Check out this walkthrough Resident Evil 5, Chapter 6-1: Ship Deck. Resident Evil 5 (RE 5) is the sequel to 2005's Resident Evil 4. This game guide shows you BSAA emblem locations, treasures, and includes strategies for all 6 missions and boss fights.

Resident Evil 5 (RE 5) is the sequel to 2005's Resident Evil 4. This game guide shows you BSAA emblem locations, treasures, and includes strategies for all 6 missions and boss fights.

Learn how to play "The Way I Loved You" by Taylor Swift, an acoustic guitar tutorial. Follow along with this demonstration, tabs and lyrics here:

Learn how to play "Why" by Secondhand Serenade, an acoustic guitar tutorial. Follow along with this demonstration, tabs and lyrics here:
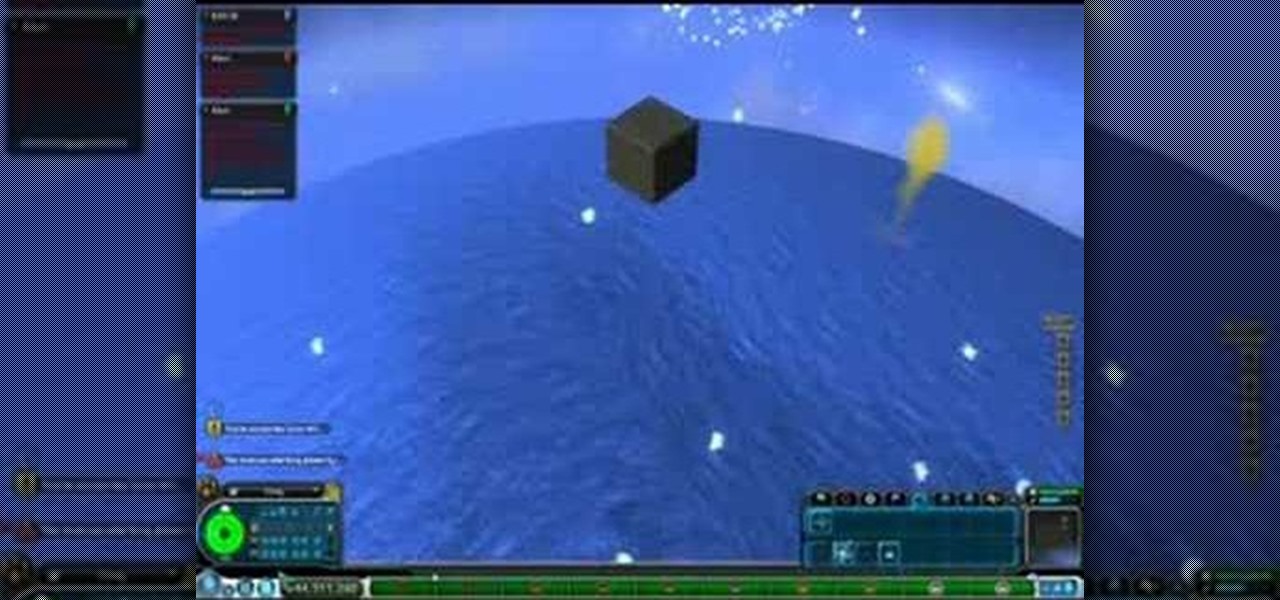
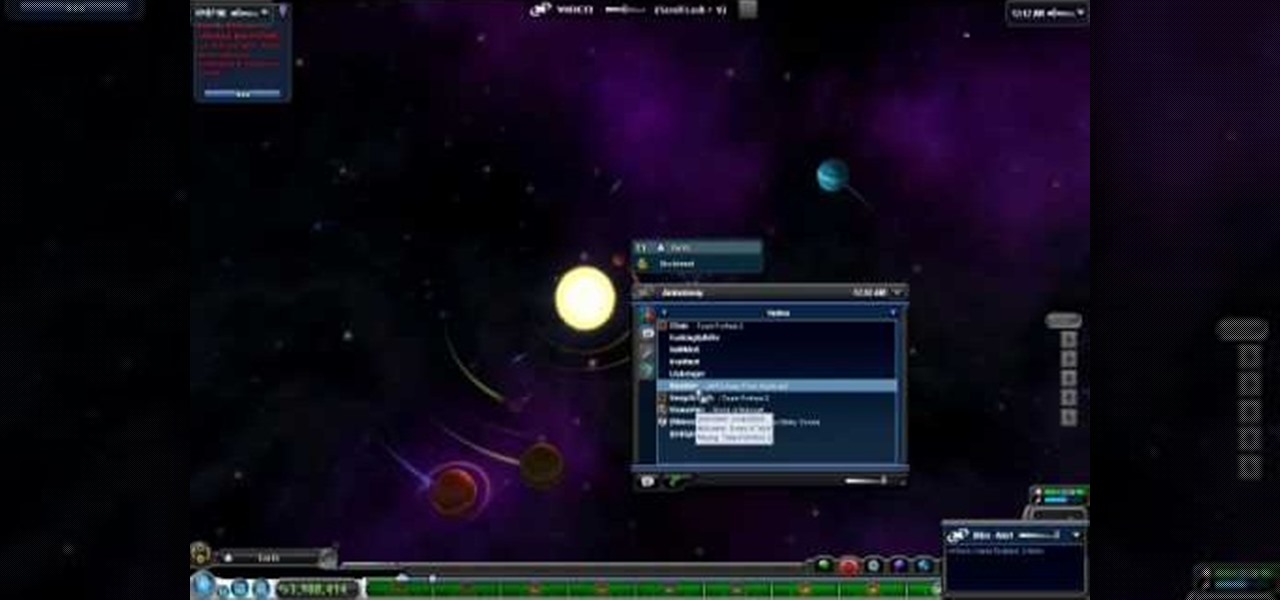
This walkthrough and cheat shows how to use the Staff of Life to turn a barren planet into a T3 planet. Then how to cover the planet with the Cutie Ocean tool. Finally you can freeze it with an ice storm & atmosphere freezer.
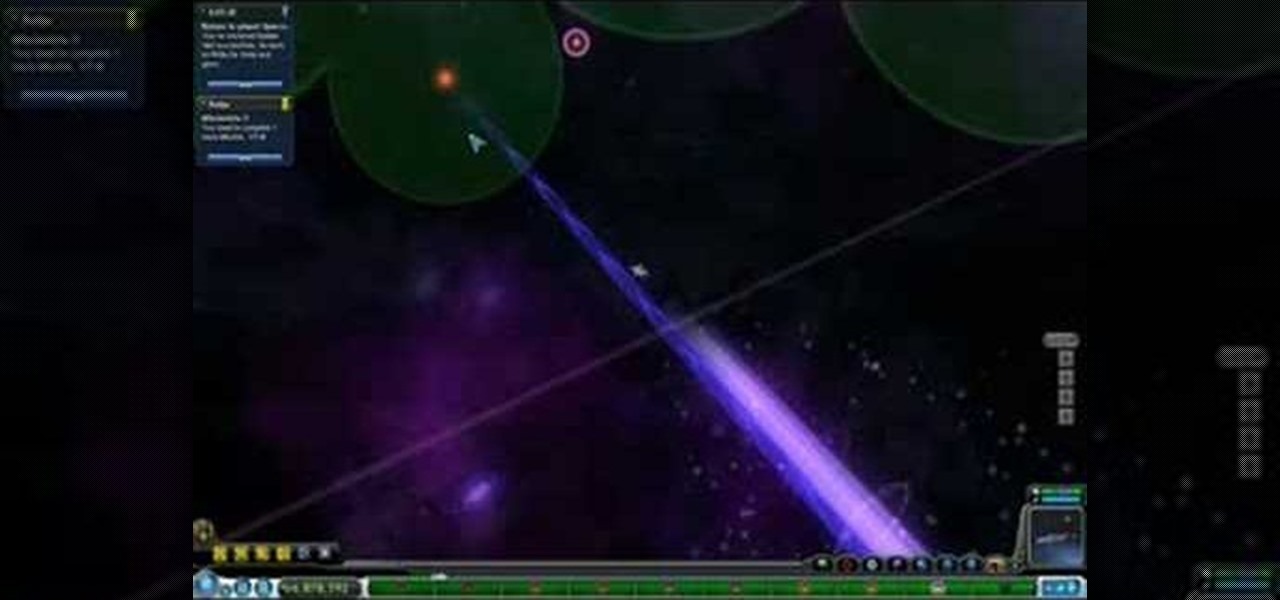
This is a walkthrough of the final moment as one achieves Warrior Hero and the title of Omnipotent. This is an ultimate goal in Spore that happens during the Space Stage of PC game play. This is a good insight into how to beat the game.

This is a walkthrough of the hunt for our solar system and home planet Earth. The searching is fast forwarded. Saw a picture on the net of a vague location of where it might be. This is an Easter egg in Spore.

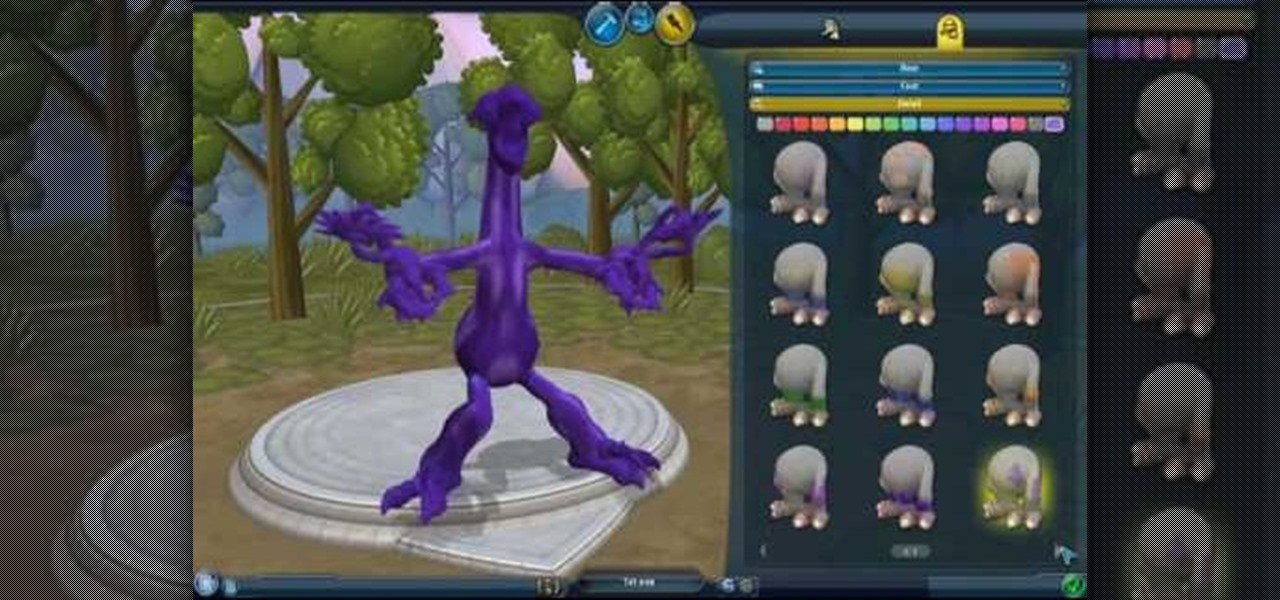
With Spore you can nurture your creature through five stages of evolution: Cell, Creature, Tribe, Civilization, and Space. Or if you prefer, spend as much time as you like making creatures, vehicles, buildings and spaceships with Spore’s unique Creator tools.

Nmap ("Network Mapper") is a free and open source (license) utility for network exploration or security auditing. Many systems and network administrators also find it useful for tasks such as network inventory, managing service upgrade schedules, and monitoring host or service uptime. Nmap uses raw IP packets in novel ways to determine what hosts are available on the network, what services (application name and version) those hosts are offering, what operating systems (and OS versions) they a...

This instructional fitnes HowTo video demonstrates how to do a ustrasana pose.

The method demonstrated in this how-to video makes the Bowline knot quick and easy to tie. It is useful when you expect a blow and need to take a few turns around your winch to use as an additional hardpoint. In this case I am simulating a mast winch but the process can be used on a horizontally mounted winch as well. The secret is to form the bowline eye by capsizing an overhand knot. With the standing part in your left hand form a turn around the winch from top to bottom then cross the runn...

Craving some classic Italian recipes? Then watch this cooking how-to video tutorial to learn how to make a stuffed pasta shells. Stuffed pasta shells are also known as Manicotti and they are simple to make.

Homemade yogurt is so simple to make that you’ll wonder why you haven’t made it before. Watch this how-to video and try this recipe. You will agree that Indian style homemade yogurt has a delicious flavor that is very different from store bought ones, not to mention how much cheaper it is to make versus buying.

Learn how to do a single small medicine ball baseball through against a wall. Presented by Real Jock Gay Fitness Health & Life.

Learn how to do cable reverse raises. Presented by Real Jock Gay Fitness Health & Life. Benefits

Learn how to do double handle low-cable speed squats and rows. Presented by Real Jock Gay Fitness Health & Life.

Learn how to use a medicine ball to do power snatch to toss ups for height. Presented by Real Jock Gay Fitness Health & Life.

Learn how to do dumbbell front raises. Presented by Real Jock Gay Fitness Health & Life. Benefits

Squats are probably the most useful exercise you can do at the gym—no other single exercise encourages more muscle growth. With a range of motion that incorporates many different muscle groups in the legs, core and upper body, squats not only strengthen those muscles, but also strengthen the tendons and ligaments that connect them. In addition to their strength-building benefits, squats also teach you core stabilization, which is important for almost any athletic endeavor. Learn how to do dum...

Learn how to do incline push-ups and sculpt your body without weights. Presented by Real Jock Gay Fitness Health & Life.

We next try some staking, because this garden has tall plants. Tall plants add verticality to the garden, but they only stay tall until a thunderstorm hits. They need staking if for no other reason to keep them out of the mud. Dahlias definitely need staking because their flowers are enormous and bend easily. Plan for this ahead of time. For staking there are lots of possibilities. You can use bamboo and string or you could use multi-purpose stakes. This metal stake is ideal for a single stem...

Minecraft just wouldn't be the same without all of those pesky monsters trying to break into your house and jump on you until you die. But that gets tiring after awhile, and sometimes you just want a safe place to go where you don't have to worry about being eaten, shot, or blown up.

In this article, I'll be exploring the basics of Python, i.e. variables, input and output. You'll need Python (2.7+), a computer, and some free time.

In this article, I'll show you how to send SMS messages with Python. You'll need Python 2.7 or later, urllib and urllib2. The code basically uses an online text messaging service to "POST" html data, as if a person was entering the data themselves. The uses for something like this are unlimited. For example, I modified the basic code so I would receive a text message letting me know every time someone rang my doorbell. The program could interface with Arduino through a serial port, and send d...

The debate over whether video games can be considered art or not has intensified in recent years as games like Braid and Flow have taken the digital aesthetic experience to new heights. These new games are great examples, but there are much older ones that present compelling arguments as well. The best is a 1986 ZX Spectrum/Commodore 64/Amstrad CPC game called Frankie Goes To Hollywood.

Lifehacker posts an article on the art of cracking weak passwords, courtesy of Internet standards expert, CEO of web company iFusion Labs, and blogger John Pozadzides. Pozadzides certainly knows a thing or two about password logic. (Note: this information is not intended to hack into accounts, but rather to protect you from using weak passwords).

A flaw in WPS, or WiFi Protected Setup, known about for over a year by TNS, was finally exploited with proof of concept code. Both TNS, the discoverers of the exploit and Stefan at .braindump have created their respective "reaver" and "wpscrack" programs to exploit the WPS vulnerability. From this exploit, the WPA password can be recovered almost instantly in plain-text once the attack on the access point WPS is initiated, which normally takes 2-10 hours (depending on which program you use).

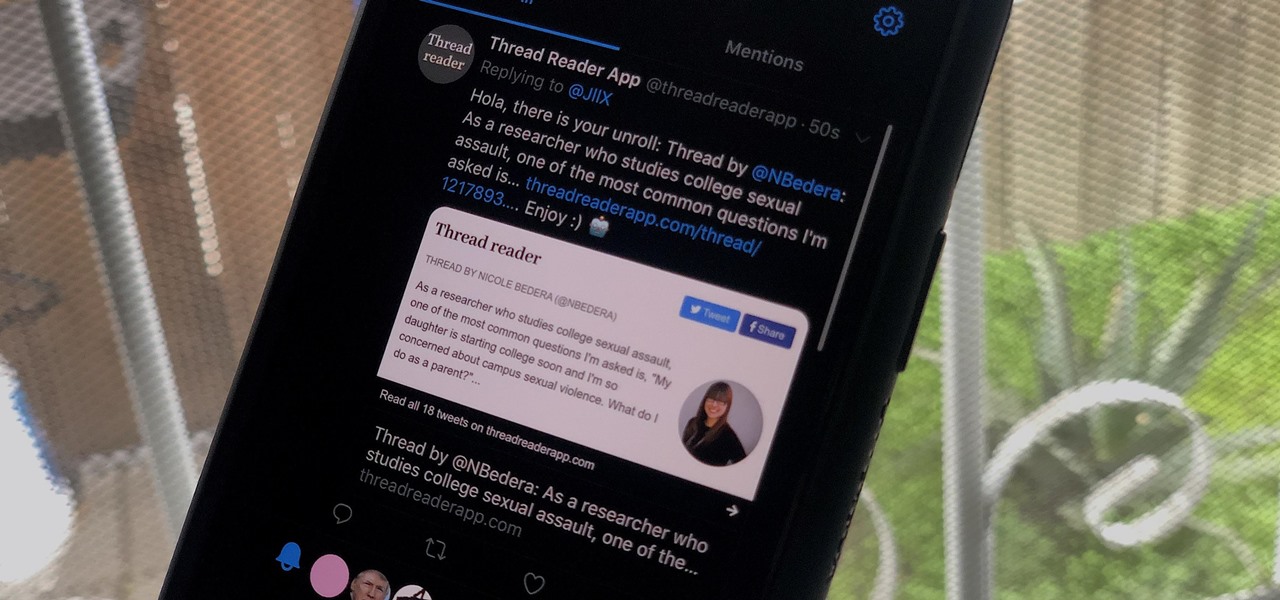
While tweetstorms were a part of Twitter since the beginning, threads, which makes tweetstorms more viable, didn't show up until late-2017. Still, threading multiple tweets at once to create long-form stories, opinions, tirades, and other lengthy Twitter posts, can be hard to digest. However, you can make reading them easier with just a single message.

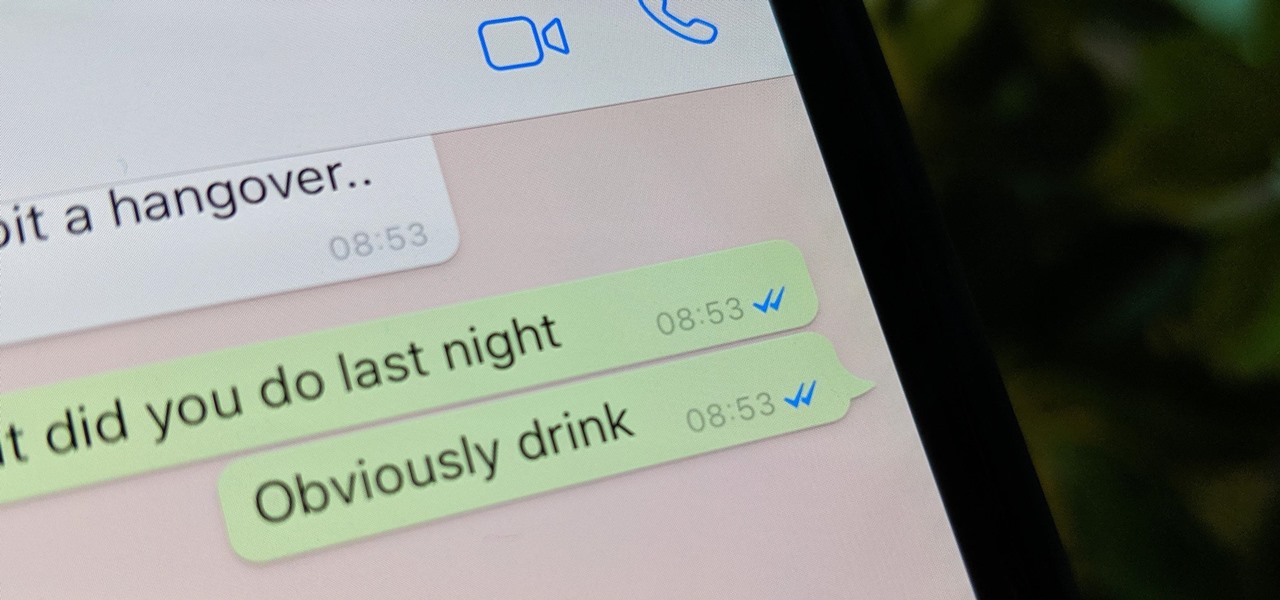
WhatsApp, like other popular messengers on iOS and Android, shows when recipients have read your sent messages with a blue double check mark indicator. On the flip side, for those of you who are bad at replying promptly or don't feel like replying at all, you can disable "read receipts" so the senders won't know when or if you even read their messages.

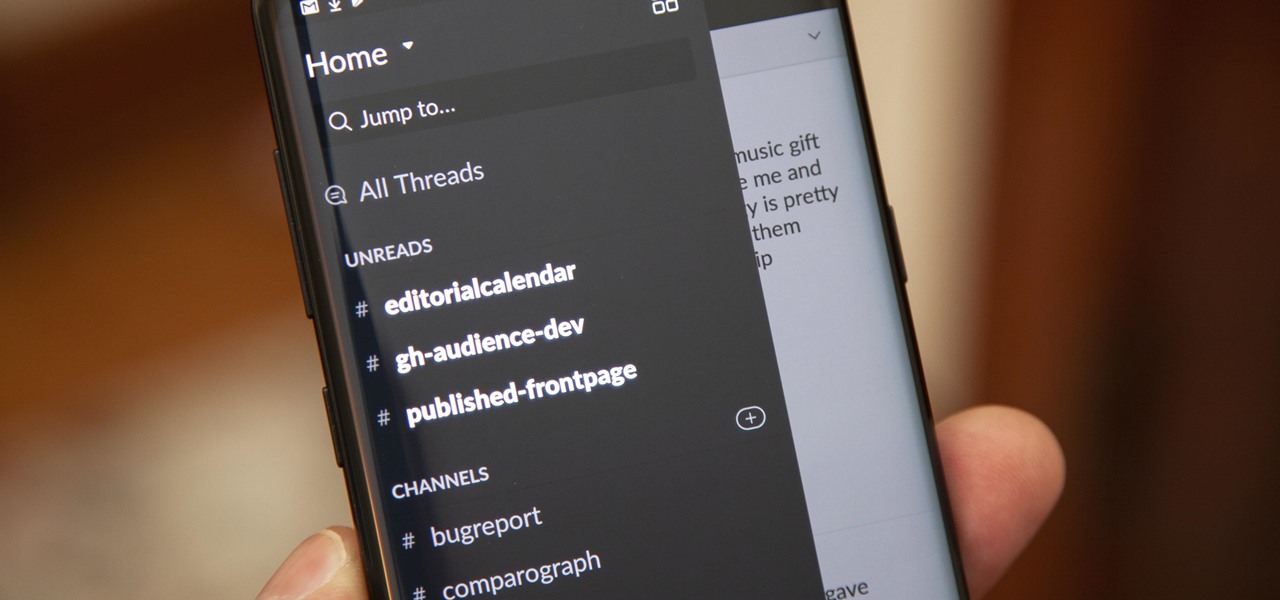
Slack recently released a dark mode for its Android and iOS apps, and for the most part, it works great. Super dark gray backgrounds and light gray fonts, which is much easier on the eyes than blinding white backgrounds and black text. But there's one thing that is not affected by the new night mode setting — your sidebar.

I was today years old when I first heard of Bhad Bhabie, but I'm told she is apparently a rapper with a rags-to-riches story.

While they don't do augmented reality just yet, the latest styles of Snapchat's Spectacles 2 camera glasses serve as a peek into the future of how mainstream AR wearables may look.

OnePlus pulled out almost all the stops with their latest flagship, but there are a few areas where the phone falls just short of perfect. The single bottom-firing speaker leaves a lot to be desired, for instance, but thanks to the awesome development community for the OnePlus 6, you can already give your phone true stereo speakers with a software mod.

After a district judge approved the $85 billion merger between AT&T and Time Warner, we knew AT&T would be quick to reap the rewards of capturing Time Warner's media properties. Today, we get our first look at this with two cellular plans from AT&T. What makes these plans unique is they include a new cord-cutting service called WatchTV.

There's always an iPhone in our list of top phones for privacy and security, due in large part to advanced security measures like Face ID, consistent iOS updates, and easy ways to prevent unwanted access and excessive data sharing. However, some of those options actually do the opposite and hinder security. It all depends on how you use your iPhone, but you should at least know everything available.

Samsung and Apple are the two titans of the mobile phone industry. After Apple deployed the iPhone X in November, Samsung had three months to brood until Mobile World Congress, where they unveiled the Galaxy S9. Now that both phones are out, it's time to put them head-to-head.

Snapchat is a wonderful app that allows users to "talk with pictures." You can send other users pictures of what you have going on in your day-to-day life, and they can respond with what's happening in their own. It's a seamless way to have a conversation with someone using visuals — sometimes even faster than you would be able to with words.

Using either iMessages or FaceTime on the iPhone is a great alternative for coworkers to stay in touch in the event that messaging services like Slack go down. They're also a handy means of communicating between buyers and sellers, as it provides a more intimate way of either checking out or showcasing a product. But you're not always going to want to give out your real number to everyone.

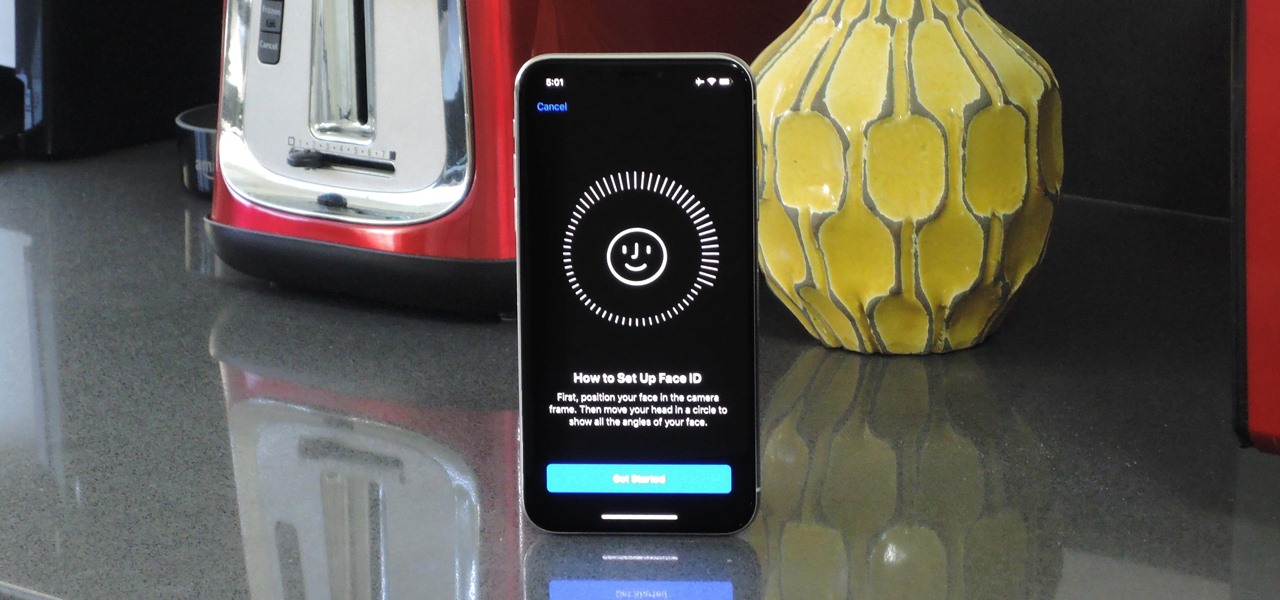
The cutting-edge iPhone X, XS, XS Max, and XR have one-upped their Android competitors when it comes to facial recognition. Apple packed these flagships with an array of front-facing sensors to complement its selfie camera, which allows the new device to more accurately analyze faces, which you need for Face ID, Touch ID's replacement.

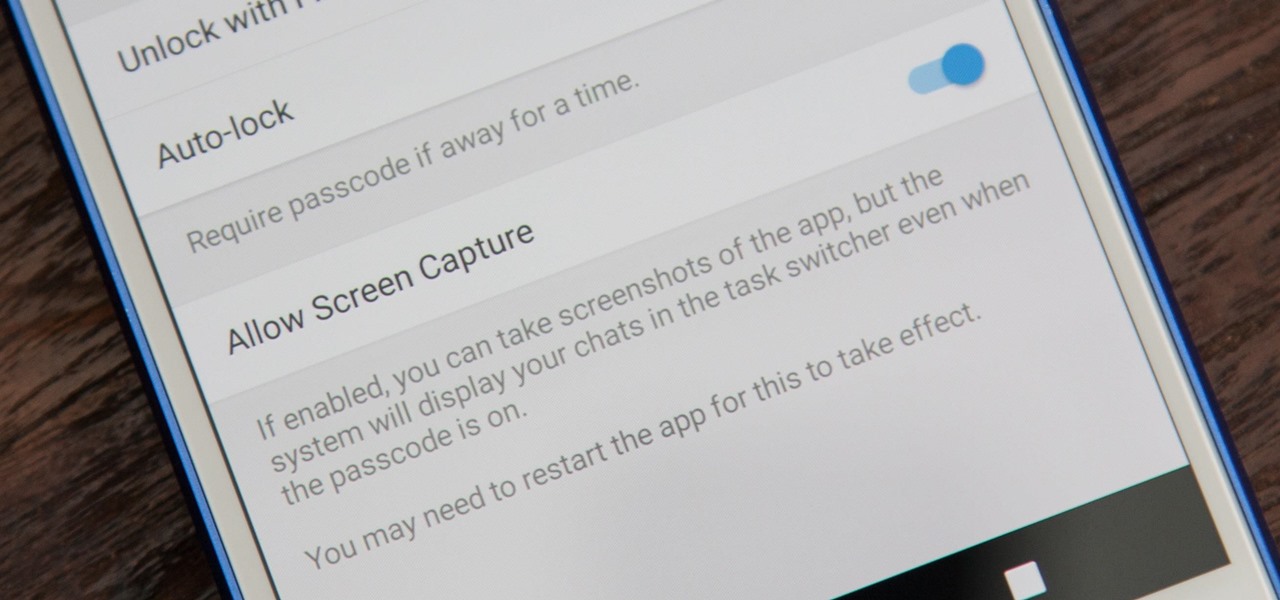
While it's easy enough to take a screenshot of an end-to-end encrypted Telegram chat thread using an iPhone, it's an entirely different story on Android phones. Telegram disables screenshots for Secret Chats by default on Android, and not everyone can turn it on.