Django is a Python web framework used for rapid application development in any environment. In under 10 minutes, you can go from a bare Linux (Ubuntu) installation to a fully functional Django server.

This is a simple recipe that just uses regular AP flour. You can, of course, use a mixture of semolina flour like many pasta recipes suggest. But, this recipe is very user friendly, and if you’ve never made your own pasta before, this would be a good place to start. By the way, those pasta machines are surprisingly affordable at your local mega-store

This video demonstrates how to work your hamstrings by doing leg curls. The video walks you through setting up the seated leg curler machine and performing the exercises correctly.

This video demonstrates how to use a leg press to work out your quads and glutes. The video walks you through setting up the machine to your body type and performing the exercises correctly to avoid injuries.

Web applications are a prime target for hackers, but sometimes it's not just the web apps themselves that are vulnerable. Web management interfaces should be scrutinized just as hard as the apps they manage, especially when they contain some sort of upload functionality. By exploiting a vulnerability in Apache Tomcat, a hacker can upload a backdoor and get a shell.

NetBIOS is a service that allows for communication over a network and is often used to join a domain and legacy applications. It is an older technology but still used in some environments today. Since it is an unsecured protocol, it can often be a good starting point when attacking a network. Scanning for NetBIOS shares with NBTScan and the Nmap Scripting Engine is a good way to begin.

One of the best ways to improve your skills as a hacker is to learn to combine different avenues of attack to achieve success. What if it were possible to get a victim to connect to our machine and execute a chosen payload on our behalf? This is indeed possible with the almighty Metasploit and the aid of a technique known as command injection.

Transferring hundreds of screenshots, webcam recordings, keystroke logs, and audio recordings between your VPS and a local Kali machine can be tricky. Services like Dropbox don't always have the best privacy policies and suffer data breaches just like any other website. To mitigate these risks, we'll use a secure, open source, and decentralized alternative.

While it has been slower to arrive than a walker limping through thick Georgia mud, location-based augmented reality game Walking Dead: Our World finally has a confirmed launch date: July 12.

UPDATE: The P20 and its variants are officially available now. However, there's no official North American variant. You can purchase the international version of the P20 Pro or P20 Lite on Amazon, but be aware that it may not work perfectly on US carriers.

Mobile apps themselves are not always the end product or service for generating revenue. More often, they are deployed as tactics within a larger marketing or public relations strategy.

In one of my previous articles, I discussed ShinoBot, a remote administration tool that makes itself obvious. The goal is to see if the user could detect a remote administration tool or RAT on their system. In this article, I'll be demonstrating the use of Pupy, an actual RAT, on a target Ubuntu 16.04 server.

A remote administration tool, or RAT, is a piece of software used for remotely controlling machines. They are commonly used by tech support to gain remote access for troubleshooting purposes, but RATs are also an important part of a hacker's advanced persistent threat (APT) toolkit. Unlike standard administration RATs, these tools are designed to be delivered stealthily and operate undetected.

Nvidia has emerged as the indisputable leader in chips for Level 3 and even more advanced driverless applications, catching some of the world's largest semiconductor makers and automotive suppliers by surprise.

This card is stunning and has lots of texture and a mix of items to make it unusual but still easy to create.

This technique shows you how I have made these gorgeous little paper flowers that match project Nos161

Arcade games have always been more about chance than skill (at least when I play them). Whether you're at a children's party at a Chuck E. Cheese's or drinking it up with your pals at a barcade like Dave & Buster's, you'll find similar games that hold the golden ticket to fun and cheap prizes that no one needs—boy, do you want them.

As far as wallets go, mine is as full as they come; think something like George Castanza's overstuffed wallet on Seinfeld. I've got receipts, pictures, and tickets jammed inside, but what takes up the bulk of the space are all of the cards—credit, debit, gift, rewards, customer loyalty... I've got pretty much any card you can think of squeezed in. While it is a strain on my rear end, there's nothing I can do besides keep some of the cards elsewhere. However, looking for them when I need them ...

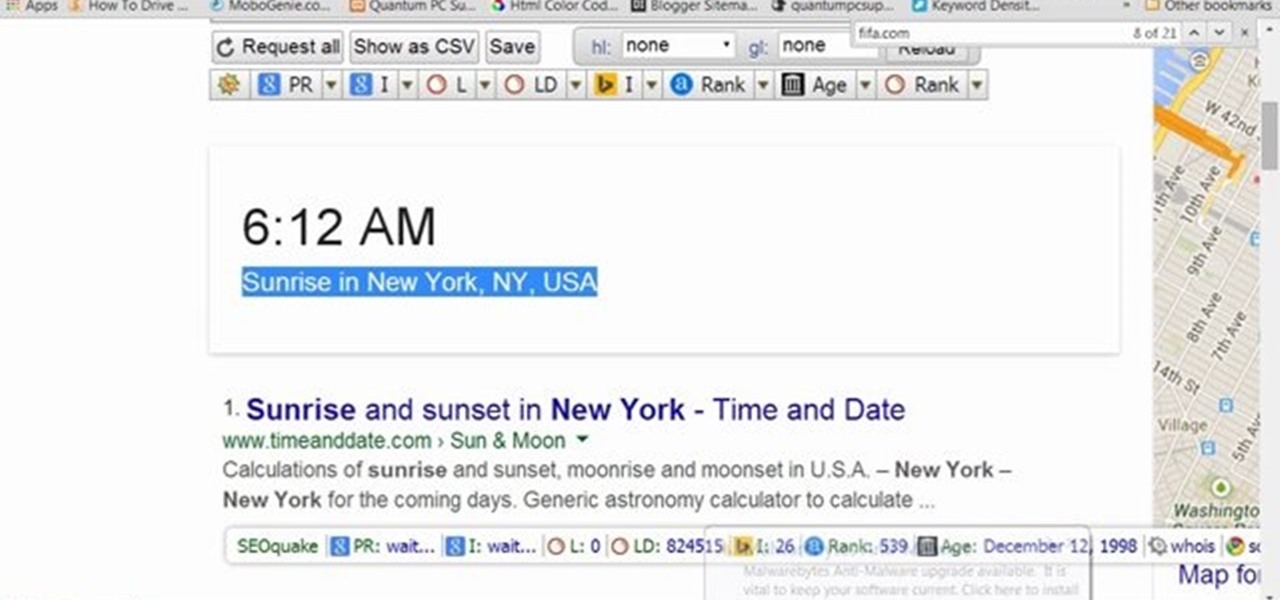
This video will guide you 5 useful tricks and tips for Google search engine. These tips include search operators, search in a single site, get definition, calculation and currency conversion, fast essential information etc. So please watch the video and follow all the steps to employ in your machine.

When Google released Android 4.2, a new feature was introduced for tablets that allowed for multiple accounts to be used on a single device. In order to create a unique experience for each user, apps and personal data were kept separate, and switching between users became as simple as tapping your profile photo from the lock screen.

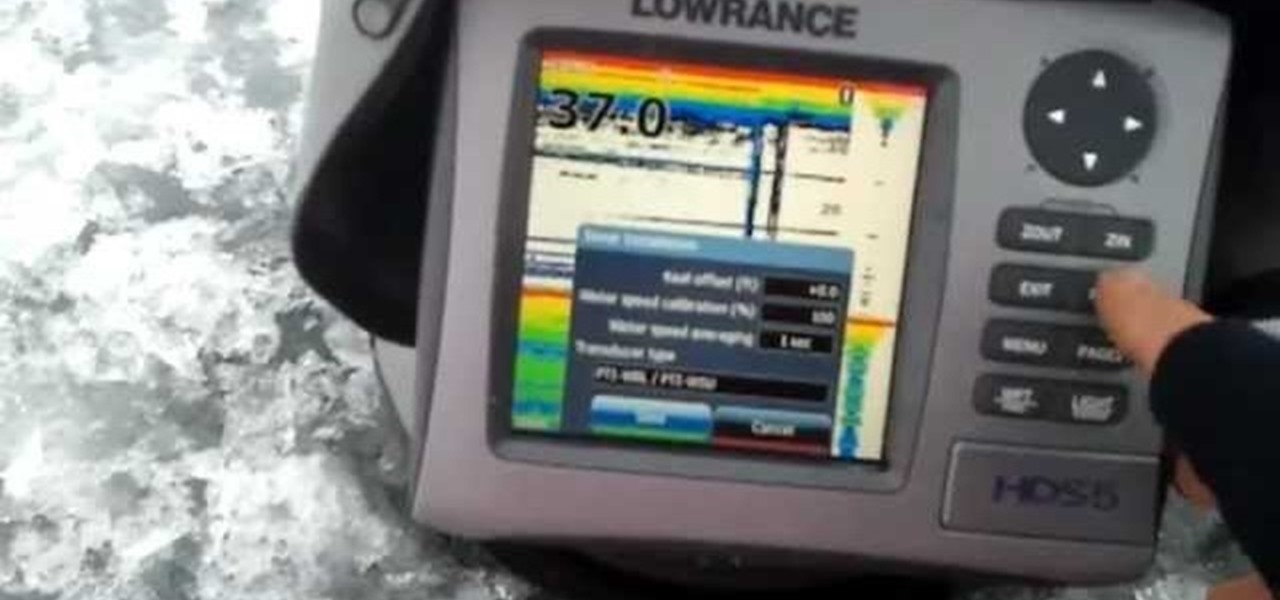
Video: . This video shows you how to set up your Lowrance unit to optimize it for ice fishing. This will also apply to Lowrance Elite and Mark series units as well as the X-67c Ice Machine.

One of the most common complaints about the Nexus line of devices is that they don't have expandable memory.

Welcome back, my hackers apprentices! To own a network and retrieve the key data, we only need to find ONE weak link in the network. It makes little sense to beat our heads against heavily fortified systems like the file and database server when we can take advantage of the biggest weak link of all—humans.

This simple contraption almost acts like a Rube Goldberg machine to give you that cold tranquility that you need during the summer.

The dryer’s idler pulley provides tension to the dryer’s drum belt so the belt won’t slip when the drum is turning. It can become faulty over time due to increased friction. If your dryer is making a squeaking or squealing nose then the idler is probably faulty. Replacing this pulley is a simple project. Repair your noisy dryer with this step-by-step tutorial!

This video shows that you can quickly replace your toilet seat with an improved seat. The video also shows how the improved seat attaches and unlocks easily for cleaning. At the rear of the seat near the hinge is a slot for access to the screw to remove the old seat. Put a screwdriver into the slot and flip up the cover and turn the screw counter clockwise while holding the nut underneath. Do the same to the other screw and remove the toilet seat. Clean the area with a disinfecting wipe. Scre...

Your car is a well-oiled machine...when you first get it. Once the new car smell wears off and the excitement of driving the latest and greatest model lessens, car maintenance becomes a chore and some of us even forget to do it regularly.

Altair from Assassin's Creed is an incredibly stylish and well-realized character, which makes him a perfect costume choice for Halloween or a cosplay convention. Watch this video to learn how to sew the red sash for an Altair costume quickly and easily.

Altair is one of the sexiest video games characters your could be this Halloween or at your next cosplay convention. The Dutchman who made this video clearly is devoted to the character, and in this video you'll learn how to make a perfect Altair under tunic for your costume. Watch this video before you start to learn how to make the template.

In this video, we learn how to reconstruct a t-shirt into an off the shoulder top. First, take a large shirt of your choice color and cut along the line on the shoulder, leaving a 1/4" seam allowance. Next, roll the hem and sew with a sewing machine. Next, cut a strap 4" wide and fold in half, then sew along the edge. After this, use a safety pin to pin one side to the shirt and then to the other side of the shirt. After these are secure, draw marks along the neck line of the shirt. Cut out t...

Create your own macro lens using the standard 50 mm lens that is shipped with your Digital SLR camera.

In this tutorial, we learn how to make a hedgehog plushy. First, choose a fabric to use, then cut out the shape of it. Once you have done this, cut it out again and pin the two pieces of fabric together. After this, use a sewing machine to sew all of the sides together, leaving a hole in the bottom. Now, turn the hedgehog inside out and then iron him flat. Place some stuffy cotton into the plushy until it is as full as you would like it. Then, sew the hole together so none of the stuffing can...

Homer Simpson would have an absolute fit over this delicious-looking kawaii donut pillow. Embellished with a thick layer of strawberry frosting and then topped lightly with candy-colored sprinkles, this pretty donut looks almost good enough to eat.

Suspension training offers an unparalleled way to train your entire upper body, from your pecs to your core to your triceps and biceps. So if you're lucky enough to have the TRX Suspension Training machine at home, or have one at the gym, then try commiting yourself to actually using it once in a while.

We know those big exercise machines at the gym can be intimidating, but the next time you hit the gym you should consider making friends with one of them because they offer a resistance (often adjustable) that you can't get with workout tapes at home.

Polymer clay is a favorite material for many crafters because it's so versatile. Those interested in creating miniatures - like small version of Domo Kun or tiny, hamster-sized apple pies - can easily mold the clay into any shape they wish, while jewelers enjoy polymer clay because you can experiment with different colors to produce all types of effects.

Okay, so just as a safety precaution before you dive right in and make yourself a batch of cotton candy at home, remember that melting sugar and corn syrup requires very high temperatures, so you could get burned if you're not careful. Make sure you keep a bowl of cool water next to you at all times just in case any of the hot stuff gets on your skin.

Photo retouchers can do a lot with Photoshop, from making a so-so gal look like a model to virtually applying makeup and cleaning up ugly cellulite. But don't you wish you could look perfectly airbrushed at the first take?

Fitlers are very important when it comes to using vacuum cleaners. Not only do they prevent damage to your cleaner's motor, but they can also prevent any dust or other debris from being layed out onto the floor.

If you like your privacy, you probably hate snoopy people, and when it comes to your briefcase, you don't want anyone's paws on it besides your own. To keep their hands off your precious belongings, you need to take some drastic measures…