Dutch police are using a system very similar to Pokémon GO on smartphones, but they aren't walking around trying to catch little pocket monsters. The purpose of this system is to give augmented reality help to first responders who may be less qualified to work a fresh crime scene. If successful, the idea of a contaminated crime scene could be a thing of the past.

Some of the best Android apps are not hosted on the Google Play Store, and that means you have to sideload them if you want to get their awesome functionality. But without the Play Store, these APKs are never automatically updated, so your only choice has been to scour the internet for a newer version when you need a bugfix.

While Leap Motion and Microsoft are looking to capture natural human motion with cameras, Enflux figured out how to do it with a shirt and pants that feel completely natural.

Security journalist Brian Krebs recently suffered a record-breaking DDoS attack to his his website, clocking in at or near a whopping 620 Gbps of traffic. Krebs' site was down for over 24 hours, and it resulted in him having to leave his CDN behind.

When Facebook purchased WhatsApp for $19.3 billion back in 2014, we all knew this was coming—it just took longer than we thought. But starting today, the data mining became official, and now, information from your favorite messaging app is no longer out of reach for the world's biggest social media site.

Snapchat has already found a compelling way to create advertisements in augmented reality with their branded filters, but they continue to experiment with new ways to monetize the bridging of the real and digital worlds. Their latest idea, which requires users to "snap" an image to unlock content, could succeed where QR codes haven't.

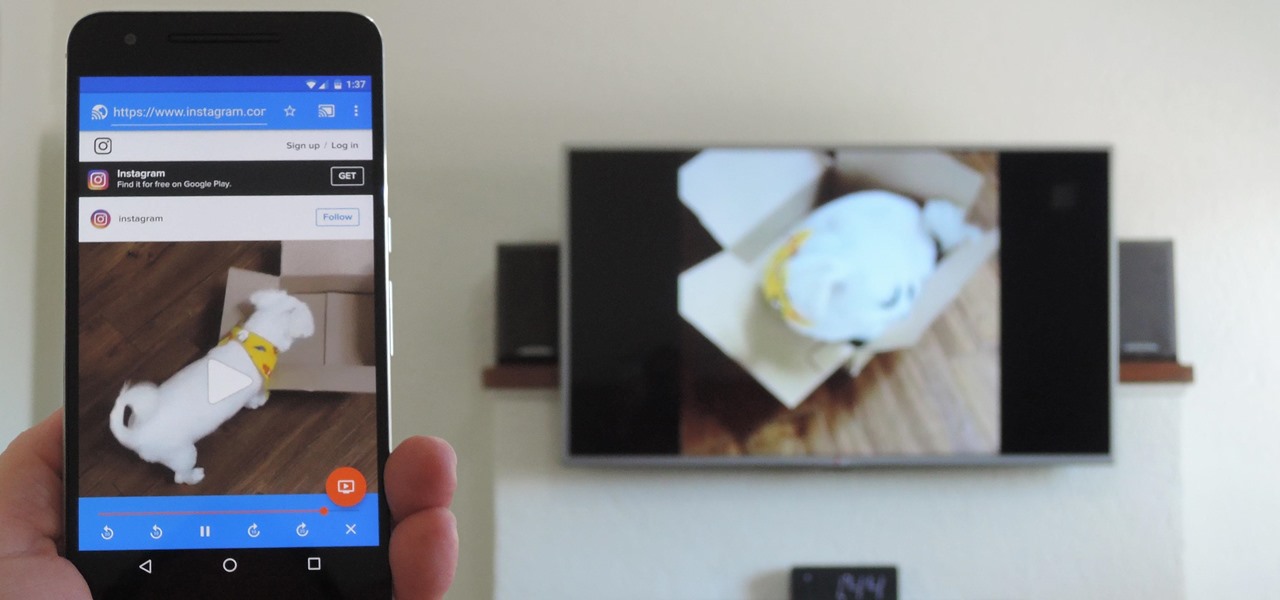
The Google Chrome browser for Android allows you to cast quite a few different videos from the web to your TV, but some sites actively disable this functionality, and others have outdated video players that won't allow for it. For example, Instagram's mobile website won't let you cast any videos, and the official app doesn't support Google Cast.

We've been hearing rumors for months now that suggest Apple will be getting rid of the 3.5 mm headphone jack in the iPhone 7, which will presumably be replaced by an adapter that connects your earbuds directly to the Lightning port. But finally, thanks to Vietnamese site Tinhte, we now have some hard evidence to back up this claim.

When the Samsung Galaxy S7 and S7 Edge came to market in 2016, they were universally praised as being the pinnacle of Android smartphone design, even topping Consumer Reports' smartphone ratings.

If you want free Poké Balls and eggs when playing Pokémon GO, you can find them at PokéStops in variation locations around your city, which are marked with towering blue icons on your map. Once you're at Level 5, they'll also grant you Potions and Revives to help you in your battles against other trainers, so they're definitely something you should be visiting whenever you can.

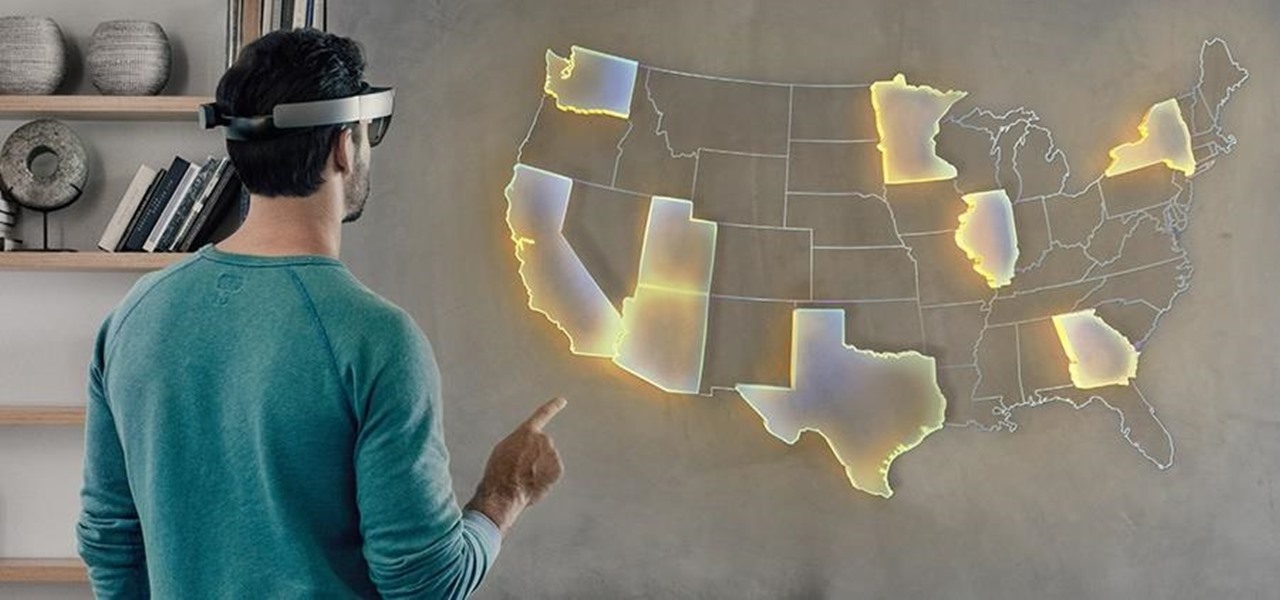
We don't know exactly what form 5G cellular technology will take, but it intends to bring faster Wi-Fi-like performance to mobile devices. While that'll provide major advantages to lots of connected technology, PC Magazine notes that it could be what augmented and mixed reality needs to become widely adopted.

Mixed reality (MR) feels like an amazing, almost mind-blowing futuristic technology—but only once you've experienced it for yourself. Words, images, and even videos simply cannot describe the experience in full. If you want to really peer into the future and experience MR for yourself, you can sign up and just go in many cities.

If you're tired of Google tracking you, but love how Chrome works, CyanogenMod has you covered. Their browser is called Gello, which is based off Chromium, Chrome's open-source counterpart. It's basically a souped-up version of Chrome—without all of the intrusive Google stuff. So if you're uncomfortable with Google displaying personalized ads based on your browsing history, or using your location to bring the "Physical Web" to your phone, you won't have to worry about any of that with Gello.

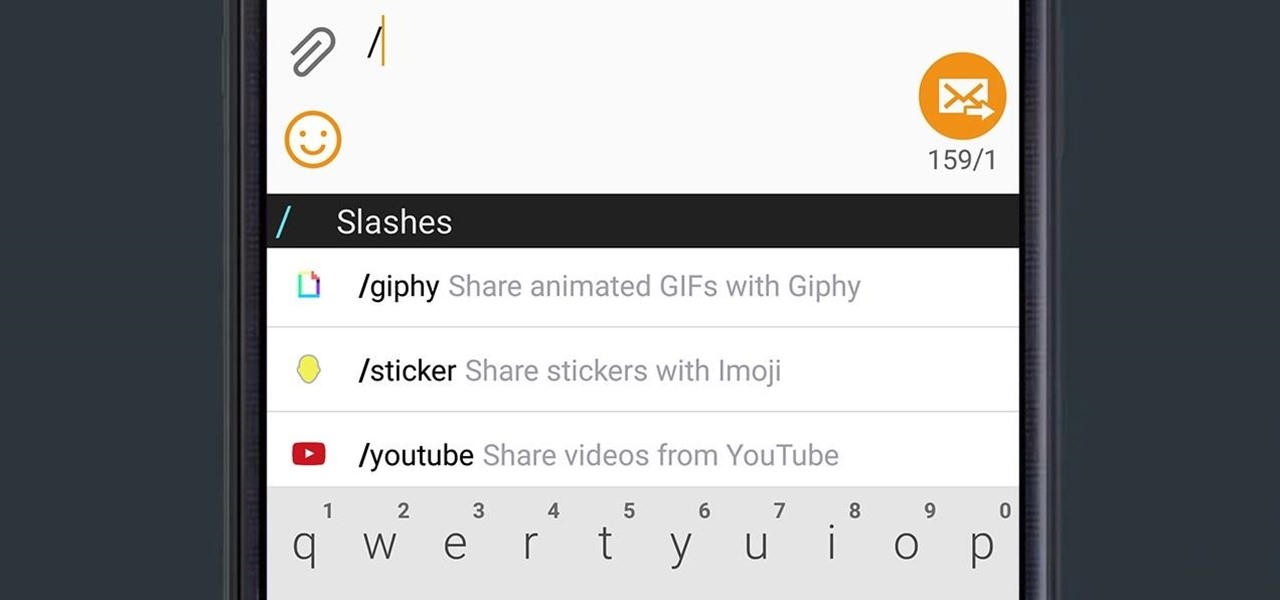
Google released an amazing swipe keyboard a few months ago called Gboard that has Google Search built right into it; This makes adding pics, GIFs, videos, and links to articles, restaurants, and shops a breeze. It even helps you search for emojis! The only problem is that Gboard is for iOS devices only, meaning only an iPad, iPhone, or iPod touch can use its magical powers.

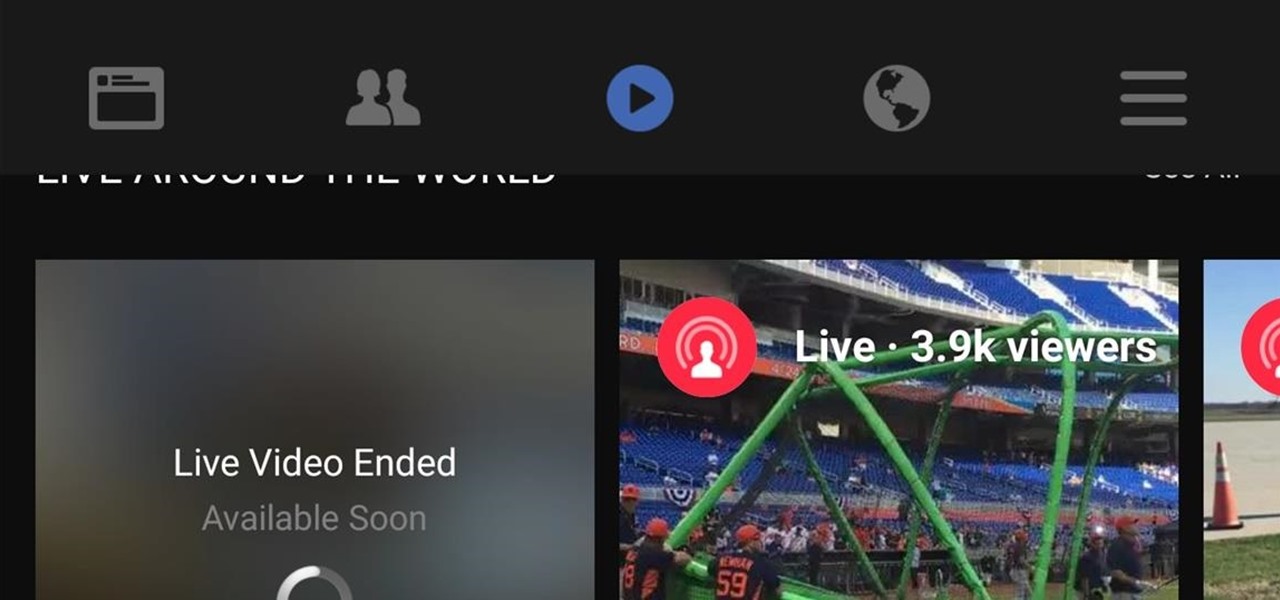
It looks like Facebook is adding a "Live" tab to the navigation bar for its Android app, and the feature has already been turned on for at least one user. A screenshot uploaded by Niko Steele shows the new feature, which lets you search for and watch live video directly on the Facebook app. Right now, you need to already be friends with a person who is streaming or be following a page or personality to receive a notification that live video has started. Some pages will post about an upcoming ...

For generations, parents have been struggling to come up with innovative ways to get their kids to eat their vegetables. They'll cut them into fun shapes, bake them in cheese, batter, and deep-fry them.

Welcome back, my novice hackers! As many of you know, recon is crucial to a successful hack/pentest. In most cases, hackers spend more time doing good reconnaissance than actually hacking. Without proper recon, you are simply guessing at what type of approach or exploit is going to work and, as a result, your time is wasted without any useful outcomes.

Have you ever run across a Facebook post that you don't necessarily want to "Like," but you're not really passionate enough about to bother stringing together a couple words for a comment? Well, you're in luck, as Facebook added five new "Reactions" that let you do more than just like a post, and they're now live for everyone.

In this how-to we will be sending an email with an image we get from a php script after running some fishy code. What you'll need

YouTube's massive user base comprises almost one third of all people on the internet, and collectively, users spend well over 100 million hours on the site watching billions of videos each day. Add it all up, and this means that YouTube is viewed by more people than any U.S. cable network—making it by far the favorite "TV station" of the internet generation.

Welcome back, my tenderfoot hackers! Web apps are often the best vector to an organization's server/database, an entry point to their entire internal network. By definition, the web app is designed to take an input from the user and send that input back to the server or database. In this way, the attacker can send their malicious input back to the servers and network if the web app is not properly secured.

Waking up can be a real struggle for some people. Alarms help, but most of them are so easy to turn off that you can shut them off while you're still half asleep and go back to bed, only to wake up in a panic as your realize you've severely overslept. Microsoft Garage wants to make you at least work for your lethargy with its new Mimicker Alarm.

In this article I will show you how to obtain victim's credentials without cracking any hashes. There are a couple of ways to perform this task (for example dumping the SAM file and cracking the NTLM hashes), but here I will explain how to do it using PowerShell and a bit of social engineering. We are going to create a fake login popup.

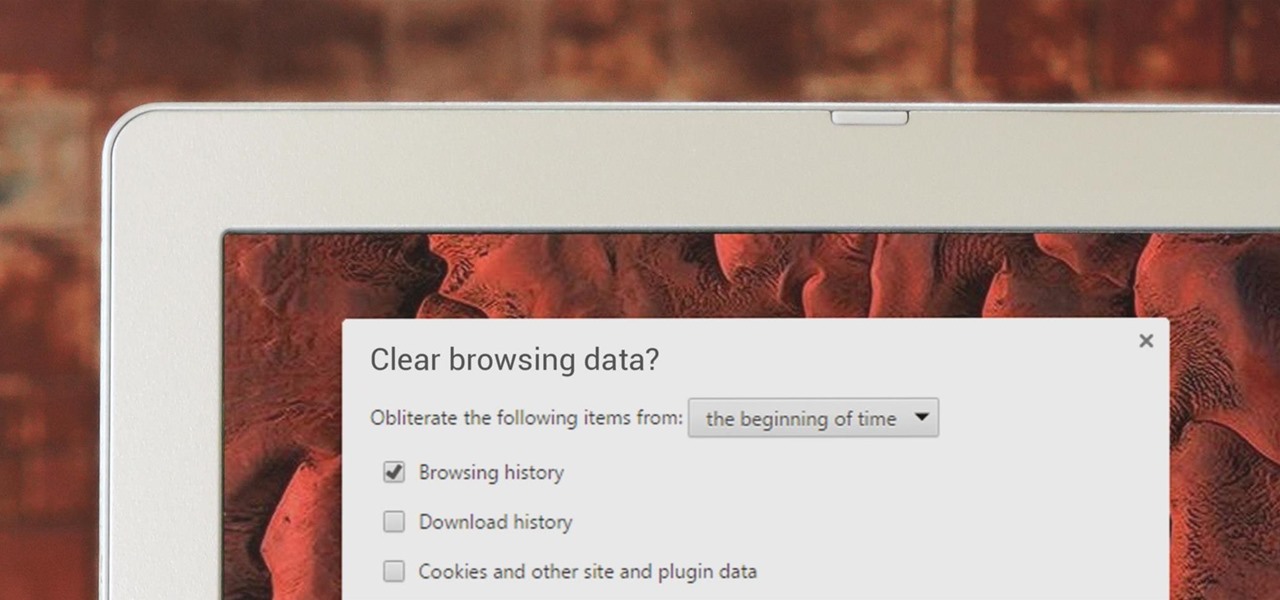
If you've been visiting websites of ill repute, or if you've been Christmas shopping and don't want to spoil the surprise, it would be a disastrous situation if anyone were to come across your browsing history. Visited sites, cookies, and cache can paint a very clear picture of your recent internet activity, and depending on the situation, you may only have a few seconds to delete your history before someone else barges in.

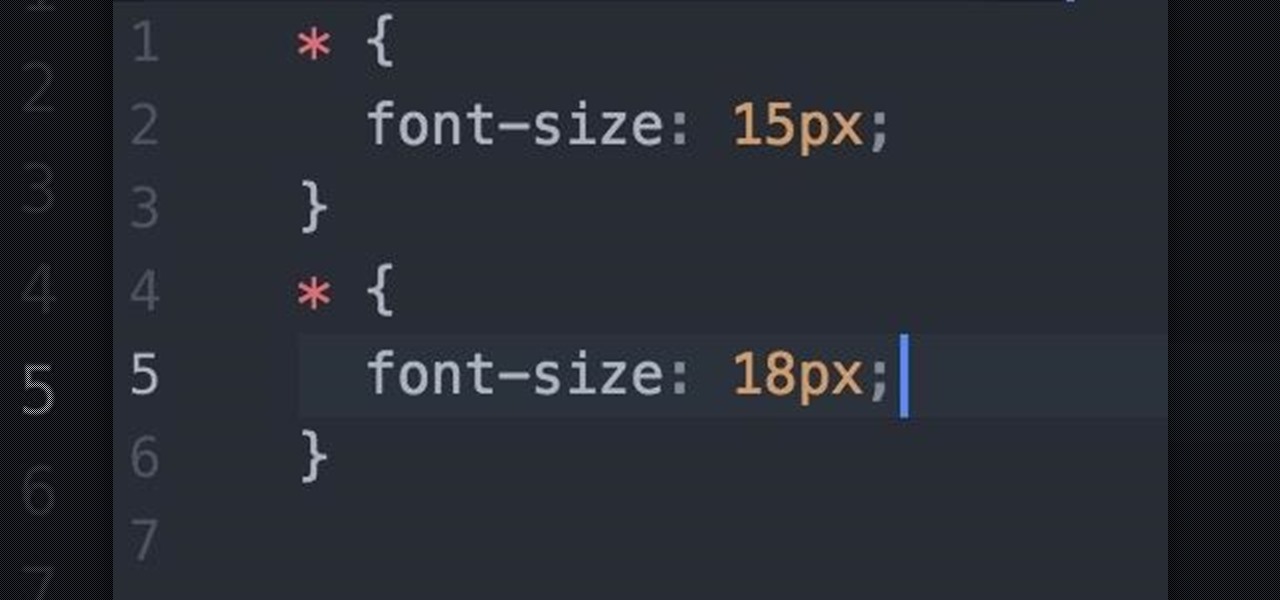
Welcome fellow Null-Byters! I would suggest you watch reading my last tutorial before we begin. In our last adventure, we began making a simple, ugly website. If we want it to make it look good, we should add some styling. But first, we need to understand the basics.

Hello, my fellow hackers. My name is cl0ck. I am a senior majoring in Computer Engineering with an emphasis is Security. I have been lurking the site for a while now reading and learning from the great minds that reside here. I, too, have some knowledge that I would like to share with all of you. This post actually comes from a personal problem I faced and had to find a solution for. Without further ado, here it is:

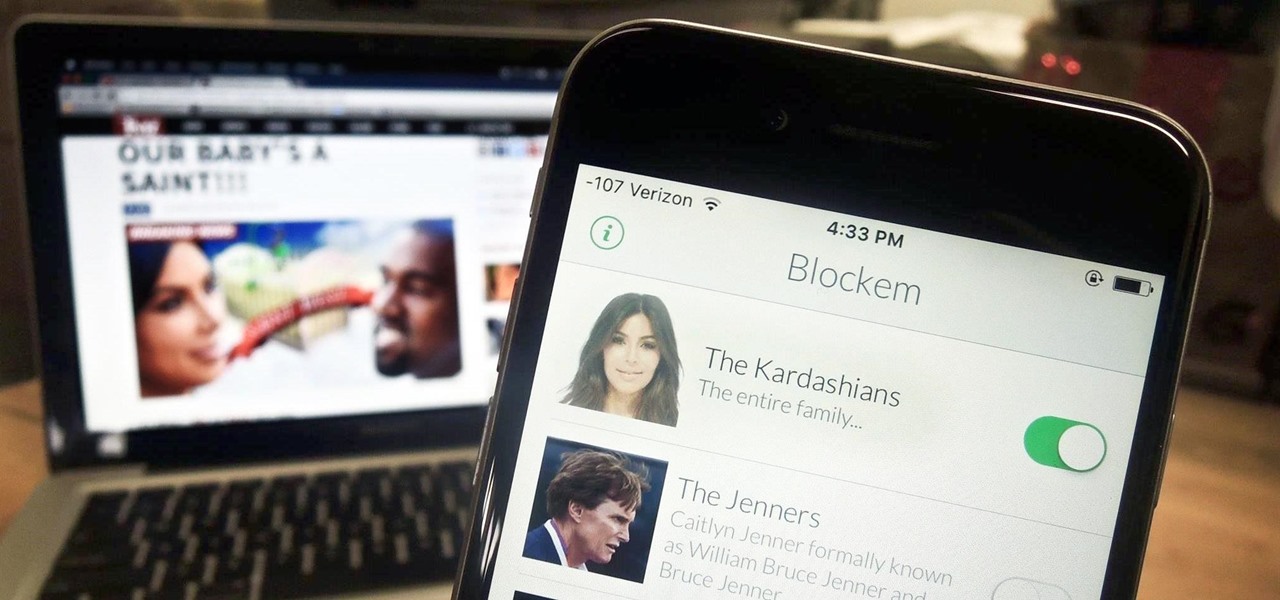
Kim Kardashian and Kanye West have fittingly named their second child "Saint," but I'm sure you don't care about that—and neither do I. Unfortunately, regardless of our pop culture interests, we're forced to know these types of stupid facts because the internet is so densely populated with Kardashian-related content that it's impossible to avoid. It's enough to make you puke.

If you're a U.S. expat living, traveling, or studying abroad, or just someone who typically uses virtual private networks (VPNs) in order to access the North American video libraries of services like Hulu or Netflix, you were probably surprised to see that these video streaming services don't work on your Chromecast or Chromecast 2.

A growing trend for many artists (most recently Kanye West) is to offer exclusive or experimental tracks on music streaming sites like SoundCloud or YouTube before releasing them anywhere else. On rare occasions, some of these great songs never make their way onto an official album, which can be disappointing for die-hard fans who need to download every song available from their favorite artist or band.

Hello, my web huggers! In today's tutorial we will learn how to use the Google Hacking Database (GHDB) developed by Exploit Database, to find vulnerable web servers and "juicy" information.

Hello My Fellow Hackerzz.. This is my first How-to and i'll be updating the “Hacking Android Using Kali” to msfvenom and some FAQ about known problems from comments. So Here we GO!!
Welcome back Hackers\Newbies!

This is second post in my series of posts for finding hacked accounts online. Please do read the part 1 of the post at http://null-byte.wonderhowto.com/how-to/find-hacked-accounts-online-part-1-0164611/

Accidentally deleting important files can happen as easily as swiping left on something and watching it disappear into the ether. Of course, Apple allows automatic backups through iCloud, which ensures that your data is always stored safely in the cloud in case of emergency.

A no-carb, gluten-free substitute for breadcrumbs. Sounds and probably tastes like cardboard, right? Unless you're talking about Pork Dust. Yes, you read that right. Pork. DUST.

This tutorial is for people who want to try different types of hacks in an environment that is the same for everyone so it will help people to ask questions and learn. This series assumes you know how to run a VM and network them together. This series also assumes that the services running on the Metasploitable machine are needed to be running.

Well, this is my first article so if it sucks tell me...lol!! Story Time

When it comes to antivirus software, you don't want some fly-by-night developer having access to the sensitive data that these apps can scan. Luckily, most of the longest-tenured antivirus companies from the realm of desktop computers offer complete security suites for Android these days.

Hi guys. I'm here to go for level 7 now lets get it start but i apologize u all that i posted this very late but now lets rock:

While the app switcher in iOS makes it easy to go from one open app to another fairly quickly, it's still not a great option if all you want to do is return to the previous app you were in.