Good makeup isn't when others notice you're wearing makeup, it's when they complement how beautiful you look today. You can enhance your own beauty by executing a couple tried and true makeup tricks. A little bit of makeup can go a long way.

Entertain your friends by turning your traditional personal headphones into a mini loud speaker with just an old mint tin and a playing card. This might not be the most advanced or prettiest way of listening to music but sure is a fun way to kill some time.

One of the coolest features on a Blackberry is BBM or Blackberry Messenger. BBM allows you to talk to anyone with a Blackberry, anywhere in the world, absolutely free! You can send messages back and forth and you phone will even keep a record of the conversation in case you need to reference something later.

Is a Bridezilla driving you crazy? Whether the bride gone wild is your sister, daughter, or BFF, you can stop the insanity. Here are some tips offered on how to deal with an out-of-her-mind bride.
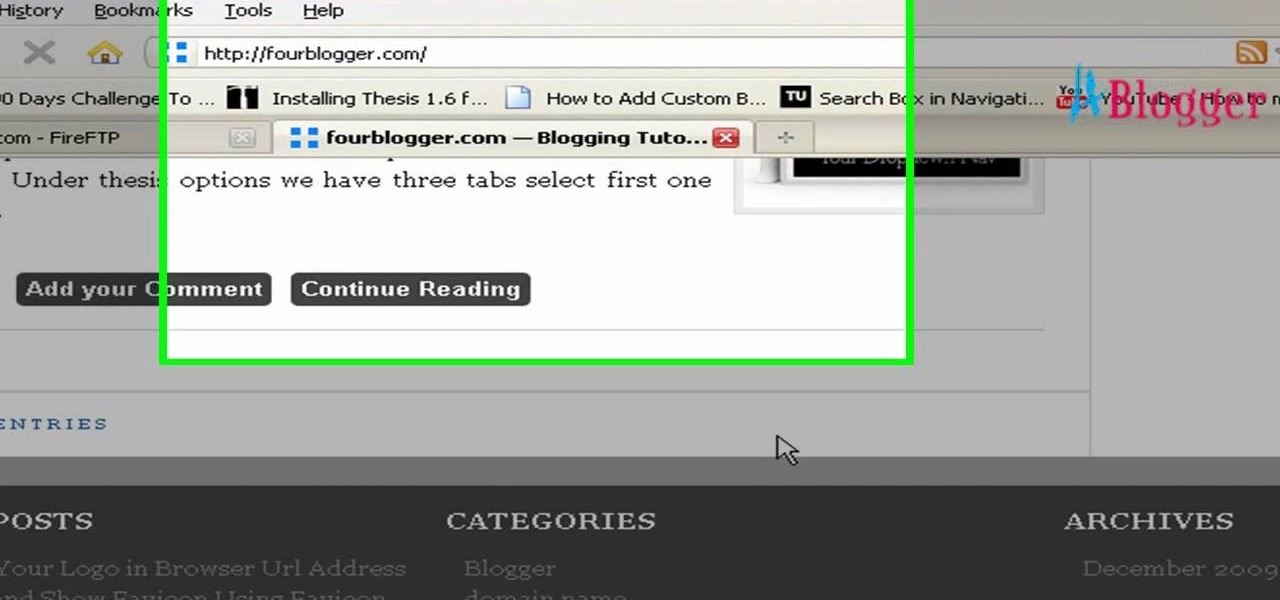
Get some great tips on Thesis themes for you WordPress blog. Watch this video tutorial from 4Blogger to learn how to remove the link in the footer of the Thesis theme.

Exercising with a Bosu Ball is a great way to engage core muscles during a regular workout. Work out with Bosu Ball exercises and these tips from a personal trainer in this free exercise video series.

Mujaddara has always been considered poor man's dish throughout the ages in the Middle East but currently it is considered a very healthy dish that provides a balanced healthy meal , with healthy fat, protein and carbohydrates. This dish is a very flavorful dish too.

The great thing about burritos is that you can make them to your personal taste and fill them with whatever you like. Today, we are going to fill the burrito with a few of my favorites. We have a base of black beans, rice, some sautéed green pepper and red onion, grated Monterey jack cheese, a little bit of sour cream and some salsa. But again, the fillings are versatile, it is the assembly of the burrito itself that we are going to concentrate on. he first key to making a great burrito, and ...

We know our Null Byte readers would like to see some iPhone-hacking scenarios on the site soon, but until we get some of those up, we understand that some of you actually use an iPhone as your primary phone. If that's you, and you would like an easier way to get information from point A (your iPhone) to point B (your computer) and vice versa, there's an all-in-one tool that can help.

We all know how volatile the stock market is, especially during times of crisis. That does not mean that the market is impossible to gauge, however. Day traders are trained to read charts in order to recognize market trends and price patterns, giving them the insight they need to make their trades as profitable as possible.

Pressing the side key on your Galaxy S20 wakes or locks the device, while pressing and holding the button activates Bixby. So "side key" is an apt name — it's not really a power button anymore. That begs the question, how exactly do you restart this thing?

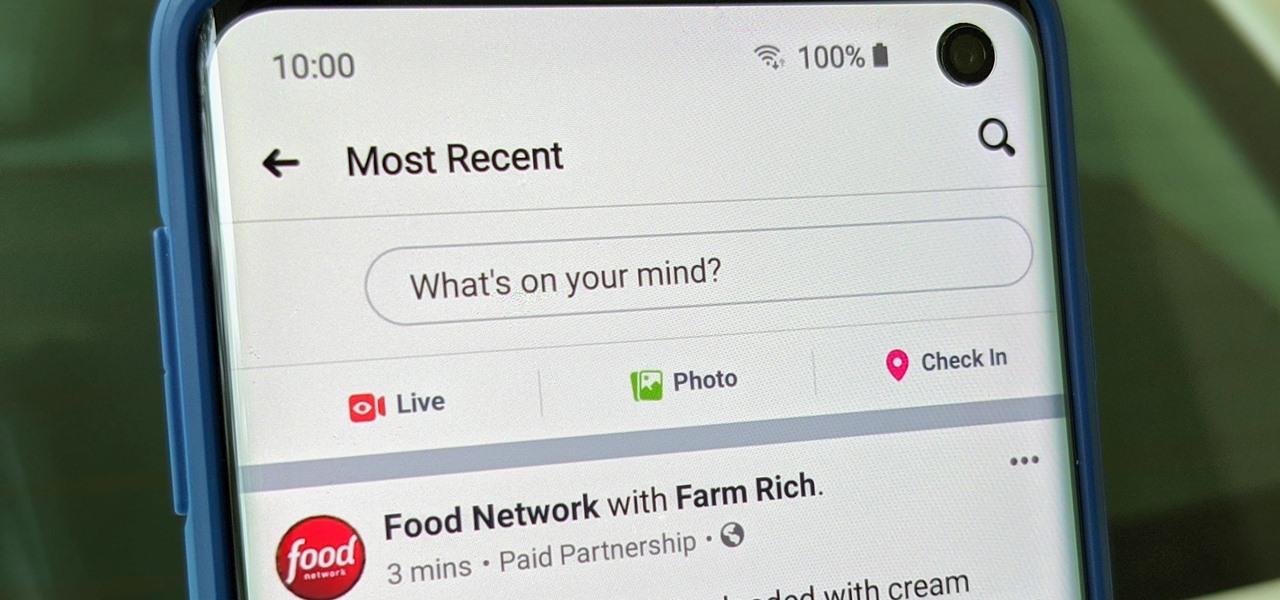
Facebook is where a lot of people get their news. The problem, though? Your Facebook feed gets jumbled with random post times, which isn't useful for keeping up with new stories in real-time.

Smartphones have so much sensitive information attached to them. If you share your home with others, then you know the pains of trying to keep anything private. Photos are surely among the things you'd prefer to keep to yourself, so OnePlus has you covered.

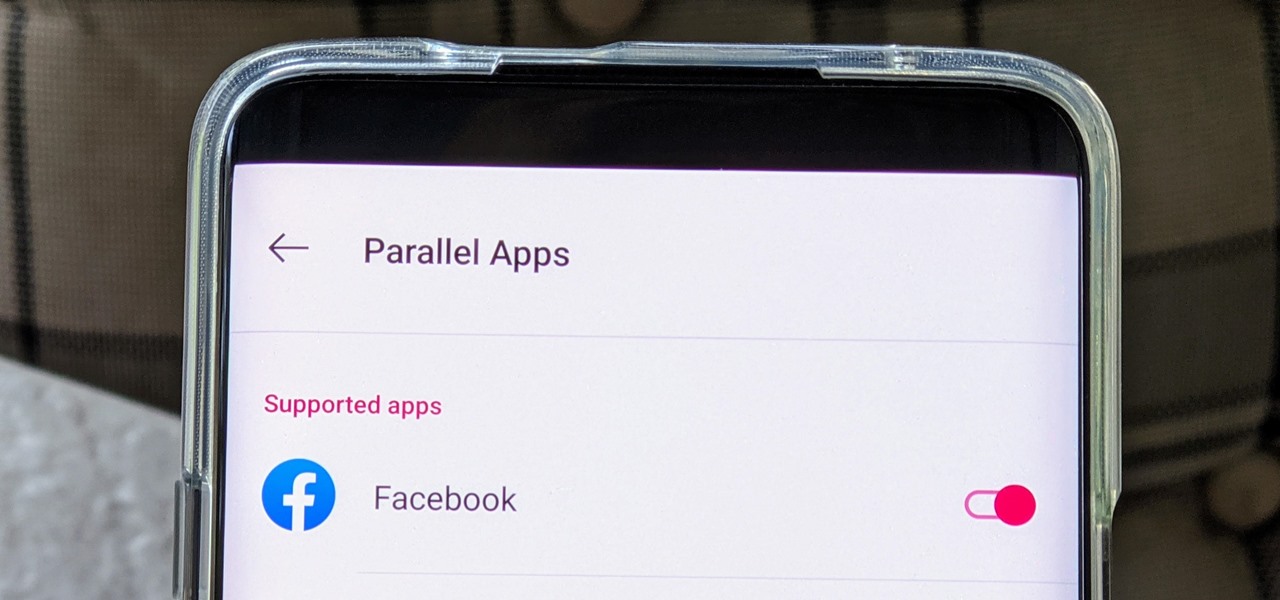
The Facebook app only supports one account being logged in at a time — but what if you need one for work and one for your personal life? That would normally involve logging out and logging in every time you need to switch accounts, but your OnePlus device offers a much better solution.

Commenting on Facebook pictures is a commonality. But you may not want to share your private and personal pictures on Facebook. Maybe you just want a select few to comment on your photos. Fear no more, you can send your pics and get private comments using Google Photos.

Your phone is loaded with contacts you've collected over the years. They're an asset, and you should use your library of connections outside the confines of your mobile device. Luckily, your Pixel uses a standardized medium to store contacts that can be used by the likes of LinkedIn, Outlook, Hubspot, iCloud, and more.

With so much of our personal data floating around the web, it's nearly impossible to get away from spam calls, texts, and emails. Unfortunately, this isn't just limited to the online world — filling in your contact information in a raffle ticket with the hope of winning that shiny new car in the mall, for instance, can often result in getting swamped with spam texts containing sketchy loan offers.

Apple is giving iPhone owners even more options to express themselves via Animojis with a wide range of customization options for their personal Memojis.

Hollywood loves to use New York City's Times Square as a setting for major scenes in a blockbuster movie, so it's only right to use the area for a choice bit of virtual apocalypse in augmented reality.

Open-source intelligence researchers and hackers alike love social media for reconnaissance. Websites like Twitter offer vast, searchable databases updated in real time by millions of users, but it can be incredibly time-consuming to sift through manually. Thankfully, tools like Twint can crawl through years of Twitter data to dig up any information with a single terminal command.

Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself from cyberstalkers, advertisers, and hackers in a time when digital lives are a high commodity.

If there was a version of the Doomsday Clock for counting down the release of Microsoft's HoloLens 2, then the caretakers of that imaginary clock would move the minute hand to "one minute to midnight."

Although Apple's Animoji game is strong, as recently exampled by its Ariana Grande collaboration, Google isn't slacking either, unleashing a far more immersive music experience for smartphone users.

In case you hadn't heard, Google is now a legit cell service provider. Google Fi has its pluses and minuses, but the biggest upside is in the pricing. Depending on how much data you typically use, there's a good chance you could save a lot of money without sacrificing coverage by switching to Fi.

As a longtime Android user, one of the changes I was most excited about with Android Pie was the fact that the volume rocker finally controls media volume by default. However, the new way isn't ideal for everyone, but thankfully, there's an app that can change it back.

With the official launch of Magic Leap One expected by the end of summer (translation: days from now), Magic Leap's hype machine just took a big hit with the sudden loss of a key marketing executive.

Using Netcat to backdoor a macOS device has its short-comings. If the compromised Mac goes to sleep, the Netcat background process will occasionally fail to terminate correctly; This leaves Netcat running infinitely in the background and the attacker with no new way into the device. As an alternative, we'll use the lesser-known Tcl shell which can handle abrupt backdoor disconnections.

With Apple preparing to bring a slew of new features to its Animoji app this fall, Samsung has updated its AR Emoji imitator with the ability to create more realistic digital doppelgängers.

Just in time for the release of Pixar's highly anticipated sequel, AR Emoji based on characters from The Incredibles 2 have arrived for Samsung Galaxy S9 and S9+.

One of the leading chipmakers for smartphones is getting ready to announce a new processor made specifically for augmented and virtual reality headsets.

Thanks to its advanced cameras, the Galaxy S9 can capture videos at an astonishing 960 frames per second (fps). To put it in perspective, you now have you the ability to record the world around you in ways that previously required expensive professional camera equipment. And that's just the tip of the iceberg.

On this, the most cherished day for Star Wars fans, May the fourth, Lenovo has released a significant new update to its Star Wars: Jedi Challenges app: real person versus person lightsaber battles.

The key to becoming a competent white hat is knowing how the technology that you are trying to exploit actually works. SQL injection is one of the most common methods of attack used today and also one of the easiest to learn. In order to understand how this attack works, you need to have a solid grasp of ... you've guessed it ... SQL.

Usually, when the public gets to see and hear Microsoft's Alex Kipman expound on the future of immersive computing, it's because the company has a new product to show off. But on Tuesday, April 24, Kipman was in the spotlight for an entirely different reason: an award nomination.

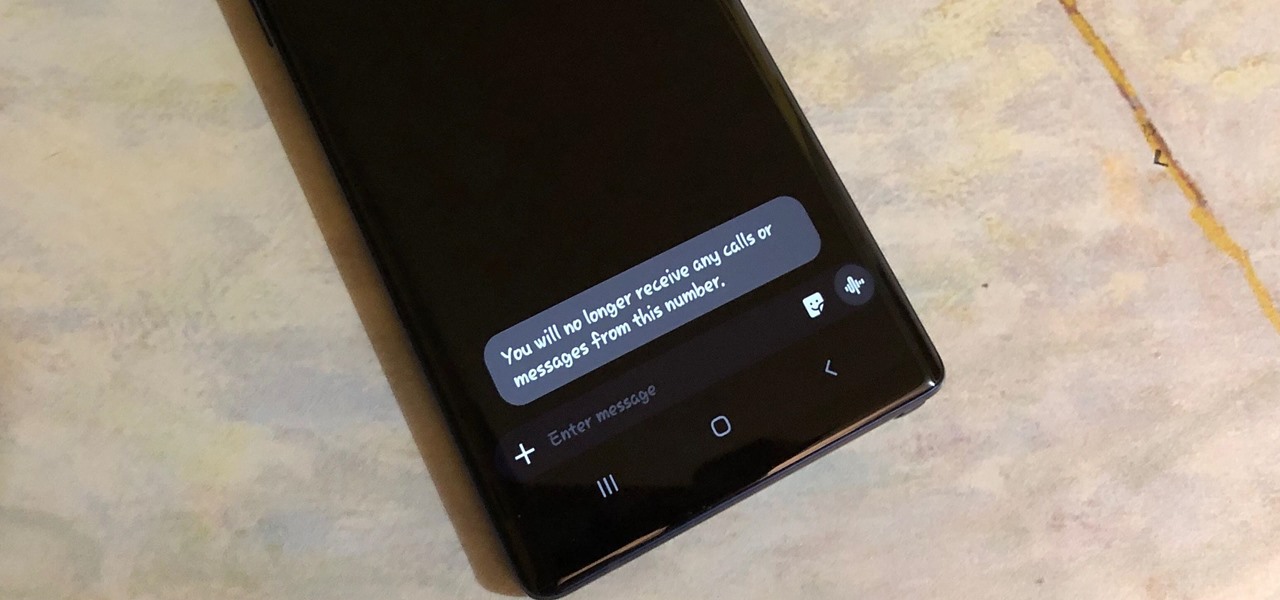
Between the Cambridge Analytica scandal and the revelation that Facebook logs your calls and text history on Android, many are considering joining the #DeleteFacebook movement. But it can be difficult to leave the site, because so much of its content is only available to active users. If you want to keep in the loop without sacrificing your privacy, you'll want to follow the steps below.

Space might be the final frontier, but NASA is making a detour into augmented reality first. The Spacecraft AR app, developed by NASA's Jet Propulsion Laboratory (JPL) in collaboration with Google, debuted exclusively for Android this week (an iOS version is also in the works).

Identifying vulnerable devices and services on a target router can be difficult without leaving logs and other traces of an active attacker on the network. However, there is a way to covertly decrypt and view Wi-Fi activity without ever connecting to the wireless network.

Conducting phishing campaigns and hosting Metasploit sessions from a trusted VPS is important to any professional security researcher, pentester, or white hat hacker. However, the options are quite limited since most providers have zero-tolerance policies for any kind of hacking, good or bad. After researching dozens of products, we came out with 5 potentials that are ideal for Null Byte readers.

It's easy to have your password stolen. Important people like executives, government workers, journalists, and activists face sophisticated phishing attacks to compromise their online accounts, often targeting Google account credentials. To reduce this risk, Google created the Advanced Protection Program, which uses U2F security keys to control account access and make stolen passwords worthless.

An incorrectly scaled object in your HoloLens app can make or break your project, so it's important to get scaling in Unity down, such as working with uniform and non-uniform factors, before moving onto to other aspects of your app.