
How To: Trim your mustache
From pirates to playboys to Village People, there are as many types of mustaches as there are types of men—but all of them need a good trim every once in a while.


From pirates to playboys to Village People, there are as many types of mustaches as there are types of men—but all of them need a good trim every once in a while.

Samsung decided to jump into the foldable category early, announcing the Galaxy Fold in February 2019. After a major hiccup, Samsung released the phone four months later to praise. But Samsung's not finished with foldables, as the new Galaxy Z Flip is just on the horizon.

Gboard is often considered the best keyboard for iPhone or Android. Google made sure to jam-pack it full of features, and you should expect nothing but the best when it comes to Google's own first-party software. But with so many capabilities, a few things might slip through the cracks.
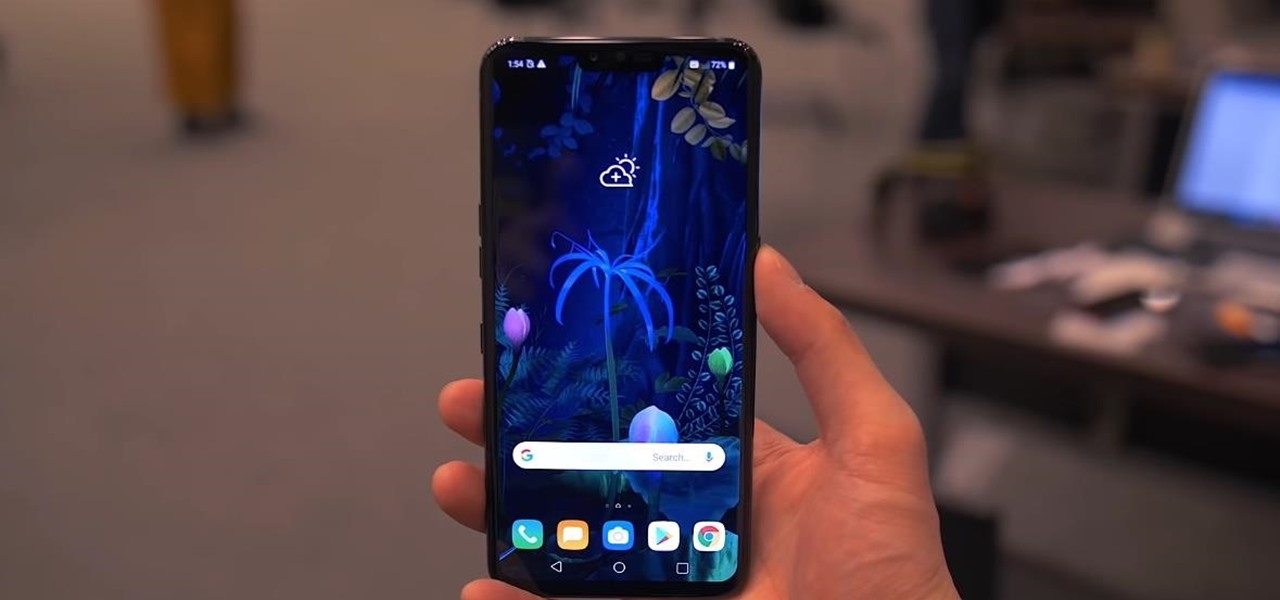
Similar to last year, LG is mixing up its releases. Instead of the G series in the first half of the year and the V series in the second half, LG is releasing both heavy hitters together. However, unlike last year, this is a true upgrade from its predecessor, the LG V50 ThinQ 5G.
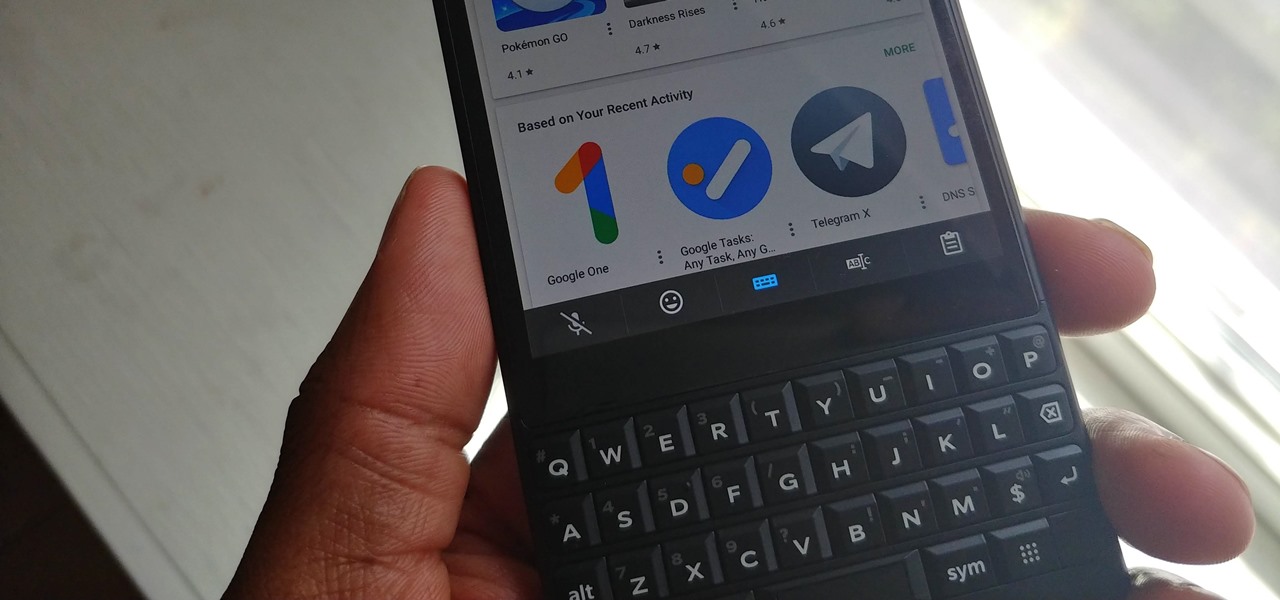
One of the best parts of the BlackBerry KEYone and KEY2 is the iconic physical keyboard. There is one major downside, though: By default, the virtual keyboard appears on these devices even when typing on the physical keyboard. Luckily, there's a way to change that.
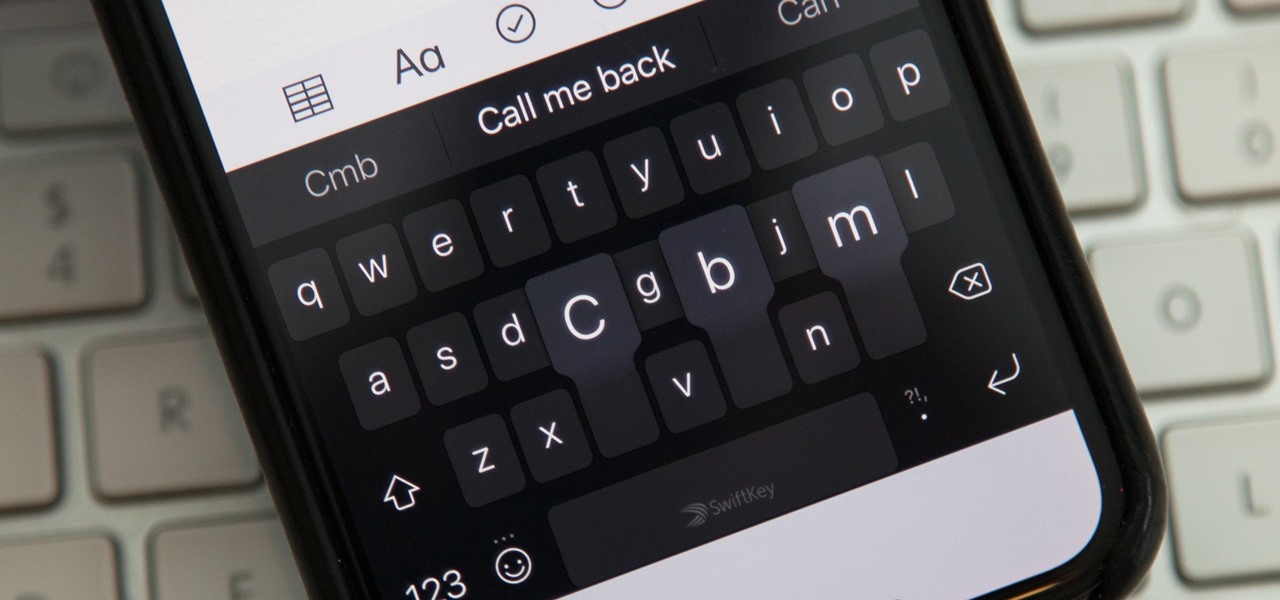
While you're probably already used to the keyboard on your iPhone, you'll likely never be able to type on it as fast as you can on a computer keyboard. But that doesn't mean you can't get any faster at typing on your iPhone. By using keyboard shortcuts to auto-populate commonly used phrases, email addresses, and other big-character items, you can drastically speed up your virtual keyboard skills.

Drug-resistant bacteria have made curing some infections challenging, if not nearly impossible. By 2050, it's estimated that 10 million people will be dying annually from infections with antibiotic-resistant organisms.

Typing on a mobile device has come a long way since the days of flip phones. Today, there are awesome keyboard apps like Gboard, which integrates Google search features and makes typing a breeze. But the whole experience still stands to improve if you take some time to learn a few useful tips.
Long before Apple and Android became household names, Nokia dominated the mobile industry. The Finnish company was one of the first to develop smartphones, and their classic N95 with 2G "high-speed" internet connectivity was declared the "best smartphone ever" by some in 2007. Outside of the US, before the iPhone became all the rage, owning a Nokia phone was a status symbol akin to wearing a Rolex or Omega watch.

If you're an Android fan, you're probably familiar with Qualcomm's Quick Charge technology or, at the very least, what it can do. Quick Charge 3.0, the third generation of Qualcomm's fast-charging technology, is built into most Snapdragon SoCs and it's what lets you charge your phone's battery up to 70% power in just 30 minutes. What's not to like?

Hello there Nullbyte users! This will be my first article here.

When performing something such as a mass mailer attack on a company, sending executables usually isn't the best option. That's why, in this tutorial, I'll be teaching you how to code a VBA script macro into a Word document in order to compromise a system. Combined with a little social engineering, this can be a very effective technique.

What's up, peeps? In this quick tutorial, we will be looking at structs, a special kind of data type.

Welcome back, my novice hackers! More and more, the world is turning to and adopting the smartphone platform as the digital device of choice. People are not only using smartphones for voice communication, but also web services, email, SMS, chatting, social networking, photography, payment services, and so on.

Welcome back, my greenhorn hackers! Throughout this series on Metasploit, and in most of my hacking tutorials here on Null Byte that use Metasploit (there are many; type "metasploit" into the search bar and you will find dozens), I have focused primarily on just two types of modules: exploits and payloads. Remember, Metasploit has six types of modules:
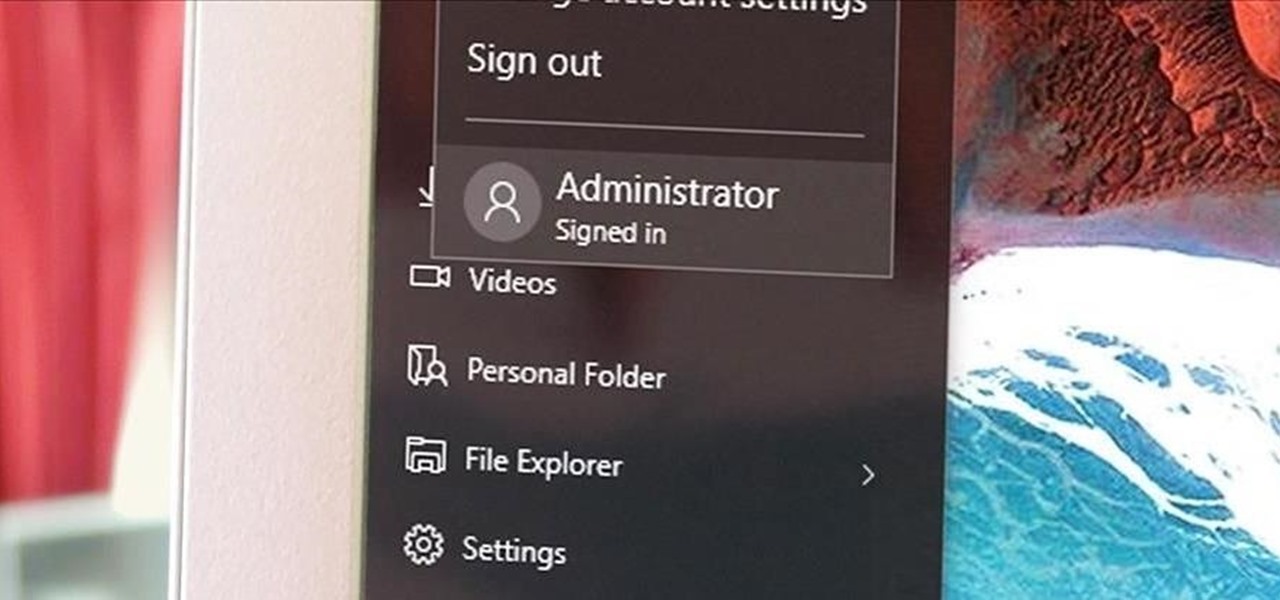
Windows has always had an "Administrator" account that allowed you to install programs and manage system files with elevated privileges. The difference between this account and a regular user account with administrator access was that you never got bothered by annoying User Account Control popups when you were logged in as Administrator.

In Minecraft 1.9 New Command Blocks can be used to make elevators. You types different commands to achieve controlling the elevator for movement you like. This tutorial tells in Minecraft 1.9 how to use command blocks to make elevator. Lets just have a look at it!

Welcome back, my greenhorn hackers! Many new hackers come from a Windows background, but seldom, if ever, use its built-in command-line tools. As a hacker, you will often be forced to control the target system using just Windows commands and no GUI.

Ruby is a dynamic, general-purpose programming language created by Yukihiro "Matz" Matsumoto in Japan around the mid-90's. It has many uses but with it's flexibility, it makes a great language to write exploits in. In fact, the entire Metasploit Framework is written in Ruby! The sole purpose of this series is to teach hackers the basics of Ruby, along with some more advanced concepts that are important in hacking.

One of Android's biggest strengths, when compared to other mobile operating systems is its open file structure. Google introduced a built-in file manager with Marshmallow that provides basic file management, but like with most apps on Android, there are alternatives. Third-party file managers are readily available, providing deeper access and control of all your files.

This is a tutorial and informational video for people who are interested in art and wondering what type of real-life jobs they can do in the art world.
There is many different types of stars in the universe. Majority of them are red dwarf stars. However, there are plenty of stars like ordinary stars (like our sun), red giants, blue stars and etc. Furthermore, when you look in the night sky, we see a lot of small and bright stars. What people don't know is that there are stars that are not even completely understood by astronomers and scientists.

When it comes to passwords, the longer and more complex they are, the better the security. Even professional hackers say so. But if you've ever tried to type in such a password, you've surely noticed that it can be a bit of a pain. Mistype one character, and you're probably going to have to clear the field and start all over again.

This is the best how-to's website that I've ever seen, and I wanted to join it. It taught me a lot, but, because I'm here to learn too, please correct me if I'm wrong.
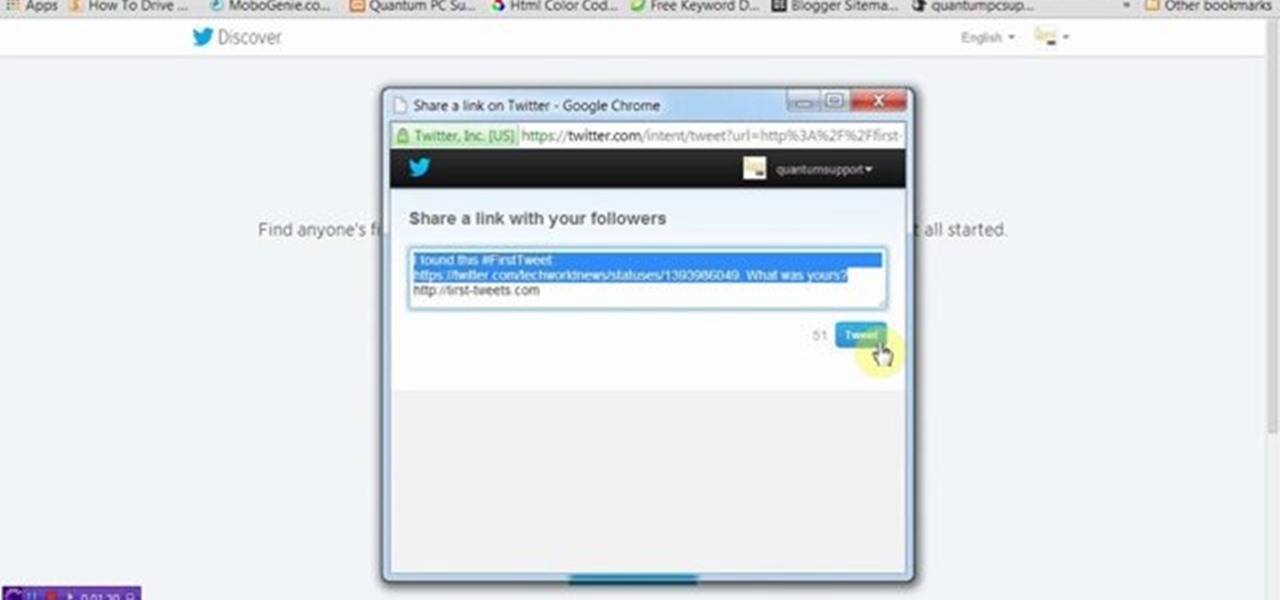
This tutorial video will show you how to find first tweet of any user in Twitter. You have to type first-tweets.com in address bar of your browser. The site will be redirected to discover.twitter.com/first-tweet page. Just type any user name and twitter will show the first twit of that user. Watch the video and try it yourself.
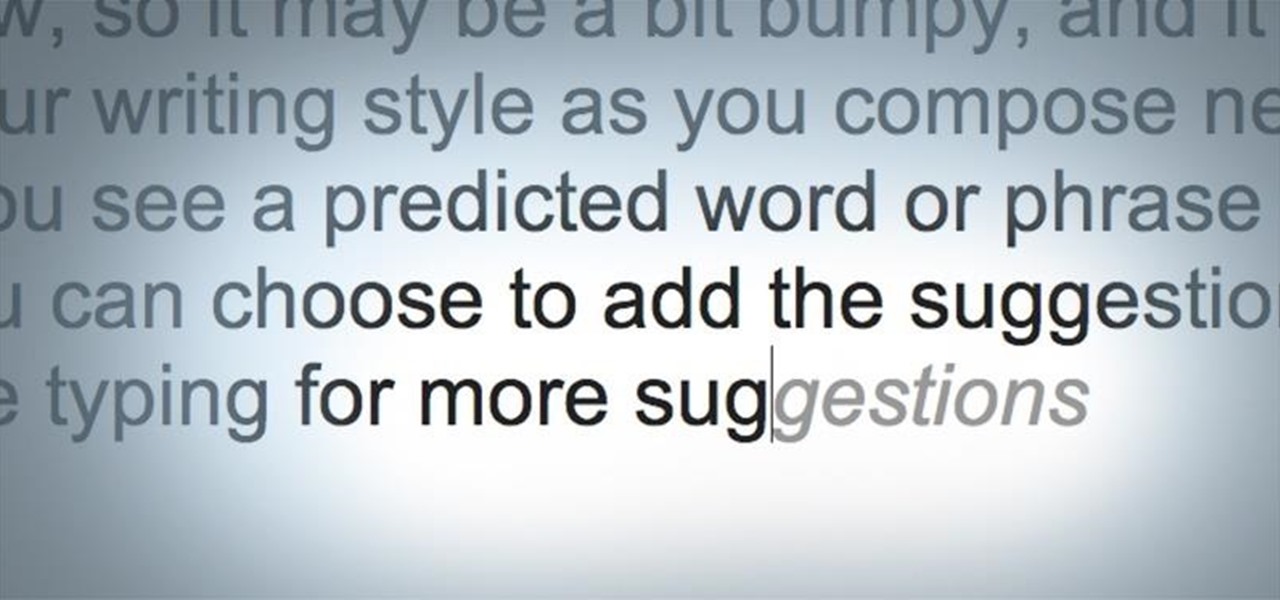
Android has had predictive text for a while now, both with stock and third-party keyboards such as Fleksy, SwiftKey, TouchPal, et al. Apple is even getting on board, with stock predictive text and third-party keyboards for iOS 8, slated for public release later this year.

Welcome back, my hacker novitiates! In previous guides, we have used one of the most powerful hacking platforms on the planet, Metasploit, to perform numerous hacks. They ranged from exploiting Windows XP and Windows 7/8 vulnerabilities, to installing a keylogger and turning on a webcam remotely. We have even been able to save the world from nuclear annihilation, see if our girlfriend is cheating, spy on suspicious neighbors, evade antivirus detection, and more.

Hello Everyone Today in this post I will teach you how to get a banner for your terminal.(Video Available at the End of the Post) To get a banner first we need "figlet" and then we have to configure it. Its Easy ..

With all of the new features and third-party apps out there making Android better and faster every day, it's quite frustrating to me that keyboard advancements remain relatively static.

Welcome back, my rookie hackers! Many newbie hackers focus upon the technical aspects of hacking and fail to give enough attention to social engineering. In fact, I would say that technical hacks should ONLY be attempted if social engineering attacks fail. Why bother spending hours or days trying to hack a password if someone will simply give it to you?

Welcome back, my greenhorn hackers! Congratulations on your successful hack that saved the world from nuclear annihilation from our little, bellicose, Twinkie-eating dictator. The rest of world may not know what you did, but I do. Good job! Now that we hacked into the malevolent dictator's computer and temporarily disabled his nuclear launch capability, we have to think about covering our tracks so that he and his minions can't track our good works back to us.

Texting is a godsend to mobile devices, but it also has its caveats. Sending a text to someone requires visual, manual, and cognitive attention—looking at what you're typing, holding the phone steady, and thinking about what you're trying to say. So, texting while doing pretty much anything else is not a wise move.
iOS 5 introduces an incredible feature that isn't very well known called "Shortcuts." It allows you to use automatic text expansion for whatever abbreviations you want. This is a great way to type several letters into your iPhone, iPad, or iPod touch and have them immediately expand into whatever phrase you want. Find out how to configure text expansion in this guide.

Colored contact lenses are becoming more popular these days, and prescription lenses are still seeing more use as well. This guide will walk you through the process of cleaning and maintaining both types of lenses as well as inserting them over your eye.

This guide to replacing the timing belt and water pump on a Ford Escort is for a 95 Escort, but it will likely help with several different types of vehicles. Watch as both the timing belt and the water pump are removed carefully from the car and then replaced with new parts.

A function or signal generator is an electronic device that can create different types of waves and send them through a circuit without building oscillators. This video will teach you how they work and how to build a basic LED dimmer that uses one as an example.

The Nokia N900 smartphone suffers from a lack of quality games due to Nokia's restrictive OS, but fortunately you can get WebOS games from the Palm Pre loaded onto it pretty easily by following the steps outlined in this video tutorial.

Fatwood is an immense boon for any wilderness survival situation. It's a type of tree that has soaked up tons of nutrients from the ground and is perfect for starting fires. It can be broken down into kindling that will start fires for you time and time again. This video will teach you how to find fatwood and how to use it once you find it.

This bloke has very strong opinions about the different types of Elemental Hero (e-hero) decks in Yu-Gi-Oh! the card game. In this video he breaks down why his e-hero deck and e-hero philosophy in general are superior to others and why Elemental Recharge is a crappy card.

An electrophorus is a type of capacitor that generates electrostatic energy. Most of you probably know this force as static electricity, the domain of door handles and polyester shirts. It can be used for all sorts of other fun science experiments though, and this video will show you how an old hard drive, some plastic, Styrofoam, foil, a cat, and other simple materials can be used to make a a simple functioning electrophorus.