
How To: Turbo Ping Sweeping with Python
Why did I write this when they're tons of scanning tools available.


Why did I write this when they're tons of scanning tools available.

Welcome back, my novice hackers! In this third installment of my Hacking Web Apps series, we will look at the authentication of web applications. Remember, there are many ways to hack web applications (as I pointed out in my first article), and cracking authentication is just one method.

Welcome back, my rookie hackers! So many readers come to Null Byte to learn how to hack Wi-Fi networks (this is the most popular hacking area on Null Byte) that I thought I should write a "how-to" on selecting a good Wi-Fi hacking strategy.

Hi there, Elites Welcome to my 6th post, This tutorial will explain how to hack windows, using a program (No-IP)

Welcome back, my greenhorn hackers! Digital forensics and hacking are complementary disciplines. The better you are at digital forensics, the better hacker you are, and the better hacker you are, the better you are digital forensics. Unfortunately, few people in either profession cross these discipline lines.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

Part 1: What is Popcorn Time? Part 2: What is a torrent?

Welcome back, my rookie hackers! "How can I travel and communicate over the Internet without being tracked or spied on by anyone?" It's a question many Null Byteans have asked me, so I have decided to write a comprehensive article addressing this issue.

Doxing is the act of finding one's personal information through research and discovery, with little to no information to start with. You may have seen doxing in the news, for instance when not so long ago, hacker team Anonymous doxed and reported thousands of twitter accounts related to ISIS. Doxing can be useful for finding the address of a coworker, or simply investigating people on the internet. The tutorial I will provide to you now will teach you the basics of doxing and how you can prot...

Willpower is a pretty significant word. It's the difference between sticking with a clean eating diet and diving face-first into a plate of brownies. It's what drags you out of bed on Monday mornings and into work rather than letting you stay snuggled under the covers asleep. And, most importantly, it's the kick in the butt we all require to both accomplish goals and make changes.

Lemons and limes might be among the most useful fruits in the kitchen and even beyond. Their bright, tart flavor livens up just about any dish, while their mildly acidic nature makes them incredibly useful when you want to clean your house safely. We already knew lemons were great for keeping fruits and vegetables from turning brown, deodorizing garbage disposals, disinfecting cutting boards, and neutralizing odors. But just when we thought we knew all the ways that lemons can be used around ...

I'll admit it: I've spent many eight-hour workdays stuck at my desk, staring at my computer as my breaks slip past unnoticed. I frequently tell myself I'll take one in a few more minutes—but somehow, the entire day will pass and I won't have taken a single break.

The idea of a no-churn ice cream seems like the ultimate dessert hack. But, in fact, this concept has been around for at least the past 100 years in what Italians call semifreddo.

Believe it or not, you can put your money to use very efficiently in a new way: your credit or debit card can serve as a blade in desperate situations. (It might even be handier than dental floss as a brilliant substitution for specialized kitchen tools.) While I wouldn't take bets on it slicing a New York strip steak, there are definitely many other foods it will easily slice through. What Is It Made Of?

Can you tell when your friends are serving up a bunch of BS, or are you constantly oblivious, unsure if they're spinning a valid story? With so many ways to lie and fake information floating around, it can be impossible to tell what's the truth from what's complete BS. Here's how to sort through what you hear and find the real truth.

When I was 12, for some mysterious reason, my dad put my little brothers and me in charge of cooking the Thanksgiving turkey. Naturally, my brothers and I spent the rest of the day playing hide-in-seek in the backyard and forgot all about the humble bird defrosting in the sink.

Welcome back, my hacker novitiates! A short while ago, I introduced you to regular expressions. Regular expressions are a language that is particularly useful for finding complex text patterns in streams of data.

Welcome back, my greenhorn hackers! In previous Wi-Fi hacking tutorials, I have shown you ways to create an Evil Twin, to DoS a wireless AP, and to crack WEP and WPA2 passwords, but in this tutorial, I will show you something a little bit different.

Admit it: you've been caught muttering to yourself under your breath in very public places. Maybe you've gotten stares while wandering the grocery store talking to yourself out loud. If you're like me, you might even talk yourself through various tasks, giving the atmosphere a little background noise.

Eating healthy poses a challenge nowadays with so many options that taste great but aren't really good for you. Nutritionists have made it their life's work to understand what actually does a body good. Here's how you can follow their example.

Complete silence or a non-stop Pandora playlist? People are often divided on what type of work environment they prefer. Whether you're a frequent loud music listener or you can't stand any kind of background noise, chances are you're pretty set in your ways.

Many Android games use large, storage-heavy OBB files to store supplemental data. Generally, games with high-end graphics download these extra files when you install them from the Google Play Store.

You're in the middle of cooking and a car alarm, cute kitten, or neighborhood brawl made you step away from the stove for a few minutes longer that you should have. It happens to almost every home cook. Most of the time, nothing dramatic happens, but every now and then, you end up with something like this:
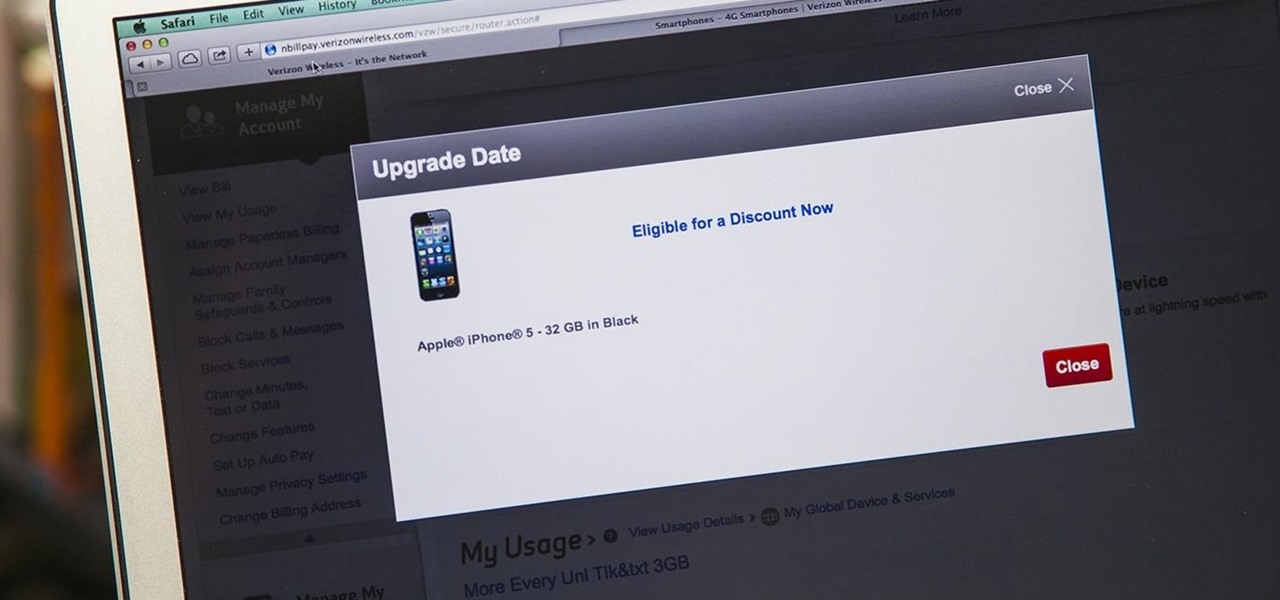
iPhone 6 pre-orders begin on September 12th, with the devices set for sale on the 19th. If you're ready to pick one up—no matter if you're a loyal iPhone user or an Android user about to make the switch—now is the time to check your upgrade eligibility.

Biting into a perfectly ripened piece of fruit is enough to convince you to give up baked goods and plant your own garden. The combination of flavor, juice, and sweetness in a ripe mango, apple, plum, or berry is the stuff of life itself.
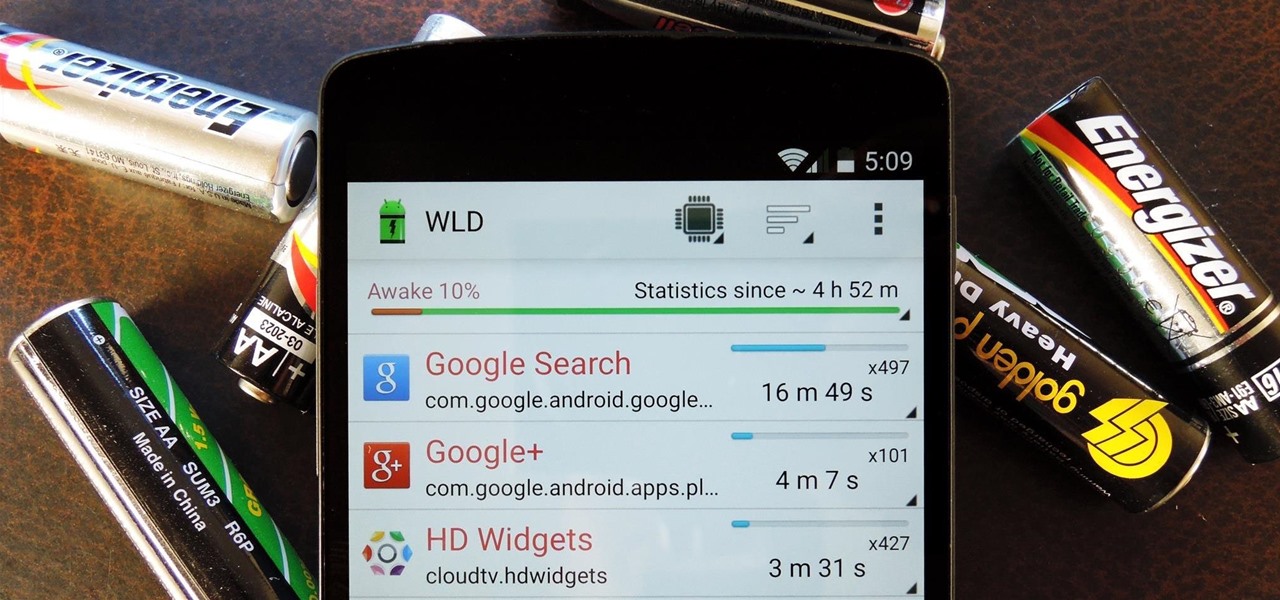
Android uses a set of permissions that apps can request to perform certain actions, and you're notified of these permissions each time you install an app. The problem here is the fact that you aren't given any built-in way to deny apps these permissions (although Danny just showed a workaround for this).

Android enthusiasts have their own opinion as to whether you need antivirus software on an Android device. This debate will never end, provided that Android malware is in existence. This guide is not here to say, "Yes, you need antivirus," or "No, you don't." It's to give you all the facts, so that you can make a decision as to whether or not you need antivirus on your Nexus.

Journals are a great source of hilarity and embarrassment, detailing everything from your elementary school crushes to those super awkward middle school dances. While rereading your old hand-scrawled entries might make you cringe, that old journaling habit could benefit you as an adult.

There are spontaneous times in everyday life that just scream to be recorded on video. The crazy guy yelling obscenities on the bus. Your favorite actor at the supermarket check-out register. Maybe even your kids just being super adorable.

What separates the work habits of the ultra-productive from us mere mortals struggling to check items off our never ending to-do lists? While the answer to that question is by no means simple, one undeniable factor in their success is a clearly defined, highly organized workflow.

Boozing it up at work might have been okay back in the days of Mad Men, but today, employers prefer that their workers stay sober. What you and your bosses probably don't know is that a little drinking on the job can actually increase your creative capacity and problem-solving skills. Alcohol Can Enhance Your Creativity at Work

Welcome back, my fledgling hackers! Scripting skills are essential is ascending to the upper echelons of the hacker clique. Without scripting skills, you are dependent upon others to develop your tools. When others develop your tools, you will always be behind the curve in the battle against security admins.

As someone who's dependent on glasses to see on an everyday basis, losing or misplacing them is obviously a bad thing. I can't even see clearly enough to find the glasses that I just lost, so I'm pretty much blind now.

Welcome back, my tenderfoot hackers! We have looked at a number of ways that we sniff traffic on the network with such tools as Wireshark, tcpdump, dnsiff, and others, but each of these tools is only capable of pulling packets off the wire.
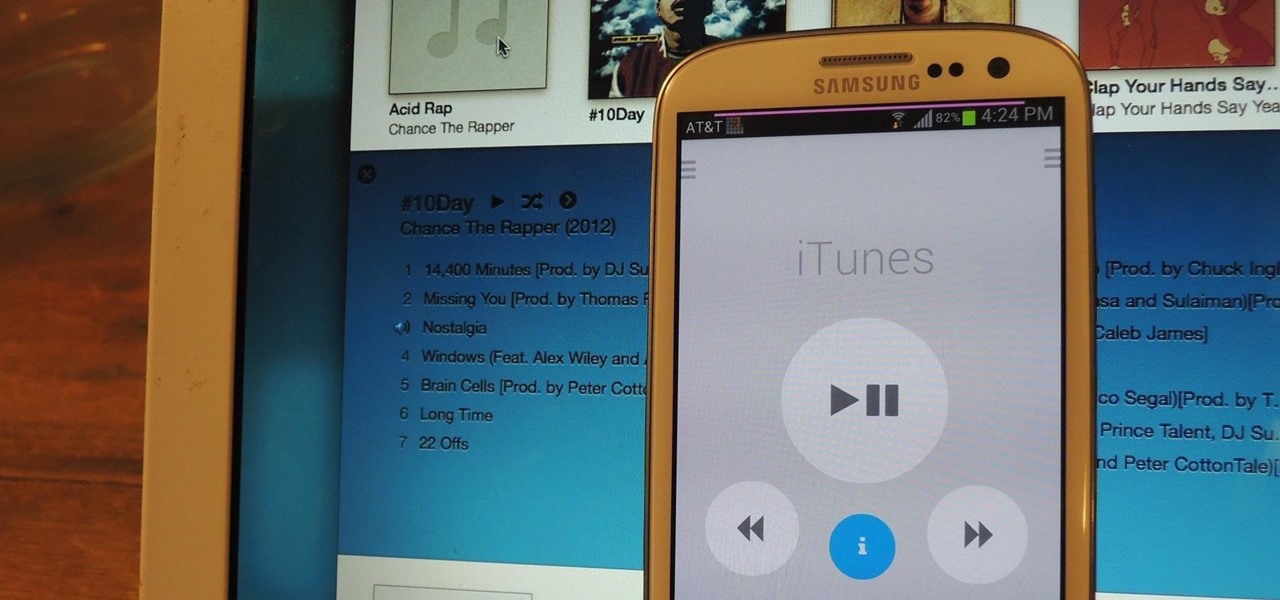
I still remember when I had to get up from my comfy spot on the couch to change the channel on my old television. So for me, the remote control may be one of the most underrated inventions of the last century. These days, remotes take on all sorts of shapes, not just the typical brick, but also in the form of watches and cell phones.

Welcome back, my hacker apprentices! I recently began a new series on digital forensics to show aspiring hackers what the forensic investigator can do and see while investigating a cyber attack. This is the second installment in that series and will focus upon network forensics. In other words, what can a network forensic investigator learn about the attacker during an investigation and how.

The integration of technology into automobiles is becoming more and more widespread each year. Tesla's Model S features a 17" display in the middle of the dash with navigation, music control, and even an Internet browser. Mercedes is working on incorporating Google Glass into their cars. Even Honda's 2014 Accord LX (their lowest trim level), boasts Pandora music streaming, Bluetooth connectivity, and a rearview camera and display.
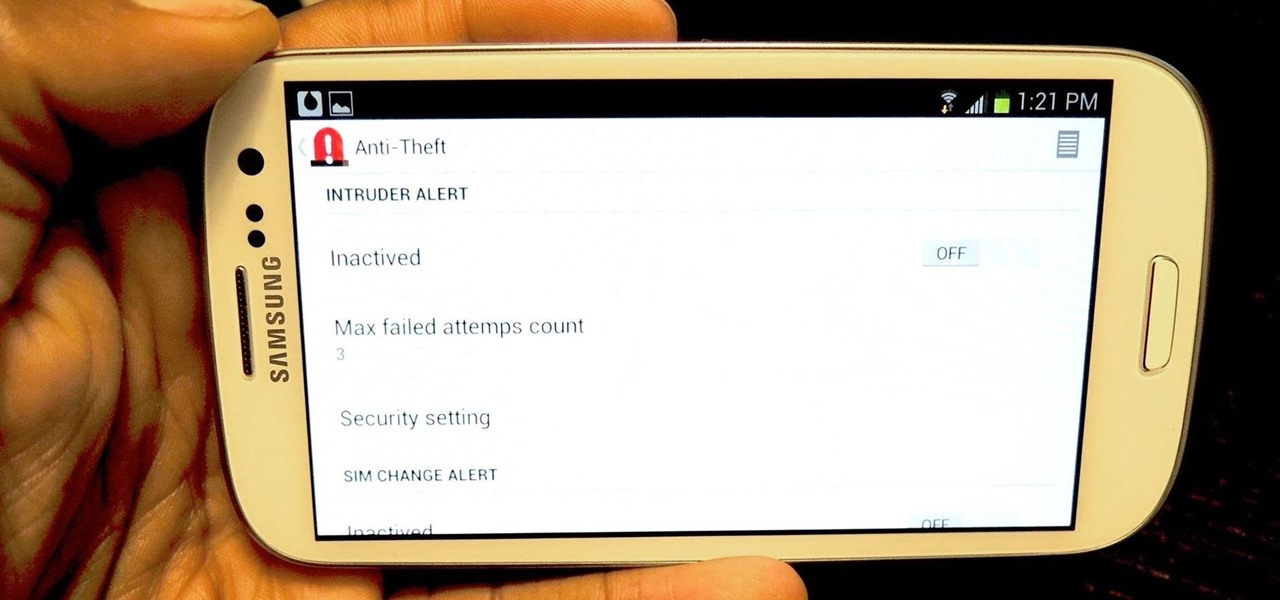
I love surprises. Surprise parties, surprise visits, surprise Patrick... But there are times when a surprise is the last thing you want, like reaching into your pocket to find that your Samsung Galaxy S3 is not where it should be.

Many of us experience highly emotional "freakouts", so to speak, more often than we'd like. Weather you experience them personally, or via your loved ones, it can be very difficult to think rationally during an episode, and for some people it can take quite a while to calm down.

Sometimes, doing the right thing is way more difficult than it should be, like trying to return a lost smartphone. Despite having the best intentions, it's often hard to track down the rightful owner, especially if the device is armed with a passcode. On the other hand, there are plenty of people who see an unattended iPhone or Samsung Galaxy S3 as a chance for profit. In 2011 alone, the number of lost and stolen cell phones in America was worth over 30 billion dollars. That's right, billion....