PVC isn't something you want to send to the landfill. It's not going to do anything good for the ground when it's buried. It is also something you really, REALLY don't want to send to an incinerator. When burned, PVC releases some really nasty chemicals, including hydrochloric acid and dioxin.

The dreaded moment you hope never happens—someone has stolen your laptop. You could have private information, pictures, or even private information belonging to the company you work for, all lost forever. It can cause you pain, money, or even a job.

As Google+ hums along, releasing new updates and unveiling new features every few days, Facebook seems to be in panic mode. Every week, they've been revealing new features that seem suspiciously similar to Google+.

Game demos are unfortunately a dying breed. While broadband has made it easier than ever to distribute demos to PC and console gamers, they've become more expensive and risky to make. They seldom come out before the full game, especially for AAA games. Developers realize their games are crud and that a demo is just going to make people not want to buy it.
If you‘re new to Mac, you may not realize that the Dock is not the only place you can access applications and folders. The menu bar of your desktop can also hold a dozen or more applications and plug-ins for easy access to lots of content on your computer.

On June 23, 2003, Linden labs created a free client program known as Second Life. This program allows users, or residents, to interact with each other in a virtual world by using avatars. Thanks to this program, residents are able to explore, socialize, and create and trade virtual property, and services with each other. Second Life has become one of the most popular programs used by various age ranges from 16 to 60, but how do you enter this world and get your own avatar?

alright my first idea is to go to a ski mountain wearing ridiculous stuff and looking retarded and then go on a chairlift and halfway at a spot you would hang off the chairlift and make them stop the chairlift and get everyones attention and then just drop and ski away or something like that haha (of course a height that you wont die from dropping from) and my second idea was to go to a fitness center/gym or anywhere that has a lockeroom and run around naked chasing eachother and falling in t...

If you're ready to take your chest to the next level, this video will show you a great set of exercises to continue your muscle growth. Instructor Hans from Scooby's Workshop will show you safe, effective ways to build muscle.

If your bags have seen too many highways and byways, treat them to a first-class upgrade with this idea from Rust-Oleum and ReadyMade: Give world-weary luggage a new lease on life with Rust-Oleum paint and hit the road, stat. Spray paint a stenciled image on your suitcase to update and personalize your look! You will need an image, rustoleum spray paint, a utility knife, masking tape, spray adehsive, rubber gloves and a mask. Cut out your bold simple design and use as a stencil. Use a spray p...

Car-part sculptor James Corbett can do things with an automobile that would make a Transformer blush! We call him the Rodin of the Hot Rod. The gallery below should give you an idea as to why.

This video shows you how to do the Poi spinning move "airwrap in wall plane". Make sure to check out the overhead view to get a full idea of the motions. Do an airwrap in wall plane poi spin.

This After Effects tutorial will show you how to create a flickering light effect. Hopefully you can take these ideas and apply them a little bit better than our teacher did. Simulate a flickering light using After Effects.

We've provided Google insiders, Google's community managers, authors, and celebrities for you to add to your circles. This week, we've discovered over 100 brilliant photographers for you to follow.

In terms of internet, faster = better. We all want faster internet, but how exactly do you get a fast wireless connection? Believe it or not, the answer is quite simple.

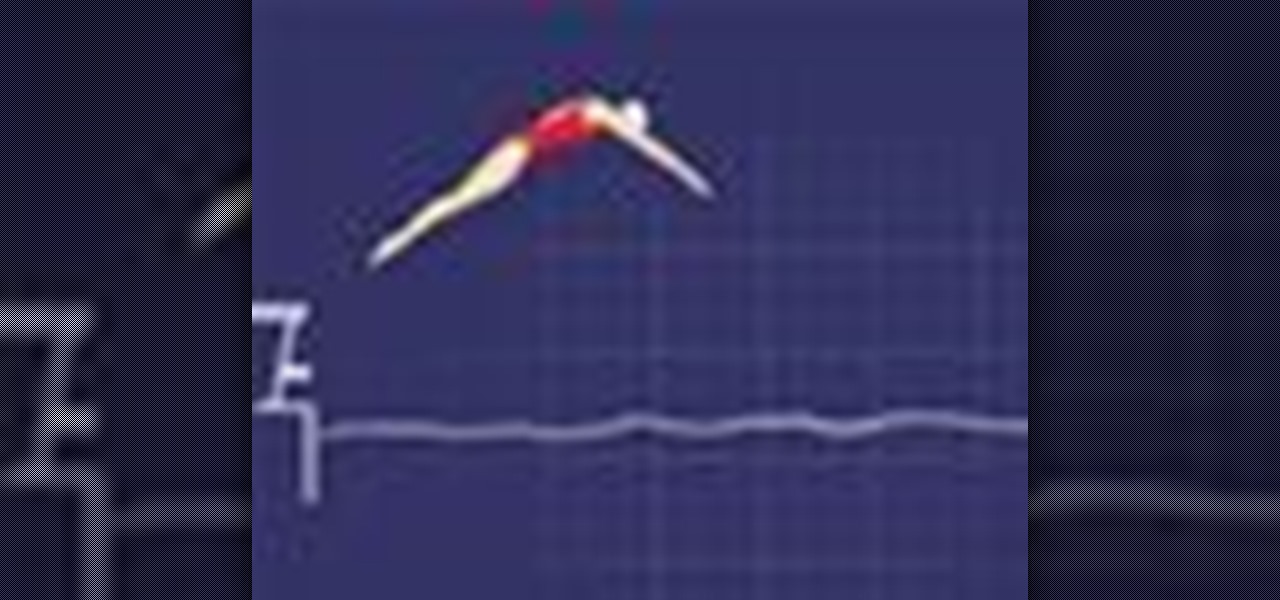
Most top swimmers use the grab start to get their race under way. This gets you moving off the blocks quickly and into the water smoothly. The starter will not begin the race until everybody is ready and still. This is really important because you can be disqualified if you fall in before the start or if you are slow getting ready. Follow along in this how-to animation to learn the best method to power off the blocks in swimming.

Clay pottery is a fun and creative art form that can be done with slabs of clay and not only on a spinning wheel. This free video clip series will show you several tips on how to construct a batter bowl and open a world of design ideas for you. Make a clay bowl - Part 1 of 20.

Toilet Payback The idea is to rig a urinal in a Men's restroom so that when a guy starts using it the fixtures on top spray back at him (hitting him in the face or chest depending on height).

its a much more intense game of dodge ball. jackass crew members will line up against a wall while another crew member peers out of the sun roof of a car with a tennisball launcher shooting tennis balls at the other crew members. idea 17

Ok look find a restroom that all the Jackass cast would would use...then replace it with a non working toilet.and the idea is that when a jackass member has to use the restroom they will sit down and poop,but inside the toilet there will be some poop hidden and that poop will explode on them and will be really gross but a great prank, and they will have poop from another jackass member.hehe sounds like great idea to me.oh yeah and it can only be one victim or maybe more who knows you guys try...

The idea is to find the biggest hill you can with a massive jump at the end. Then bomb the hill, taking flight and landing in prickle bush. The bike can't have any breaks.

Okay go with me on this one, I've had this idea for years. Play bobbing for apples, but instead of having the apples in water you should use piss (urine). Or you could use beer or some other liquid that looks like piss, and for the last person switch the beer tank with a tank filled with piss. It would be hilarious

Watch this blurb about wands and how to attach a crystal to the end of yours. If you use wood, and you harvest it from the wild, it's a good idea to leave an offering of some sort. Also, research the magical qualities of various types of trees first. Attach a crystal to your wand.

In the following video we will show you how to fold your napkins into cones. Great idea for those children's birthday parties. Fold a napkin like a cone (Pliage en cone).

Ever wanted to display text in Minecraft? It's actually not overly difficult. In this tutorial, I will endeavor to guide you through the process between storing and displaying text from memory. To do this, we will examine two different methods of displaying and storing text in memory.

Three-dimensional printing is one of the many wonders of modern technology. It's the first step towards real life Star Trek replicators and Timeline-esque teleportation chambers. While we aren't at the level of reconstructing strands of DNA, it's already possible to make tons of fun and useful designs on a 3D printer.

Mad Science is looking for more hackers, makers, and DIYers to participate in our community madness. If you've recently designed or made a project, we want to see it! Share with the other Mad Scientists out there by posting up a how-to of your pet project on our community corkboard, or even just a few cool, inspiring photos of the build.

Panasonic announced an interesting concept today that could advance millimeter-wave radar technology for automotive safety uses in detecting pedestrians, bicyclists, and other motorists.

Dreams are like an internal human holodeck. Inside your mind, anything is possible, from your grandest wishes to your worst nightmares. This is all well and good, but what if you could control your dreams and become the omniscient god of a handpicked reality whenever you go to sleep? Inception took this idea to the logical extreme by invading other people's dreams.

Over the next few months, I'll be focusing on building a fully functional, long range UAV. This series will consist of several in-depth articles on my progress and the steps involved, so you can follow along and build your own unmanned aerial vehicle!

Wireless networks. Nowadays, everyone uses 'em, but most don't secure 'em. On average, I can drive up and down any block in my city and find at least one or two open or semi-open networks on any given day. With some changed MAC addresses for good measure, an attacker can use your network as a spring board for who knows what. When the police come a few days after, they are coming to your door—and not to talk about how nice your lawn is. Don't be that guy.

How to Read a Poem Poems can be read many ways. The following steps describe one approach. Of course not all poems require close study and all should be read first for pleasure.

Okay, so what are we going to make our videos about? I’ve written before about creating articles, and what kind of content we are going to put in our articles. So what are we going to put into our videos? Let me give you a few ideas that I have. These are some things that I would do if I had a service business.

In this article, I'll show you how to built a Wireless Transfer of Energy Transmitter. Simply put, this device will send electricity to a florescent light bulb and light it up, from up to three feet. The idea originally (at least, prominently) came from Nikola Tesla (read more about this amazing inventor here), who used his Tesla coils to transfer wireless energy to light bulbs in demonstrations (photo below). However, the circuit described in this article consists of a flyback transformer, n...

Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server. This past weekend, our Weekly Workshop focused on building a suffocation trap. But today, we're going to be covering a different type of redstone trap in Minecraft—one with a 100% success rate (perfect for PvP servers).

In this article, I'll show you how to create a simplistic AES python based text encryptor. You'll need python 2.7 and PyCrypto (found here). The code is fairly simple, a user enters an encryption key (which basically tells the program how to scramble the text, using an algorithm), then the text to be encrypted. The program takes the key and text and inputs it into the "cryptograph" or code-based algorithm from PyCrypto. PyCrypto can use 16, 24, or 36 character encryption keys, but for the sak...

If you saw my last tutorial on retiring early and wealthy, you now know how anyone can invest a small amount of money over the course of their life, and by exploiting compound interest, achieve an extremely comfortable and easy going retirement. In Part 2, we are going to dive into something a little more risky: Tax liens.

When you're meeting new people, chances are they're no longer interested in collecting your phone number or email address. Instead, they're more interested to see if you have a Facebook account. So, what's a better way to get connected online in the offline world than a business card of your Facebook Timeline? The new cover image and info section on your profile makes for a great Facebook business (or personal) card.

Time-lapse photography used to require expensive and dedicated equipment, but in today's futuristic world, we now have easy access to universal machines like the iPhone, which are pretty much tricorders.

A few days ago, CloudOn released their free mobile app that brought Microsoft Office directly to your Apple iPad. The cloud-based service effectively runs Office on their end, allowing you to use apps like Word and PowerPoint to edit your documents, which you would house in Dropbox. But after overwhelming demand, they removed the free app yesterday from the iTunes App Store.