with just a few taps.

After reviewing the international plans for major US wireless carriers, it became obvious they're all pretty bad. Your data is heavily restricted, requiring a daily fee which can cost an extra $100+ on a seven-day vacation. That's when I learned about Google Fi, and how for most travelers, it's the best option.

Giving up your Wi-Fi password can be giving up more control than you think. Because of the way Chromecast and other IoT devices communicate, anyone on the same Wi-Fi network as your device can often make it do whatever they want. With a script called "Cast All the Things," we can hijack a Chromecast to play nearly any kind of media with a single command in terminal.

Websites are often misconfigured in ways that allow an attacker to view directories that are not ordinarily meant to be seen. These directories can contain sensitive information such as private credentials or configuration files that can be used to devise an attack against the server. With a tool called Websploit, hackers can scan targets for these hidden directories without difficulty.

Current-generation mobile augmented reality apps offer users numerous opportunities to punch up photos and videos with 3D content, but there's surprisingly few options for users to express themselves using virtual characters.

After months of waiting, it looks like HMD has finally answered the call. Nokia's parent company is finally releasing a true flagship phone — one that isn't just an enhanced version of a previous phone and actually brings something new to the table. That phone is the Nokia 9 PureView.

Every step in the evolution of computing brings an in-kind leap forward in user input technology. The personal computer had the mouse, touchscreens made smartphones mainstream consumer devices, and AR headsets like the HoloLens and the Magic Leap One have leveraged gesture recognition.

Reading the augmented reality news lately has felt a bit like reading a John Grisham novel, as the business side of things has dripped with legal drama.

Augmented reality startup Nreal was a hit at this month's CES event, with some even calling the device a worthy challenger to the Magic Leap One.

In late-2017, Instagram rolled out a feature that automatically saves your ephemeral Stories to a private archive. Before that, Stories disappeared into the ether after 24 hours, but not everyone was comfortable losing these precious photos and videos. If you post to Instagram Stories quite often, you can now easily access your history from your account — and you might not even know it.

When it comes to attacking devices on a network, you can't hit what you can't see. Nmap gives you the ability to explore any devices connected to a network, finding information like the operating system a device is running and which applications are listening on open ports. This information lets a hacker design an attack that perfectly suits the target environment.