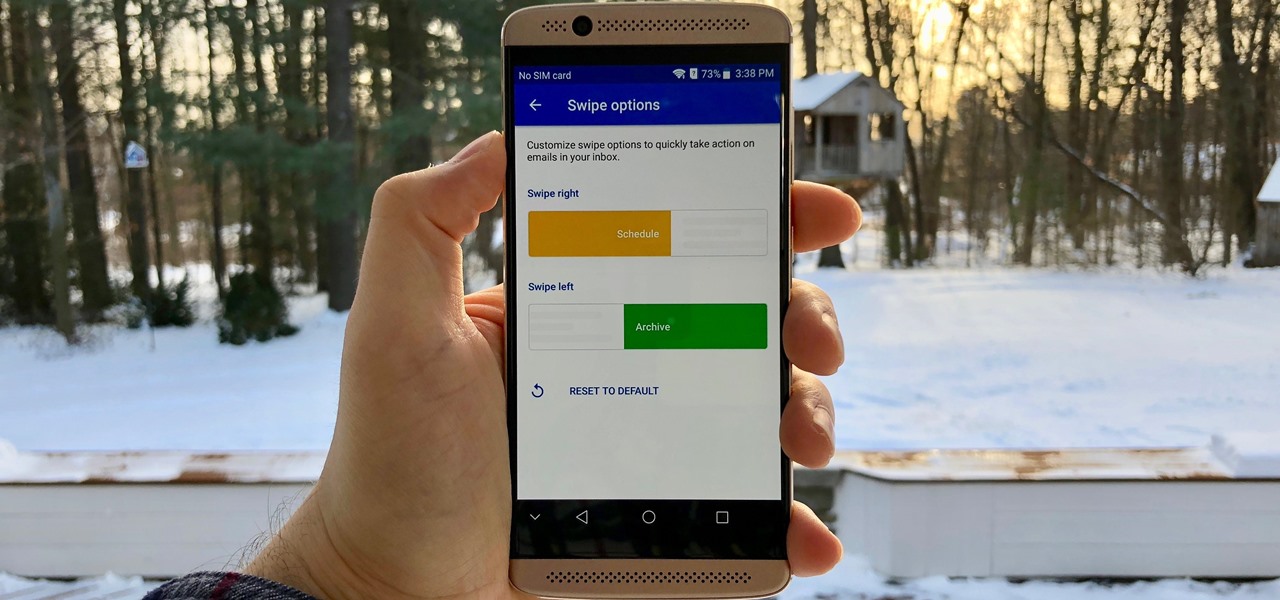
Swipe actions are an integral multitasking feature of any good email client, and Outlook is no exception. The application allows for two swipe actions at a time, but offers seven total options for those actions. We'll show you how to choose which actions go with which swipes to best tailor the app to your needs.

An attacker with shell access to a Linux server can manipulate, or perhaps even ruin, anything they have access to. While many more subtle attacks could provide significant value to a hacker, most attacks also leave traces. These traces, of course, can also be manipulated and avoided through methods such as shell scripting.

Ever wanted to communicate with another driver on the road, but just didn't know how? Sure, you could flag them down by waving or honking at them, but that assumes that they're in close proximity, that you have a unobscured path, and that they're paying attention. And if you're in a fit of road rage, flagging them down probably isn't the best idea for either of you.
Google continues to be the most commonly-used search engine for a reason. While continuing to stay ahead of the pack with advanced semantic search functions, Google even introduced Knowledge Graph results that offer key information without ever having to click a search result.

Being politically correct on social media sites is super boring. I've had my fair share of rage tweets and angry Facebook posts with some colorful wording, but sometimes using and F-bomb just gets the point across better. Now that Facebook is pushing out their new Graph Search, it might be time to clean up your profile. FaceWash is a web app that searches your Facebook profile for common bad words. You will need to give the app permission to access all of your wall posts (or course). Once acc...
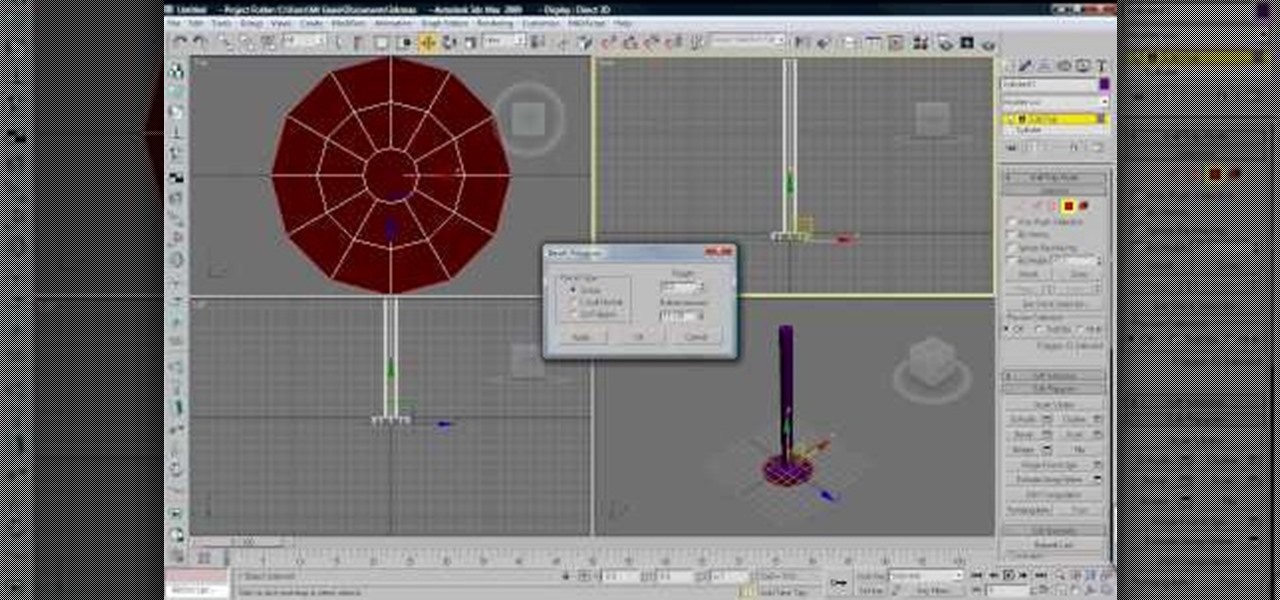
Cloth is an essential part of almost any 3D modeling project involving people. This video will show you how to properly use the cloth modifier in 3D Studio MAX to create the waving, tarnished American flag shown in the thumbnail. This tutorial does NOT feature Reactor, the in-program physics engine included with 3DS MAX, only the actual 3D Studio MAX cloth modifier.

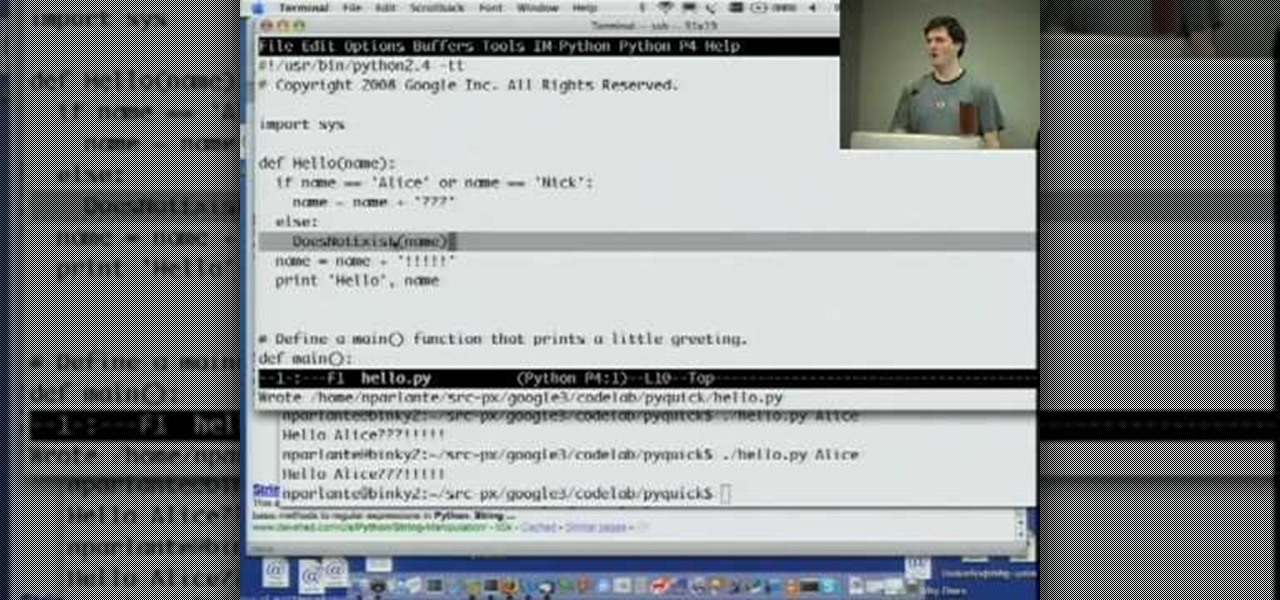
Welcome to Google's Python Class – a seven-segment, two-part free virtual class for people with a little bit of programming experience who want to learn Python. The class includes written materials, lecture videos, and lots of code exercises to practice Python coding. The first exercises work on basic Python concepts like strings and lists, building up to the later exercises which are full programs dealing with text files, processes, and http connections. The class is geared for people who ha...

Summer is coming so start saving your popsicle sticks (or more conveniently buy them from a craft store) to make your very own mini American flag. This is a great activity to take into the class room or just to pass the time on a summer’s afternoon.

Micro misters allow for low volume of water over a wide area. They give good moisture coverage. Systems can be pulled up, changed and made into what you need it to be. Keep potted plants separate from other plants. They should have their own system. There is a system to encourage growth of root systems of various plants. Shrubs get two emitters in case one clogs up, the plant still has moisture. Having the water at the base of the plant limits weed growth. There is a temporary system to get t...

Fourth of July is near, which means we'll soon be seeing an influx of red, white, and blue flags, banner, and of course patriotic sweets for those who indulge in the foodie side of the holiday.

If you've ever needed to prove you have remote access to a device, or simply want a way to convince someone their computer is haunted, SSH can be used to make a device begin to show signs of being possessed.

EternalBlue was a devastating exploit that targeted Microsoft's implementation of the SMB protocol. Metasploit contains a useful module that will automatically exploit a target, as long as it's vulnerable. But what if we wanted to exploit this vulnerability without Metasploit holding our hand? It can be done using a Python file to exploit EternalBlue manually.

Cracking the password for WPA2 networks has been roughly the same for many years, but a newer attack requires less interaction and info than previous techniques and has the added advantage of being able to target access points with no one connected. The latest attack against the PMKID uses Hashcat to crack WPA passwords and allows hackers to find networks with weak passwords more easily.

Everybody's favorite food is pizza. But not everybody knows how to actually make a pizza, which is practically a sin. And this "margherita" style pizza is a great one to learn, full of Italian simplicity— red tomato sauce, mozzarella cheese, and green basil— all the colors of the Italian flag. Check out the recipe for this delicious margherita pizza.

Figure out the 10th puzzle, Apollo, in Assassin's Creed 2. Image 1: Highlight the lunar lander just down and to the left of the moon. Puzzle wheel: Another linked-ring rotation puzzle. Your job here is to align all the channels; do this by moving the fifth ring to the left six times, the second ring to the left four times, the fourth ring to the right three times and the third ring to the left five times. Then snap the first ring into place. Image 2: Move the cursor down between the flag and ...

Why have a plain old barbecue when you can host an Oktoberfest? Make it authentic with these tips. You Will Need

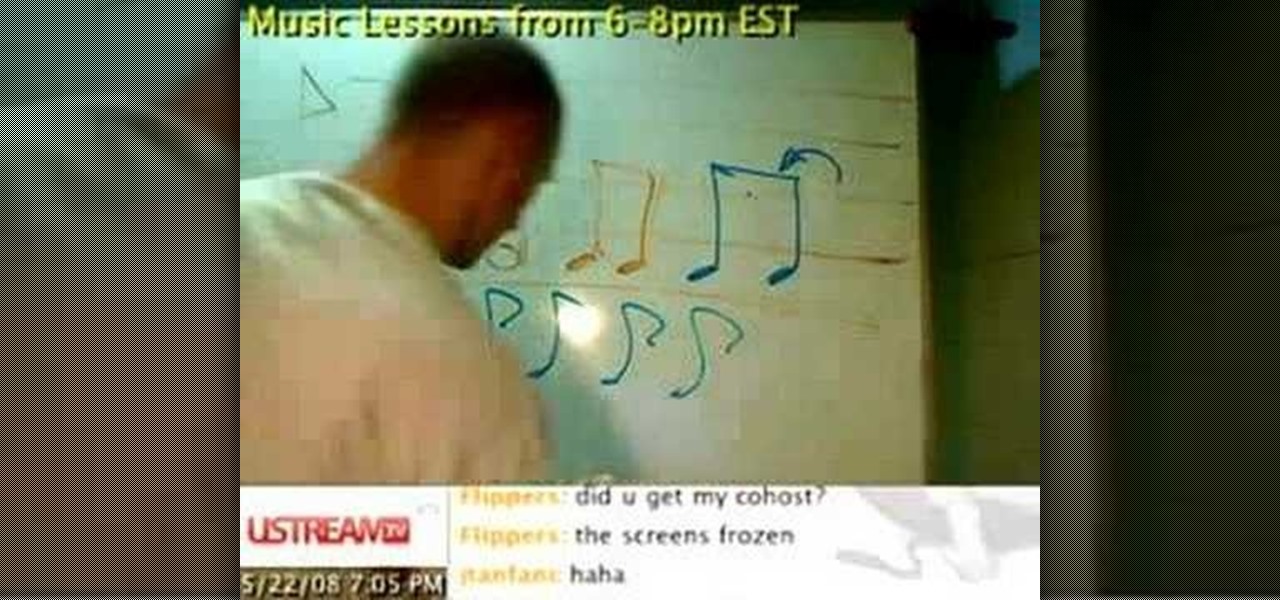
Connecting the flags on eighth notes, sixteenth notes, etcetera, is very important to neat, legible music. This how to video teaches you when to connect the flags in the music notes. Learn how to read and write music better with this music theory tutorial.

Dr. Aaron Katz explains what red flags men need to watch out for that could indicate prostate cancer and also explains what the PIN test is and how it relates to prostate health.

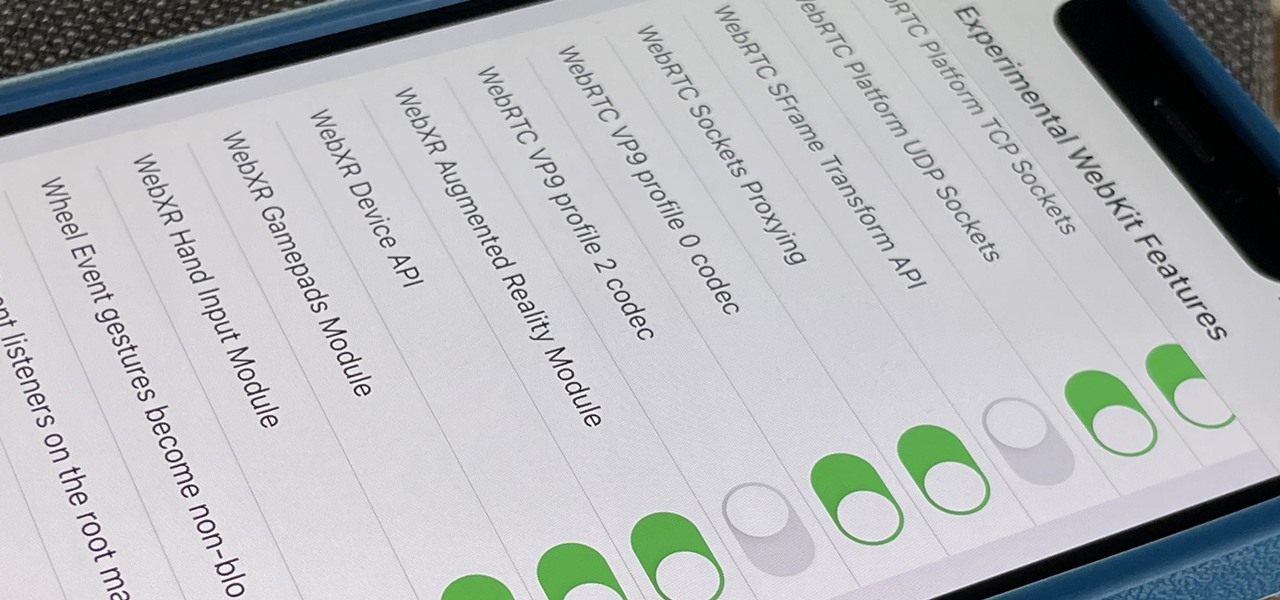
Safari's advanced experimental features give you access to new browser initiatives, upcoming web tools, element changes, behavior adjustments, and other preliminary feature tests in development by Apple. If you use them on your iPhone, you can either improve your Safari experience or wreck it. Resetting the flags provides a fresh start.

When it comes to iOS beta updates, developers get their updates first, and once they do, public testers play the waiting game. Sometimes Apple releases the public version three hours later. Other times it waits 24 hours. It's a roll of the dice almost every time. As for iOS 13.4 public beta 2, it's the latter case, coming exactly one after developer beta 2.

Web applications are a prime target for hackers, but sometimes it's not just the web apps themselves that are vulnerable. Web management interfaces should be scrutinized just as hard as the apps they manage, especially when they contain some sort of upload functionality. By exploiting a vulnerability in Apache Tomcat, a hacker can upload a backdoor and get a shell.

Gathering information on an online target can be a time-consuming activity, especially if you only need specific pieces of information about a target with a lot of subdomains. We can use a web crawler designed for OSINT called Photon to do the heavy lifting, sifting through URLs on our behalf to retrieve information of value to a hacker.

When it comes to customizing Android, there's no better way to make it your own than by installing a custom ROM. You gain new features that were not accessible on the stock firmware that came with the phone, and you get complete control over how your system looks and feels. But there's definitely a learning curve.

Microsoft Office files can be password-protected in order to prevent tampering and ensure data integrity. But password-protected documents from earlier versions of Office are susceptible to having their hashes extracted with a simple program called office2john. Those extracted hashes can then be cracked using John the Ripper and Hashcat.

With the number of web applications out there today, it comes as no surprise that there are just as many vulnerabilities waiting for hackers to discover. Finding those vulnerabilities can be a difficult task, but there are plenty of tools available to make the process easier. While it won't help find any zero-days, web scanners such as Uniscan will detect common vulnerabilities.

The ability to execute system commands via a vulnerable web application makes command injection a fruitful attack vector for any hacker. But while this type of vulnerability is highly prized, it can often take quite a bit of time to probe through an entire application to find these flaws. Luckily, there is a useful tool called Commix that can automate this process for us.

Analysis of photographs and social connections can be a huge component of social engineering. Understanding who a person is, as well as who they know, can establish links within a company. This information could be used by hackers to execute elaborate social engineering attacks.

In the last iteration of how to train your python, we covered basic string manipulation and how we can use it to better evaluate user input. So, today we'll be covering how to take user input. User input is very important to scripting. How can we do what the user says if we can't tell what the user wants? There are multiple ways to take input, we can give the user a prompt and take input from them directly, or we could use flags/switches, and take their input before the script is even execute...

In the Apple's iOS beta 3, we were introduced to a new iCloud Drive feature, an option to disable QuickType, time indicators for Recently Deleted pics, and a way to keep "self-destructing" media.

You'll need five baked eight inch square cakes, five - seven cups of white icing, five sugar cones, a little glitter, a little bit of pink icing, a pastry bag, silver non parils, gummy balls, candies, pink and red icing, mini canned hearts, red sprinkles, colored paper and tape and 5 toothpicks. Cut one cake into fourths and stack them one by one on top of a stack of the other four cakes, secured by white icing. Poke a hole in the tops of each of the cones, then sprinkle each one with edible ...

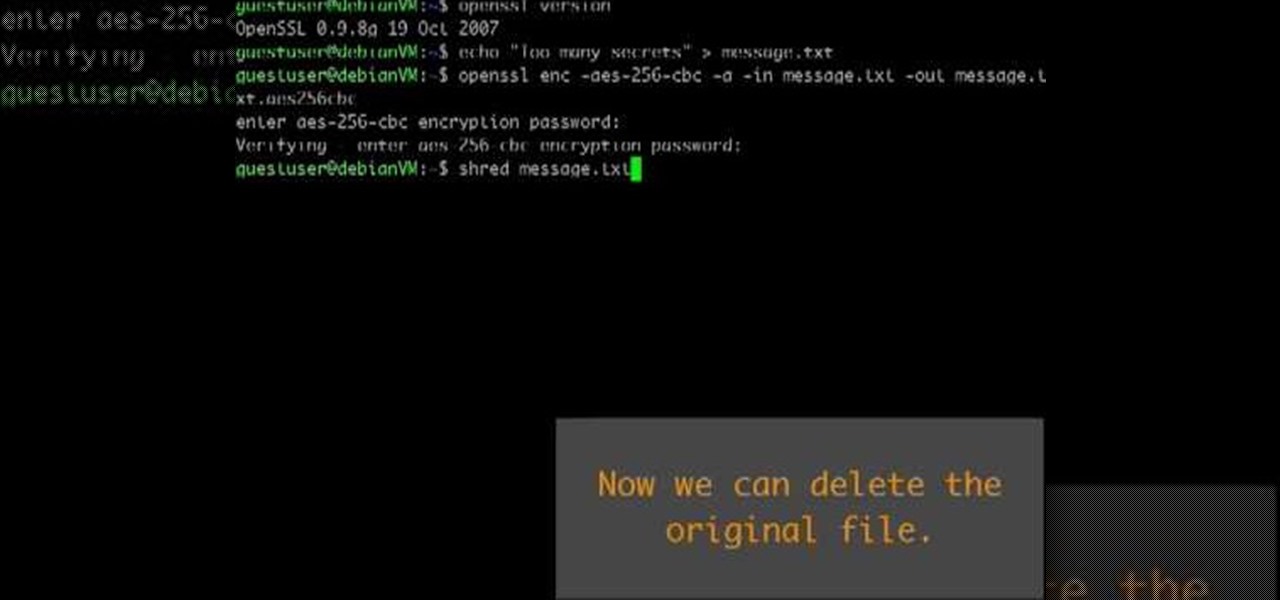
This video shows how to encrypt files with OpenSSL in Debian Linux. First we check if open SSL is installed on the system. If not, install it using packet manager. Next create the file going to be encrypted. Now encrypt the file. In this case AES algorithm in ypher block chaining mode is used. AES is US-government standard and can be considered secure. Now we are prompted for a password. In order for the encryption to be secure, we need to choose a strong password. Now we can delete the origi...

If you've changed jobs or transferred your old Rolodex onto the computer, you will have a ton of left over business cards. Why not go green and reuse the cards as something unique? Check out this video for tips on what to do with all those tiny squares of paper.

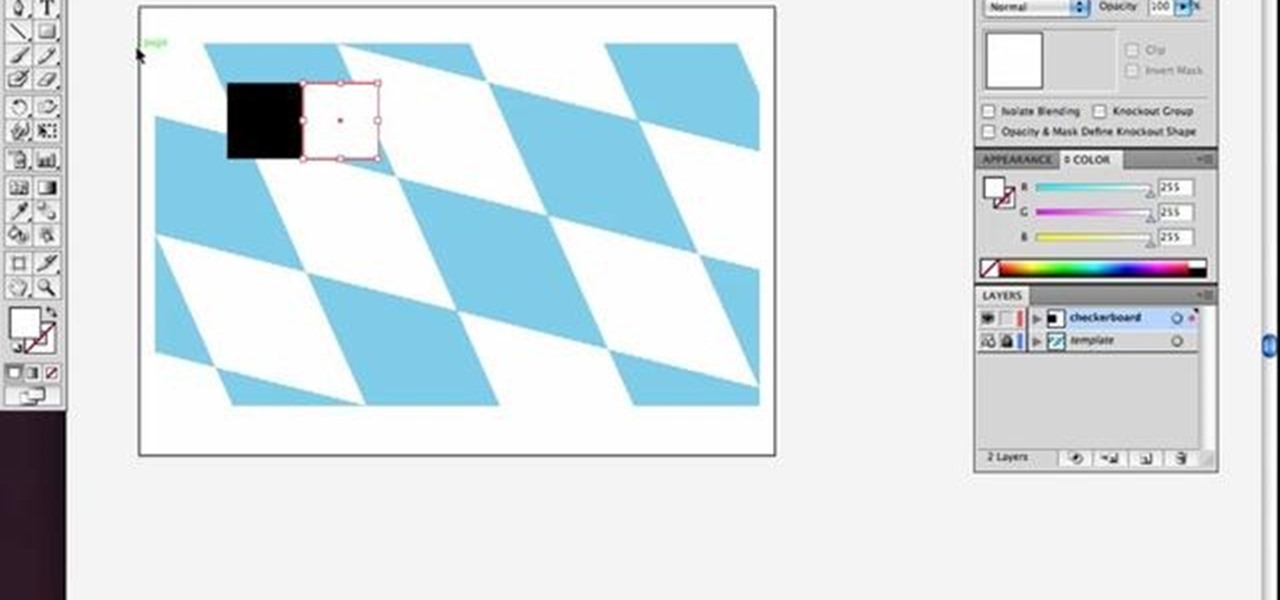
Check out this simple Adobe Illustrator CS4 tutorial to learn how to create a skewed checkerboard pattern. This technique will save you the trouble of having to use the Option and Drag method multiple times. Veerle Pieters expertly takes you through this easy pattern technique. For more Adobe Illustrator tutorials, search for Illustrator on WonderHowTo.

Last month was a whirlwind for the augmented reality industry, with the Augmented World Expo, Apple's Worldwide Developers Conference, and an exciting Magic Leap Twitch livestream all wrapping up before the ides of June. Now that we've had a chance to fully digest it all, we have a real sense of where the augmented reality industry is heading.

Mobile apps themselves are not always the end product or service for generating revenue. More often, they are deployed as tactics within a larger marketing or public relations strategy.

Whether or not The Purge franchise will be as successful as Friday the 13th, A Nightmare on Elm Street, Halloween, or even the Saw movies remains to be seen, but it's definitely winning in the Halloween costumes department.

Things are definitely starting to shape up with iOS 10. After three developer betas of the upcoming operating system, Apple has begun rolling out the developer beta 4 release for iPhone, iPad, and iPod touch, which focuses mostly on refining some of the cool new features.

If you thought humans were reading your résumé, think again. Robots do, and their one solitary objective is to systematically crush the hopes and dreams of those who don't make the cut. Instead of paying a few humans to read thousands of résumés over a couple weeks, many companies use computer programs that can do the job in less than an hour. In fact, at least 90 percent of Fortune 500 companies use what they call an applicant-tracking system, aka rejection machines.

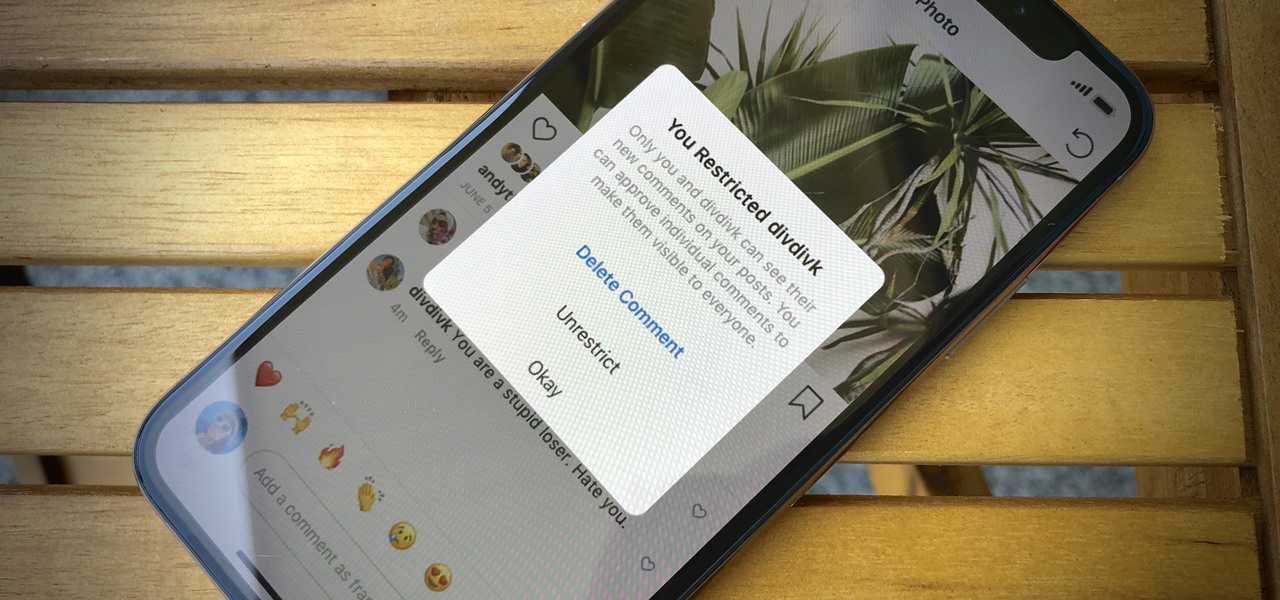
In general, the internet can be a cruel place, and Instagram is no exception. Most of the time, the platform is a fantastic way to share and view unique and creative content, to reach an audience of both fans and friends. People can step out of line and harass or bully others on posts to the detriment of the entire community. However, this type of commenting won't be sustainable for much longer.

If you're worried about the security of your Mac, there are easy measures to prevent the most dangerous attacks. Named after the tactic of accessing an unattended computer in a hotel room, we can thwart "evil maid" attacks with Do Not Disturb and LuLu, free macOS tools by Objective-See that keep an eye on unattended computers and flag suspicious network connections that indicate a malware infection.