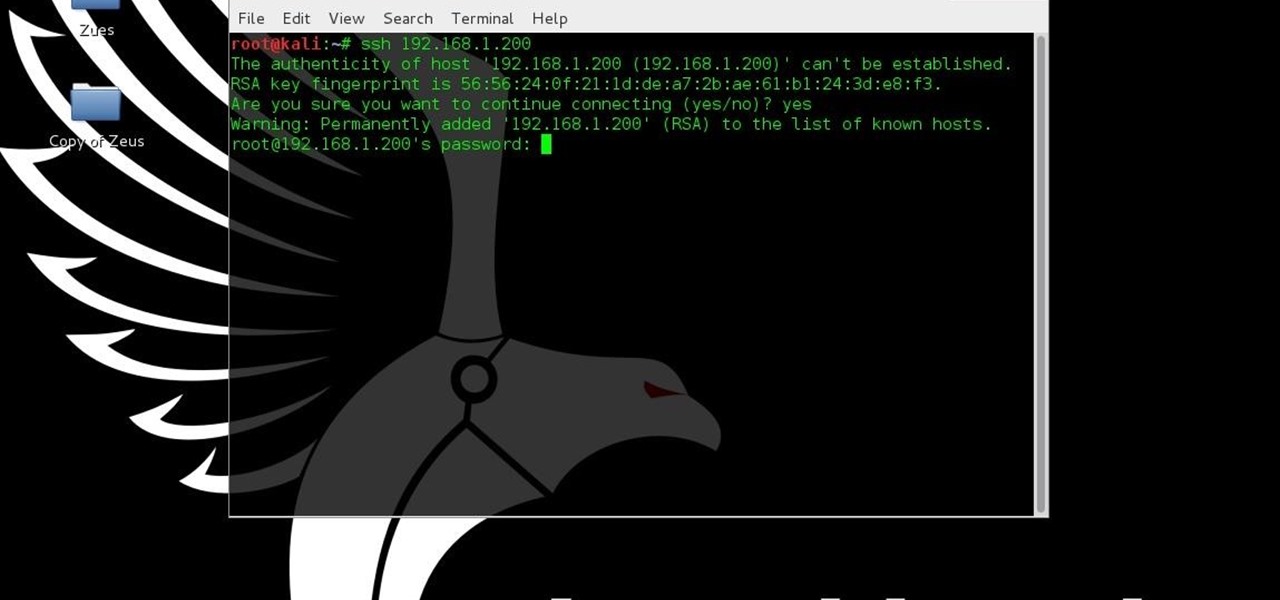
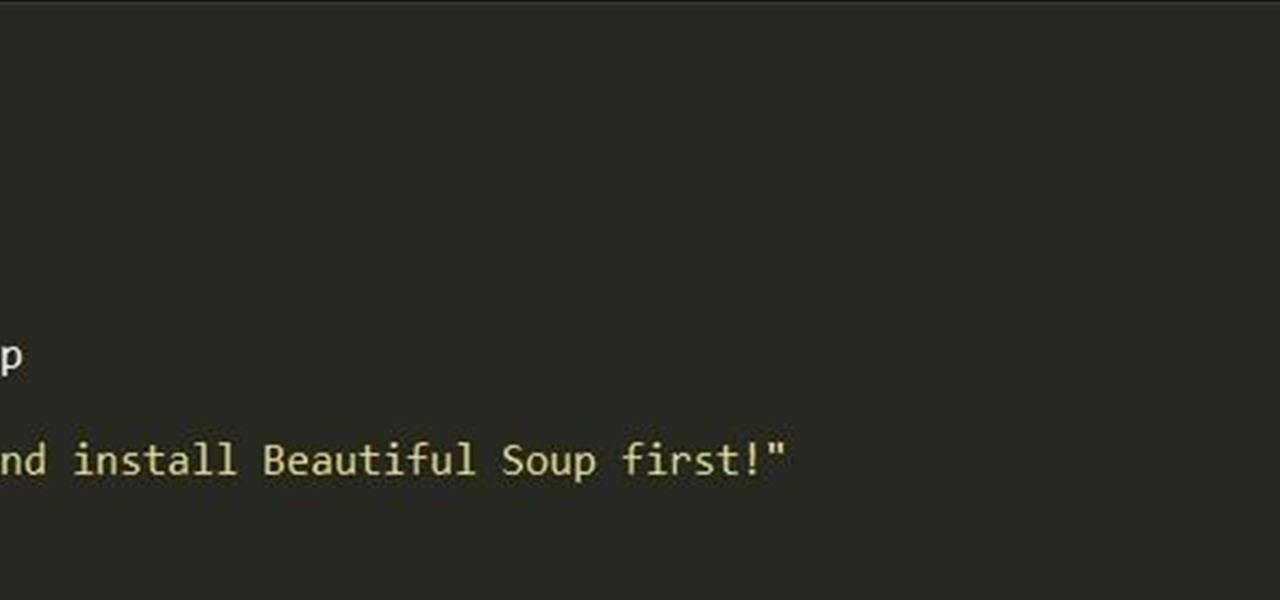
Hello, my fellow hackers. My name is cl0ck. I am a senior majoring in Computer Engineering with an emphasis is Security. I have been lurking the site for a while now reading and learning from the great minds that reside here. I, too, have some knowledge that I would like to share with all of you. This post actually comes from a personal problem I faced and had to find a solution for. Without further ado, here it is:
Have you ever used an open wifi, which after you connect displays a website to enter your credentials to get internet? That website is called captive portal and widely used in airports, hotels, universities etc. Have you ever wondered what would happen if someone would set up an open wifi with the same name displaying a very similar web page asking for credentials? Usually if there are multiple wifi networks with the same name and encryption, devices only display the one with the highest sign...
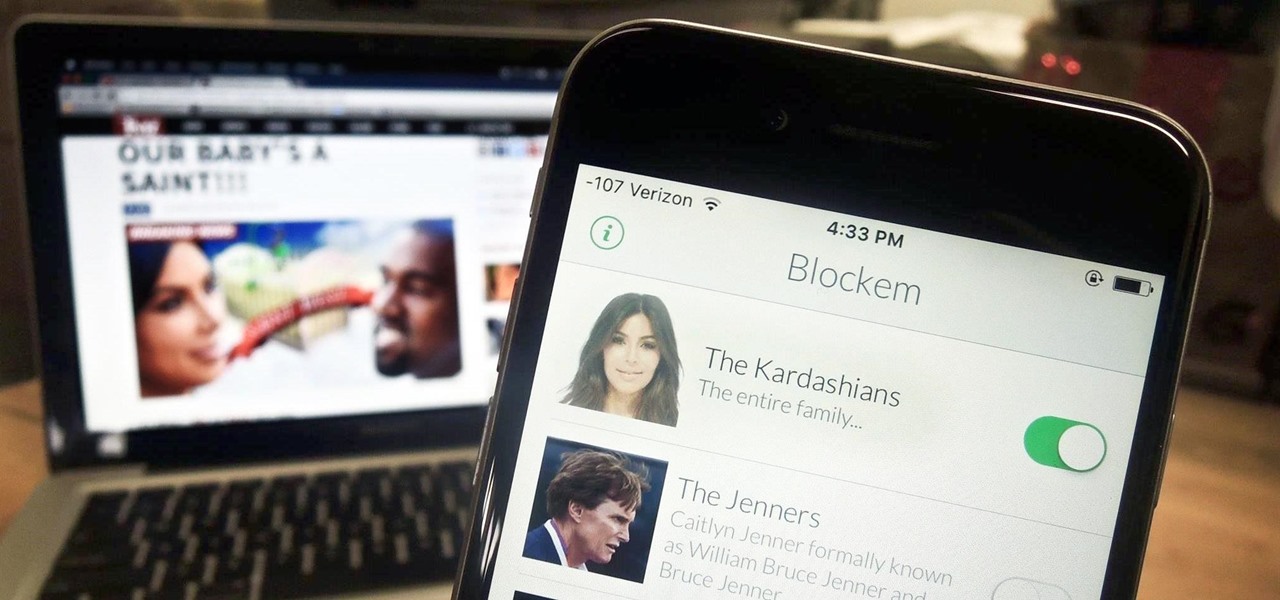
Kim Kardashian and Kanye West have fittingly named their second child "Saint," but I'm sure you don't care about that—and neither do I. Unfortunately, regardless of our pop culture interests, we're forced to know these types of stupid facts because the internet is so densely populated with Kardashian-related content that it's impossible to avoid. It's enough to make you puke.

Welcome back, my budding hackers! In this series, we are trying to understand how AV software works so that we can learn to evade it. To that end, we are working with the open-source AV software, ClamAV. I had previously introduced ClamAV in Part 2 of this series. If you have not installed it yet, go back to that and install it.
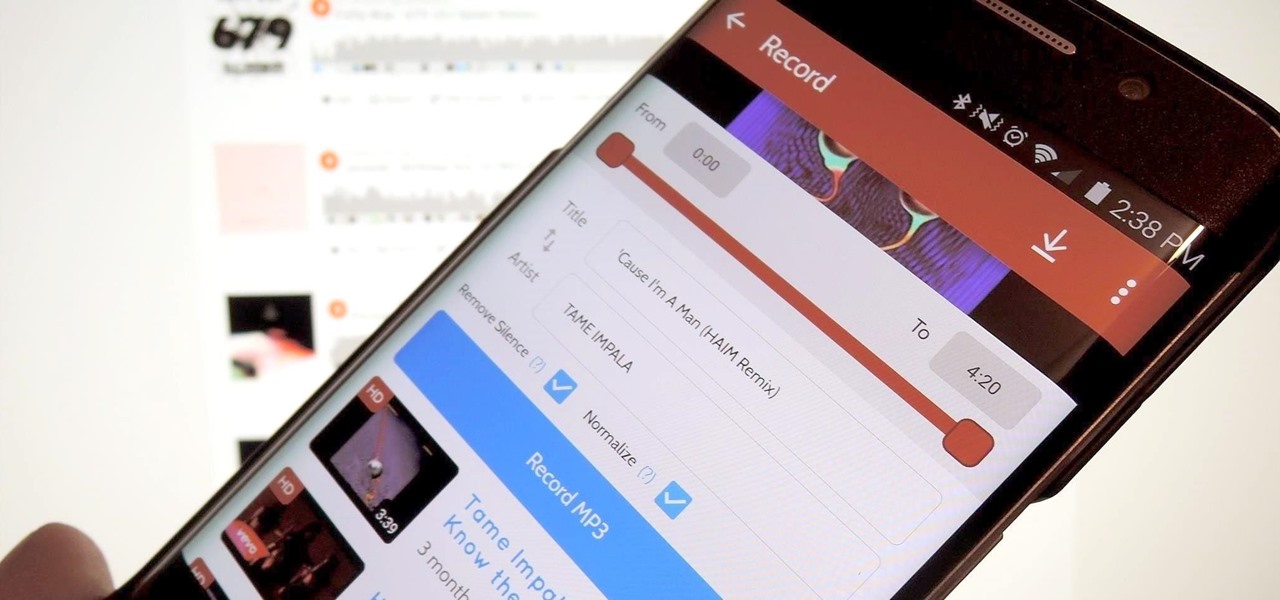
A growing trend for many artists (most recently Kanye West) is to offer exclusive or experimental tracks on music streaming sites like SoundCloud or YouTube before releasing them anywhere else. On rare occasions, some of these great songs never make their way onto an official album, which can be disappointing for die-hard fans who need to download every song available from their favorite artist or band.

If you somehow forgot the pattern, PIN, or password that locks your Android device, you might think you're out of luck and are destined to be locked out forever. These security methods are hard to crack by design, but in many cases, it's not entirely impossible to break into a locked device.

Hello, my web huggers! In today's tutorial we will learn how to use the Google Hacking Database (GHDB) developed by Exploit Database, to find vulnerable web servers and "juicy" information.

Google has finally released the next version of the world's leading operating system—Android 6.0 Marshmallow. This latest iteration isn't as much of a visual overhaul as Lollipop was, but it packs in more new functionality than almost any update before it. Awesome features like Now on Tap, granular permissions control, and a deep sleep battery-saving feature called Doze round out the highlights, but there is far more to it than that.

Hello My Fellow Hackerzz.. This is my first How-to and i'll be updating the “Hacking Android Using Kali” to msfvenom and some FAQ about known problems from comments. So Here we GO!!

Accidentally deleting important files can happen as easily as swiping left on something and watching it disappear into the ether. Of course, Apple allows automatic backups through iCloud, which ensures that your data is always stored safely in the cloud in case of emergency.

When attempting to gain access to a server, there may come a point when you need to get around file upload restrictions to upload something. If we can find a way to get around the restrictions, then we can upload anything we want to the server, effectively compromising it. That is what we'll be doing here today, so let's get started!

A no-carb, gluten-free substitute for breadcrumbs. Sounds and probably tastes like cardboard, right? Unless you're talking about Pork Dust. Yes, you read that right. Pork. DUST.

This tutorial is for people who want to try different types of hacks in an environment that is the same for everyone so it will help people to ask questions and learn. This series assumes you know how to run a VM and network them together. This series also assumes that the services running on the Metasploitable machine are needed to be running.

Well, this is my first article so if it sucks tell me...lol!! Story Time

Hi, everyone! Recently, I've been working on a pretty interesting and foolish project I had in mind, and here I'm bringing to all of you my findings. This guide's main aim is to document the process of building an Android kernel, specifically a CyanogenMod kernel and ROM, and modifying the kernel configuration to add special features, in this case, wireless adapter Alfa AWUS036H support, one of the most famous among Null Byters.

When you think of Terminal, you probably imagine some hacker sitting in front of their computer in a dimly lit room trying to break into an FBI database. In reality, it's just a simple tool that can make using your Mac much easier.

Welcome back, my greenhorn hackers! One of the most important issues any hacker must address is how to get past security devices and remain undetected. These can include antivirus software, intrusion detection systems, firewalls, web application firewalls, and numerous others. As nearly all of these devices employ a signature-based detection scheme where they maintain a database of known exploits and payload signatures, the key is to either:

While the app switcher in iOS makes it easy to go from one open app to another fairly quickly, it's still not a great option if all you want to do is return to the previous app you were in.

All of Apple's products are praised for being extremely easy to use. So much so, that your grandma can pick one up and be a "pro" within a few hours. However, this isn't necessarily a good thing for us real power users who want more granular control of our devices.

Meet the Wonderbag. The "first non-electric slow cooker" uses an insulated bag made of poly-cotton fabric, polyester, and repurposed foam chips. You bring your one-pot meal to the desired cooking temperature, usually via the stovetop. Then you turn off the heat, pop the pot into the Wonderbag, and it will continue to cook thanks to the retained heat in the bag.

An app called Launcher was released for iOS 8 last September that let users open any installed app directly from a widget in the Notification Center pull-down. For some reason, Apple didn't take too kindly to this and banned Launcher from the iOS App Store just a few days after its release.

Welcome back, my greenhorn hackers! Digital forensics and hacking are complementary disciplines. The better you are at digital forensics, the better hacker you are, and the better hacker you are, the better you are digital forensics. Unfortunately, few people in either profession cross these discipline lines.

As someone who loves to run around my neighborhood, the Apple Watch feature that excited me the most was the ability to go out and exercise while listening to music, all without having to lug my iPhone around.

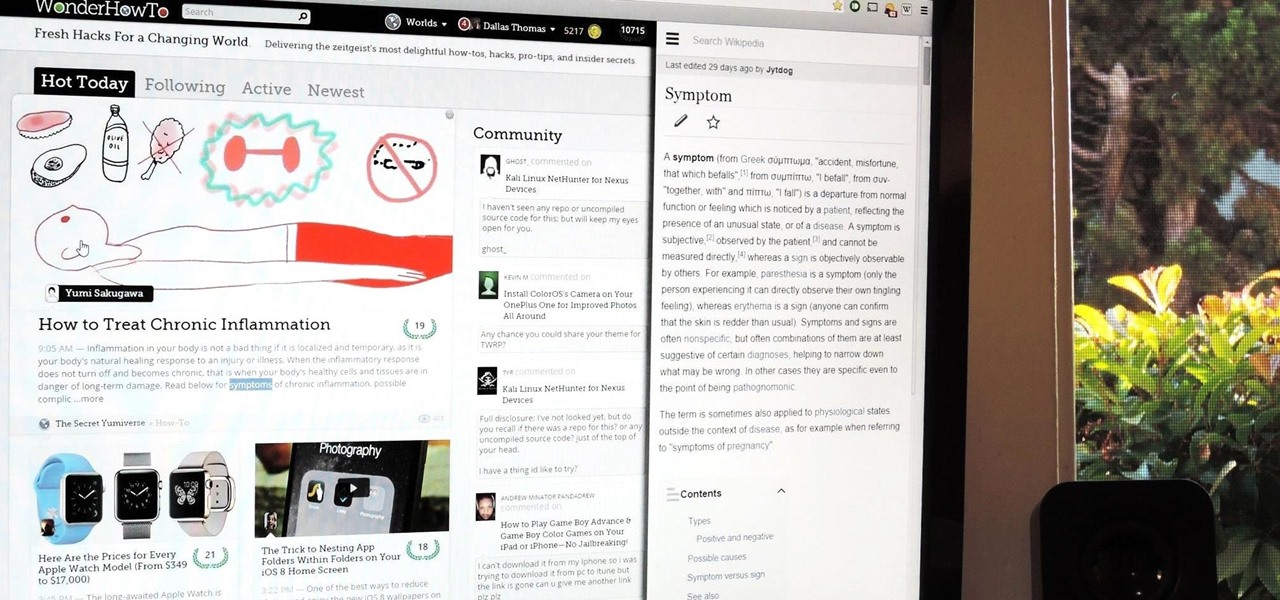
For all of the flak that it catches, Wikipedia is still a great source of information. Contributors take their work very seriously, so the vast majority of information is cited, and the site serves very well as a starting point to learn about a new topic.

Back when CRT and plasma monitors were still a thing, screensavers served a purpose beyond just aesthetics: the moving images and patterns prevented static images from being burned into the display.

Are you a lawyer who's married to a computer programmer? Chances are you might not have even dated if you first met online.

You didn't have to attend this year's CES to have gadget envy. There are so many great smartphones, computers, laptops, and other gadgets available in the market that the real challenge becomes choosing the right one to fit your needs and your budget.

The majority of Android web browsers carry a "desktop mode" feature that makes mobile websites look like normal computer versions. Mobile versions are designed to work faster and more efficiently on smartphones, but sometimes the desktop version looks better on large displays or has additional features not included in the mobile one.

Getting caught using your iPhone at school or work (when you're using it for personal reasons) can be a little bit embarrassing. Even worse, it can be detrimental to how you're perceived by your teacher or boss. But sometimes you just have to beat that next level of Candy Crush, view a risqué photo on Snapchat, or send an important WhatsApp message.

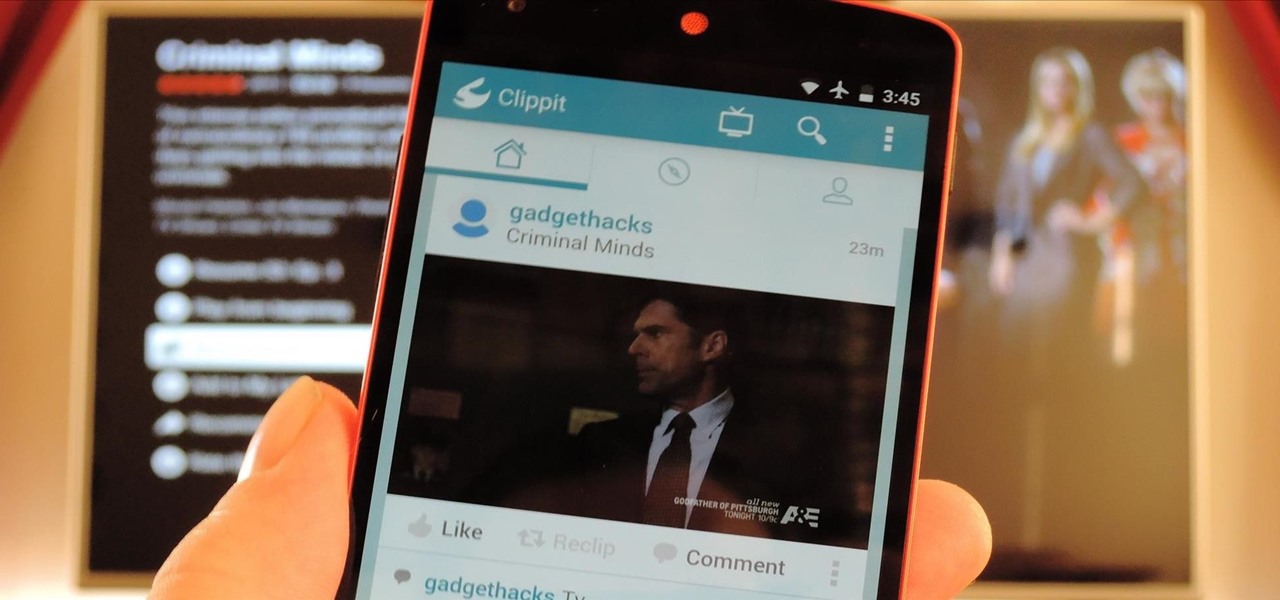
Social media is constantly evolving, and as a result, we're now capable of sharing much more than we were even just a few years ago. Television, on the other hand, continues to hold strong as one of America's favorite pastimes.

Who says you have to cook on Thanksgiving? If you need a break, have surprise guests in town, or simply don't want to be in the kitchen cooking all day long, never fear: you have options.

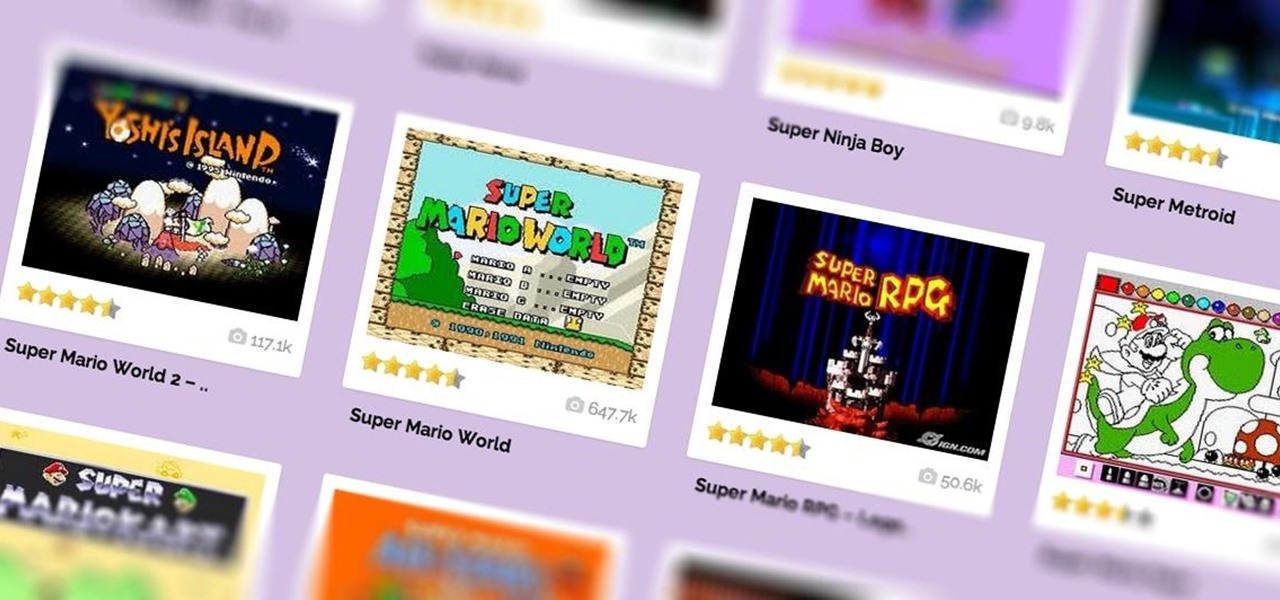
You'd be hard-pressed to find a working Super Nintendo in someone's house nowadays, but back in my adolescence it was gaming heaven. But now there's no reason to have an SNES console at home, because there are so many ways to play those retro games without one. All it takes is a good emulator.

Welcome back, my hacker novitiates! A short while ago, I introduced you to regular expressions. Regular expressions are a language that is particularly useful for finding complex text patterns in streams of data.

Automator takes the work out of common repetitive tasks in Mac OS X. One of my least favorites is resizing images for the web, so I created a drag and drop action to quickly do it for me.

In late 2012, Instagram CEO Kevin Systrom made a sudden and controversial change to his social media service when he removed Twitter Card support.

Amid rumors of a 6-inch phablet Nexus and the impending release of Android "L", Google posted—then quickly removed—a trio of ads for their industry-leading mobile OS.

Unless you're waiting in line for your iPhone 6 or iPhone 6 Plus, it's a sure bet that you'll be sitting by at home for your new device to get delivered today.

Now that you've updated your iPad, iPhone, or iPod touch to iOS 8, there's a lot of cool new things to explore. If you felt a little overwhelmed from all of the detailed information available in our Coolest Hidden Features of iOS 8 post, then I've got a simple breakdown of all of the new features available with quick links to their walkthroughs and pictures, if available. Watch the short video roundup, or skip below for the list.

Anytime you surf the web on your iPad or iPhone, Safari saves which webpages you visit, the information you enter into them, and other types of data. This not only make your internet experience quicker, but it'll also keep track of everything you're doing.