More bad news for patients who have undergone heart surgery in the past five years. A new study suggests about one-third of heater-cooler units used in cardiac procedures remain contaminated with a slow-growing, potentially fatal bacteria.

While you may not notice them at first, iOS 11 included some pretty significant improvements to the Photos app on your iPhone. These upgrades will help you make your Live Photos livelier, surprise you with photos you totally forgot about, keep your photos and videos organized, and more.

Colorado State University scientists have developed new tech that quickly identifies the presence of Zika virus in mosquito populations — and in human body fluid.

Within the coming months, software startup Neurable plans to introduce the next paradigm in virtual and augmented reality: the brain–computer interface (BCI).

Apple's MacBook line of laptops is quite famous for their extensive battery life, thanks to various technologies that Apple has utilized. However, all things must pass, and over time your MacBook's battery will degrade. Certain use scenarios can accelerate the degradation of the battery—from excessive usage to high temperatures to overloading the system—and this can all lead to the untimely obliteration of your battery.

Alright so last time I gave you a homework assignment. This week we're gonna look at my version of the UDP-Flooder.

Hello ladies and gentlemen, PySec here coming at you with another informative(hopefully) article for you all. In the last tutorial, we finally finished our discussion about IP Addressing and I intentionally didn't mention a really important concept with which IP Addressing wouldn't be feasible without it. What I'm talking about is how our network device gets the IP Address in order to communicate with other devices on the network/Internet. There are many different ways for that to be accompli...

welcome back my masters , teachers and classmates , in this second part of this 0-day series we will learn the basic of fuzzing, and i bought some gift for nullbyte(a 0 day vuln that will be released today exclusively on null-byte) .

One of my favorite things to do when I visit my parents is cook. Aside from the fact that I adore cooking with my mom, there's something comforting about returning to the kitchen that I first started playing in 20 years ago. Nearly all of the tools and appliances are the same ones that I used as a kid, and the familiarity is palpable.

Welcome back, my amateur hackers! Over the course of the next year, we will be developing our own zero-day exploits. In my first article in this series, I introduced you to buffer overflows, which are the source of some of the most lethal exploits, particularly the "remote code execution," so we are focusing our exploit development here on a buffer overflow.

Welcome back, my aspiring hackers! Those of you who use Windows in a LAN environment understand that Windows machines can share directories, files, printers, etc. using "shares." This protocol dates back to the 1980s when the then dominant computer firm, IBM, developed a way for computers to communicate over the LAN by just using computer names rather than MAC or IP addresses.

Greetings. This how-to on hacking Windows 7/8/10 etc. admin account passwords using Windows Magnifier is focused on adding, changing, or deleting an admin level account on a Windows 7/8/10 etc.

Marinades are among my all-time favorite tricks as a cook for several reasons. They're easy like Sunday morning, they let time do what it's supposed to, which is work for you, and you get a huge return for relatively little effort on your part.

Welcome back, my rookie hackers! The more we know about a system or network, the better our chances of owning it and not leaving a trace for investigators to follow. One of the often overlooked sources for information is the Simple Network Management Protocol (SNMP). Many rookie hackers are not even aware of it, but it can prove to be a treasure trove of information, if you understand how it works and how to hack it.

If you're marginally inclined towards computers, you've probably been approached at some point by a family member who wants you to "fix" their system during a visit home. With the holidays coming up, these opportunities (or ambushes) are even more likely.

Welcome back, my fledgling hackers! Awhile back, I demonstrated one of my favorite little tools, netcat, which enables us to create a connection between any two machines and transfer files or spawn a command shell for "owning" the system. Despite the beauty and elegance of this little tool, it has one major drawback—the transfers between the computers can be detected by security devices such as firewalls and an intrusion detection system (IDS).

Welcome back, my fledgling hackers! The database is the hacker's "pot-of-gold," as it contains information that is very valuable to both the business and the hacker. In this, the second of my series on hacking databases, we're on the "hunt" for Microsoft's SQL Server. Although far from the most commonly used database (Oracle hold's that title), Microsoft's SQL Server is very often found in small-to-medium sized businesses. Even a few big businesses use it.

Welcome back, my rookie hackers! Many newbie hackers focus upon the technical aspects of hacking and fail to give enough attention to social engineering. In fact, I would say that technical hacks should ONLY be attempted if social engineering attacks fail. Why bother spending hours or days trying to hack a password if someone will simply give it to you?

Welcome back, my hacker novitiates! Many of you have written me that you're having difficulty installing and running Metasploit on a variety of platforms. No matter if you're using Mac, Linux, or Windows, I strongly recommend you install BackTrack as your secondary OS, a virtaulization system, or on an external drive. This particular Linux distribution has many hacking and security tools integrated—including Metasploit.

Wet shoes are uncomfortable, no one can deny that. Just think about walking around with soaking wet footwear ... and each squishy step you take. Makes you cringe, doesn't it? It can happen in heavy rain, at the beach, or from an unforeseen puddle on the street. And while you can't always avoid soggy shoes, you can rest easy knowing that the next time this happens to you, you know the secret trick to drying your shoes faster without damaging them with excessive heat.

Remote Desktop gives you access to your Windows 8 PC or device from wherever you are to run your applications and access your files remotely.

Stand out from the high street fashion clones with stuff you’ve fashioned yourself. It’s easy to take old pieces of electronic junk and transform them into all sorts of fun ‘n’ funky geeky accessories. Like a totally useful tote bag, a what-on-earth-is-that wallet and a bedazzling belt. It’s terribly geeky but chicy too. Here’s how…

When I left off on our last hack, we had hacked into the ubiquitous Windows Server 2003 server by adding ourselves as a user to that system so that we can return undetected at any time. The problem with this approach is that a sysadmin who is on their toes will note that a new user has been added and will begin to take preventative action.

Welcome back, hacker novitiates! In the next few hacks, we will be breaking into Windows servers. In this installment, we will learn to add ourselves as a user to a Windows 2003 server. Of course, when we have added ourselves as a user, we can come back any time and simply log into our account without having to hack into the system and risk detection.

Notes: My guides are setup like old Lego instruction booklets; picture intense/text lacking. Just remember you're building from the ground up, each step is a layer to go onto the previous layer.

Tutus are not just for ballerinas anymore! Anyone who feels like twirling, dancing or just running around with a little extra poof can wear one! Follow this tutorial and make a tutu for yourself, your daughter or anyone else looking for a little fluff!

Messy drawers getting you down? You no longer have to spend another day rummaging through unruly junk drawers. With some cardboard and character expressing contact paper you can turn any drawer into a neat and well organized one.

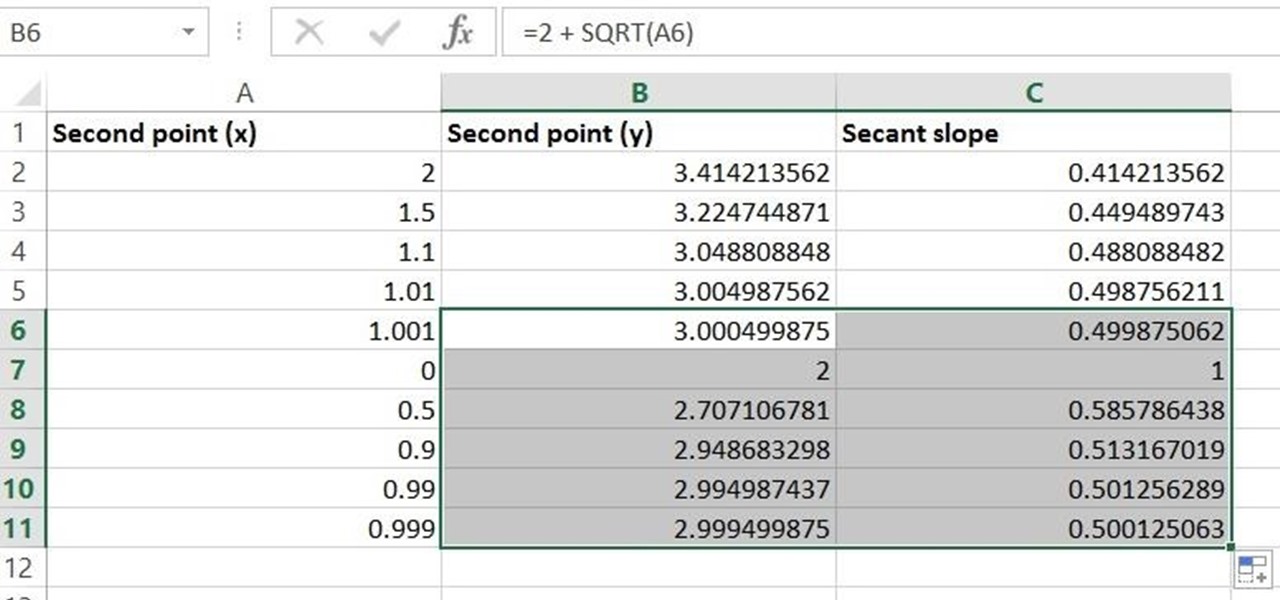
Given a function, you can easily find the slope of a tangent line using Microsoft Excel to do the dirty work. That is to say, you can input your x-value, create a couple of formulas, and have Excel calculate the secant value of the tangent slope. This is a fantastic tool for Stewart Calculus sections 2.1 and 2.2.

Find out how everything in a chemistry lab works, from pipettes to burners to recrystallization to storage. You'll get precise instructions on how to work and perform certain scientific duties in the chem lab, whether it's chemical or just ordinary high school science.

All you science and astronomy nuts out there, pay attention, this detailed video tutorial series will tell you everything you need to know about using the Meade EXT Backpack Telescope to ogle the universe.

In this tutorial, Tom Howard shows us how to bleach jeans the proper way. This is far better than just placing your clothes in the washing machine the normal way. To do this the correct way, put your water level low (for one item) in your washing machine. Now, make sure the temperature is around 50 degrees give or take 5 degrees. Now, add 1/2 c of chlorine, adding more if you want your jeans to be lighter. Now, leave this is to soak for about 20 minutes and wash your jeans for 30 minutes. Mak...

Your first bank account can be exciting and confusing at the same time. Check out this video and learn how to manage your money and accounts so you don't wind up in the red. You don't have to earn an MBA to make good financial decisions; this video offers plenty of suggestions to keep your accounts on track.

We don't mean to alarm you, but we may have just found the coolest charger in the world. The Mopoint World's Smallest 65W GaN PD Charger offers fast and simultaneous charging, and it just happens to be on sale right now for 14% off, costing just $42.99 (regular price $49).

What does it mean when a software company obsessively focused on innovating the way we use our mobile devices to see and communicate with the world adds virtual voice agents? Possibly e-commerce magic, with a powerful layer of augmented reality.

Few things are more important than being well-versed in data analytics and interpretation when it comes to succeeding in today's increasingly data-driven world. As a data scientist, these skills are the key to a high-paying career. For hackers, there's no better way to defeat the enemy than to become the enemy.

Legendary drum-and-bass artist Squarepusher, the Warp records labelmate of fellow electronic music legend Aphex Twin, is back with his fifteenth album called Be Up a Hello, which is set to drop on Feb. 1.

Whenever a new Apple event invite arrives, the entire tech industry begins tearing the invite's graphics apart in a bid to decipher what the company may be planning on releasing in the coming weeks.

The Pixel 4 is one of the most talked-about phones of 2019, so you know there will be lots of third-party developer support. Mods are already popping up, so you'll want to get Magisk installed as soon as possible to get root access. The current method used to gain root is the quickest way yet, thanks to the recent TWRP custom recovery support for the Pixel 4.

Higher-fidelity 3D content and next-generation AR experiences take more computing power than most modern AR headsets and mobile devices can handle. But Nvidia is introducing a new cloud-based solution to address that need that will stream AR content to modern devices.