Our site contains many videos on how to draw different kind of demons, but comparatively few for angels. Go figure. This video demonstrates how to draw angels wings, their distinguishing feature, in pencil. It is only a sketch at this stage, but with a little inking this could be a really beautiful wing.

So, you've started playing golf, and you've started getting competitive... Figure out a golf handicap with help from this free video from expert golf site, Golf Link. A golfer's handicap is determined by two factors, which are the course rating and the slope of the golf course. Subtract the course rating from a golf score, multiply by 113 and divide by the slope, and finally multiply by .96 to find a handicap.
This video shows you how to install language packs on Windows 7. It can be a bit tricky to figure out where to download these language packs, but this video does a great job explaining where to go. The invitation key needed to access the downloads section on Microsoft's site is Win7-3HQW-RF74. This also allows you to download Windows Server R2 2008 and Windows 7 Home Premium

Believe it: Your perfect pecs are a soup can away!

Partial seizures begin in a limited area of the brain, but each is profoundly different.

Follow these top seven tips to effectively engage the elderly or disabled!

Discover the top ten tips for communicating effectively with the elderly and disabled.

This video will help you learn the basics of safe and considerate wheelchair operation.

Get ready to get "back" with a simple at-home squat.

Thiamine, aka Vitamin B1, keeps your body fully functioning and ready to move!

Ladder Safety is a video tutorial designed to highlight the important safety procedures associated with ladder use on construction sites. The video uses classic B&W comedic film footage and computer graphic simulations to illustrate safe ladder techniques. Learn how to use a ladder safely while on the job or at home by watching this instructional video.

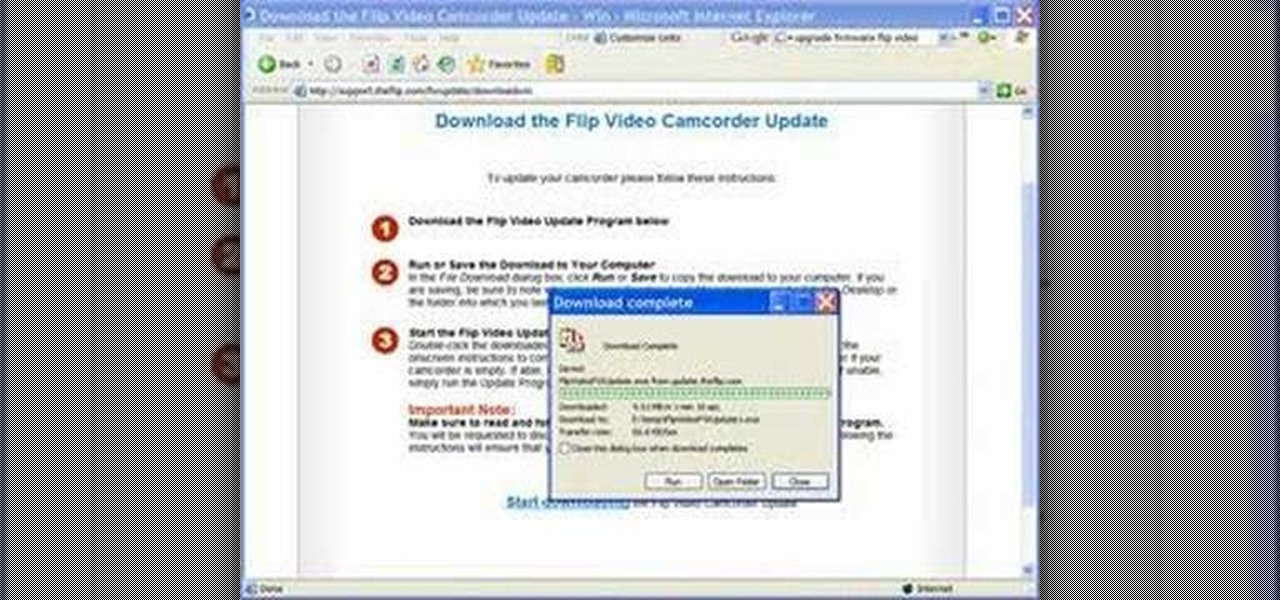
Here's how to solve problems and get better results with the Flip Video camcorder software by upgrading the firmware. Bill myers shows you how it's free and easy to do.

Watch this iPhone tutorial video to learn how to use the new web clips function, which lets you save a shortcut to a Web site right to your iPhone desktop. Saving websites to your iPhone desktop will be easy even for new iPhone owners after watching this how-to video.

Do you ever forget what your log-ins or passwords are for your favorite sites? This helpful software tutorial video shows you how to find them in Firefox 3. You'll never lose a log-in or password again in Firefox 3 after watching this how-to video.

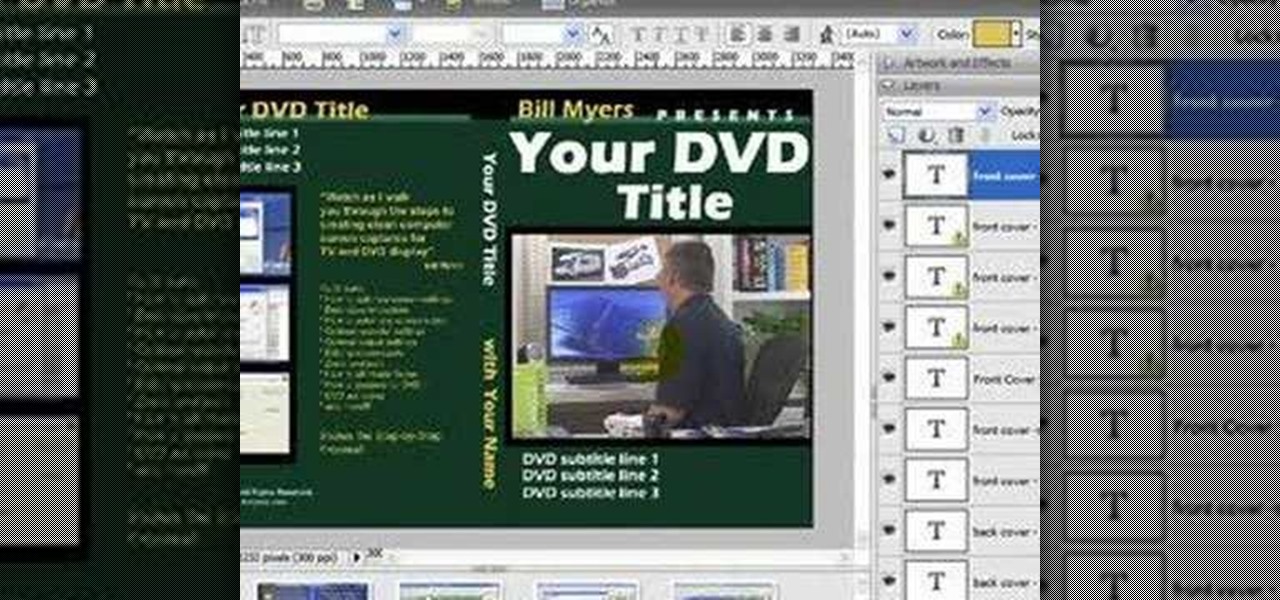
Bill Myers shows how to quickly create 'retail ready' DVD case and box covers using free Photoshop Elements template.

This tutorial with Bill Myers shows how to quickly create an instant play DVD when you have one long movie and don't want any DVD menu or buttons.

Check out this how-to video to learn how to crochet a beret reggae rasta cap. Wonderhowto.com has many videos in the knitting and crochet genre. Feel free to explore the site.

Matt covers some lines with a black ...Bg4. He found the first game with analysis on the Kenilworth Chess Club site. Most of the analysis he gave for this game is taken verbatim, but he does mention a couple side variations that you should be curious about. So watch!

If you are afraid to cook fish, this is this demo for you! This has to be the easiest “gourmet” method for fish you have ever seen. This will work for any thin, flaky white fish fillets, but Sole is the traditional choice.We topped the fish with is a simple lemon, caper butter sauce. Chef John will also demo this on the site and you would be well-served to learn this classic and versatile sauce.

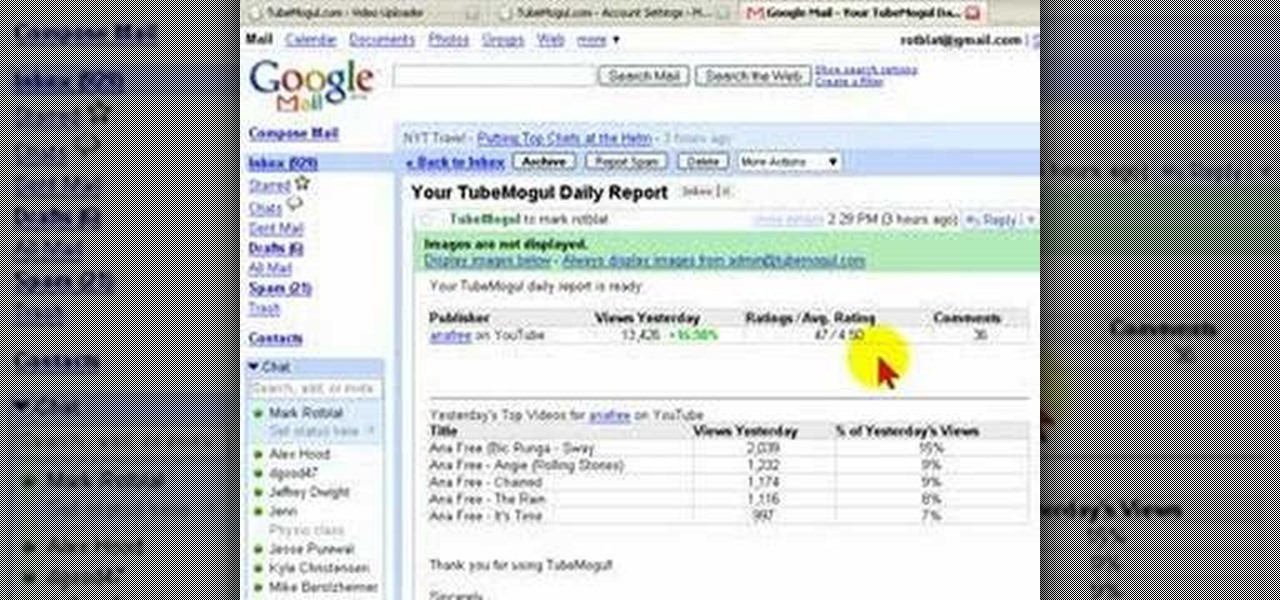
Here, Mark Rotblat of Tubemogul shows how simple and easy it is for you to e-mail your tracking reports to yourself and other people.

In this video, D.Lee Beard reviews two products: the Epson R280 6-color inkjet printer which can print on CDs and DVDs as well as 8.5 x 11 paper, and a review of the Kensington 19-in-1 Media Card Reader. He also explains how to find free books online, and viewer questions are answered on video instant messaging, and mac compatible mp3 players. Be sure to check out our http://AsktheTechies.com web site, Episode 71, for links to items discussed in this video.

Perfect for your web 2.0 designs or site, or even another type of interface, this shiny button will add some depth and style to your design. See how to make one in Photoshop in this tutorial.

If you're putting your email address online on your own website, or sites like facebook or myspace, you may want to be a bit clever about it. Check out this tutorial and see how to protect your email address from spam.

Tim Carter shows how to use a table saw and explains its benefits at a project site. Tim's table saw has wheels on it showing the portability of the table saw.

It's pretty much a given at this point that Facebook has a lot of data on us. While you might be conscious of the data you share with Facebook when you post, upload photos, or chat with friends on Messenger, you might not be thinking about all the data it receives from websites and apps you use outside the social media giant. Now, you can actually do something about it.

The Messages app on iOS features contact photos for every one of your conversations — including group chats. Even if you don't have a picture for a specific contact, their initials will appear instead. For non-contacts, a generic profile avatar appears. These give threads a bit of flare, but if you're looking for extra privacy or don't enjoy the look, you can easily hide those images and icons.

Every photo you take is brimming with metadata such as iPhone model, date and time, shooting modes, focal length, shutter speed, flash use, and geolocation information. Share these pictures with friends, family, or acquaintances via texts, emails, or another direct share method, and you unwittingly share your location data. Even sharing via apps and social media sites can compromise your privacy.

The internet is constantly under siege by bots searching for vulnerabilities to attack and exploit. While conventional wisdom is to prevent these attacks, there are ways to deliberately lure hackers into a trap in order to spy on them, study their behavior, and capture samples of malware. In this tutorial, we'll be creating a Cowrie honeypot, an alluring target to attract and trap hackers.

A virus easily spread among trout and salmon could make it harder to keep your favorite fish on the menu.

PowerShell Empire is a post-exploitation framework for computers and servers running Microsoft Windows, Windows Server operating systems, or both. In these tutorials, we will be exploring everything from how to install Powershell Empire to how to snoop around a target's computer without the antivirus software knowing about it. If we are lucky, we might even be able to obtain domain administrator credentials and own the whole network.

Today, Facebook Messenger is rolling out Discover, a feature that helps you chat with companies and locate nearby businesses of interest to you. First discussed in April at Facebook's developer conference F8, Discover is finally available for public use.

The beta firmware for OnePlus devices lets you record calls from the stock Oxygen OS dialer, but this feature is never included in official updates. This is likely due to legal issues with recording calls in some jurisdictions, but thankfully, there's a way to get this feature without having to run beta software.

A virtual design and construction services firm has built an augmented reality application that uses the Microsoft HoloLens to improve the efficiency of quality control on construction sites.

YouTube won't let you play videos in the background on Android without paying for YouTube Red, so if it's your primary source for streaming music, and you don't want to shell out $9.99/month, you'll just have to take matters into your own hands. The simplest solution to this problem would be to download MP3s straight from YouTube for offline playback, but in the past, this hasn't exactly been easy on a mobile device.

With the release of the Mirai source code, botnets are back in a big way. In the early days of botnets, zombies (infected hosts) would report to IRC (Internet Relay Chat) channels for CNC (command and control) instructions. Modern botnets have evolved, but they continue to use the same concepts as their predecessors.

Welcome back, my novice hackers! In this series, we have been exploring how a forensic investigator can find evidence of illegal or illicit activity. Among other things, we have examined the registry and prefetch files for artifacts and have done some rudimentary forensic analysis. For those of you who are seeking career as a forensic investigator or security engineer, this can be invaluable training. For hackers, it might be life-saving.

Starting in Android 4.3, Google added some code to AOSP that tagged your internet traffic when you were running a mobile hotspot, which made it incredibly easy for carriers to block tethering if you didn't have it included in your plan. But as of Android 6.0, this "tether_dun_required" tag has been removed, which means you no longer have to edit a database file to get tethering up and running.

Before we dive into the world of frustration, I first would like to thank whoever of the admins and mods made the folder for Raspberry Pi in the How-To's, thank you. Now with that outta the way, this article is about Metasploit on Raspberry Pi (hence the title). I should say that I ran into a error, but I think I figured what the problem is. First of all this is not on Kali Linux, but on a regular Linux OS. With that said let's open up a terminal and begin.

The Nexus 5X and Nexus 6P have identical camera hardware—in fact, both use one of the highest-end camera sensors ever put into a smartphone. The only real difference between the cameras on Google's latest flagship devices is that the 6P natively supports electronic image stabilization (EIS) whereas the 5X does not.

Hello everyone Today I will show a different way to exploit a windows machine with a reverse https payload..."wait...why https? Isn't tcp good anymore?"