Mobile scanning applications are nothing new in the world of Apple, except that the majority of them usually come with pesky in-app purchases that stifle the entire experience and render some features useless until you pay for them.

It doesn't really matter what kind of cell phone you have—battery life is one of the most important features for any electronic device. We've written tons of articles on how to get better battery life from your Android, iPhone, Kindle, and more, but we've never really covered Windows Phones before—until now. The Nokia Lumia 920 and other devices running Windows Phone 8 suffer from battery problems just like any other mobile device. So, if you've got one in your hands that can't seem to make i...

This guide will explain how to configure a USB Flash Drive / Memory Stick so that you can run a keylogger within just a few seconds of plugging it in any computer.

A man once told me to never complain about gas prices. With the average price of regular unleaded gas at $3.34 a gallon, it's hard not to, even if it is the holiday season. Since my car averages about 22 mpg, the man offered me this proposition: "If I offered you $3.34, would you walk 22 miles?"

Will the predicted apocalyptic date—December 21st, 2012—really be the end of the world? In this ongoing five-part series, we examine what would happen if zombies, nuclear weapons, cyber wars, earthquakes, or aliens actually destroyed our planet—and how you might survive.

Master Rafael Negron, 6th DAN Master Instructor, and Jessica Sherlock, 2nd Degree blackbelt. Hapkido is an eclectic Korean martial art that is literally translated as “the way of coordinating energy” or “the way of coordinated power.” Hapkido is ultimately used as self-defense and combines other skilled martial arts with common attacks. he main focus of Hapkido is footwork and body positioning used to employ leverage.

Want to take your productivity to the next level in the new year? Whatever industry you're in, The Complete Google Master Class Bundle will teach you the tips and tricks to become more efficient and highly skilled in its most popular apps. Right now, the entire bundle is on sale for just $39.99 — that's an amazing 97% discount off the regular price of $1,990.

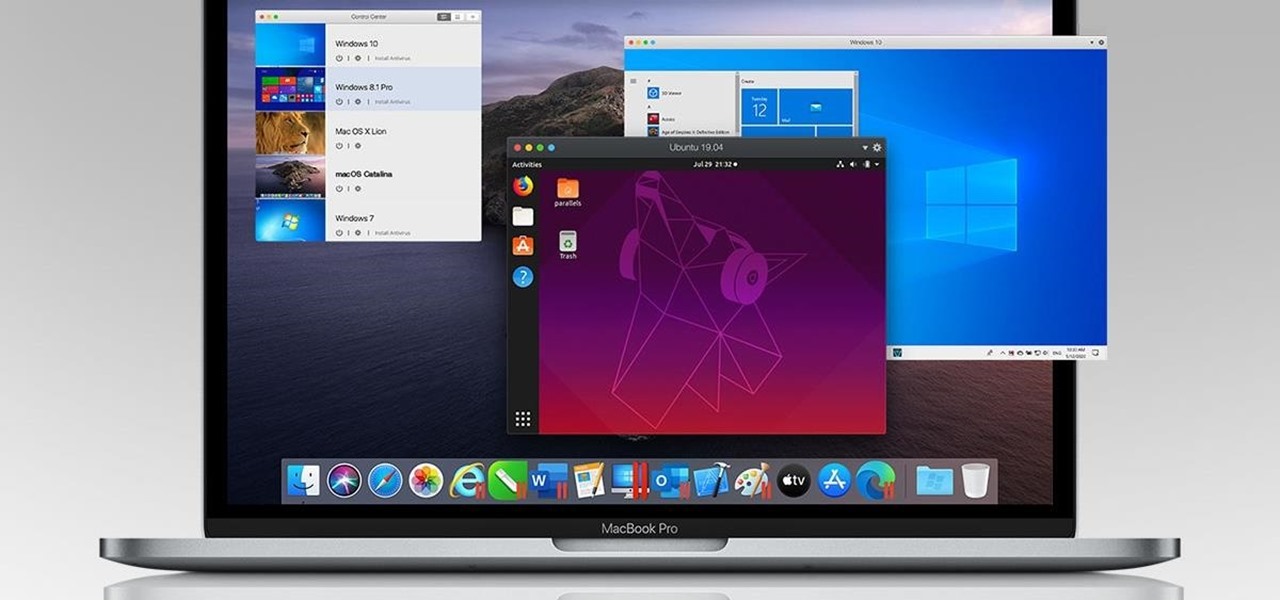
You're on your computer a lot, so it only makes sense that you download the best apps and software for it. The Official Cyber Monday Mac Bundle Ft. Parallels Pro & Luminar 4 is available for only three weeks at an additional 40% off the sale price of $69.99. Just use the promo code CMSAVE40 at checkout.

The road to becoming a skilled white hat is paved with many milestones, one of those being learning how to perform a simple Nmap scan. A little further down that road lies more advanced scanning, along with utilizing a powerful feature of Nmap called the Nmap Scripting Engine. Even further down the road is learning how to modify and write scripts for NSE, which is what we'll be doing today.

With all the web applications out on the internet today, and especially the ones built and configured by novices, it's easy to find vulnerabilities. Some are more perilous than others, but the consequences of even the slightest breach can be tremendous in the hands of a skilled hacker. Directory traversal is a relatively simple attack but can be used to expose sensitive information on a server.

While not cuddly to most, bats are shy, skilled flyers that fill an important role in their environments. A new study reveals a deadly disease decimating North American bat populations has stepped up its attack on vulnerable bat populations in the summer months.

Social engineering makes headlines because human behavior is often the weakest link of even well-defended targets. Automated social engineering tools can help reclusive hackers touch these techniques, but the study of how to hack human interactions in person is often ignored. Today, we will examine how to use subtle, hard to detect persuasion techniques to compromise a human target.

When the time comes to replace your car, you most likely have a checklist of criteria that you would like on the new one. Your car is possibly the most expensive possession you have—or the second-most expensive, after your home—so you want to make sure that you are not only getting what you want, but that you are getting the best deal possible.

I mentioned in one of my earlier articles something about ghost hackers, and very shortly stated a thing or two of what they do.

Continuing this series, I am now moving on to the section, 'Anonymous'. Hope you are looking forward to read this.

Arcade games have always been more about chance than skill (at least when I play them). Whether you're at a children's party at a Chuck E. Cheese's or drinking it up with your pals at a barcade like Dave & Buster's, you'll find similar games that hold the golden ticket to fun and cheap prizes that no one needs—boy, do you want them.

Welcome back, my greenhorn hackers! In previous Wi-Fi hacking tutorials, I have shown you ways to create an Evil Twin, to DoS a wireless AP, and to crack WEP and WPA2 passwords, but in this tutorial, I will show you something a little bit different.

A lot of people rely on the date on the packaging to tell them when food has gone bad, even with eggs, but the sell-by dates are often somewhat arbitrary and are not expiration dates. If you've been tossing your eggs based on the dates on your carton—you could be wasting perfectly good food.

Former Vice President Dick Cheney was so fearful of attacks, he had his heart defibrillator re-calibrated to block incoming wireless signals so that highly skilled hackers couldn't send him into cardiac arrest.

Mixing water and electricity is extremely risky and potentially lethal, yet that's exactly what I did with the Scariac. In its simplest form, the Scariac is just a glorified version of two wires in a bucket of water, but it's actually one of the cheapest power controllers you can make.

Remember those old vinyl records? Remember jumping on the 8-track bandwagon? Switching over to cassette tapes? How much money you spent converting your music collection to compact discs? To MP3s?

If you call yourself a hobbyist or a kid at heart, you know that remote-controlled vehicles are more than just fun. If you're a serious R/C man, you'll know all about doing everything to your model truck or car, like fixing wheels, vamping the pinion gears, waterproofing, troubleshooting, electronic diagnostics, setting up, programming and finally... racing. As much as you know about these remote-controlled vehicles, it will never be enough, you'll always be looking for more...

Products with dual capabilities make life easier, allowing us to carrying around one less electronic device. The PlayStation Portable does just that. You not only have hours of entertainment with hand-held games but can store music for on the go as well!

The Mad Hatter from Tim Burton's Alice in Wonderland not only makes a great costume but a great project. The hour-glass shaped hat, the striped pants, the fingerless gloves, and the Hatter's signature scarf are the most important components in this costume. If you're fairly skilled with costuming already, this shouldn't take more than four or so hours.

If you call yourself a hobbyist or a kid at heart, you know that remote-controlled vehicles are more than just fun. If you're a serious R/C man, you'll know all about doing everything to your model truck or car, like fixing wheels, vamping the pinion gears, waterproofing, troubleshooting, electronic diagnostics, setting up, programming, and finally... racing. As much as you know about these remote-controlled vehicles, it will never be enough; you'll always be looking for more...

For years, smartphone makers have been caught up in a megapixel spec race to prove that their camera is better than the next guy's. But we've finally come to a point where even the lower-end camera phones are packing more megapixels than they need, so it's getting harder to differentiate camera hardware.

In recent years, Hollywood has taken a shine to hackers, with hackers appearing in almost every heist or mystery movie now. This can be both good and bad for our profession. As we know, whichever way Hollywood decides to depict our profession is how most people will perceive it.

A PA system, or public address system, is an electronic amplification system with a mixer, amplifier, loudspeakers, cables, mikes and cords. Learn how to properly set up a PA system with tips from a multimedia technology expert in this free technology video series.

In this video tutorial you'll get tips on how to use the various controls of a synth keyboard, including how to use attack, release, cut-off, pitch , modulation, sustain and more, as well as how to amplify your keyboard, and the best way to create a workspace for all of your gear so you can start composing and constructing electronic masterpieces.

For almost 15 centuries the Shaolin Monastery has been synonymous with the greatest fighting skills on the planet. Boxing Classic: Essential Boxing Methods references the Shaolin Monastery as the birthplace of Chinese Boxing, and the practitioners of this martial art are known to be skilled beyond imagination. The battles fought by Shaolin Monks have become legend worldwide, retold though the ages in print, performance and film. While the origins of Shaolin Kung Fu are often disputed, and man...

Valentine's Day is almost here, and if you're like me, you're scurrying to do something special for your mate. The standard chocolates and flowers just isn't cutting it anymore, and you can only make so many homemade cards before it becomes banal and meaningless. So, what can you do that shows you put some work into it, while not breaking the bank?

If you're considering purchasing Apple's new 2020 iPhone SE, which brings many modern components into the compact body of an iPhone 8, you should know what its dust and water resistance rating means. Just how dirty and wet can the iPhone SE get without breaking any functionality?

It's been said time and time again: reconnaissance is perhaps the most critical phase of an attack. It's especially important when preparing an attack against a database since one wrong move can destroy every last bit of data, which usually isn't the desired outcome. Metasploit contains a variety of modules that can be used to enumerate MySQL databases, making it easy to gather valuable information.

After months of waiting, the iPhone 11 is here. At an event in Cupertino, Apple unveiled the iPhone 11, 11 Pro and 11 Pro max. You probably have a lot of questions after reviewing the specs sheet, including wanting to know more about the IP68 rating that all three phones have. We're here to clarify.

Even with all the success HMD had with reviving the Nokia brand in 2017, it seems their second year is shaping up to be even better. Nokia has been steadily releasing sequels to last year's lineup, most with the new minimal bezel design language. The Nokia 7.1 is just their latest creation.

They're finally here. Apple announced three new iPhone models at their "Gather Round" event in Cupertino, and they're all absolutely gorgeous phones. With bezel-less screens and polished titanium edges, the iPhone XS, XS Max, and XR are truly marvels of engineering — but perhaps the most impressive design feat Apple pulled off is the fact that two of these models are rated IP68 under the IEC standard 60529.

During E3, many major game developers announced plans to bring console and PC franchises to mobile. These titles are designed for more serious gamers with competition in mind. All of this points to a shift in mobile hardware priorities — soon, gamers will need gaming phones just like PC players need a gaming rig.

Magic Leap's recent flurry of patent applications prompted us to look around for any trademark movements from the company, and it turns out that the Florida-based company has been quite busy.

In what's becoming something of a regular occurrence, Magic Leap has yet another internal, unforced error on its hands. Thankfully, this time it's not about legal skirmishes or theft, but a rather unusual break from company protocol that has been quickly swept under the rug.

Last year, OnePlus released not one but two excellent flagship devices with the OnePlus 5 and 5T. While the 5T released sooner than expected, it brought some worthwhile upgrades, such as a near bezel-less display and a much-needed camera enhancement. Now, that the OnePlus 6 has arrived, it's time to see what OnePlus has in store for 2018.