If you are stuck using a computer in a place with safety filters, you can use this tutorial to bypass those controls and get to your YouTube account. So, whether you are in a school, library or your parents have parental controls activated, just follow along and you will be able to get past them every time. There are two methods described in this tutorial, one is easy for beginners and the other more advanced. They both work like a charm, however, and you will be watching your favorite videos...

Ramses and Tara from Skills of the Game explain why creating an attention-getting headline is important in online dating, especially on dating sites that emphasize a headline rather than a thumbnail picture. They explain how and why a poor headline can diminish a person’s standing. They give examples of bad headlines, and suggest writing headlines that are either lighthearted or call the reader to action. After giving a few examples of good profile headlines, Tara explains why the most import...
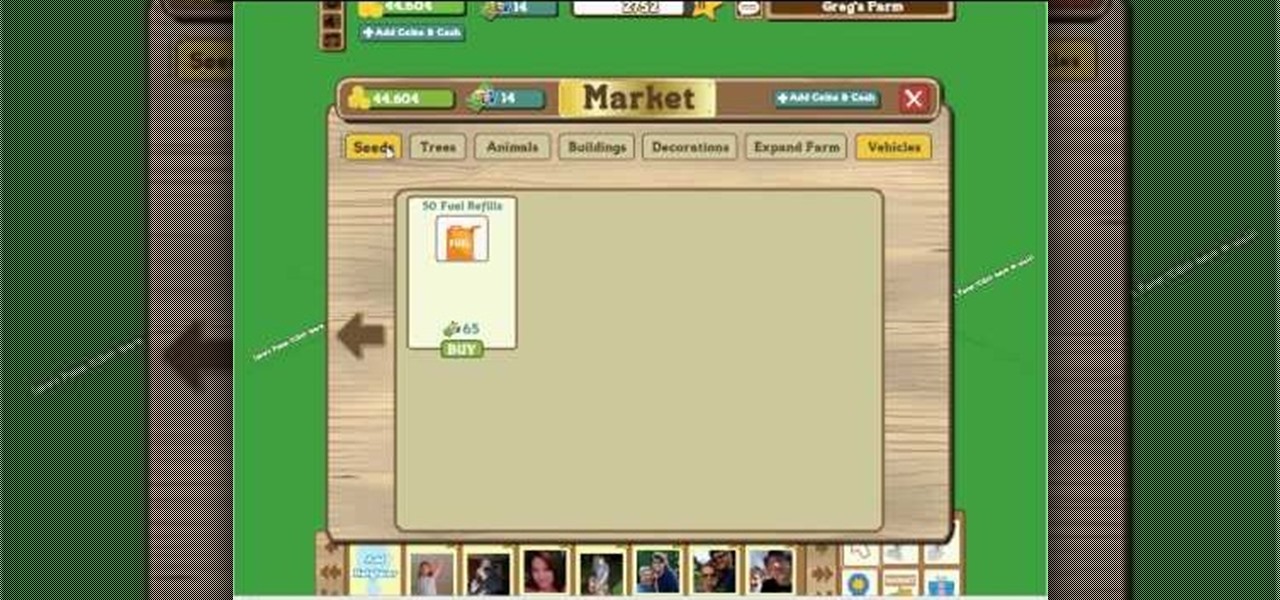
Facebook is the number one Social Networking site that hosts the number way farming game, FarmVille! This video will give you a few basics to bring you back to your farming roots! Your game screen will show your plot of land surrounded by some neighbor's farms. Using your click took, plow tool or shovel tool you can plant, delete, move and plow your plots of land. The market shows you the crops that are available to buy as well as buildings, animals and decorations too! Watch the rest of the ...
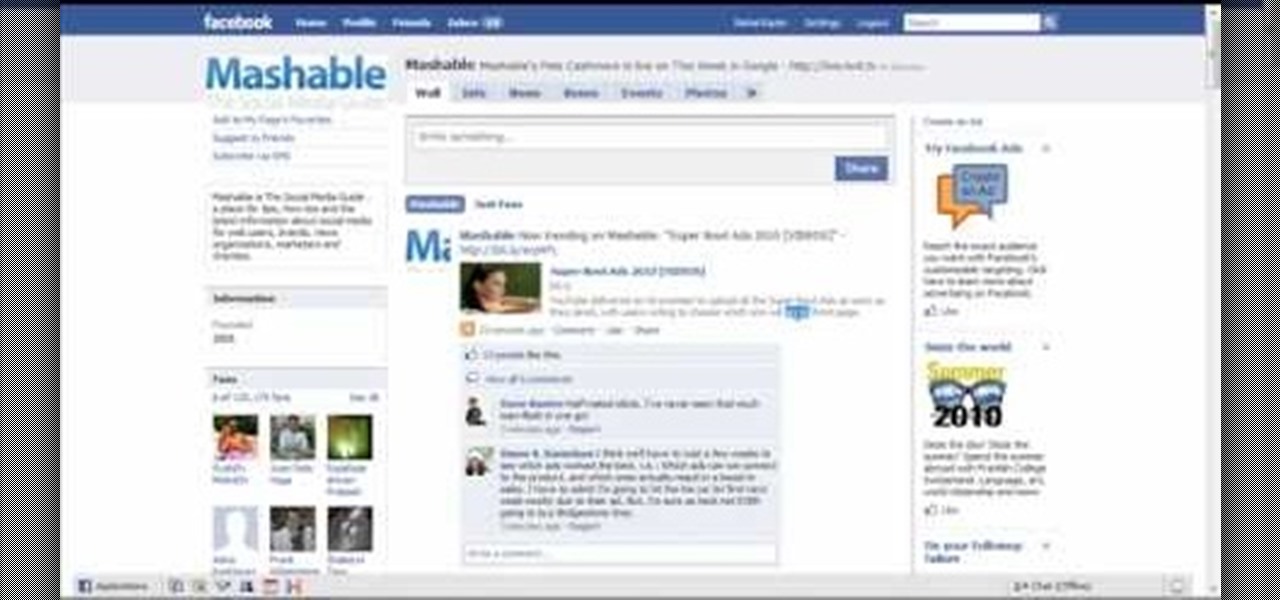
This instructional video Nehal Kazim from Site shows you how to make a complete Facebook fan page. Before creating a fan page evaluate the reasons of making a fan page. A fan page lets you connect with your future clients and fans and keeps them updated and gives them a platform to talk about your organization. To create a fan page go to the bottom of any page and click 'Advertising', select pages and click create a page. Select a suitable category and a suitable name make sure to select it c...
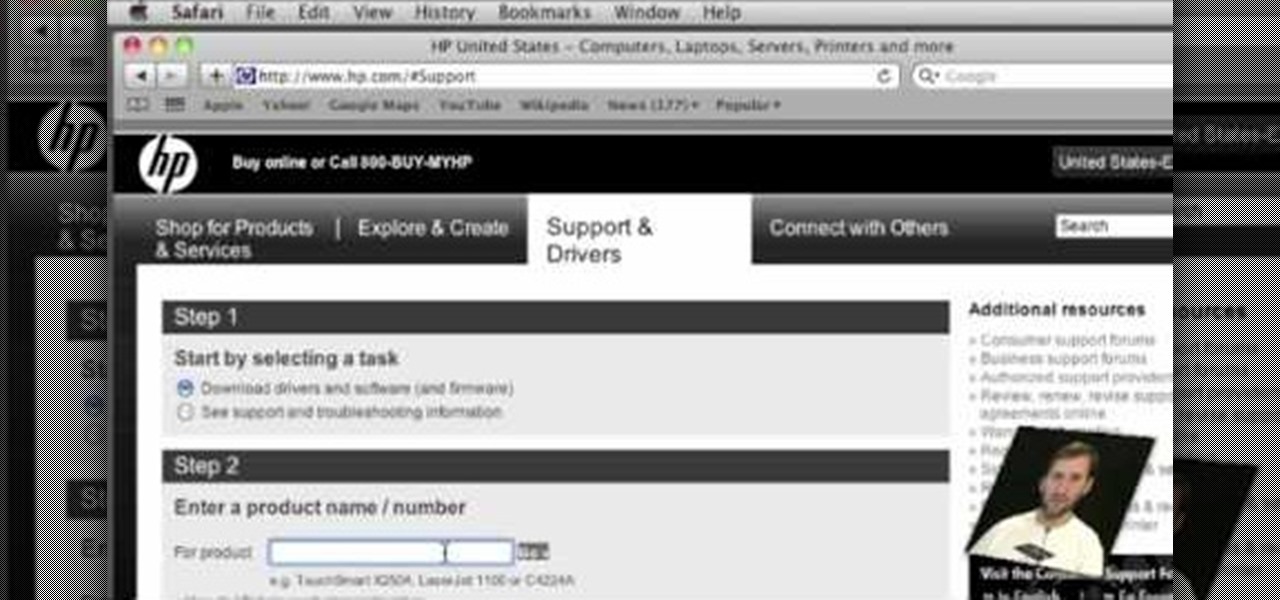
In this video, Gary from MacMost gives some tips on how to set up a new printer with your Mac. Some printers don't work for Macs, so make sure it's compatible before purchasing it, by checking the internet. Check if a USB cable comes with a cable and buy one if necessary. Ignore the CD that comes with the printer, because it probably doesn't have the correct Mac drivers. Leopard or Snow Leopard systems will find the correct drivers for you automatically most of the time. You might need to dow...

If you're wondering what FoWsc stands for in Guild Wars and what it's all about, here's your lesson. Dooom Box teaches us everything we need to know when it comes to Fissure of Wo Speed Clear: The basics, the parts, the teams, and more.

Wondering how you can finally use that Paragon? Dooom Box shows how to finally start using the Paragon using the Imbagon build in Guild Wars in what he calls the "Imbaguide".

In this video, Dooom Box shows us how to farm raptors quickly an easily using a warrior necro. Clear the raptor cave in under a minute in hard mode using a WARRIOR! Farm.

Curious about the Norn Fighting Tournament? In this video, Dooom Box gives some great tips on the Norn Fighting Tournament in Guild Wars, and some great insight on how to beat Magni The Bison.

Adobe Bridge -- why should you use it? That is one of the most frequent questions for Adobe Design users. Most don't even know what it is. This entire video explains some of the great reasons why you should actually use the Bridge. By the end of the video, you should be a die-hard Bridge user. Don't use the plain old regular file browser!

Check out these tips on the Adobe Bridge Center. Not only does the Bridge have excellent features for file browsing and file organization, but it also has the central area, consider it the hub, where you will find features that will further streamline your workflow. In this video tutorial, learn how to use the Adobe Bridge Center, which is a default favorite in the Favorites pane.

Here, see some tips on the collections and smart collections in the Adobe Bridge. Bridge has a lot to offer and is a great organization tool. Collections and smart collections are great workflow features available to you. In this video tutorial, learn about organizing your files without messing up your folder structure and automatically bringing files in that you want based on your settings you assign to that collection. Check them out and learn a great new feature of Adobe Bridge CS4.

Using GoLive CS2, you'll learn how to create some CSS-based rollovers. This is really an easy way to create some rollovers, using CSS, which is an incredibly useful and powerful way to style and design your website pages. In this GoLive video tutorial, learn how to style not only your links, visited links, and active links using CSS, but you will also see how to give your links a rollover or hover style as well. You will quickly see how much more you can achieve by styling your links using CSS.

Hak5 is at it again, with a plethora of somewhat accessible solutions to your technological problems. If you've ever needed to get through your school's firewall, or secure traffic tunneling, or try out applications in a fast, efficient manner? This video has it all and more.

Watch this video fashion design lesson to see who took second place in the Generation-t tee recon contest with how-to make a wrap shirt. All you need is two t-shirts and the steps, so follow along and get sewing.

Watch this fashion design lesson to see who took third place in the Generation-t tee recon contest with a how-to for making a no-sew fringe halter top!

This week Meg takes us back in time and shows us how to make an amazing Starburst mirror. Follow along with the home interior how-to video, and learn how to add a little vintage flair to your own home decor.

Grand Illusions is a site for the enquiring mind. This how to video demonstrates how to make Japanese origami tumblers. Your wonderful & charming host represents Grand Illusions, an amazing toy, magic & illusion web shop and gallery.

Tim and Kevin meet up/hang out & talk their talk. They discuss buying domain names, choosing business names, starting companies, and selling books by their color. These two entrepreneurs have lots to teach us about selling ideas and making profitable businesses.

This video explains how to fold the Spiral by Tomoko Fuse. You need 4 sheets of paper of different colors of any combination of your choice. 2 sheets of 2 colors each would give you a dual colored spiral.

This video will show you how to fake a RAM, Flash, or entire memory clear. Lots of teachers and test administrators go around and clear your calculator so students don't cheat. This is any easy way to subvert the teacher's security measure. This is a good thing to know if you want to cheat on your GED, SAT or ACT test / exam.

This homemade cake mix can turn your least kitchen-savvy friend into a star baker. And you’ve done 90 percent of the work, which is the greatest gift of all.

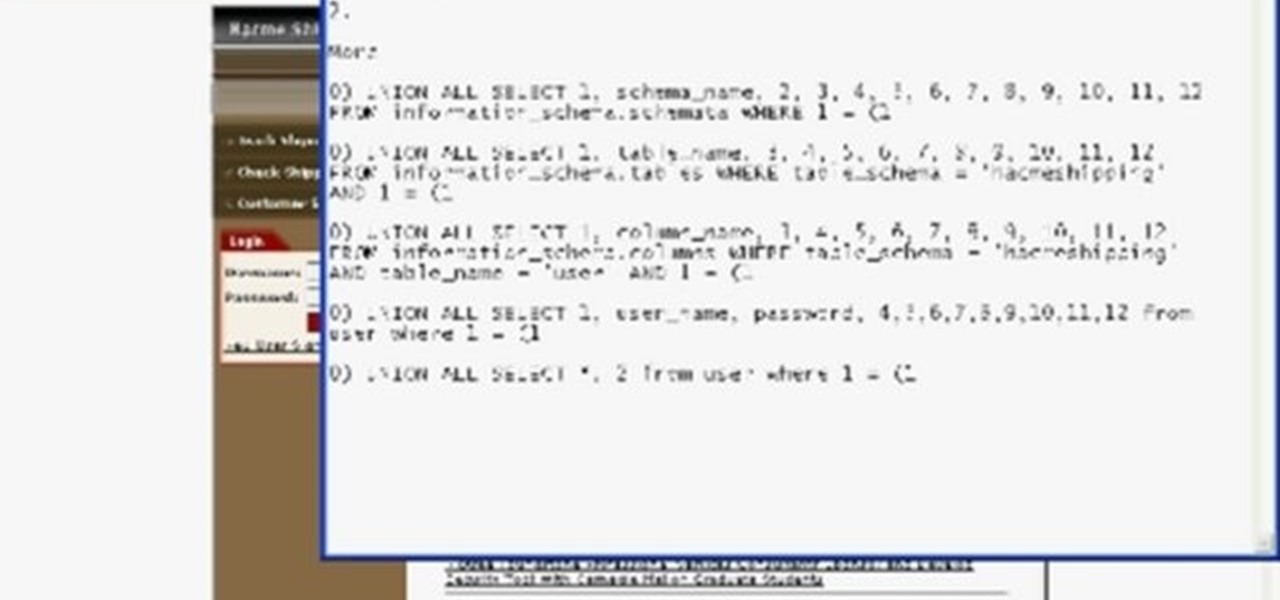
Foundstone Hacme Shipping is a web-based shipping application developed by Foundstone to demonstrate common web application hacking techniques such as SQL Injection, Cross Site Scripting and Escalation of Privileges as well as Authentication and Authorization flaws and how they are manifested in the code. Written in ColdFusion MX 7 using the Model-Glue framework and a MySQL database, the application emulates the on-line services provided by major shipping companies. This video will get you st...

How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.

How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.

Watch this video tutorial on how to perform a bone marrow aspiration biopsy on an animal, specifically a dog or cat.

In this video tutorial, Chris Pels shows how to create a custom profile provider to store and retrieve data associated with a user profile in SQL Server tables separate from the standard ASP.NET membership provider’s aspnet_Profile table. The principles covered in this video will apply to creating profile providers for other databases like Access and Oracle. After learning how to create the custom profile provider we learn how to install the provider in a web site and see a demonstration of l...

In this video tutorial, Chris Pels will show several aspects of defining and using master pages in an ASP.NET web site. First, see how to create master pages declaratively using the ASP.NET master page model and learn what information is best suited to a master page compared to an individual content page. Next, see how to programmatically assign master pages on-the-fly in an individual content page. Also learn how to create a base page class which assigns a master page programmatically for al...

It's pretty much a given at this point that Facebook has a lot of data on us. While you might be conscious of the data you share with Facebook when you post, upload photos, or chat with friends on Messenger, you might not be thinking about all the data it receives from websites and apps you use outside the social media giant. Now, you can actually do something about it.

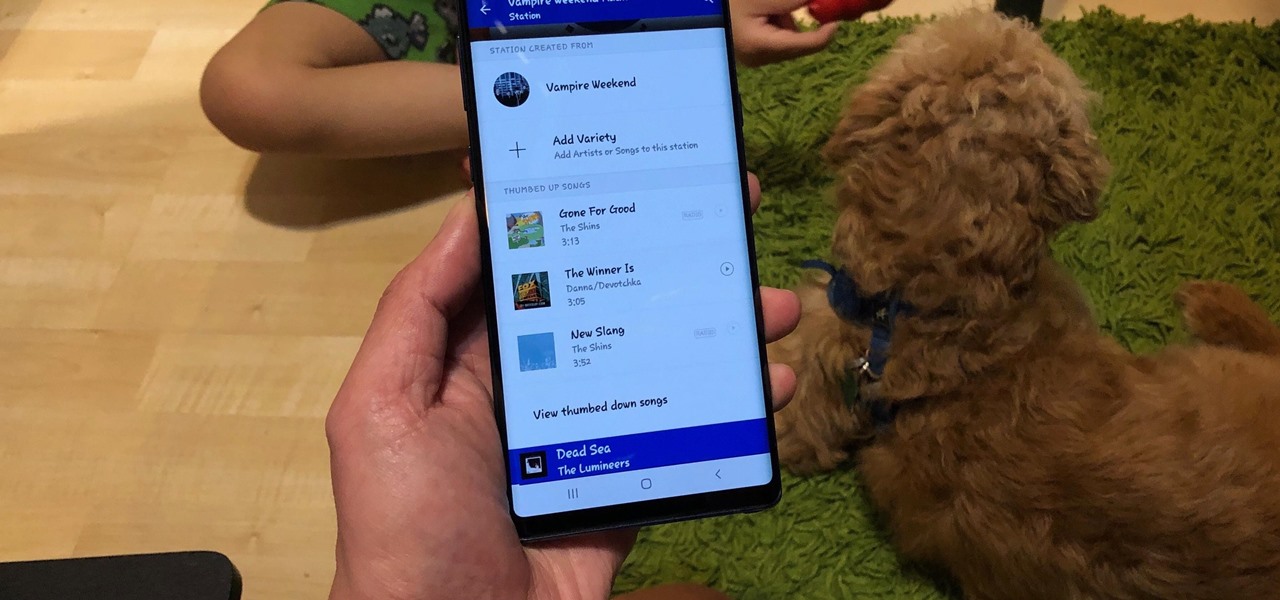
Pandora has a simple rating system that works by hitting either the thumbs-up or thumbs-down icon on a track that's playing on your station. If you choose the former, the song you like along with others similar to it will play with more frequency, while selecting the latter will prevent that song and others like it from playing in your station moving forward.

When it comes to digital security, one of the best ways to protect yourself is to use two-factor authentication. Most apps these days support it, including Facebook, a site where the more privacy you can muster, the better. However, of the two 2FA options available for Facebook, only one should be used as the other will share your phone number with the world, a huge privacy concern.

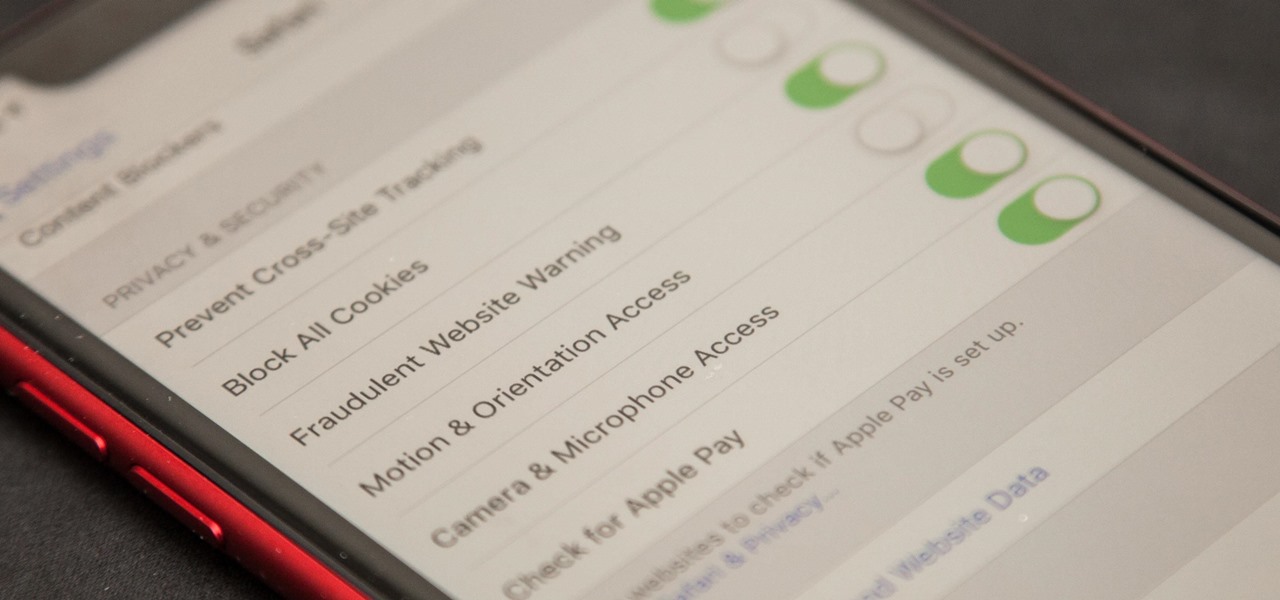
Apple first added the "Do Not Track" option to Safari in iOS 7, which sent a request to site owners and advertisers to not track your browsing activity. By tracking your activity, those third-parties could tailor content to you that you're more likely to interact with. While the feature was always opt-in, it's no longer a feature at all in iOS 12.2 on your iPhone.

Every photo you take is brimming with metadata such as iPhone model, date and time, shooting modes, focal length, shutter speed, flash use, and geolocation information. Share these pictures with friends, family, or acquaintances via texts, emails, or another direct share method, and you unwittingly share your location data. Even sharing via apps and social media sites can compromise your privacy.

Cross-site scripting can be one of the easiest vulnerabilities to discover, but to be successful with this type of attack, it is essential to learn how to get past filters. In the previous guide, we explored some ways to do this, such as abusing attributes and event handlers and tricking the application into accepting unusual characters. Now, let's take a look at more techniques used to defeat filters.

Amid the opulent and historic confines of Paris, Microsoft is now hosting an exhibit at a local museum that brings a historic map of a Normandy tourist destination to life in augmented reality.

Database technology has vastly improved the way we handle vast amounts of data, and almost every modern application utilizes it in one way or another. But the widespread use of databases naturally invites a slew of vulnerabilities and attacks to occur. SQL injection has been around for awhile, and as such, there are many defense methods in place to safeguard against these types of attacks.

Two-factor authentication (2FA) is a great way to add another layer of security to sensitive third-party apps and websites like Venmo. However, before iOS 12, to log into a particular 2FA-secured app or site on your iPhone, you'd have to memorize or copy the SMS code from Messages, then jump back in a timely manner to log in. Apple's latest iOS version streamlines this process.

When you visit a website in Safari, it's most likely keeping tabs on your browsing activity. It could be keeping track directly, or its third-party content providers and advertisers can be spying on you. All three could happen simultaneously. This enables them to serve you content that's tailor-made for you, but it can also feel like an invasion of privacy.

When it comes to your security, you want the best of the best. Why settle for mediocre service with something as valuable as your protection? Malware continues to make its way onto the Play Store, leaving millions of devices vulnerable. You need an app that will shield your devices from both the latest malware threats and threats nearby. And when it comes to antivirus apps, there is only one choice.

Augmented reality was recently named the "Mobile Disruptor of the Year" for 2017 by Mobile Marketer, but the technology is showing no signs of slowing down as we head into 2018. In fact, the technology appears to be gaining momentum.