Your iPhone has a lot of personal information contained within it, so of course you want your device to be secure. You don't want that information getting into the wrong hands — or any hands other than your own, for that matter.

Apple's iOS 11 is finally here, and while they showed off several of the new features it brings to your iPhone, iPad, and iPod touch back at WWDC 2017, they've only just touched the surface of what iOS 11 has to offer. There are a lot of cool new (and sometimes secret) features to explore, so we've collected them all here for you.

On July 20, 1969, humans set foot on the moon for the first time. But some say our microbes beat us there. With the Space Age came new questions about microscopic invaders from outer space and concern about where we are leaving our microbial footprints. The questions are even more relevant today.

Besside-ng is the hidden gem of the Aircrack-ng suite of Wi-Fi hacking tools. When run with a wireless network adapter capable of packet injection, Besside-ng can harvest WPA handshakes from any network with an active user — and crack WEP passwords outright. Unlike many tools, it requires no special dependencies and can be run via SSH, making it easy to deploy remotely.

Step 1: What Exploit Development Is and Why Should I Be Interested on About This Topic

Android comprises an entire ecosystem of apps, games, functions, and features, so it would only make sense that it has its own lexicon. Words, phrases, and acronyms that didn't exist ten years ago are now used in an off-the-cuff style by developers and support technicians across the web.

It always looks different when it's not about you. The Internet is our world's Alterego. Those many bits don't really make sense unless we want them to be valuable, to mean something.

My first encounter with a phablet was late last year with the AT&T version of the Samsung Galaxy Note 2, having never touched or even seen its highly-acclaimed and pioneering predecessor. Initially, I was a bit overwhelmed by the enormous screen and taken aback by the dated stylus, which brought up ugly memories of my dad using his ten pound PalmPilot.

The very first banknotes were used by the Chinese in the 7th century, during the Tang Dynasty. Before it was used as an actual currency, paper money was part of a deposit system in which merchants would leave large amounts of coins with a trusted associate and receive a paper receipt for the transaction. The reason was simple — the copper coins used as currency then were heavy.

Thought I would cross-post a piece I did a while ago.

To some, SCRABBLE is just a board game to play during family game night or during a casual get-together. Others think of SCRABBLE as a mere hobby. But with any activity, there will always be fanatics—the ones who would rather sell their soul than stop—the ones with a constant yearning for self-improvement—the merciless.

Ever wanted a specific directory in your site to be available only to certain people? Password protecting a directory can be done several ways. In this cPanel video tutorial you will learn how to password protect a directory. Make sure to hit "play tutorial" in the top left corner of the video to start the video. There is no sound, so you'll need to watch the pop-up directions. Password-protect a directory in cPanel.

I was looking around on this site and this article caught my eye. It was about hiding text in ADS or Alternate Data Streams. While this is nothing new in the tech world, it seems that more and more people are looking at ADS for one reason or another.

This article describes the very basics of compiling a program on Linux. It is targeted at the absolute beginner. Sometimes beginners search for programs on the web for their Linux systems, and is faced with the reality that they have to compile the program themselves, either because there exists no binary for their architecture, or the author of the program just doesn't release any binaries at all, but only sources.
Warnings this only for educational use i dont take responsiblety for any use of this article if you want to use this for use at a school plz contact me at sebzy4@hotmail.com hi im a computer enginer/programmer (NOT games) but i am good at hacking and i want to help. notise that this is just a help site not hacking site but this will help firstimers

This is it! That last basic mission. Last Friday's mission was to accomplish solving HackThisSite, basic mission 11. This final mission in the basic series was made to give us the skills and a place to apply our Apache server knowledge. This will teach us how to traverse through awkward and custom directory structures.

Update 2: 1.9 Version3 is currently out. Click here to download and install 1.9 Version 3. Update: 1.8 is now officially out! It'll prompt you to update the next time you launch.

Friday's mission was to accomplish solving HackThisSite, basic mission 7, which required us to learn some basic Unix commands. If you have any prior experience using Unix commands, this should be a breeze for you if you sit and think for a second.

A proxy is a server that lets a client to connect to it and forward its traffic. This enables a certain "layer" of protection by masking your IP. An IP address can be used to learn your location and track you on the Internet, thus eliminating any form of anonymity that you may have.

This is a tutorial showing you how to easily hack flash (.swf) games! You only need two things:

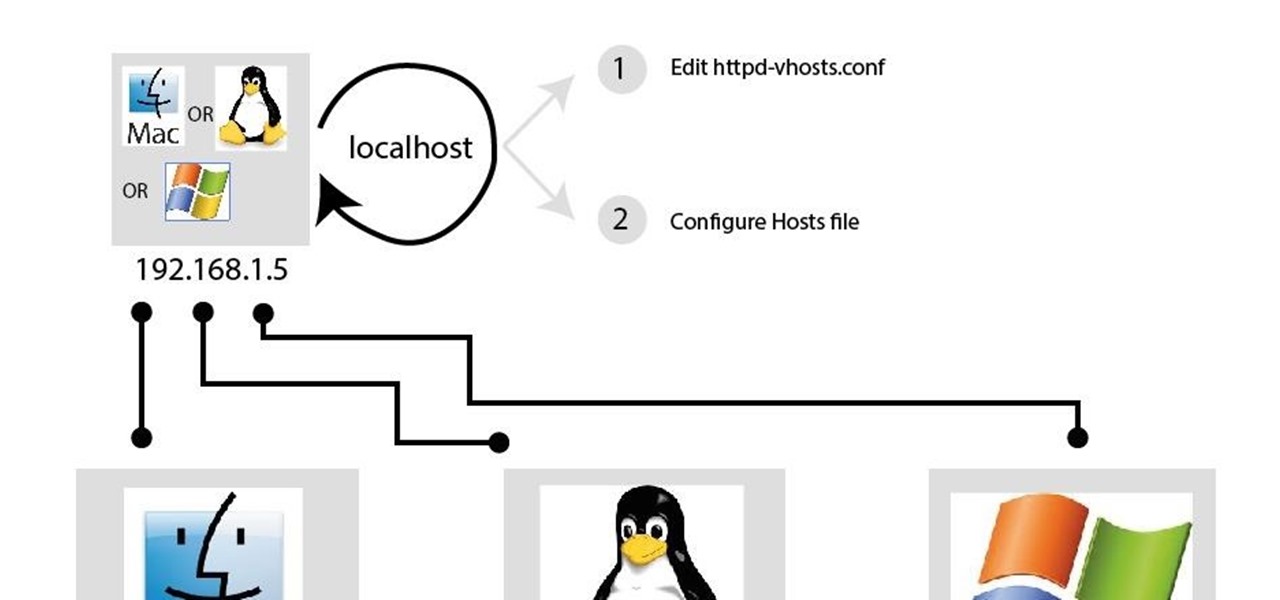
In my last article, I discussed: How to install xampp

Null Byte is looking for forum moderators! Last Friday's mission was to accomplish solving HackThisSite, basic mission 9. This mission delves a little further into Unix commands and remote directory traversal (which is just a fancy term for going through folders blindly).

More password cracking action from Null Byte! Today we aren't going to be cracking passwords per se, rather, we are going to learn the basics of generating rainbow tables and how to use them. First, let's go over how passwords are stored and recovered.

This may be an old trick, but it is still very useful. Head.js proudly proclaims that it is the only script you need in your head. You can use it to parallel load all your scripts. This is much faster than loading them one by one.

A directory of amazing movie posters from Korea. Its amazing how much type they put on a poster, far more then American movie posters.

To the displeasure of many loyal Firefox users, Mozilla has been deploying what seems like a new marketing strategy to "catch up" to Google Chrome. I have no idea if this is because the version number is higher than theirs, but it is downright annoying. It's not all complaints, though. Firefox has done an amazing job at completely revamping its source code and redesigning all of its engines, making it a more than worthy competitor to Chrome. However, we are displeased with Firefox because eve...

File recovery on Linux is a bit different than Windows. It requires different software than the Windows counterparts because every OS has their own file system. Windows uses NTFS, or FAT file systems, while on the other hand, Linux uses ext-based file systems. I personally use ext4 file system because it's the latest and greatest ext-journaling system and supports a large level of directory recursion and file sizes, but most installations still use ext2 or ext3. When files are deleted from a ...

If you're having a little trouble operating your newly purchased Motorola Nextel i1000plus cell phone, let Sprint help you out. This Sprint interactive mobile phone tutorial takes you through every step necessary to fully familiarize yourself with the i1000plus cell phone by Motorola. This instructional tour will help you learn how to use Nextel Direct Connect - Digital Walkie-Talkie, Nextel Online - Wireless Web, Mobile Office Email, Nextel Mobile Text Messaging, 100-Number Phone List Direct...

Some of you might be using Tor to host hidden services, and some of you might not even know what hidden services are. If the latter's you, do not miss this article. Why? Because you can host your websites and services on the I2P darknet. It's safe and secure—it's anonymous.

Here's a nasty little Null Byte. An open redirect vulnerability was found in both Facebook and Google that could allow hackers to steal user credentials via phishing. This also potentially allows redirects to malicious sites that exploit other vulnerabilities in your OS or browser. This could even get your computer flooded with spam, and these holes have been known about for over a month.

Last Friday's mission was to accomplish solving HackThisSite, Realistic 5, the fifth and last in my series of realistic hacking simulation missions. This time, telemarketers are invading people's privacy, and it was up to us to stop them! The job was to get root on the site and delete the contact database in order to return the right of privacy to its victims.

The Website above is about congress. It has the recent activities of Congress. It also allows you to contact them to stop any law which you might disagree with. This is a great way to help make a decision that might effect others.

Linux can have the most beautiful interface in the world, because it is simply what you make of it. You can change every little detail with relative ease because that's what Linux is all about: Freedom and OpenSource.

Hello everyone, I am Brandon Hopkins from TechHut and I am going to be showing you how to install Minecraft Texture Packs on Windows, Linux, and Mac. I will also link you to one of the best Texture Pack I have used and a website where you can download 100+ different texture packs.

hey everyone ,im a newbie here at null byte and i want to say thanks for all the tutorials and information people give me here.

Social networks like Facebook and Google+ are great for staying connected with family, friends and coworkers—even fans. But sharing and communicating with practically anyone in the digital realm has alienated us from most of the flesh-and-blood beings we see everyday—our neighbors. How well do you know your neighbors?

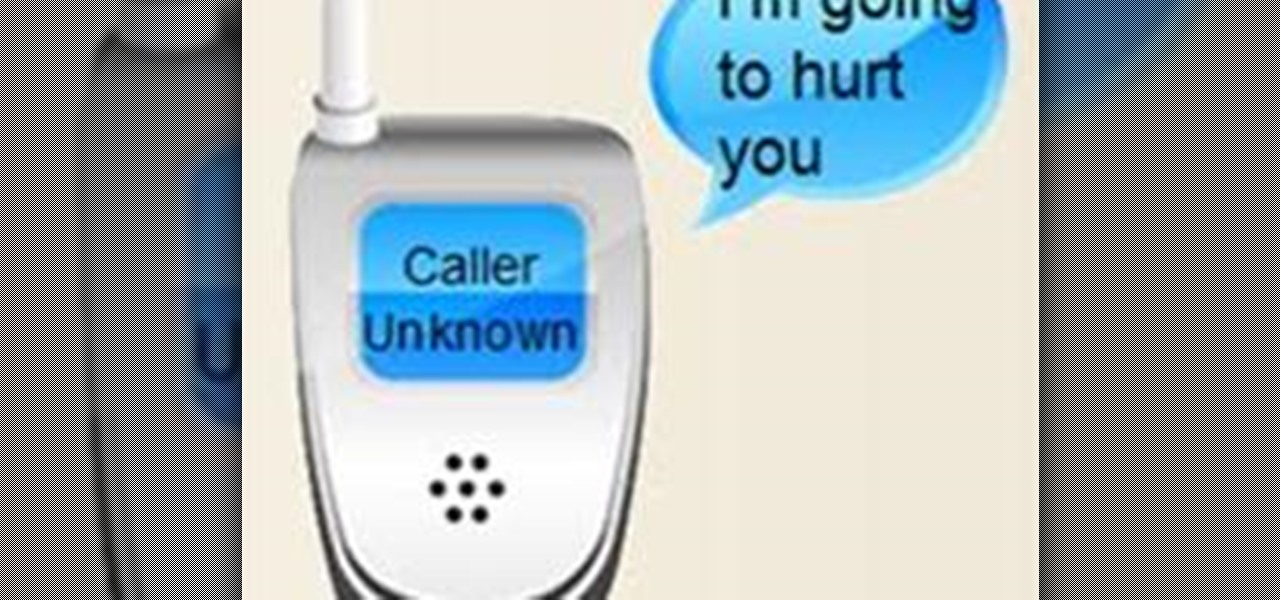
Prank Calls, Masked NumbersWho is calling your phone or your child's? Pranksters use a lot of tricks to make sure they can get on your nerves. Being able to trace prank calls is important because you're not going to learn much from your Caller ID, since most prank callers use an unlisted number - such as, a cell phone number. Many also use special code *67 to mask the number so your Caller ID will show "Blocked Number" or "Private Number". There are a lot of mild cases of so-called phone bull...

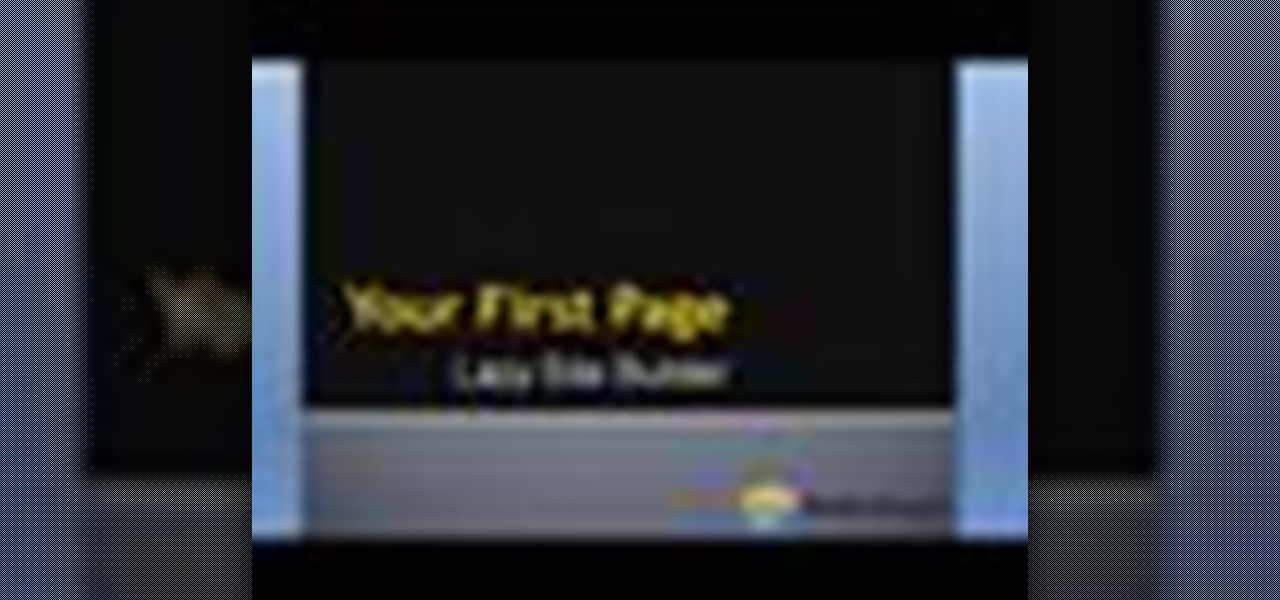
This is a quick overview of how you can create your first webpage with the Lazy Site Builder. PART 1: setup your site

Here's something fun for the Null Byte community to do—a coding competition! This week, I wanted to get everyone involved by offering you all a nice library of possible program types to choose from and try to code. At the end of this competition, all of the submitted programs will be reviewed by the community and myself. The coder that receives the most votes will be dubbed THE BEST.