
Mark Ramprakash of Surrey and England demonstrates how to do the one-handed pick-up and throw. It is the best way to run out a batsman taking a quick single. The key is to approach the ball with short strides. Do the one handed pick-up and throw in cricket.
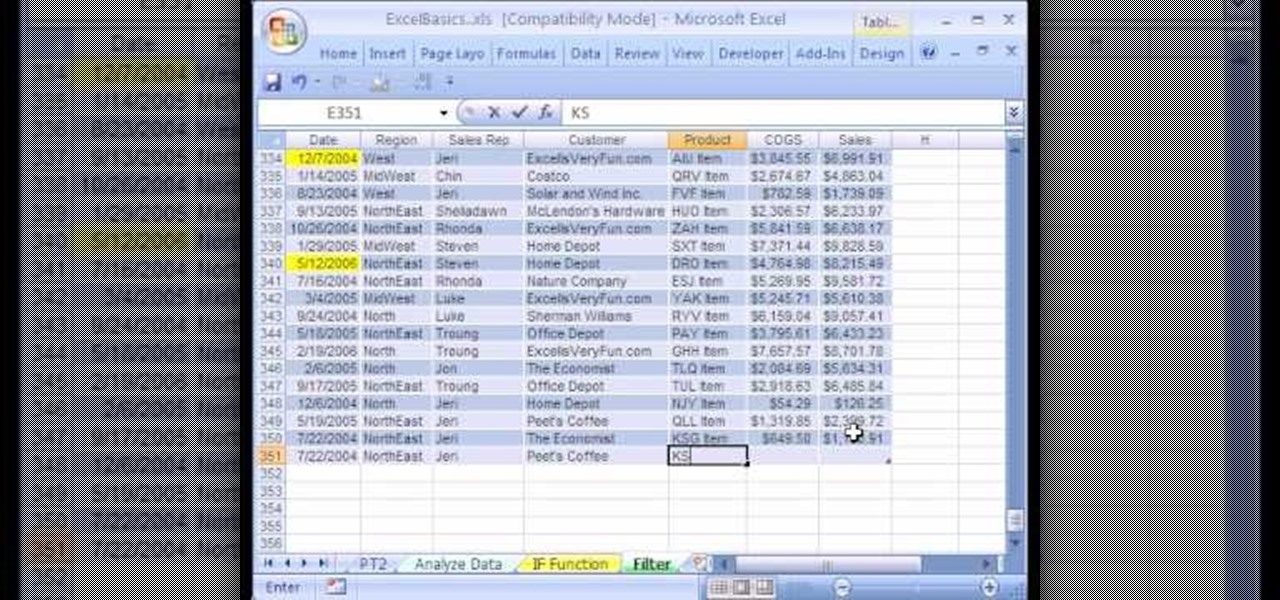
We're on sheet, tab, filter. We want to talk about filter, but we also want to talk about an Excel table or list. It is simply a data set with field names at the top, records in rows, no blanks anywhere and no other data sets touching this data set. When we convert to a table, it does a lot of amazing things. The new keyboard shortcut is "Ctrl T". If data is set up correctly, it will work. Click Ok. You can build a function based on a column of data, i.e. "Alt =" which is the shortcut for sum...

This 3D software modeling tutorial series shows you step by step how to create a suitable model for Google Earth within SketchUp. The series will start by showing you how to export data from Google Earth to use for reference, how to build and optimize the modle, texture it in Photoshop or Picasa and export and load it to Google Earth.

Diet = Die or Eat As Biological definition, food is defined as; any substance consumed to provide nutritional support for the body. It is usually of plant or animal origin, and contains essential nutrients, such as carbohydrates, fats, proteins, vitamins, or minerals.

Can a free cloud-based video editor that lives in your browser replace iMovie? In three words: yes, it can. But whether you should use it instead of iMovie or an equivalent depends not on the functionality of the editor you need, as WeVideo can do what most of what iMovie does, but on what you need to do with your videos once they're finished.
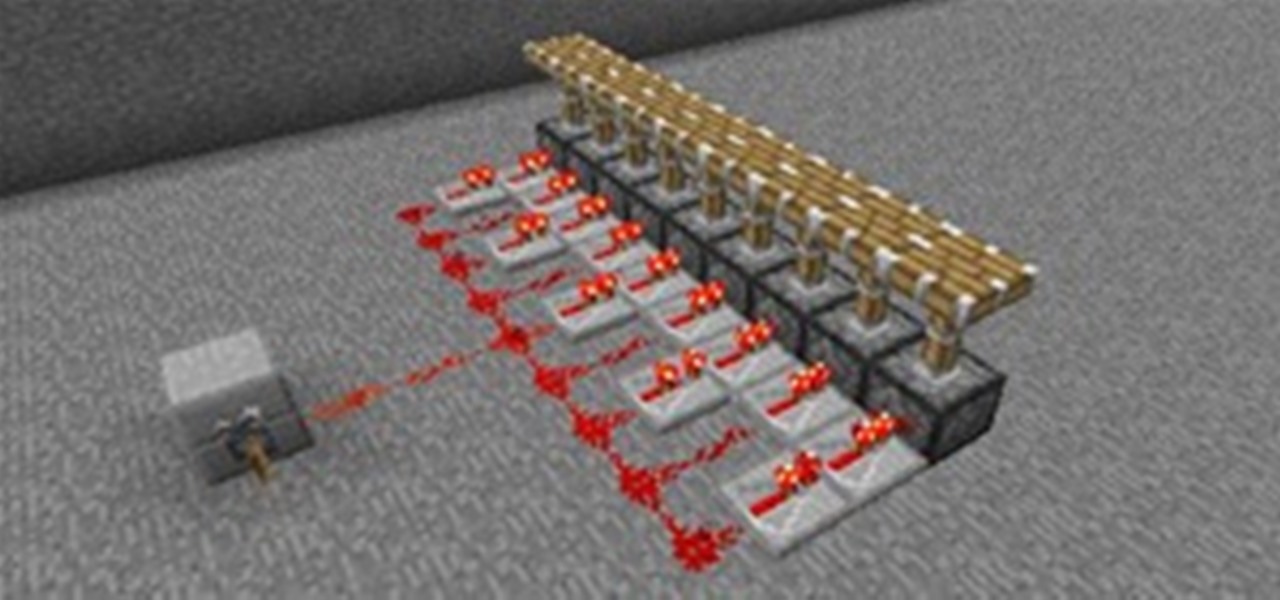
Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server. As we all know, redstone can be a very useful tool for make basic things in Minecraft more complex and intricate. For beginners to redstone, today's article will give you a basic understanding of how it functions, as well as its many uses.

Lisa Nichols, contributing author of The Secret and one of the great inspirational speakers of our time, believes the best way to stay motivated when continuing your education is to “begin with the end in mind.” Pushing forward through challenges is what makes accomplishment so gratifying. Every accomplishment leads to personal growth. Nichols believes that making the completion of your degree “non-negotiable” means that you will not settle for anything less.

The small size of most indie game development teams is a strength, but also a weakness. It allows them to take risks and explore revolutionary ideas that a larger company could never justify to its shareholders, but also means they must navigate the game development labyrinth with minimal help, taking much longer than those with big development teams. Some of the most exciting indie games currently in development have been so for years, or look like they will be.

As I was listening to Apple's WWDC conference today, what ran through my mind the most is if there were ever a time to switch to the world of Apple computing now is it. Today's WWDC keynote presentation was chock-full of new and updated iOS mobile software—too much to cover in this one article. But the most "new thing" coming from Apple this Fall is iCloud, a file sharing and streaming service that requires no wired connections.

Leave it to to channel lust into a dance hit all about f-ing. The Spanish singer just has this impossible-to-pinpoint, irresistible charm that excuses his chauvinistic qualities and makes him radio gold.But at least he knows he's a pig, and this is the second song where he implores a lady at a club to forgive his forwardness. His rumored girlfriend Anna Kournikova better watch out, with all these groupies at the clubs Iglesias is going after.

This origami tutorial will show you how to fold a six pointed star out of a regular piece of 8 1/2" X 11" paper. There are verbal instructions in Japanese for those who will find it useful, but the step by step visuals are quite clear. To fold an origami six pointed star, one only needs a single piece of rectangular paper and a little patience.

In this video legendary jazz drummer Joe Morello shows some practice techniques for the snare drum. Paradiddles, single stroke and double stroke technique are all addresses in this short but informative video.

SCRABBLE. To some it's just a game, but to me it's life or death. Well, not really, but it feels that way anyway. On a normal weekend, a game becomes much like Jon Thomas' "friendly game of death Scrabble."

Your iPhone is fairly secure by default, but Apple's Lockdown Mode takes it to Fort Knox levels of protection. If you're a high-value target for spyware, phishing attempts, and other sophisticated cyberattacks, it's an essential feature. But for almost everyone else, it's an extreme move. If you simply want to verify someone's identity when chatting, Contact Key Verification is a more practical option.

The era of virtual meetings has been evolving every few months, with augmented reality filters leading the charge in changing the way we interact when chatting via video streams.

Who had Lil Nas X, blood-drop Nikes, and satan worship on your 2021 bingo card? In a story that's stranger than fiction, the "Old Town Road" rapper has ruffled some feathers with the video for his new single, "MONTERO (Call Me By Your Name)" filled with demonic imagery usually reserved for death metal bands.

When you're talking about collectibles, in 2021 it's heresy not to include the world of sneakerheads. Nowadays, a single, limited batch of newly designed sneakers from Nike can quickly sell out and then go on to be resold for many thousands more than they were purchased for at launch.

People are going nuts with their iOS 14 home screens. One look on social media shows just how creative people can be with their home screen widgets and customized app icons. That said, maybe you aren't looking for a crazy setup. Maybe you're someone who wants a simple, clean home screen. Friend, this trick is for you.

Wi-Fi networks come in two flavors: the more common 2.4 GHz used by most routers and IoT devices, and the 5 GHz one offered as an alternative by newer routers. While it can be frustrating to attack a device that moves out of reach to a 5 GHz Wi-Fi network, we can use an Alfa dual-band adapter to hack Wi-Fi devices on either type of network.

This week's Magic Leap Lumin OS update contained a number of goodies, including iris authentication, and a way to stream to Twitch from the device.

The long wait is over — the best augmented reality device on the planet is finally available.

The idea of a world without passwords used to be a pipe dream. But as we inch closer to making that a reality, we have services now that securely store all of our passwords under a single master password. It's a convenient way to keep our accounts safe and sound without having to remember all of their credentials. And there's no reason to be afraid — I'll explain why.

When researching a person using open source intelligence, the goal is to find clues that tie information about a target into a bigger picture. Screen names are perfect for this because they are unique and link data together, as people often reuse them in accounts across the internet. With Sherlock, we can instantly hunt down social media accounts created with a unique screen name on many online platforms simultaneously.

Motorola is a shell of its former self. In 2010, it had just released the Motorola Droid, a phone so popular it led to all Android phones being called "Droids" by non-techies. But there have been some rough years between then and now, and Motorola's latest "flagship" doesn't look like it will help get them off this path.

Particular vulnerabilities and exploits come along and make headlines with their catchy names and impressive potential for damage. EternalBlue is one of those exploits. Originally tied to the NSA, this zero-day exploited a flaw in the SMB protocol, affecting many Windows machines and wreaking havoc everywhere. Here, we will use EternalBlue to exploit SMB via Metasploit.

While the Galaxy S10 is a beautiful phone, its software isn't for everyone. One UI makes huge strides toward undoing the mess known as TouchWiz, but for purists, it's still not quite on par with stock Android. Fortunately, the beauty of Android is you can change this with a few apps.

Information gathering is one of the most important steps in pentesting or hacking, and it can often be more rewarding to run things on the target itself as opposed to just running scripts against it remotely. With an SQL injection, a hacker can compromise a server and, ultimately, upload and run the "unix-privesc-check" script locally in order to further identify possible attack vectors.

The Moto G7 Power is a phone that screams battery life. From its display resolution to the massive battery, it was designed for those who hate to recharge each night. But unlike other battery-focused smartphones, it comes at a price almost anyone can afford.

One of the ultimate goals in hacking is the ability to obtain shells in order to run system commands and own a target or network. SQL injection is typically only associated with databases and their data, but it can actually be used as a vector to gain a command shell. As a lesson, we'll be exploiting a simple SQL injection flaw to execute commands and ultimately get a reverse shell on the server.

Many online users worry about their accounts being breached by some master hacker, but the more likely scenario is falling victim to a bot written to use leaked passwords in data breaches from companies like LinkedIn, MySpace, and Tumblr. For instance, a tool called H8mail can search through over 1 billion leaked credentials to discover passwords that might still be in use today.

There is no shortage of defenses against cross-site scripting (XSS) since it is so prevalent on the web today. Filters are one of the most common implementations used to prevent this type of attack, usually configured as a blacklist of known bad expressions or based on regex evaluation. But there is hope with a wide variety of techniques that can be used to defeat these filters.

If you store important, sensitive information on your iPhone in Notes, you'll want to be more careful. When Notes syncs across your iPad and Mac via iCloud — devices that family members or coworkers may share — you run the risk of having your notes read, edited, and deleted by other people. Such a catastrophe is easily avoided.

The "controversial" Pixel. No phone in the history of Google's Pixel lineup deserves this title more than the Pixel 3 XL. For some (including myself), the design is a welcome change that embodies the modern design of 2018 flagship phones. For others, it has an ugly huge display notch that destroys symmetry.

It's important to know who you're dealing with after hacking your target's MacBook. Getting remote access is simple, but covertly gathering information about the user and their system can be a challenge.

One of the first steps in reconnaissance is determining the open ports on a system. Nmap is widely considered the undisputed king of port scanning, but certain situations call for different tools. Metasploit makes it easy to conduct port scanning from directly inside the framework, and we'll show you three types of port scans: TCP, SYN, and XMAS.

When rumors first emerged of Sony's Xperia XZ3, many of us wondered why. With the Xperia XZ2 just releasing in April of this year, why is Sony already releasing its successor? But now that it is officially announced, it makes a bit more sense, as what Sony is calling the XZ3 is actually more like the XZ2S.

Database technology has vastly improved the way we handle vast amounts of data, and almost every modern application utilizes it in one way or another. But the widespread use of databases naturally invites a slew of vulnerabilities and attacks to occur. SQL injection has been around for awhile, and as such, there are many defense methods in place to safeguard against these types of attacks.

Hackers rely on good data to be able to pull off an attack, and reconnaissance is the stage of the hack in which they must learn as much as they can to devise a plan of action. Technical details are a critical component of this picture, and with OSINT tools like Maltego, a single domain name is everything you need to fingerprint the tech details of an organization from IP address to AS number.

Using a keylogger to intercept keys pressed on an infected computer can circumvent encryption used by email and secure chat clients. The collected data can often reveal usernames, passwords, and potentially compromising and private information which hackers abuse for financial gain.

It seems like each day new rumors and leaks come out for Huawei's upcoming P series devices. Everything from its name change to its specs has been leaked, sometimes with contradicting rumors. One of the biggest leaks is the inclusion of triple rear cameras, a first for smartphones.







































