Imagine that you're the last person alive. After losing all of your loved ones, you thought you'd never see another human being in your life. Then, they arrive. The hoard of 15-year-old zombies looking for a cute British YouTuber so they may feast on his brains.

One booze hack that's been making the rounds for years is that inserting a spoon by the handle in a champagne bottle's neck will preserve its carbonation. This is one of those tips that I wish were true. Champagne is a great thing to have around on a special occasion, and it seems a shame to pour any leftovers down the drain once its lost its fizz. While there's lots of anecdotal evidence surrounding this trick, Harold McGee and Stanford University chemist Richard Zare debunked this myth as d...
Google is widely renowned for its mastery in using data to tailor specific search results and ads. Their Android and iOS search apps put this ability to use in finding the most relevant pages for your query, and their desktop site is the most-used search engine on the web as a result of it.

Google's new camera, aptly named Google Camera, has been all the rage since it was released onto Google Play last Friday. The main reason is the amazing Lens Blur feature that adds depth-of-field Lytro effects to photos, without the use of any expensive accessories or extra hardware, like on the new HTC One M8. The camera does this by utilizing a depth map through the processing of multiple images. Frame your photo, move the camera (phone) in an upward tilt or motion, and the software capture...

While rooting your Galaxy Note 2 certainly has its advantages—everything from increasing security to relieving the Power button of its duties—it's definitely not for everyone.
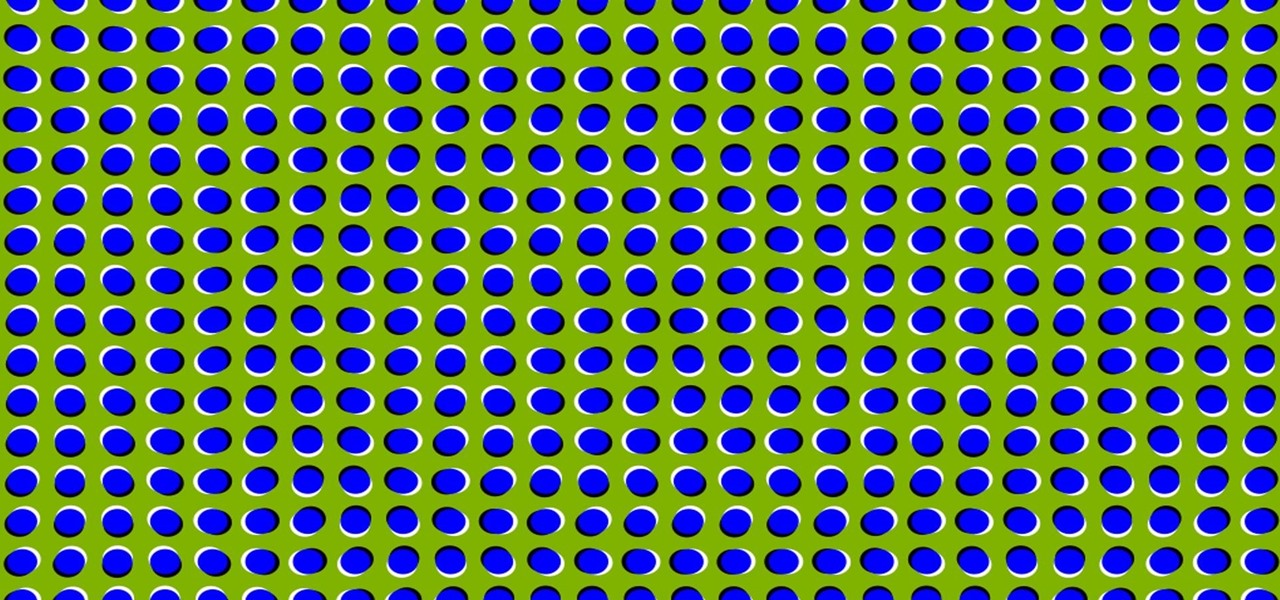
It's time to trip out with your tablet. If you're not looking to drain that precious battery life with a fancy-looking live wallpaper, then apply an optical illusion that appears to be moving on your Nexus 7 (or any other Android device) instead.

So, you've got a brand new PlayStation 4, but unfortunately, you've got "No Signal" now, too. You can't really game or watch movies on your new toy if you can't even bring up the PlayStation menu on your TV screen.

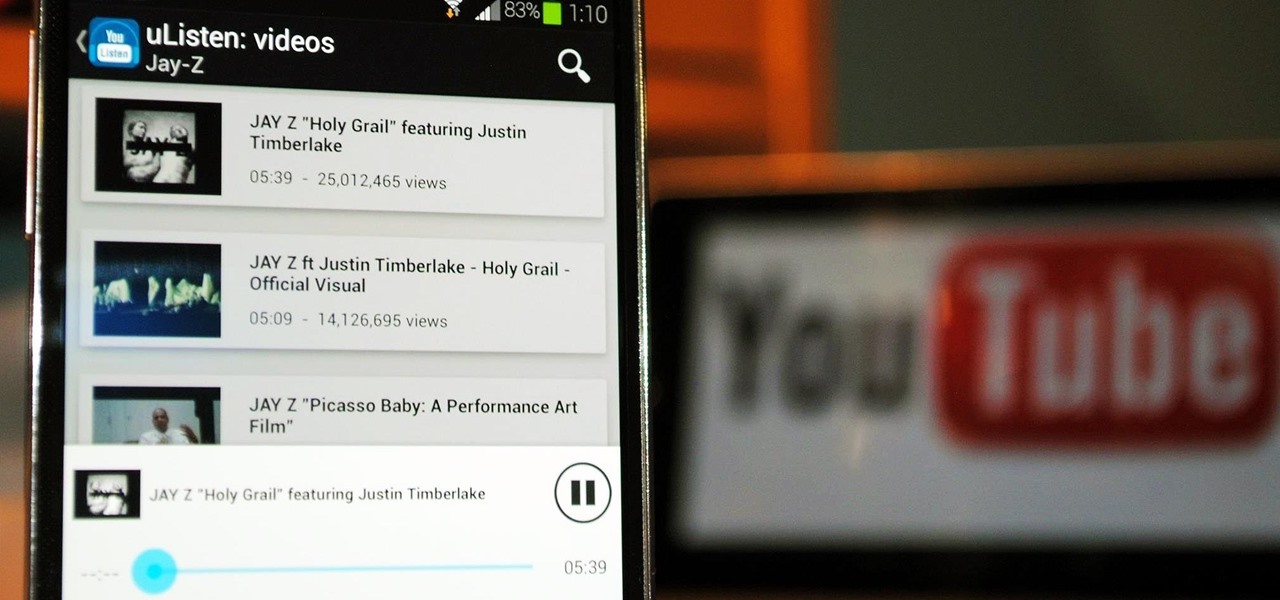
YouTube may have started out as a video-sharing site, but these days a lot of people use it as a source for music. When I'm browsing the internet on my desktop, I usually have a YouTube tab open in the background playing some music.

The dryer’s idler pulley provides tension to the dryer’s drum belt so the belt won’t slip when the drum is turning. It can become faulty over time due to increased friction. If your dryer is making a squeaking or squealing nose then the idler is probably faulty. Replacing this pulley is a simple project. Repair your noisy dryer with this step-by-step tutorial!

A mustachioed Italian plumber collects coins and battles bullets, plants, fish, mushrooms, and turtles in strange environments to save a princess held captive by a crazy, spiked-shell, bipedal tortoise.

If you want to play games that aren't in the iOS App Store, Apple makes it pretty tough for you. Usually, the only solution is to jailbreak your iPad or iPhone, but that's something most avoid because it will void the warranty and may cause potential bricking issues.

I've never understood gift cards. Aside from being severely restricted as to where you can use them, they're also a strange gift, especially if you don't shop at that particular store. Some even have expiration dates and service fees.

Some of my favorite games include Super Mario World, Super Mario Kart, Super Punch Out, and Super Metroid. If you still haven't caught on, I'm a big Super Nintendo fan. Growing up in the '90s meant spending Saturday mornings engulfed in front on my TV with the good old SNES running hard.

If you thought humans were reading your résumé, think again. Robots do, and their one solitary objective is to systematically crush the hopes and dreams of those who don't make the cut. Instead of paying a few humans to read thousands of résumés over a couple weeks, many companies use computer programs that can do the job in less than an hour. In fact, at least 90 percent of Fortune 500 companies use what they call an applicant-tracking system, aka rejection machines.

Craigslist is probably the greatest site ever created, and I'm just talking about it's classified section, both awesome and amazingly creepy. Seriously, spend 20 minutes scrolling through the personals and you'll never want to take your eyes off the screen. But I digress—Craigslist is also one of the most convenient places to buy and sell pretty much anything you can think of. I've used it to buy my bed, my old bike (which was stolen!), and my couch. And while Craigslist is great in many ways...

There are a number of reasons why you might want to trick a web server into thinking you're on a different operating system (OS) or web browser. One might be that you want to test the mobile version of your website from your computer. Or perhaps for some reason a website is restricted to a certain OS or browser and you wish to circumnavigate that barrier. Today's guide shows you how to do just that!

It's almost here. Another year has come and gone, and it's time to watch the Baltimore Ravens and the San Francisco 49ers battle it out in New Orleans for Super Bowl XLVII. For the truly football-obsessed, this Sunday is a day almost as exciting as Christmas. Personally, I just use it as an excuse to cook food that's way less healthy than usual since I never quite became a football fan (sorry, Dad).

I recently wrote about Twitter's super now app called Vine, which lets people create 6 second video clips that can be embedded in a tweet. Those videos have their own proprietary extension, but if you want to turn those 6 second videos into an animated GIF, you can now do so thanks to developer Esten Hurtle, who created VineGifR, a seamless way to transform your (or someone else's) Vine movies into GIFs.

The number of passwords I have for different websites and emails is easily in the triple digits. And if I had to actually remember all of those individual passwords, I would be locked out of accounts on a daily basis.

Skype is a great way to stay in contact with friends and family over the internet, and people tend to share a lot in their chats, so why not try and find a way to hack it! Once a Skype account is hacked, you can view all conversations within the last three months, see how long each video call was, and even access files that were shared through chat.

There's really nothing safe about transmitting sensitive information electronically, but even if it gets there safely without being seen by prying eyes, there's no guarantee what happens to it once it reaches its destination. And let's face it, there are some things that you just don't want floating out there forever. So what can you do? Whether you want to send an email, a text, or a link, there are ways to send messages that self-destruct so that once they're read, they immediately vanish. ...

If you're like me, you've already spent a ton of money on your costumes, your badge, and your hotel room, and now you're looking for ways to cut costs. There are all kinds of ways to save money at DragonCon, but many of them involve violating the rules in some way, such as not buying a badge, sleeping on the floor in a hallway somewhere, etc. However, the one thing you can do that is totally not against the rules is eat for free. It requires a little self-discipline and a willingness to eat w...

It's summer, which means vacations, barbeques, and, most importantly, no school. But that doesn't mean you can't learn something while you lounge by the pool. Schools and organizations all over the country are offering online courses taught by real professors—for free.

3D printing has been around for a while, but until recently it was used mostly for prototyping and research. Now, with technological advancements, it seems like everyone is using 3D printers, from crime scene investigators to garage hobbyists and hackers. Below are some of the most innovative uses people have come up with so far.

There are lots of people who want to stay anonymous online, and lots of reasons they want to do this. Staying anonymous on the internet isn't easy, and it's probably possible to trace almost anyone with enough time and resources. A lot of people think that they're completely secure with just one method of cover. For example, a lot of people thought anyone using the Tor network was nearly untraceable, but then things like this often cast doubt on just how secure these networks are. Unless you ...

Firstly, let me say a few quick things: Once built, this is a lazy (one button) way to harvest melons, but this is going to be a complex and lengthy build.

There are loads of reasons for somebody to want to recover a Windows password, and there are lots of different ways of doing it. My favorite of all of these ways is to use a piece of software called Ophcrack because:

Bokeh (which translates to "blur" in Japanese) is a photography technique referring to the blurred areas of a photograph. Basic bokeh photographs often have one point of focus, while the background falls away into a dreamy, blurred haze.

Learn how to use a site: http://www.copyscape.com to check if people are stealing content from your website.

You can learn how to drive traffic to your website using links. The most important thing is to get people to your website. You can not spend hours and hours writing emails to people who steal your articles.

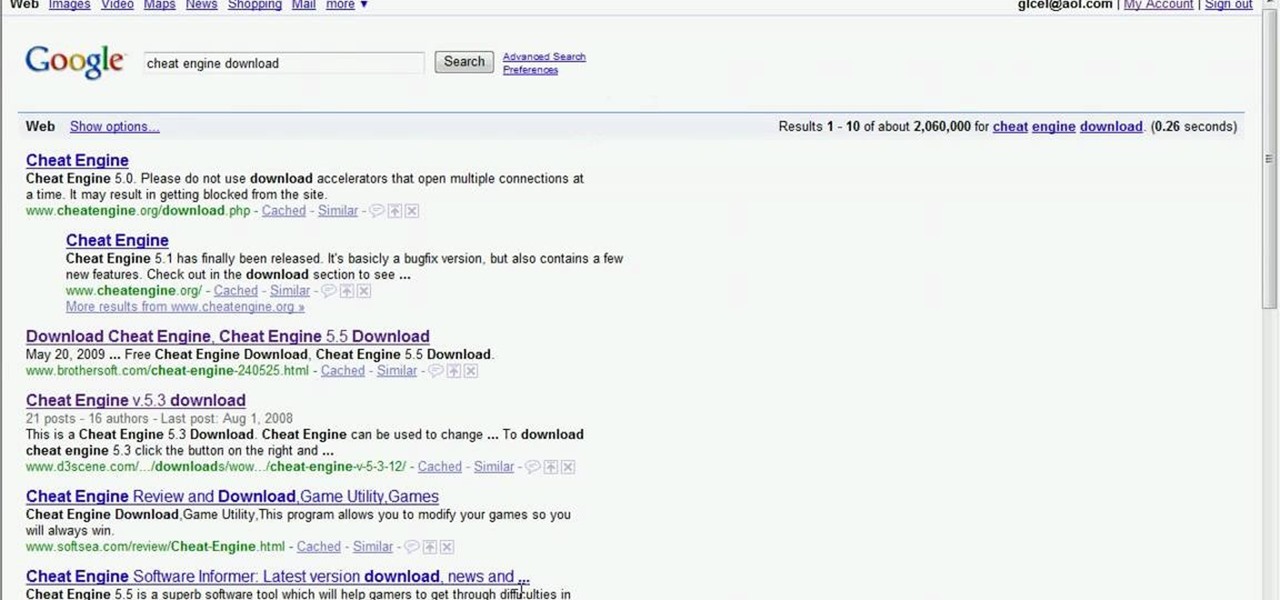
This video tutorial will show you the one thing everybody wants to know… where's the Cheat Engine 5.5 download at? There's nothing to getting Cheat Engine on your computer. Once you have it, you can start hacking and cheating all of the flash games you play on Facebook and MySpace and every other site with online games. So, to download Cheat Engine 5.5, you just need to Google it and you'll find it in the first result. Or you can just go to http://www.cheatengine.org or the download page for ...

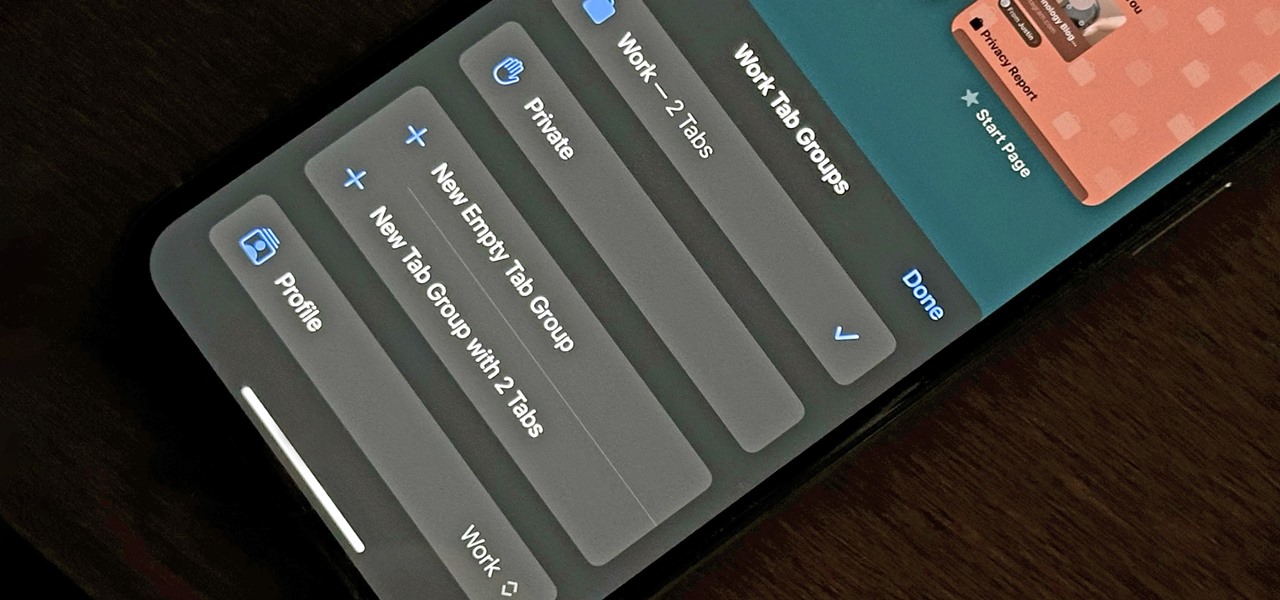
Apple is finally adding profiles to Safari, so you can now keep your personal, work, and other topical browsing totally separate in their own instances, with their own history, cookies, website data, and active extensions.

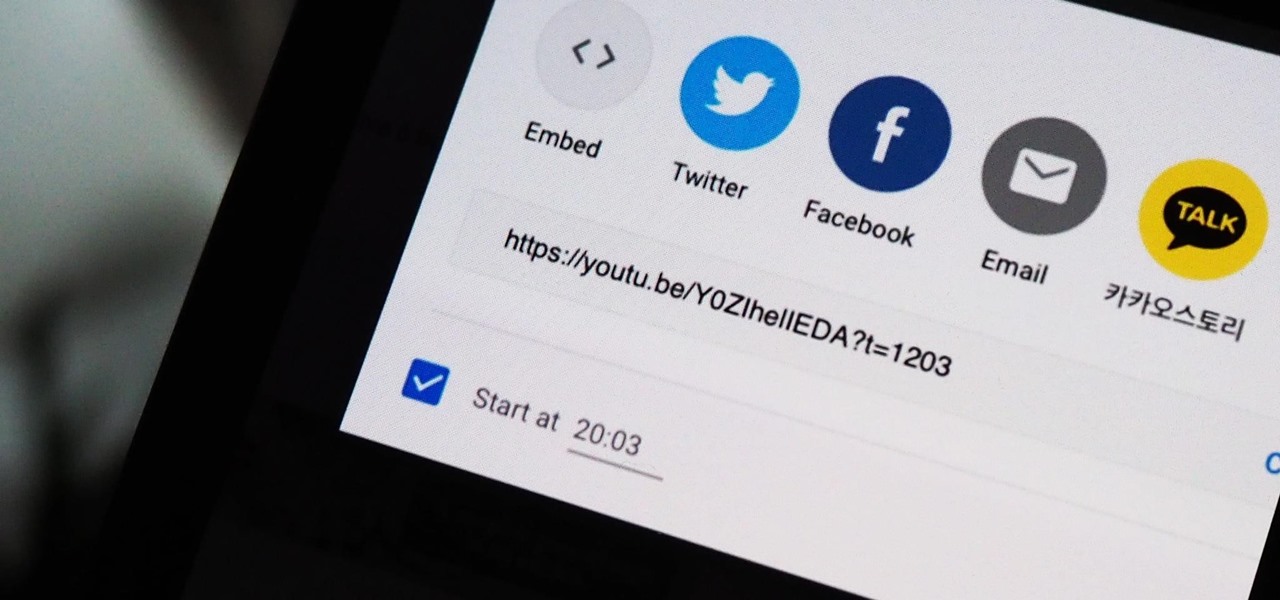
You can add a timestamp to any YouTube video in just a few clicks from the desktop website on your computer but not from YouTube's iOS or Android app. Until YouTube adds a "start time" when sharing videos from the mobile app, you'll have to use one of these workarounds on your phone or tablet.

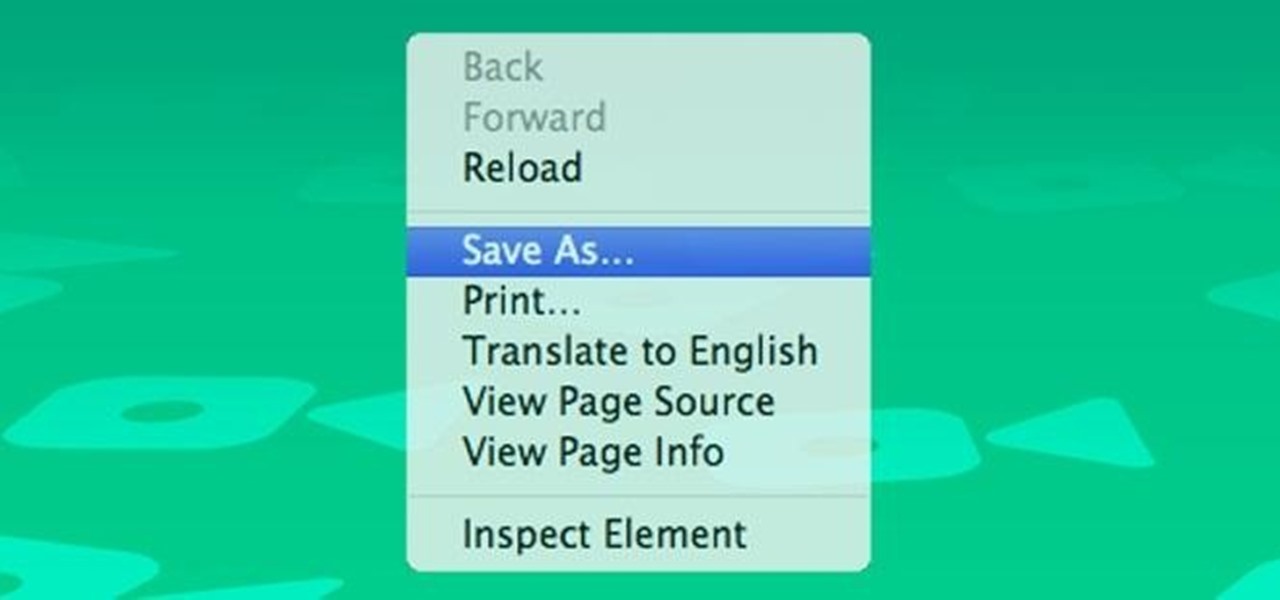
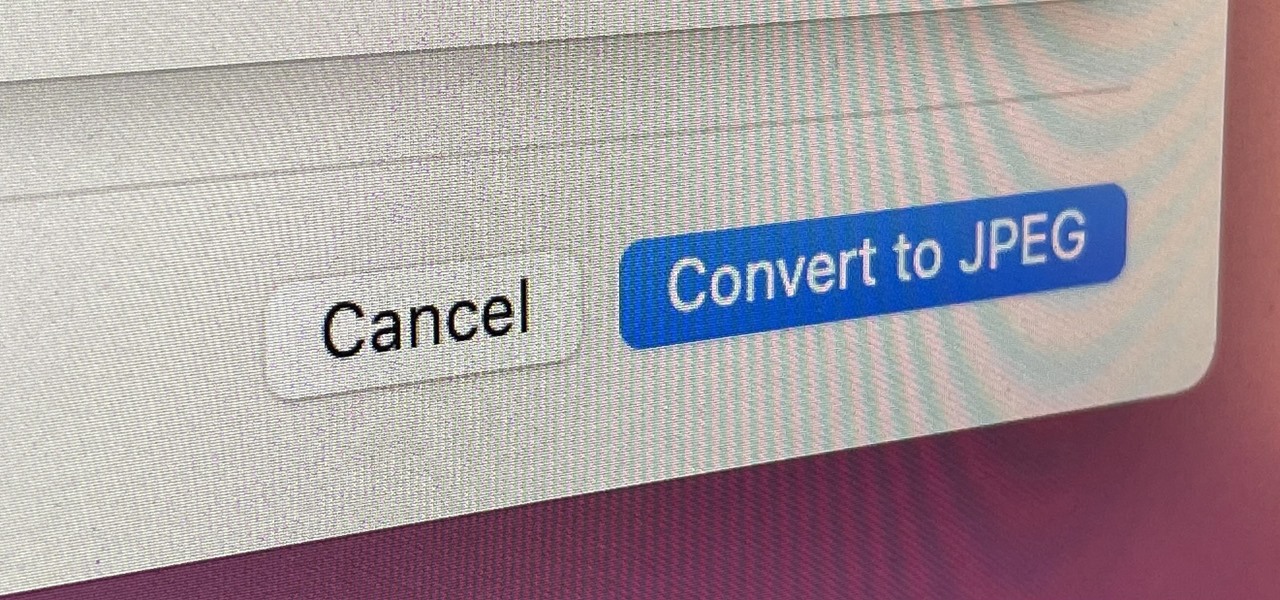
If you regularly run into issues opening images that use the .heic extension, the easiest solution is to convert the file into a more compatible format. Using apps like Photos and Preview on a Mac makes the process simple, but macOS Monterey just streamlined the process so that you don't even have to open an app anymore.

There are tons of tools out there that do all kinds of recon, but it can be hard to narrow down what to use. A great way to be more efficient is by taking advantage of scripting. This doesn't have to mean writing everything from scratch — it can simply mean integrating existing tools into a single, comprehensive script. Luckily, it's easy to create your own subdomain enumeration script for better recon.

GTFOBins and LOLBAS are projects with the goal of documenting native binaries that can be abused and exploited by attackers on Unix and Windows systems, respectfully. These binaries are often used for "living off the land" techniques during post-exploitation. In this tutorial, we will be exploring gtfo, a tool used to search these projects for abusable binaries right from the command line.

Microsoft's built-in antimalware solution does its best to prevent common attacks. Unfortunately for Windows 10 users, evading detection requires almost no effort at all. An attacker armed with this knowledge will easily bypass security software using any number of tools.

Getting files from an Android device to a Mac or iOS device is not always easy or convenient, and the same goes for transferring content from a Mac or iOS device to an Android device. But we're here to tell you there is a better way than using USB cables, email, and cloud storage, and it gives you the look and feel of AirDrop.

A macOS computer can reveal a lot of information about the owner, including which Wi-Fi network they have permission to access. With an Arduino-based attack, we'll use a five-dollar setup to inject a rogue Wi-Fi network and steal the list of trusted Wi-Fi networks, allowing us to see where the computer has been.

Network enumeration is one of the essential phases of an attack, but it can take a lot of time and effort depending on the size. We've all been spoiled by Nmap and similar tools, and while there is a learning curve involved, they are extremely useful. But there's also GoScan, a tool that builds upon Nmap, offering an automated way to enumerate networks and services quickly.