Take a lesson in architecture from renowned architect Doug Patt by watching this video tutorial. If you want to learn about drawing and designing, without going to school, Doug's just the teacher. Watch to see how to design and draw an architectural water tower house.

Want a cartoon avatar of yourself to load onto all of those websites you belong to? Well, in this video, see how to obtain a cartoon avatar of yourself to display on Twitter, FriendFeed, your blog, and your corporate logo (if you want to go that far). The process is fairly simple. The first step is to take a good picture of yourself with decent lighting (try to do this alone as it will help). The next step is to visit cartoonme.com and submit the photo to the site. Pay them via PayPal (3.50 E...

Check out this video tutorial to see how to collect blood with the BD Vacutainer Safety-Lok Blood Collection Set.
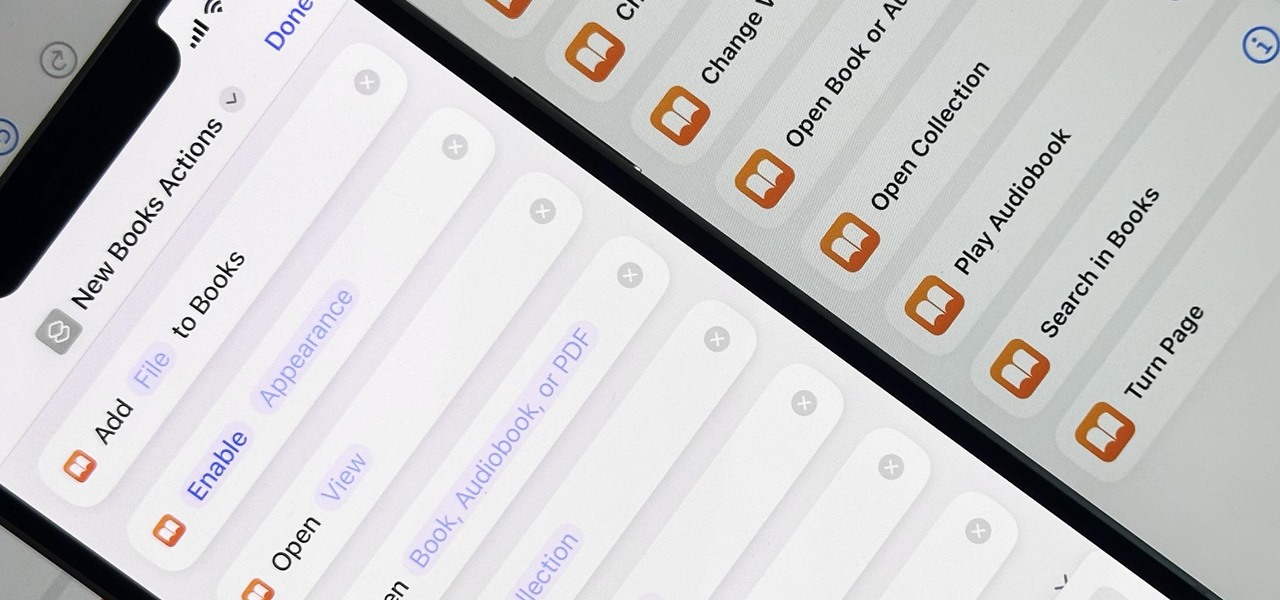
When iOS 16.0 was still in early beta testing, Apple teased us with a slew of new Books actions in the Shortcuts app, but none of them materialized in iOS 16.0 or 16.1. That changes with Apple's latest software update for iPhone.

When you first open Safari after updating your iPhone to iOS 15, you might be a bit surprised by the design change. Apple attempted to make browsing the web on its smartphones more natural and cohesive, but it may leave you wondering just how to actually navigate your tabs.
It should be simple to select and copy all text on a webpage in Safari, but it won't work as it does in other apps. Usually, you can press-and-hold down anywhere on a page and choose "Select All" from the edit menu, but that functionality is disabled in Safari and WebKit-based browsers by default — including in the latest iOS 14 version. Luckily, there is a workaround to getting a "Select All" button back.

Android 11 is available as a simple beta install for Pixel devices right now. Just visit Google's beta signup page, make sure you're signed in with the same account used on your Pixel, then opt into the program. You'll get an OTA update that will put you on Android 11 in no time. But is it ready to be a daily driver?

For the average consumer, augmented reality is a fun way of dressing up photos and videos for social media. However, AR is also gaining momentum as a medium for storytelling, particularly in sharing powerful messages.

Apple released the first public beta for iOS 13.5.5 on Monday, June 1. The update comes just hours after Apple seeded developers their first 13.5.5 beta, as well as the public release of iOS 13.5.1, which introduced a patch for the Unc0ver jailbreak exploit. It was a big day for iOS software.

If you were upset about "Friends" leaving Netflix, fret no more. The entire series, all eight Harry Potter movies, as well as HBO's massive catalog, are now available as part of HBO Max. If you're already an HBO Now subscriber, however, it can be a bit confusing to know how to switch over to this brand new service. Here's how.

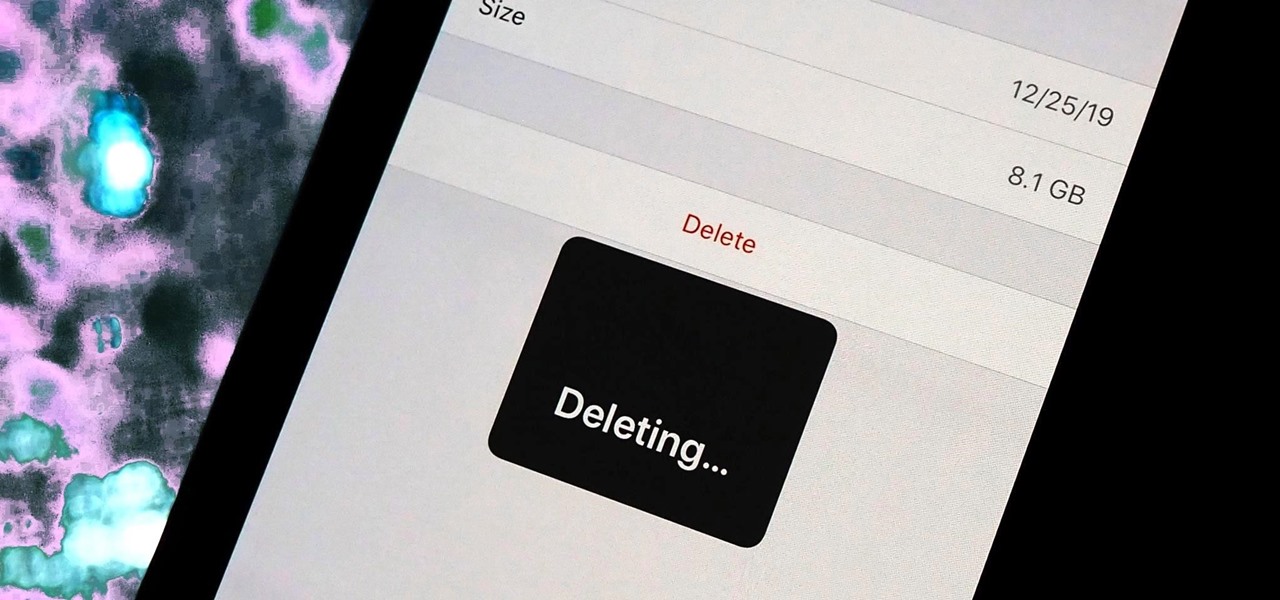
If you use iCloud, you may have experienced alerts such as "Not Enough Storage" and "iCloud Storage Full," especially if you're on the free 5 GB plan. To clear up space on your iCloud account fast, you can delete large files here and there, but trashing one thing, in particular, can clear up gigabytes worth of space instantly.

We know our Null Byte readers would like to see some iPhone-hacking scenarios on the site soon, but until we get some of those up, we understand that some of you actually use an iPhone as your primary phone. If that's you, and you would like an easier way to get information from point A (your iPhone) to point B (your computer) and vice versa, there's an all-in-one tool that can help.

Whether you're coding a simple app, trying to learn a new programming language, or building an entirely new operating system from scratch, being able to quickly and clearly organize your thoughts is absolutely paramount — even as an ethical hacker or penetration tester.

If you're one of the many professionals transitioning to working from home amidst the current pandemic, there's a good chance you're now realizing how far behind your at-home setup is compared to what you had at the office.

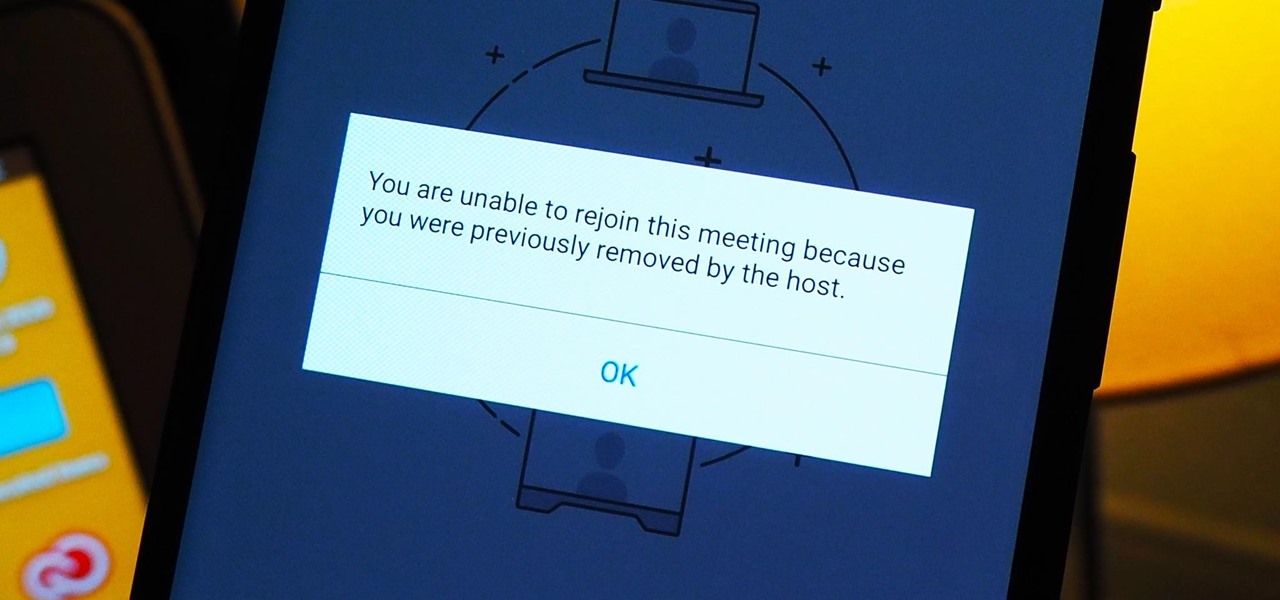
As more and more people use the video conferencing service Zoom, the chances of trolling behavior and attacks only increase. But it's not just "Zoombombers" you need to worry about. A heated discussion between family, friends, or colleagues could turn sideways real quick, and sometimes the best course of action is to remove the participant from the group video meeting altogether.

Apple just released the first developer beta for iOS 13.4.5 on Tuesday, March 31. The update follows the previous week's stable release of iOS 13.4.

The worldwide health crisis around the coronavirus has gripped the live events industry, particularly in the tech sector, with the cancellations of Mobile World Congress, the Game Developers Conference, Facebook's F8, Google I/O and now South by Southwest.

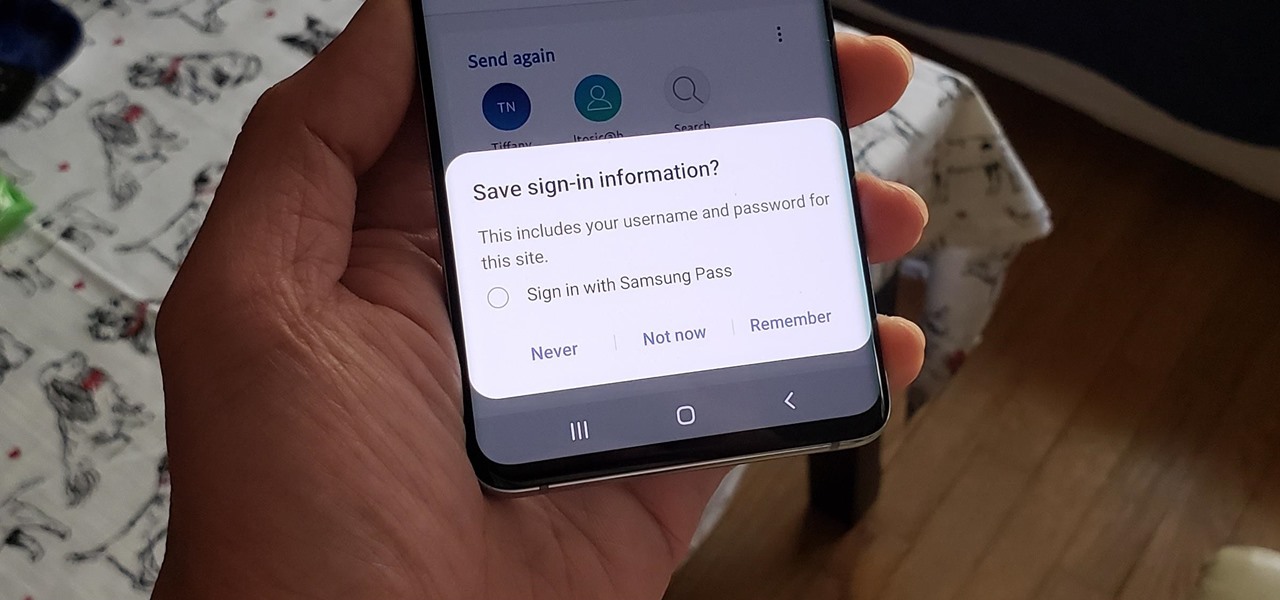
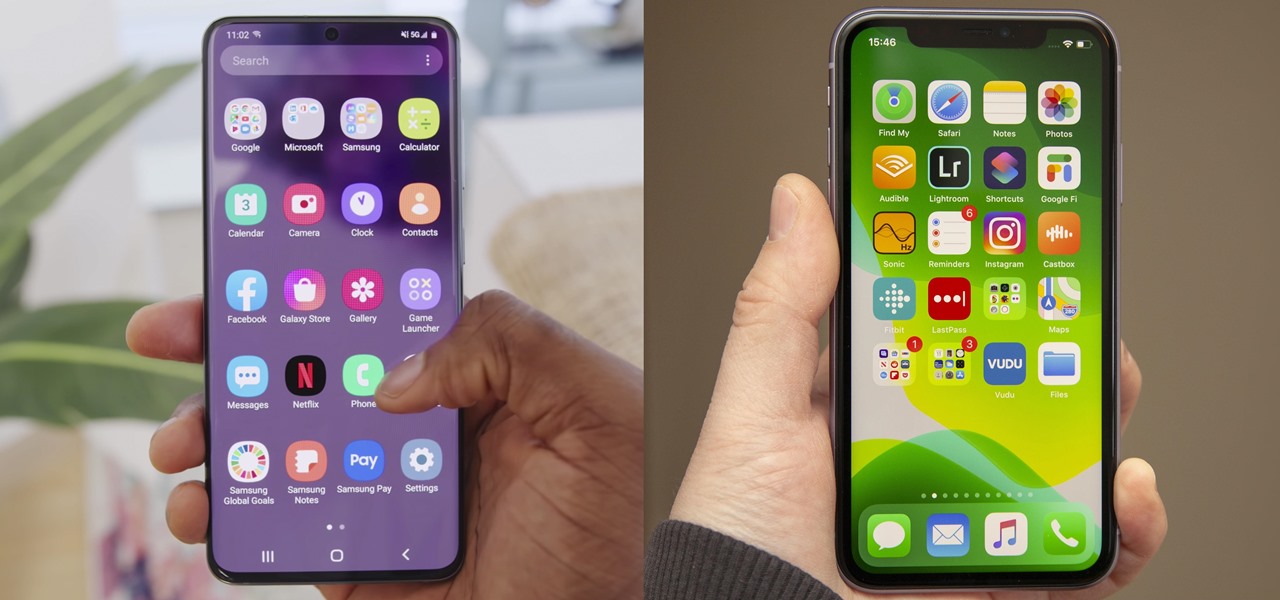
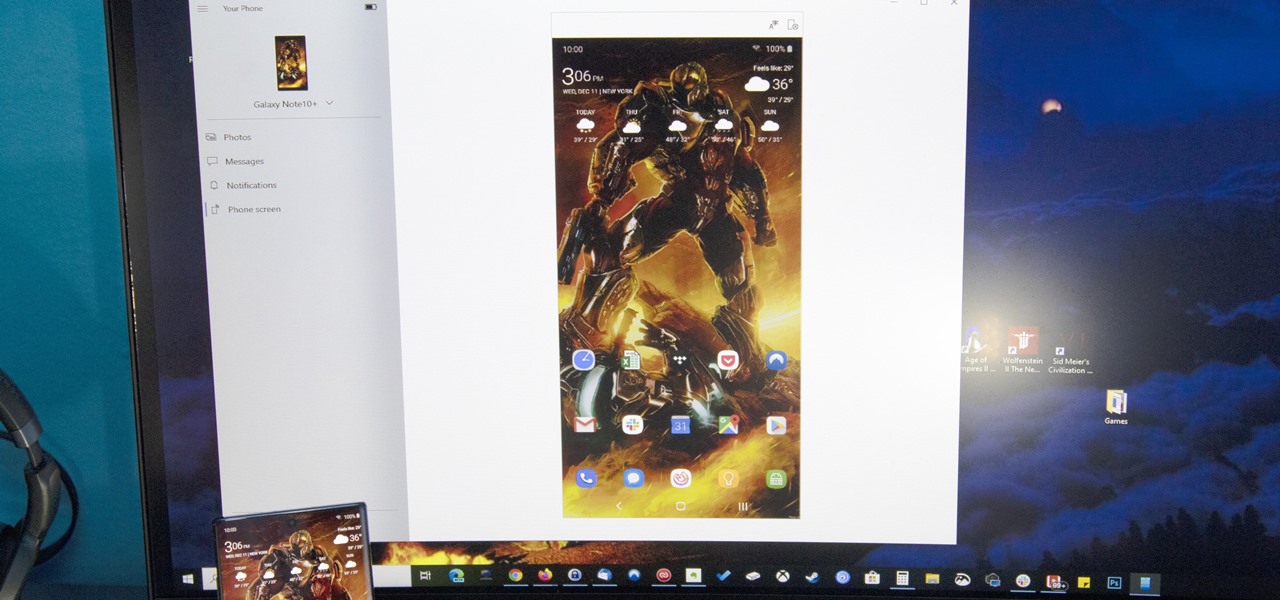
If you use Google Chrome on your computer, you've undoubtedly saved a ton of passwords since the browser always prompts you to. But Samsung uses their own password service on their phones by default, so you'll have to change a setting if you want to use your Chrome passwords to log into apps and sites on your Galaxy.

The still-unfolding story of China's Nreal augmented reality startup continues to develop, with each turn uncovering another unexpected wrinkle.

Alongside Sesame Street, the Dr. Seuss universe has been a constant presence in the formative years of several generations of children in the US.

While holographic Whitney Houston is hitting the road, a new mobile app is bringing volumetric captures of up and coming performers directly to the iPhones and iPads of fans.

If you thought the news coming from China about the coronavirus might not affect your daily life in Europe and in the Americas, think again.

Apple has their regular iPhone 11, then two higher-end "Pro" models. Samsung went the other way — they have the Galaxy S20 and S20+, then there's the S20 Ultra. But one thing these smartphone lines do have in common is the base model flagship. How do they compare?

The Oscars are just a couple of days away when Hollywood will celebrate the best crop of films from 2019 in the US and internationally.

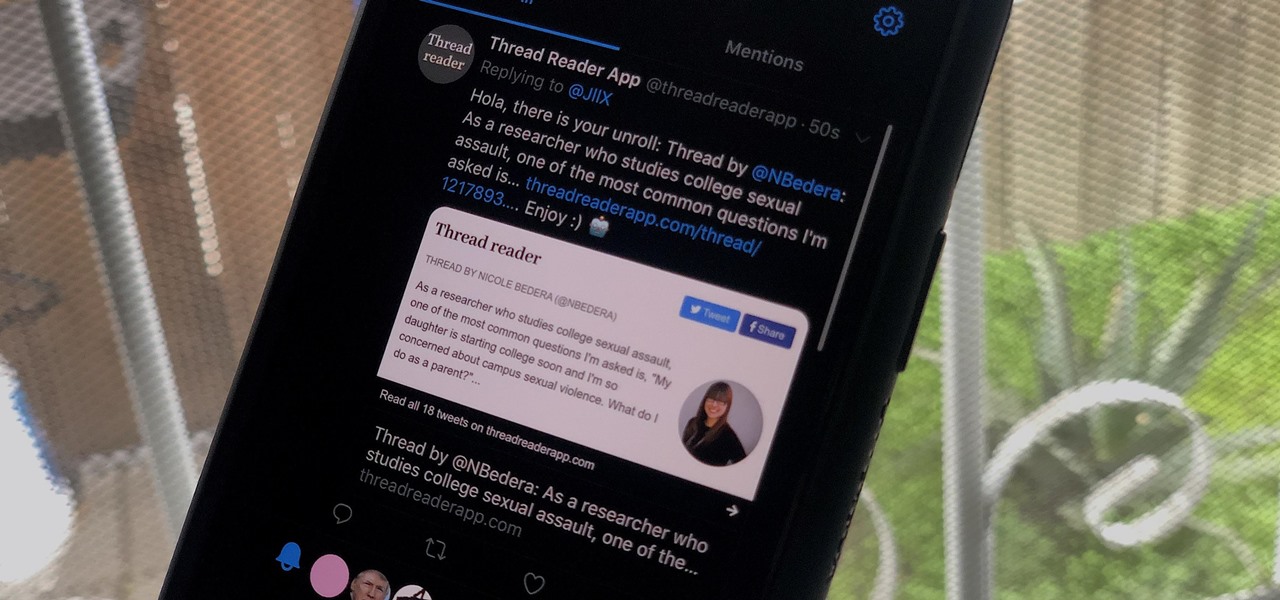
While tweetstorms were a part of Twitter since the beginning, threads, which makes tweetstorms more viable, didn't show up until late-2017. Still, threading multiple tweets at once to create long-form stories, opinions, tirades, and other lengthy Twitter posts, can be hard to digest. However, you can make reading them easier with just a single message.

Some of the leading big tech companies are still working in the lab on actual products, but at least some of their leadership did have some thoughts to share on the future direction of the technology this week.

It's been said time and time again: reconnaissance is perhaps the most critical phase of an attack. It's especially important when preparing an attack against a database since one wrong move can destroy every last bit of data, which usually isn't the desired outcome. Metasploit contains a variety of modules that can be used to enumerate MySQL databases, making it easy to gather valuable information.

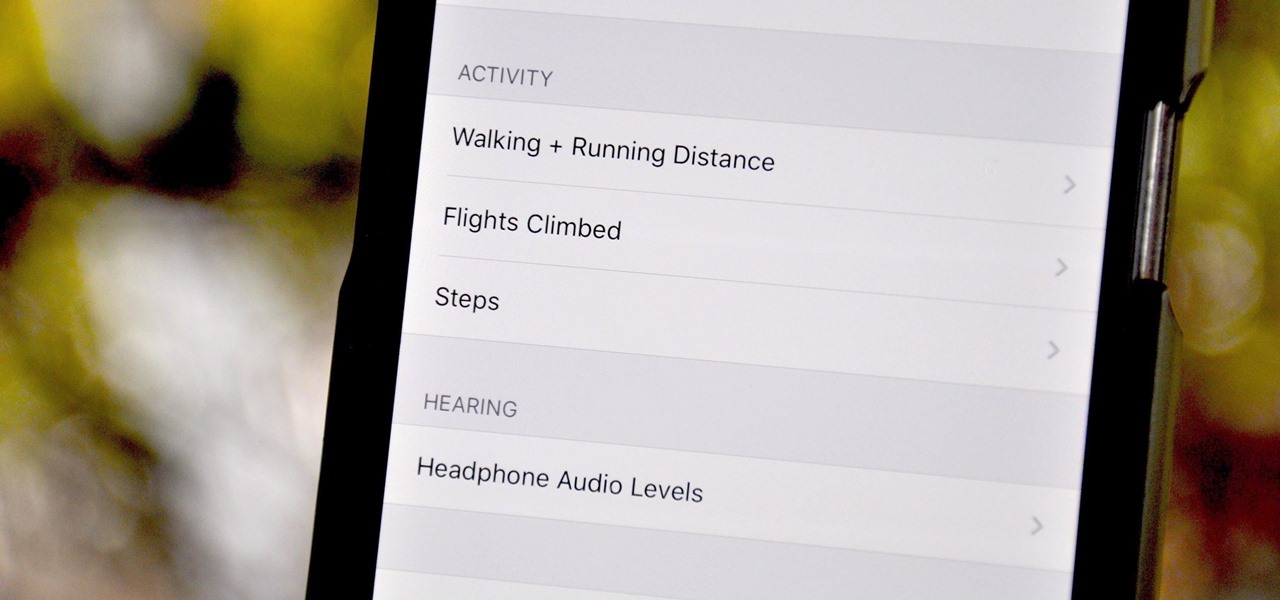
Although the Health app mostly focuses on fitness, Apple has slowly added features to help with other aspects of well-being, including hearing. In iOS 13, there's now a headphones volume tracker in Health that monitors audio levels and lets you know when your music, podcast, movie, or whatever else is too loud.

In his famous 1996 "Content is King" essay, Bill Gates predicted that content is where tech companies will make money on the Internet. The adage clearly holds true in the current phase of augmented reality experience.

Your iPhone tracks how many steps you take, how far you walk, and how many stairs you climb each day. That may seem a bit frightening, but it's all for a good reason: the Health app stores this data so you can view your progress in one place. But interestingly, opening the Health app isn't the easiest way to view this info.

A lot of time can be wasted performing trivial tasks over and over again, and it's especially true when it comes to hacking and penetration testing. Trying different shells to own a target, and testing out privilege escalation commands afterward, can eat up a lot of time. Fortunately, there is a tool called One-Lin3r that can quickly generate shells, privesc commands, and more.

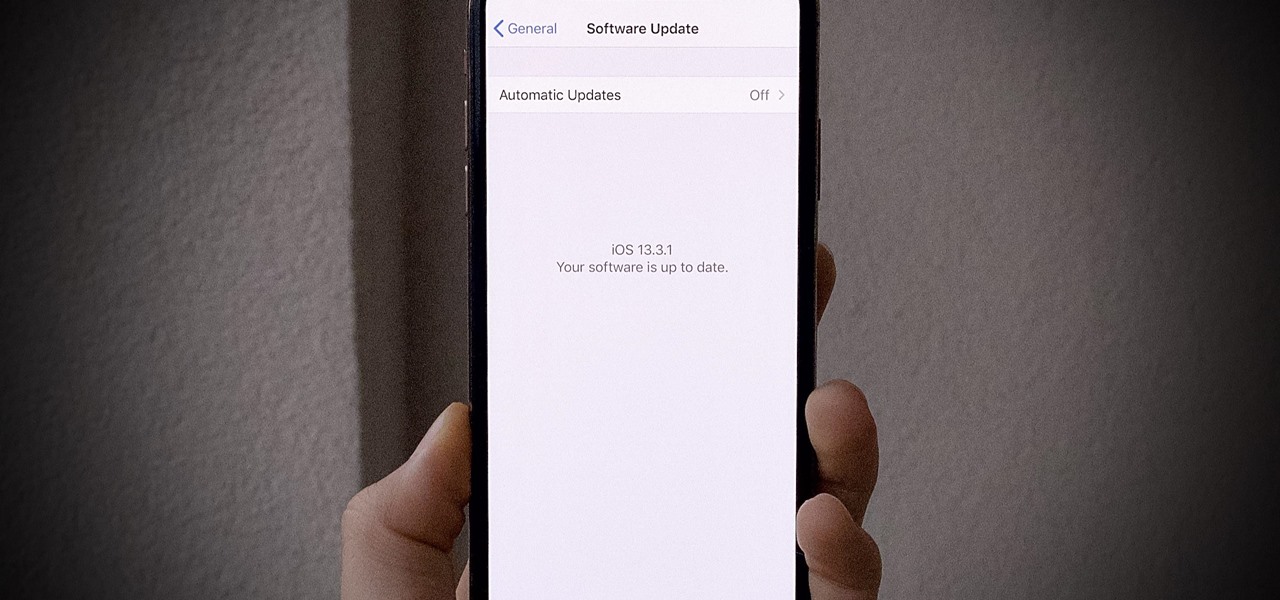
Yesterday, Dec. 17, Apple released the first developer beta for iOS 13.3.1. The update marked the first new beta in almost a month since iOS 13.3's fourth beta dropped on Nov. 20. Now, one day later, Apple has pushed out iOS 13.3.1 public beta 1 to everyone who wants to try out new features first.

After exiting the mobile market, Microsoft has redirected its efforts to better integrating their services with Android. Thanks to a partnership with Samsung, that Windows integration is even better if you have a Galaxy phone.

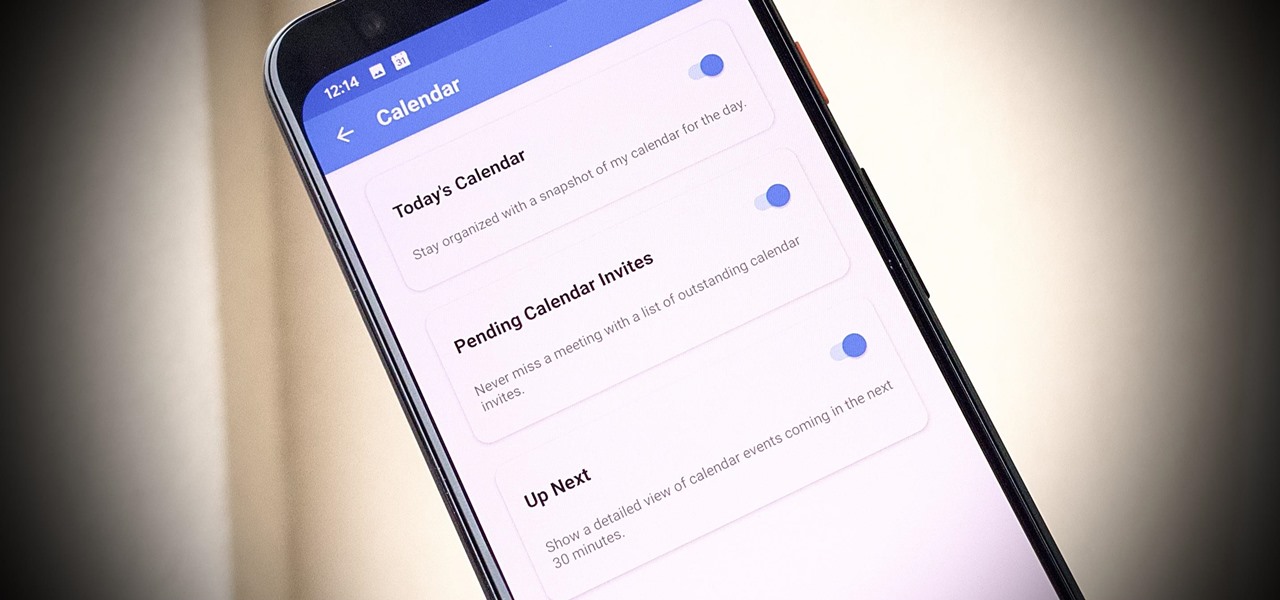
One of our favorite email apps, Edison Mail, just got even better. In versions 1.17.0 (iOS) and 1.12.0 (Android), the app introduced a new Assistant, a powerful tool that makes organizing travel, packages, entertainment, bills, calendar, and more a breeze over email. The best part? You can customize it to your liking, so the Assistant works precisely as you need it to.

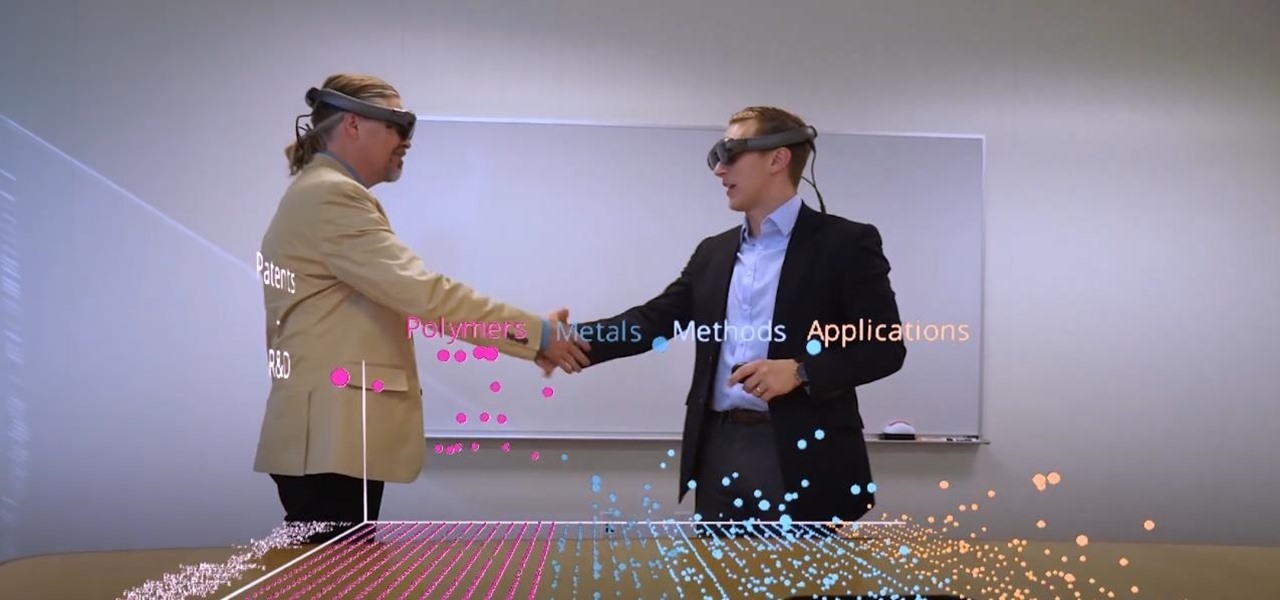
Thanks to the expanding universe of augmented reality tools being made available, increasingly, anybody can liven up sleepy office meetings with immersive computing.

Rumors are what Apple dreams are made, so most of the time it's best to ignore the juicy ones -- but some Apple rumors demand a least a little attention.

You may not have thought of dorks as powerful, but with the right dorks, you can hack devices just by Googling the password to log in. Because Google is fantastic at indexing everything connected to the internet, it's possible to find files that are exposed accidentally and contain critical information for anyone to see.

Apple has seemingly always made it a priority to show how much it cares about user security and privacy — enough that it has a page dedicated to it, proclaiming that "privacy is a fundamental human right." It's true that there are few issues more important than user privacy when it comes to technology, and Apple only makes things better in iOS 13.

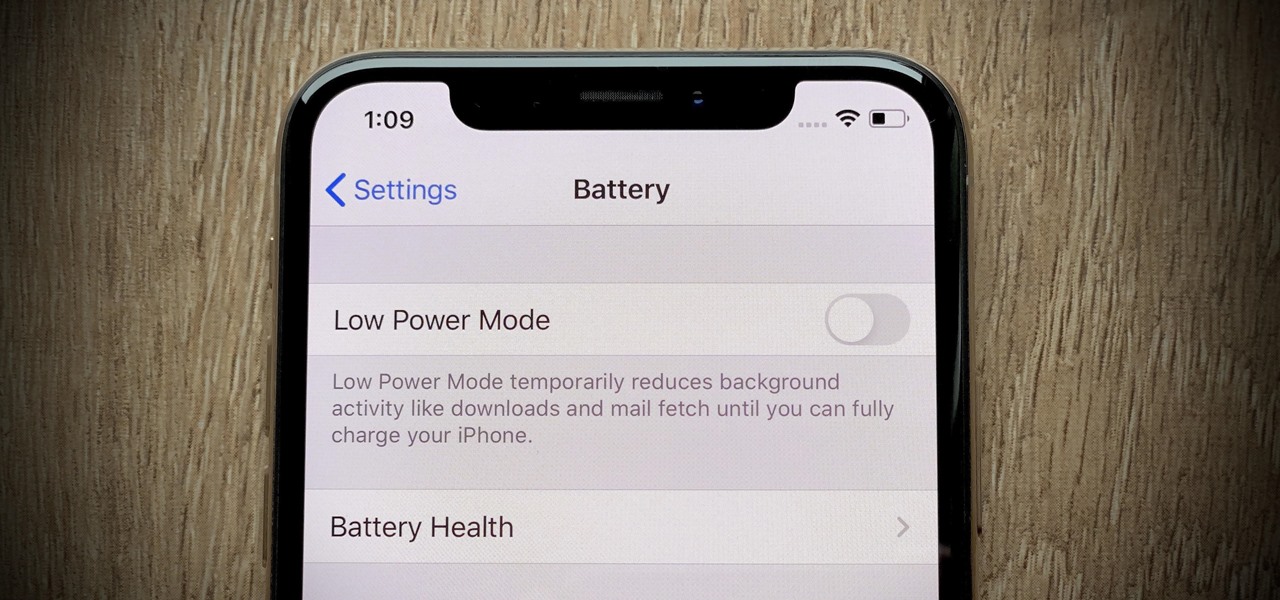
There are plenty of jokes out there about the battery indicator on iPhones. Some people complain about their iPhones dying randomly at 11%, while others see hours of use at the 1% mark. Despite its inconsistencies, that battery percentage is a useful tell for how desperate you need a charger. There's just one problem: the icon is hiding on your iPhone 11, 11 Pro, or 11 Pro Max.

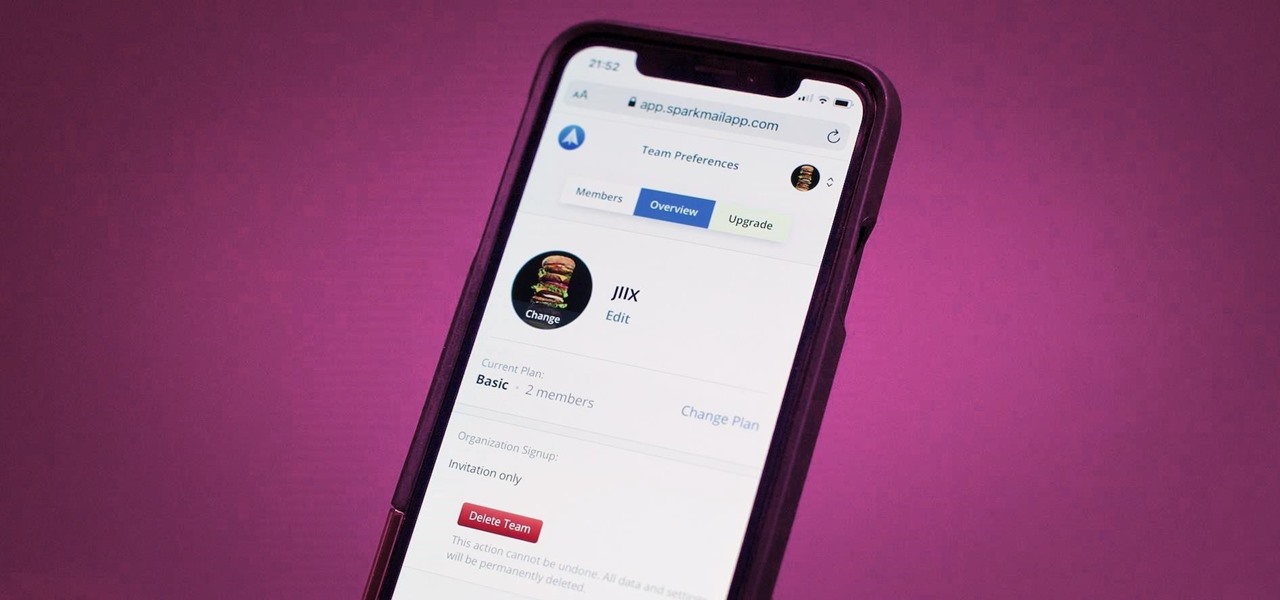
Last year, Readdle released a major update to their popular intelligent email client Spark, which brought a number of new features and improvements, including the ability for team members to collaborate on emails. You can draft new emails and privately discuss existing ones with your team, invite team members into email threads, and create and share links to specific emails.