Keep the kids learning and entertained with this fun pinwheel project. Summer is a great time for family activities, and these Fourth of July pinwheels are a math lesson, craft project and decoration-making session all-in-one.

Here an instructional video to go along with the free American flag quilted table runner pattern on MoonlightQuilts.com. Follow these step by step instructions to piece together this patriotic table runner. Quilting can be easy if you can borrow a few tricks of the trade.

We've shared a capture-the-flag game for grabbing handshakes and cracking passwords for Wi-Fi, and there are some upcoming CTF games we plan on sharing for other Wi-Fi hacks and even a dead-drop game. While security-minded activities and war games are excellent ways to improve your hacking skills, coding a real video game is also an excellent exercise for improving your programming abilities.

Alternate US history is the go-to move for hot new cable and streaming shows, from HBO's Watchmen to Hulu's The Handmaid's Tale, reimagining how things might have turned out is an endless well of narrative inspiration.

While Apple and Google have paved the way for developers to create web-based AR experiences through their respective mobile toolkits, an open source option has entered the space.

Unless you've been totally off the grid, there's a good chance you're aware that the Disney Plus streaming video service launched this week. And, if you're on this site, you're likely salivating over the new Star Wars series, The Mandalorian.

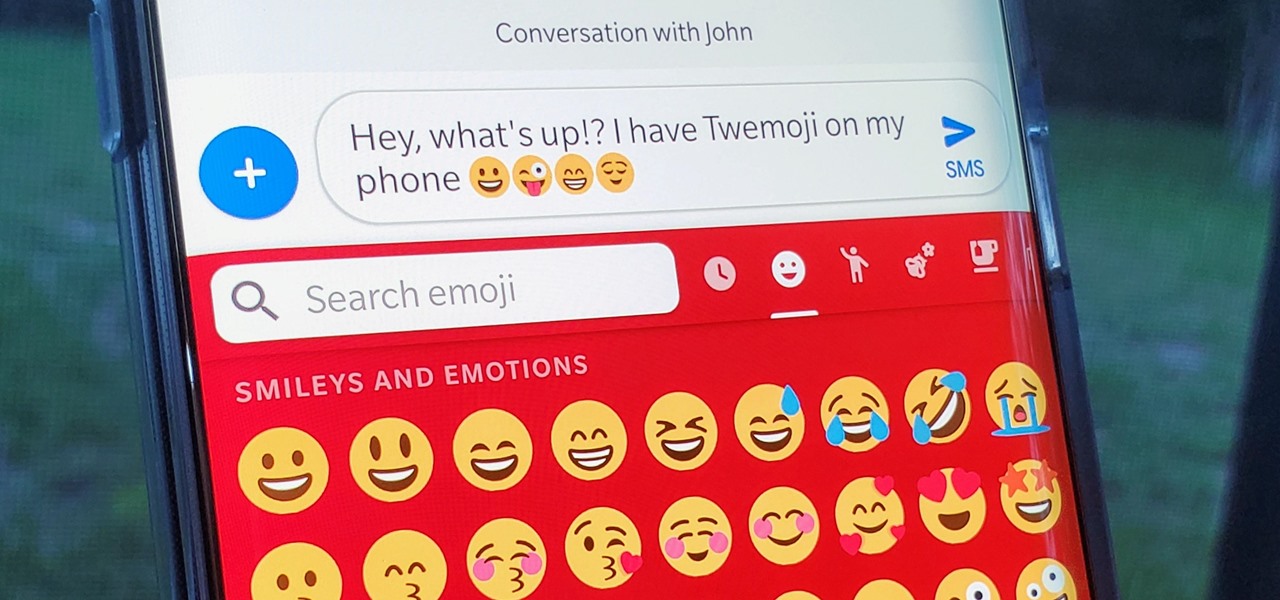
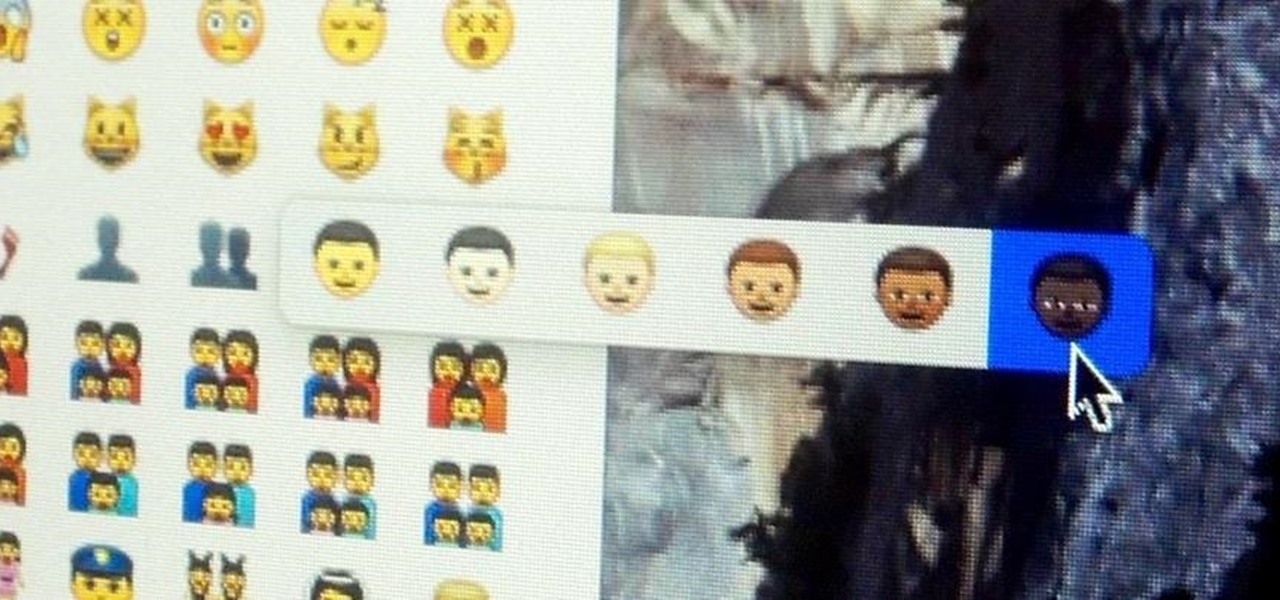
The art of emoji — the next level beyond the simple text-based emoticons we used once upon a time in the not so distant past. We rely upon emojis so much in our always-connected world of today simply because they help portray emotion into our typed out words. They've not been around very long, but have taken the world by storm just as quickly as they made their first appearance in our society.

It looks like Microsoft will finally make good on its promise to bring Minecraft to augmented reality, as foreshadowed via a HoloLens demo in 2015.

Just over two months ago, smartglasses startup North opened the doors at its two brick-and-mortar retail locations in Toronto and New York and began accepting orders for Focals. On Thursday, the company announced that those initial customers can get ready to pick up their wearables, as the first shipments have now arrived in stores.

As the stigma of online dating fades and swiping potential suitors on your phone becomes the new norm, one very real issue that you may have to deal with is catfishing: the act of being deceived by a fictional online persona. Although dating apps do their best to weed out fake accounts, a few of them slip through the cracks and take advantage of innocent people just looking for a connection.

A new augmented reality framework from Disney Research could make it possible for fans to take selfies with an augmented reality Mickey Mouse, Darth Vader, or Iron Man that mimic the user's poses.

You may have heard of a signal jammer before, which usually refers to a device that blasts out a strong enough radio signal to drown out the reception of nearby devices like cell phones. Purpose-built jammer hardware is outright illegal in many countries. Still, Wi-Fi is vulnerable to several different jamming attacks that can be done with Kali Linux and a wireless network adapter.

Augmented reality experiences created in Lens Studio now have a permanent home in the Snapchat app. On Tuesday, Lens Explorer will begin giving users access to a scrollable screen full of a variety of new Lens Studio creations.

Developers can now publish augmented reality experiences that are viewable through the experimental version of Chrome and ARCore.

Hello, budding augmented reality developers! My name is Ambuj, and I'll be introducing all of you Next Reality readers to the world ARKit, as I'm developing an ARKit 101 series on using ARKit to create augmented reality apps for iPad and iPhone. My background is in software engineering, and I've been working on iOS apps for the past three years.

The Android version of Google Chrome only shows a home button on some devices. Unfortunately, this feature isn't available to all Android phones due to several factors. But thanks to a simple workaround, you can now enable this button and set a home page regardless of what device you have.

Rovio created one of the first mobile gaming hit franchises with Angry Birds, so perhaps it is surprising that, aside from a promotional mini-game developed with Zappar, the company has yet to adapt the game to augmented reality via ARKit.

As a side scrolling game, performing various jumps in Super Mario Run on your iPhone or Android is as vital as eggs in a breakfast buffet.

Kik is an extremely popular messaging app, but it has a few annoying features that we all just sort of put up with. You can't turn off read receipts, nor can you hide when you're typing, and the photos you take with Kik's camera show up differently than ones you send from your gallery app. At least a couple of these features should be subject to change, but they aren't — well, not without some tinkering.

T-Mobile just unveiled two new services—Scam ID and Scam Block—which specifically target those pestering robo-calls that reach out to 2.4 million Americans every month.

Hello fellows nullbyters, first of i will start saying that im addicted to this community, i feel the challenge growing up so fast, all the newbies, amateurs,advanced and professionals hackers around trying their best to help the community, badly but we got some script-kids too but anyway, today we are going to learn how to install and use clanAV in kali linux.. INTRODUCTION

Surprise desserts (aka peekaboo desserts) are a gorgeous way to celebrate anything, whether it's a birthday, new baby, or just a brand new day. You can pretty much hide anything you want inside: candy, a cool design, and even other desserts. To help inspire you, try one of these fun-filled desserts out for a special, photo-worthy occasion. Then get creative and try out your own ideas (and make sure to share them with us when you're done).

Apple just recently launched its 10.10.3 Public Beta for Mac OS X Yosemite, and while it comes with mostly bug fixes for 10.10.2, it also includes a brand new Photos application that's meant to replace iPhoto and Aperture, as well as the inclusion of more diverse emojis.

Now that you've updated your iPad, iPhone, or iPod touch to iOS 8, there's a lot of cool new things to explore. If you felt a little overwhelmed from all of the detailed information available in our Coolest Hidden Features of iOS 8 post, then I've got a simple breakdown of all of the new features available with quick links to their walkthroughs and pictures, if available. Watch the short video roundup, or skip below for the list.

Apple's iOS 8 brings a few new features to the Mail app, including some speedy swipe gestures to flag, delete, and mark emails as read or unread.

For those of you who have (or had) and iPhone, one of the cooler photo apps for iOS was VSCO Cam, an extremely popular camera with pro-quality filters and effects. Now this app is available for Android on Google Play for your Nexus 7 tablet and any other devices running Android 4.0 and up.

The next generation gaming systems are so close to release I can almost taste the plastic. The new PlayStation 4 is set to be released in just a couple days on Friday, November 15th, but if you're like me, there's only one thing preventing you from upgrading in a second.

Search Engine Optimization is important for every successful SEO or blogging campaign. Therefore it is required to be implemented in the correct manner. Google consider many factors while ranking a webpage and it keeps on changing. Some of the common SEO mistakes which you must avoid are as follows:

Do you guys remember those things you hold with your fingers to write stuff down? I think they're called pens, or something like that...

Creating a class in Black Ops 2 is kind of like an art form. Every player has an insane amount of options for creating a character for all sorts of situations. Combining perks, with secondary weapons, and attachments allows for a wide range of killing options. But in order to unlock a lot of these perks and attachments, you need to gain XP. Gaining XP and collecting tokens is the lifeblood of the online gaming experience.

What's your Twitter handle worth? If it's considered "desirable" (aka short and simple), it'll get you around 100 bucks, or, if you prefer, the affections of a teenage girl.

Celebration Shoppe shows viewers how to make a Princess cupcake castle! First, you will need to make normal cupcakes - your choice of flavor - an top them with pink icing. Next, you need a stand that is three tiers in descreasing size. Next, you should embellish them and apply to the cake plate. Next, you can add in ribbon and on the top add in little castle tops and towers. You can also add in ribbons tied around each cupcake. Next, you can take sugar cones and decorate the top tier with the...

If you want something more than the standard white flash from the LED on your iPhone 4, sure you could take it apart and replace it with a new colored LED or cover it with colored material, but why would you want to do all that when you can do something a lot cheaper and A LOT CHEAPER!

June is Pride Month, an annual celebration of LGBTQ+ communities in commemoration of the Stonewall uprising of 1969.

With some of the groundwork out of the way in getting a Mac set up for hacking, it's time to start looking at toolboxes. Our first toolbox is Git, which will be used throughout future tutorials.

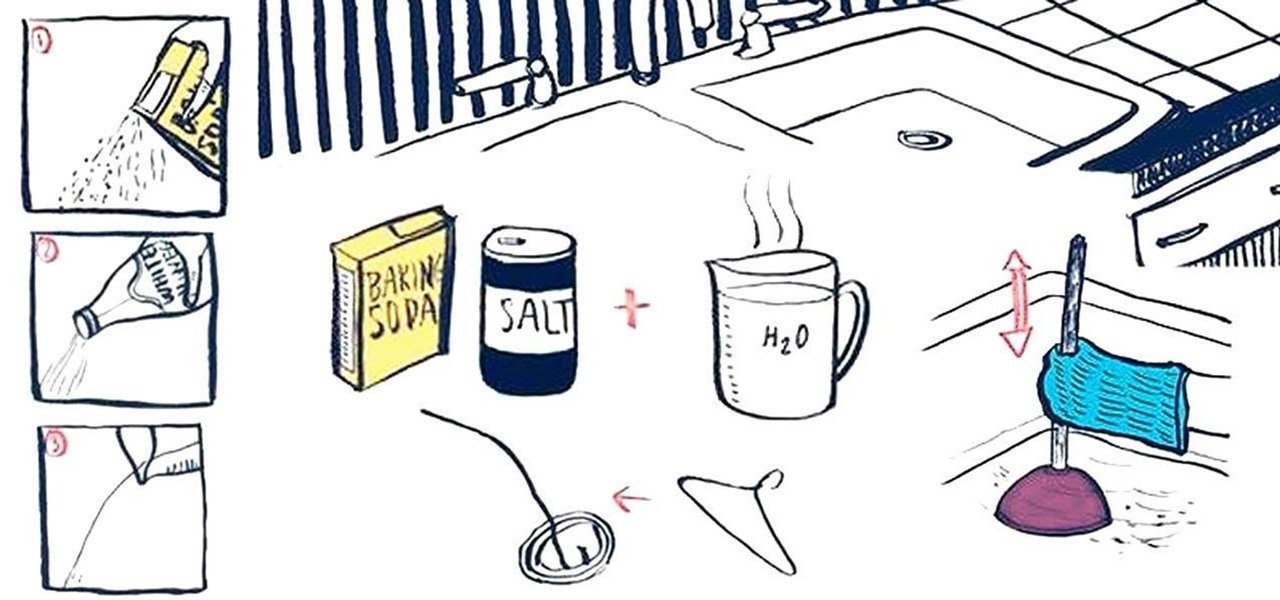
Oh, boy. A stopped-up drain. It'll inevitably happen with any home plumbing system and your kitchen sink is no exception. That clog won't go away on its own and will require immediate attention to keep any standing water from rising. But you don't have to resort to calling an expensive plumber or using a bottle of hazardous chemicals. Using simple kitchen staples or common household objects, as well as some determination, you can unclog your kitchen sink on your own without paying a dime.

SSH, or the secure shell, is a way of controlling a computer remotely from a command-line interface. While the information exchanged in the SSH session is encrypted, it's easy to spy on an SSH session if you have access to the computer that's being logged in to. Using a tool called SSHPry, we can spy on and inject commands into the SSH sessions of any other user logged in to on the same machine.

Last week, Apple released the first iOS 13.4 beta with fun and useful new features, such as new Memoji, an upgrade Mail toolbar, and the ability to control your NFC-compatible car via CarKey. To add to that, Apple just released iOS 13.4 developer beta 2, but does the update have any more new changes to be excited about?

Web application firewalls are one of the strongest defenses a web app has, but they can be vulnerable if the firewall version used is known to an attacker. Understanding which firewall a target is using can be the first step to a hacker discovering how to get past it — and what defenses are in place on a target. And the tools Wafw00f and Nmap make fingerprinting firewalls easy.

The Reminders app has always lacked the oomf that would make a person switch from a powerful third-party task manager. But Reminders has received quite the makeover in iOS 13, including a revamped UI and several new features, such as timed reminder alerts, which make the app a worthy to-do list option for the iPhone.