
How To: Keep skin healthy with vitamin B3
You need to re-stock your supplies of Vitamin B3 each and every day. But why?


You need to re-stock your supplies of Vitamin B3 each and every day. But why?

Want softer skin, and to see in the dark? Then step right up for your daily dose of Vitamin A!

ADHD can be hard-hitting for children and their parents. Luckily, there are a host of treatment options available.

Over 300,000 Americans who are infected with HIV don't even know it! Learn how to avoid being among them.

Could you boost your brain power by eating a banana? Improve your memory and IQ by pressing certain points on your body? Absolutely! In this video, we'll show you how to amp up intelligence using super simple natural remedies.

You love to drink, but could do without the (literal!) headache. Imagine a world in which hangover prevention is actually possible! In this video, we'll teach you how to prevent a hangover, so you'll never waste another day post-drinking.

You've probably tried every alleged hangover cure--from cold showers to hot coffee--with little success. But a hangover remedy does exist! So watch this video and learn how to be a drunk without suffering hangovers ever again!

Between torturous tests and Friday frat parties, the last thing you want to think about is bed bugs. Unfortunately, these and other parasites, like head lice, may lurk around your dorm room. Here, everything you need to know to prevent these bug bites.

Pink eye, or conjunctivitis as your doctor may call it, is a contagious disease that affects many college students. Blame close quarters and bad hygiene for this itchy ailment that affects the eyes. Here's how to treat and even avoid this condition.

Someone you love is consuming much too much and you want to stage an intervention. While interventions can work, a person who abuses alcohol has to be willing to stop drinking. Here, everything you need to know to help encourage a friend to quit drinking.

You know you're in pain, but are you just feeling the aftershocks of that spaghetti dinner, or is it a heart attack?

Every year, 250,000 Americans are diagnosed with a form of skin cancer called squamous cell carcinoma. What exactly is SCC?

If you know the triggers that bring on a migraine you can more easily sidestep experiencing one.

Heart disease affects more than 20 million Americans. Let's explore the various forms that heart disease can take.

This video explains how to fold an origami goldfish using a single sided solid colored sheet of paper of size 6".

Learn how to fold an origami rabbit with instruction by Ancella Simoes. This video is in two parts, so be sure to click on Chapter 2 for the complete tutorial.

Learn how to fold an origami Reindeer with instruction by Ancella Simoes. Ancella Simoes is the author of the Origamiancy Blog and creator of all the Origamiancy origami tutorial videos on WonderHowTo. From Ancella's site:

Whether you miss the good old days of Telnet or you want to know what hacking was like when security was nothing but an afterthought, Telehack is the game for you. The text-based hacking game is a simulation of a stylized combination of ARPANET and Usenet, circa 1985 to 1990, with a full multi-user universe and player interactions, including 26,600 hosts.

We're living in uncertain times. The sudden outbreak of the novel coronavirus and subsequent self-isolation of roughly half the world's population has led to a massive reorganization of the economy, countless layoffs, compromised security networks, and a variety of other significant disruptions that will forever alter the landscape of our daily lives.

Sudo is a necessity on most Linux systems, most of which are probably being used as web servers. While the principle of least privilege is typically applied, sudo misconfigurations can easily lead to privilege escalation if not properly mediated. Which brings us to SUDO_KILLER, a tool used to identify sudo misconfigurations that can aid in privilege escalation.

Brute-forcing is an easy way of discovering weak login credentials and is often one of the first steps when a hacker finds network services running on a network they gain access to. For beginners and experienced hackers alike, it's useful to have access to the right tools to discover, classify, and then launch customized brute-force attacks against a target. BruteDum does it all from a single framework.

A lot of time can be wasted performing trivial tasks over and over again, and it's especially true when it comes to hacking and penetration testing. Trying different shells to own a target, and testing out privilege escalation commands afterward, can eat up a lot of time. Fortunately, there is a tool called One-Lin3r that can quickly generate shells, privesc commands, and more.

Correctly identifying the underlying technologies that run on a website gives pentesters a considerable advantage when preparing an attack. Whether you're testing out the defenses of a large corporation or playing the latest CTF, figuring out what technologies a site uses is a crucial pen-tester skill.
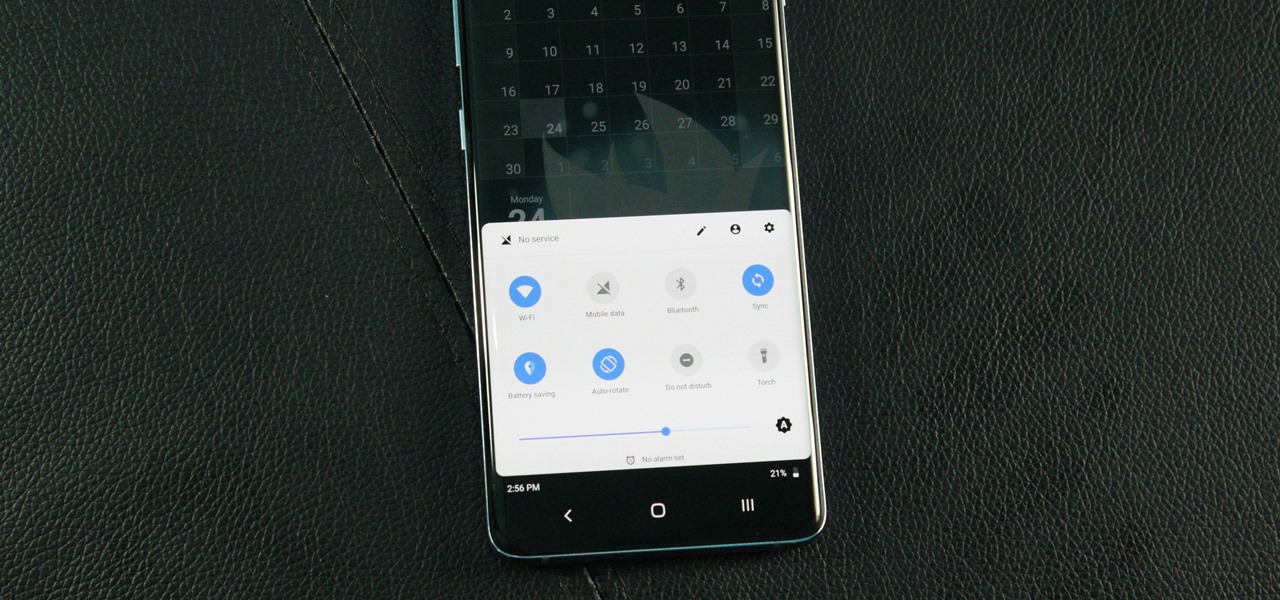
For those with small hands, smartphones have gotten out of control as of late. Nearly every flagship phone is over six inches in length, so many are forced to use phones that are too big for them and hope they don't fall. Well, thanks to one developer, using these phones can be a lot easier.
The Pixel 3a runs smoothly out of the box already, but installing a custom kernel can supercharge your experience even more. From fine-tuned CPU tweaks for boosting performance or battery life to adjusting the display colors for your screen how you want, ElementalX kernel can provide you with a ton of new features you didn't know you were missing.

KeePassX, 1Password, and LastPass are effective against keyloggers, phishing, and database breaches, but passwords managers rely on the operating system's clipboard to securely move credentials from the password vault to the web browser. It's within these few seconds that an attacker can dump the clipboard contents and exfiltrate passwords.

UAC is something we've all dealt with on Windows, either as a user, administrator, or attacker. It's a core feature of the Windows security model, and for the most part, it does what it's supposed to. But it can be frustrating as a hacker when attempting privilege escalation, but it's easy enough to bypass UAC and obtain System access with Metasploit.

Apple had its Worldwide Developers Conference on June 3, 2019, which showcased big software announcements for all of Apple's hardware, and anyone can watch the keynote as it happened.
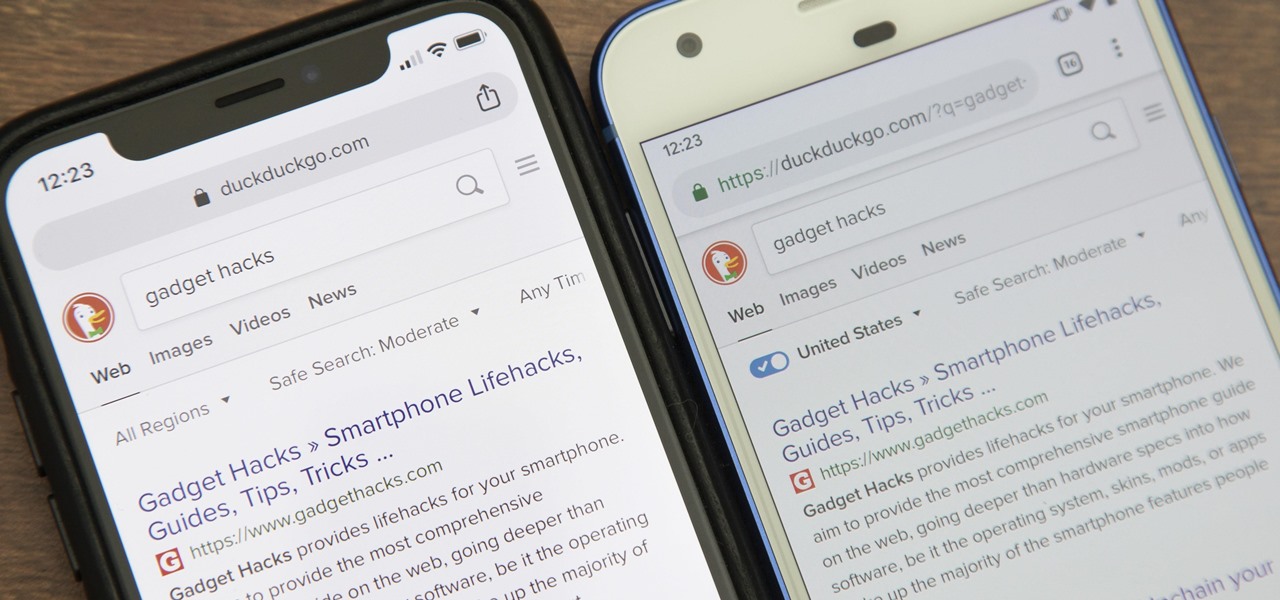
While Google would rather you use Google as the default search engine in Chrome, there's a way to switch to the more privacy-geared DuckDuckGo search engine for all your web browsing needs. With DuckDuckGo, the company does not track anything you search or allow anyone else to track it, so you can effectively search from your iPhone or Android phone anonymously.

One of the ultimate goals in hacking is the ability to obtain shells in order to run system commands and own a target or network. SQL injection is typically only associated with databases and their data, but it can actually be used as a vector to gain a command shell. As a lesson, we'll be exploiting a simple SQL injection flaw to execute commands and ultimately get a reverse shell on the server.

Update February 25: The new Sony Xperia flagship has been announced, and it has a new name: The Sony Xperia 1. You can read all of the official specs and details at our full article on Sony's new model.
The main draw for Google's Pixel series is the software. It rocks a clean version of stock Android instead of a heavy OEM skin like TouchWiz, it gets frequent prompt OS updates, the camera software is downright amazing, and it has perhaps the most fluid UI of any phone. But an understated advantage of the software is how dead-simple it is to modify with root-level tweaks.

If you want the best two-factor authentication app out there, our pick is Authy. A close second is LastPass Authenticator. If neither of those is to your liking, try Duo Mobile or Microsoft Authenticator. But if you're fine with missing out on great features, then and only then should you look at using Google Authenticator.

Once you've installed Ubuntu with security in mind and reduced the possibility of network attacks on your system, you can start thinking about security on an application level. If a malicious file is opened on your system, will an attacker be able to access every file on the computer? The chances are much slimmer if you put the proper defenses in place.
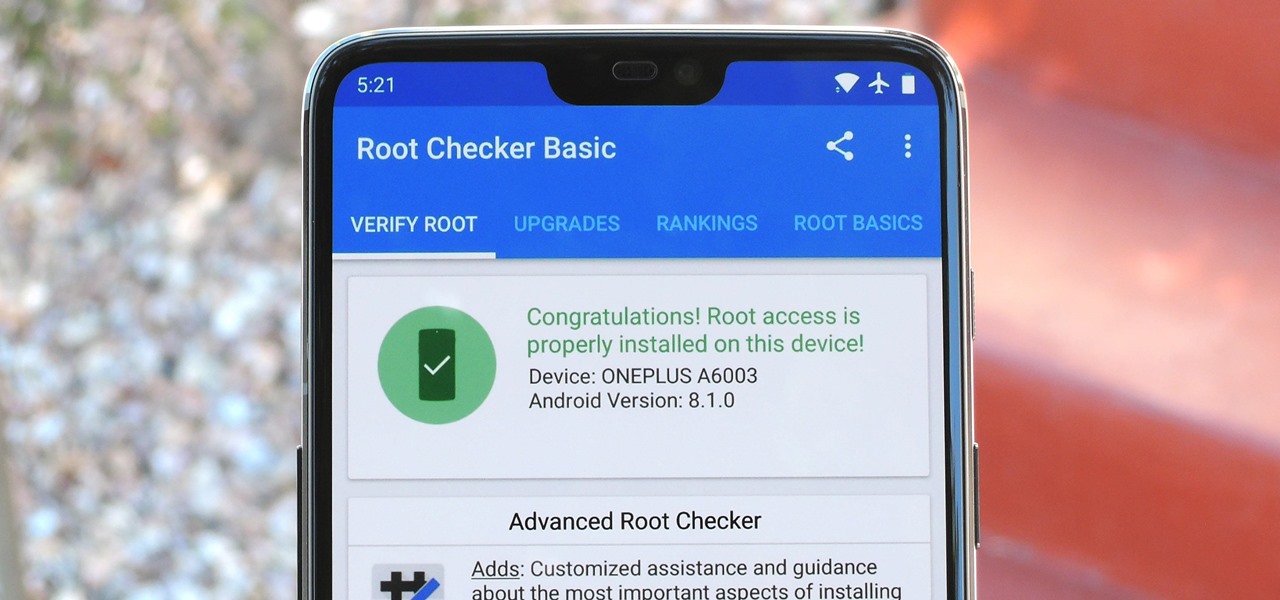
Year in and year out, OnePlus flagships top our list of the best phones for rooting. Why? Primarily because rooting does not void your warranty, and OnePlus goes out of their way to make the whole process as easy as possible.
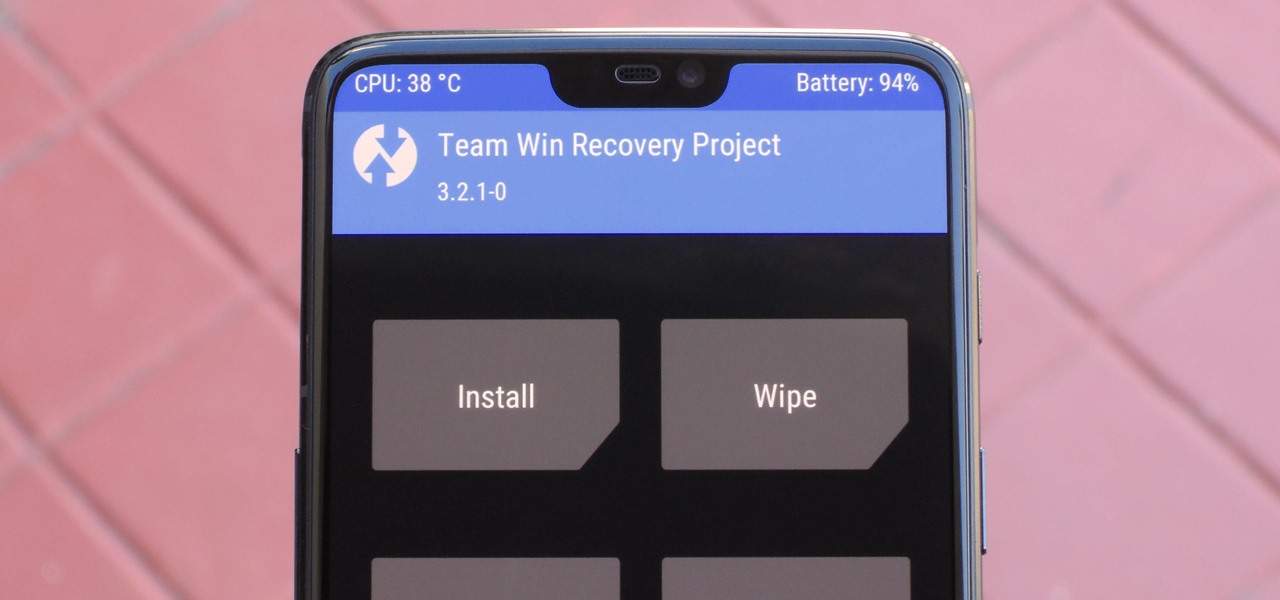
When it comes to modding Android, there's no better tool than Team Win's TWRP custom recovery. You can use it to root your phone, flash mods like Magisk or Xposed, and even replace the entire operating system with a custom ROM like LineageOS — honestly, there's not much this utility can't do.

Earlier this year, we got our first taste of Android Pie in the form of Developer Preview 1. As with all past Android previews, DP1 was limited to Google devices — but at Google I/O 2018, Google announced that Developer Preview 2 would be accessible to other devices, including the Essential PH-1.
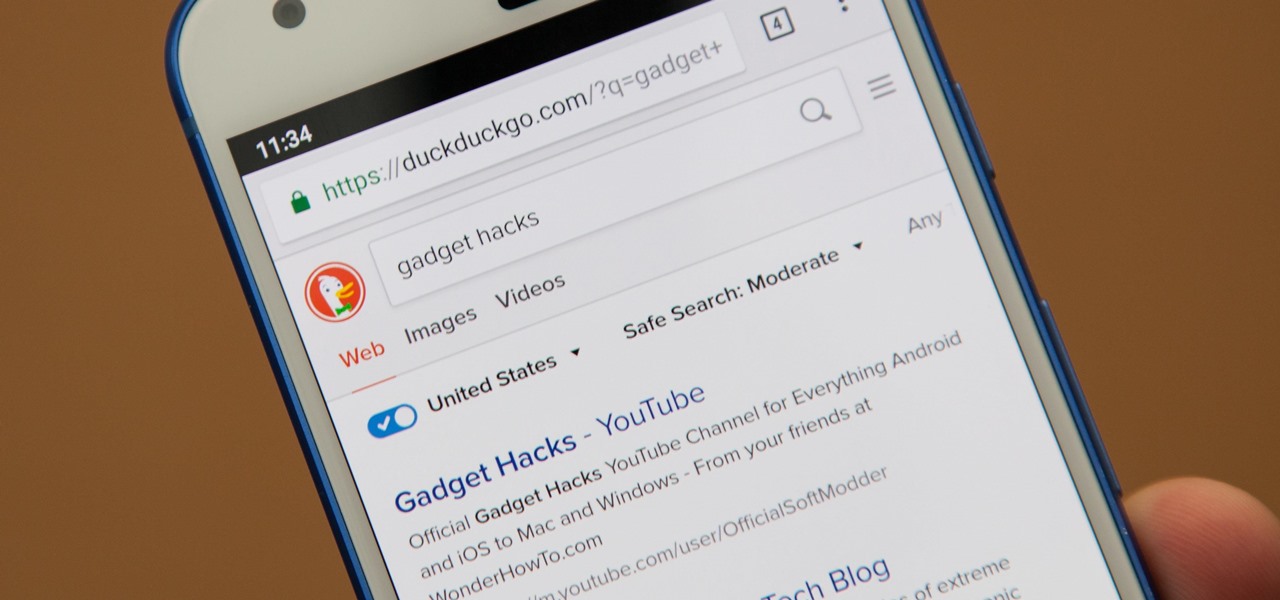
Even if your default mobile browser is Google Chrome, you may not want Google to also be your search engine. Maybe you're not impressed with Google's search results all the time, maybe you want a more private search experience, or maybe you just don't want Google's hands over everything in your life. Whatever the case, it's easy to switch from Google to another default search engine.
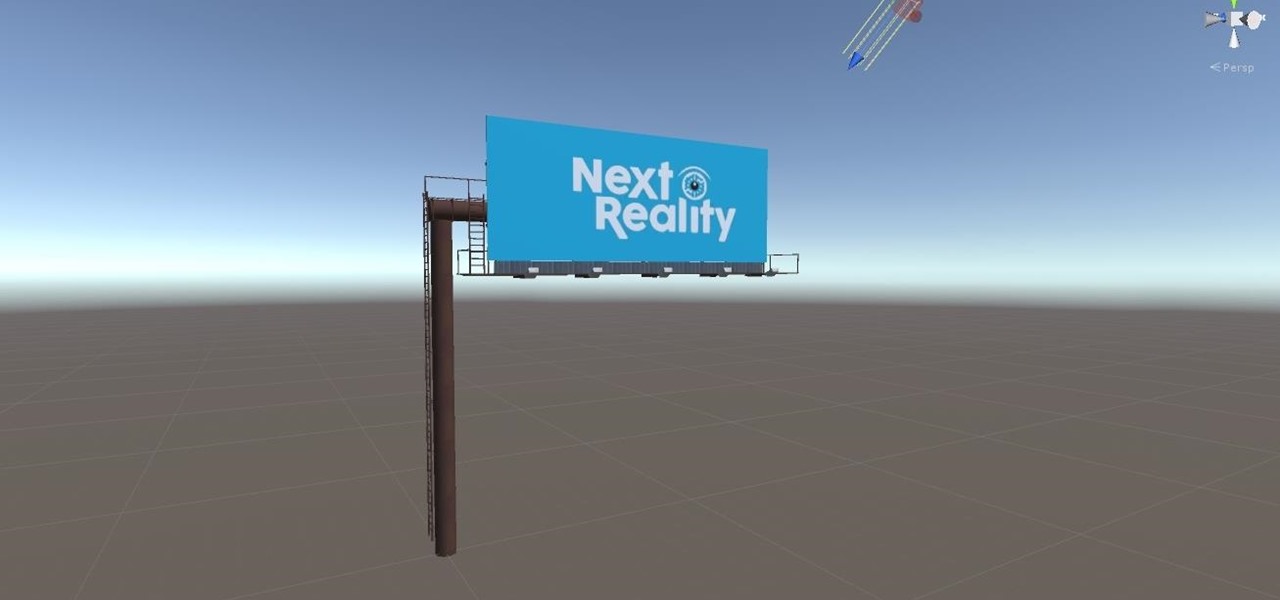
With the software installation out of the way, it's time to build the framework within which to work when building an augmented reality app for Android devices.
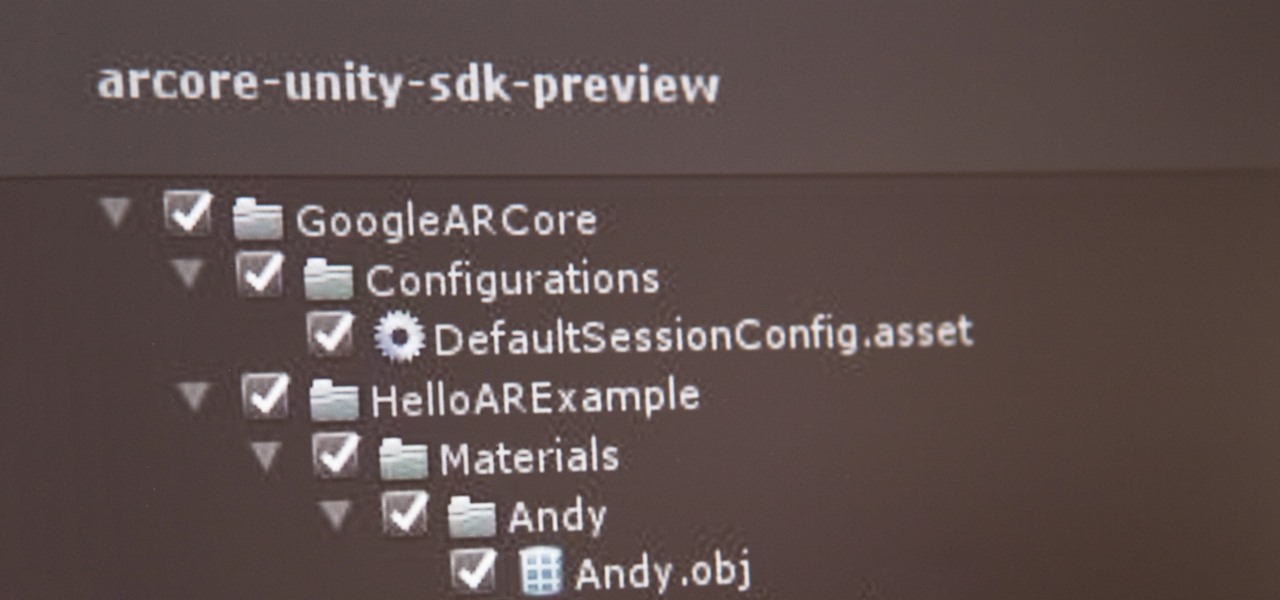
If you've contemplated what's possible with augmented reality on mobile devices, and your interest has been piqued enough to start building your own Android-based AR app, then this is a great place to to acquire the basic beginner skills to complete it. Once we get everything installed, we'll create a simple project that allows us to detect surfaces and place custom objects on those surfaces.