Phishing is the easiest way to get your password stolen, as it only takes one mistake to log in to the wrong website. A convincing phishing site is key to a successful attempt, and tools to create them have become intuitive and more sophisticated. SocialFish allows a hacker to create a persuasive phishing page for nearly any website, offering a web interface with an Android app for remote control.

In off-record discussions with AR experts, the consensus on ARKit is that it takes a software approach to the depth-sensors available on Tango devices. As a result, the toolkit has shortcomings, such as detecting walls and vertical surfaces.

With tools such as Reaver becoming less viable options for pen-testers as ISPs replace vulnerable routers, there become fewer certainties about which tools will work against a particular target. If you don't have time to crack the WPA password or it's unusually strong, it can be hard to figure out your next step. Luckily, nearly all systems have one common vulnerability you can count on — users!

Hello friends. This is actually my first how to.

While password cracking and WPS setup PIN attacks get a lot of attention, social engineering attacks are by far the fastest way of obtaining a Wi-Fi password. One of the most potent Wi-Fi social engineering attacks is Wifiphisher, a tool that blocks the internet until desperate users enter the Wi-Fi password to enable a fake router firmware update.

Edit: Some of the methods I show you may be difficult, or not work at famous or high quality hotels.

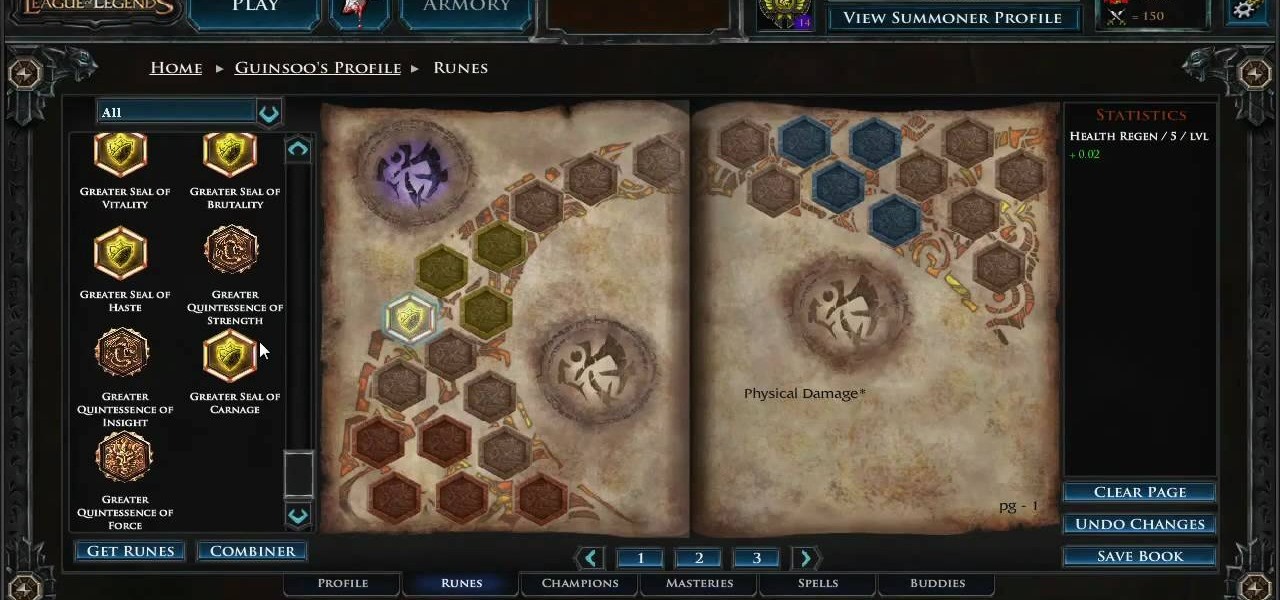
Runes are special abilities in the game which allow you customize your summoner in League of Legends. Here's how to equip runes and unlock the abilities to accumulate more runes. You can even save rune configurations in your tome and combine them to create special runes!

Poison Ivy is a villainess in the Batman comic books, a seductive femme fatale with poisonous blood and the ability to control plants. She makes excellent inspiration for a Halloween costume. Make you sexier and more beautiful. Hair: Poison Ivy is portrayed as a beautiful redhead, contrasting with the green of her outfit. Buy a red wig or use hair dye to dye your hair red. Body: Purchase a cheap green leotard, bodysuit, or swimsuit, along with 30 or so fake ivy leaves. Using a needle and thre...

Learn how to organize your kitchen. You might cook more if your kitchen weren’t so cluttered. Okay, maybe not. But, still—wouldn’t it be nice to have an organized cooking space?

The Native Americans were reknown for their ability to make use of every part of the animals they hunted for food. In this tutorial, you're shown how to make a traditional tribal flute from the leg bone of a deer.

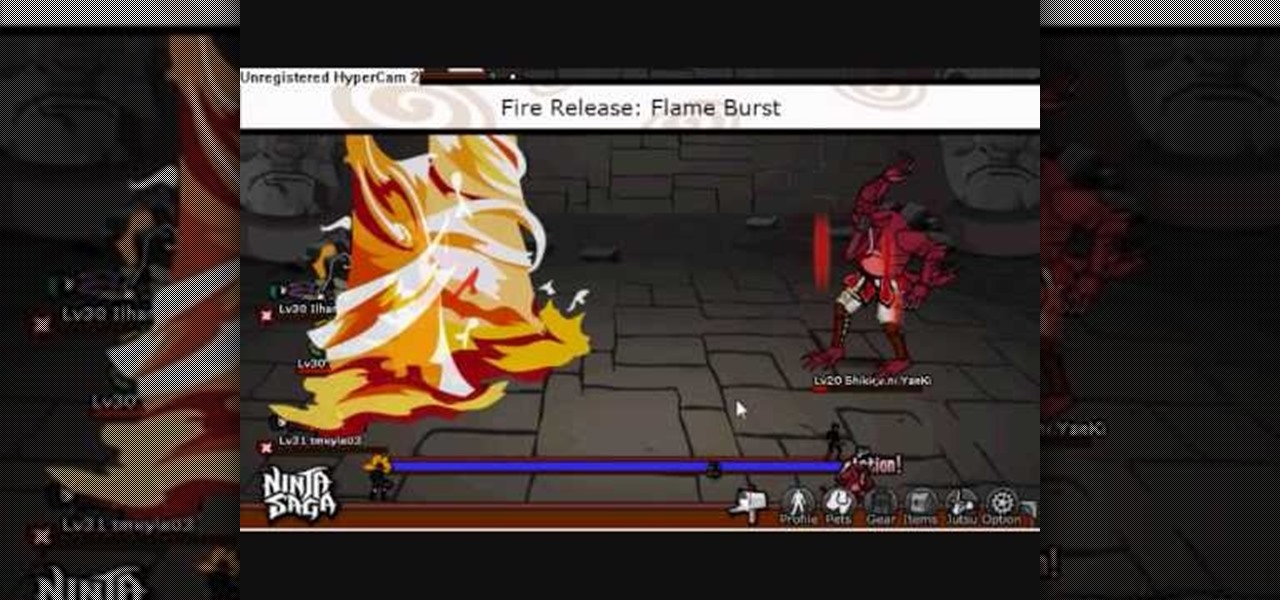
Can't just seem to get past the dreaded Shikigami Yanki in Ninja Saga? That's what this video is for! Make sure you're at least level 30 before going up aganist Shikigami, and have enough flame abilities to be able to defeat him.

Scale mail is slightly superior to chain mail, since it has a greater ability to deflect blows. But it is a little trickier to make than chain mail - but not by much! This tutorial shows you how to make an excellent suit of scale mail.

Working out your abs strengthens your core, the center of your body that holds everything together. The stronger your core is, the stronger the rest of your body will be.

One of the great innovations of Canon's DSLR technology is the relatively inexpensive ability it gives to any filmmaker to make professional quality video. This video is a great demonstration of a Glidecam and Steadicam mod designed to carry the Canon 5D Mark II and give any image a slick, professional look.

Using your iPhone is cool, but why not take it to a whole new level and use your iPhone on the computer? This video shows you how to install an application called ScreenSplitr to allow you the ability to operate your iPhone from your computer. This is especially great if your iPhone screen is broken, and you still need to use it.

Office oddballs are rarely dangerous, but they can be unnerving. Before you resort to a restraining order, try this approach. You will need:

This voice tutorial shows you how to start your baby with early childhood voice lessons. Early childhood voice exercises are a great way to nurture your child's musical ability. This how to video gives you tips so you can teach your baby to sing along with you.

Babies can learn to sing on pitch starting at age 3-5 months. This tutorial teaches you techniques so your baby can learn to sing. Start nurturing your child's musical ability with the tips from this how to video.

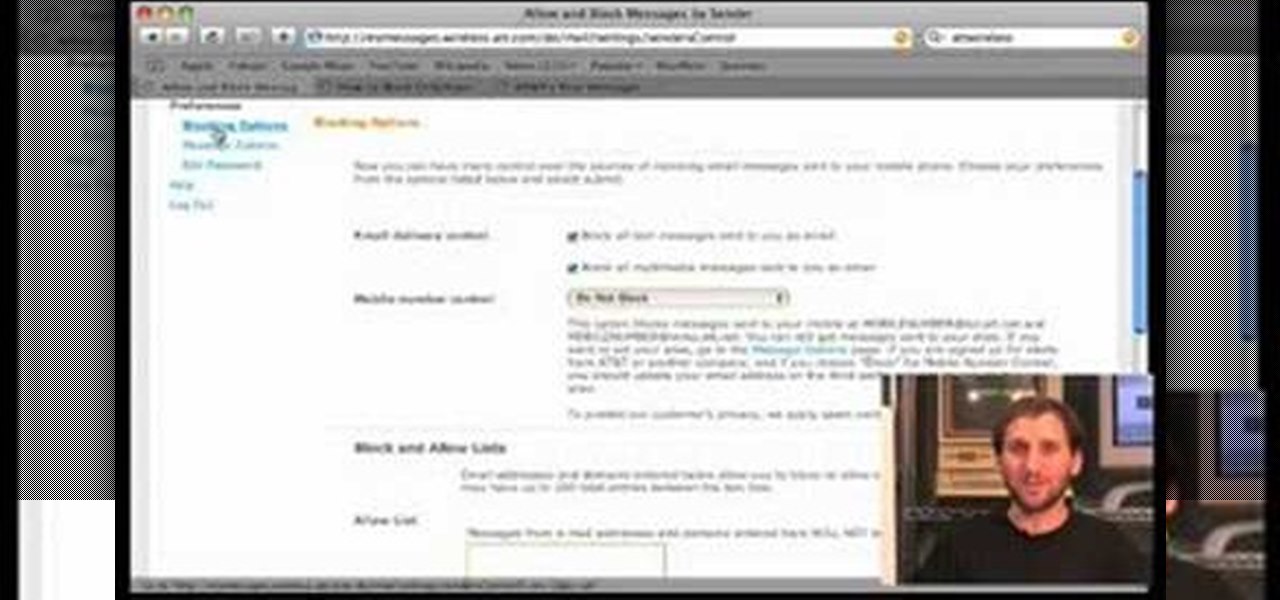
If you're among the throng of Apple iPhone users to refuse to pay $5 for a monthly SMS allowance, then each text message you receive, whether you like it or not, will run you $0.20. In this how-to, Gary Rosenzweig shows you how to prevent unwanted text messages by turning off the ability for someone to send you a text message via email. Learn also how to request that text messaging be turned off completely in this video.

In this tutorial you will learn a deceptively simple exercise that will give you more control over your bow arm. The bow is where we create most of our expressivity so more control means more ability to shape the sound of what you play. Watch this how to video and you will be able to learn proper cello bow control.

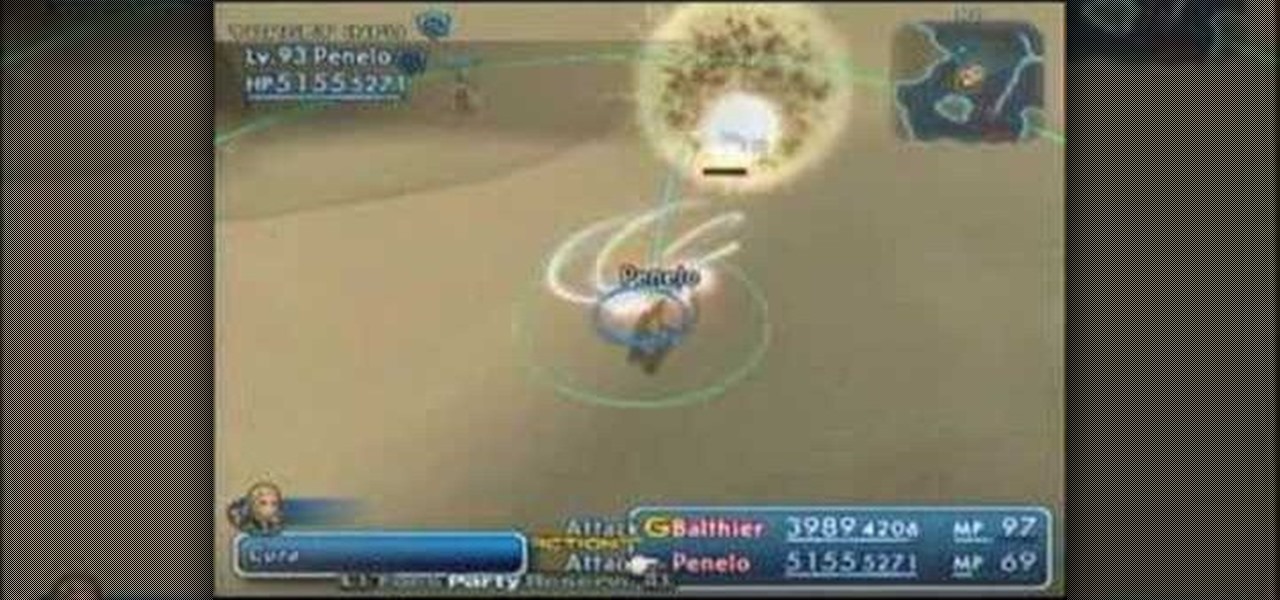
Like the previous Final Fantasy games, the latest installment Final Fantasy XII on the Playstation 2 has hidden bosses to test the mettle of hardcore RPG gamers. The Gnoma Entite is a hidden boss you can find in the Midfault area of the Damasca Wasteland following a sandstorm. Take a look at this instructional video that shows you how to take on this boss even with characters with weak equipment and abilities.

Learn how to perform David Blaine's card trick in this instructional video by a fellow magician who figured out this magic trick and breaks it down step by step. In this trick, a chosen card seems to switch places with the one on the table. All it takes is a duplicate card, and the ability to perform a double lift. Watch this video magic tutorial and learn how to perfrom David Blaine's card change trick.

This language lesson teaches you how to pay someone a compliment or thank someone in Mandarin Chinese. This how to video covers the following Mandarin Chinese phrases:

Stun run through is the ability to put the right spin and speed on the cue ball that allows you to move the cue ball between 3 and 12 inches.

Learn how to improve your swing with the help of this tee drill, and perfect your abilities and confidence on the gold course.

Learn how to employ simple plyometrics with box jumps and box runs in order to build up speed, power and athletic ability on the soccer field.

Learn how to improve your athletic abilities on the soccer field with the help of these plyometric exercises.

Learn how to improve your athletic ability on the soccer field with the help of this core workout drill.

If you know how to use After Effects, you're probably very familiar with the ability to add 3D lights to a scene, and allow them to interact with 3D layers. In 3D applications like CINEMA 4D, lights are an essential part of your project, but how do you make them look at a specific "point of interest" or object? This tutorial shows you how.

iMovie allows the average computer user the ability to quickly make movies out of your digital video footage or home movies. This is not the most professional way to color correct your footage, but it should be sufficient for the average Mac user. Follow along and see how to adjust color using iMovie.

iDVD '08 has the ability to create DVD slideshows of your photos. This is a great way to show family and friends your vacation photos or other events, without using the web. Just create your slideshow DVD and pop it in the DVD player. See how to make one in this tutorial.

Here is another magic trick to add to your collection. Learn how to break a fork seemingly with your mind. This trick requires little prep time and will make your audience believe that you have supernatural mental abilities.

The frustration of searching for the perfect image can be overwhelming. Then there's the issue of copyrights: Can you use it? Do you have to give credit? Are you allowed to manipulate the image?

Unless you're completely new to Instagram, it's likely that you've linked your account with a third-party service at some point and forgotten about it. Those services still have access to data such as your media and profile information, so it's important that you not only know how to find these "authorized" apps, but that you know how to revoke their permissions.

The ability to stay organized and be resourceful with data gathered from recon is one of the things that separates the true hackers from the script kiddies. Metasploit contains a built-in database that allows for efficient storage of information and the ability to utilize that information to better understand the target, which ultimately leads to more successful exploitation.

Whether it's for health reasons or just to look better, many of us want to get in shape. It's a long process that starts with nutrition, and dieting is never easy. Fortunately, there are some great food-tracking apps that will make it a lot easier to become a healthier version of yourself.

Overall, iOS is more impressive than ever with its stability enhancements, security tools, suite of apps and services, and intuitive user interface. With each passing update, things just get better and better for iPhone users. But don't think for a second that this is all because of Apple's genius — many of these features were at least partly inspired by tweaks made by the jailbreak community.

This week, we're beginning to see the wide ranging impacts of some of the early iterations of augmented reality hardware and software.

The photo-centric Instagram app is a great way to share "evergreen" pictures and videos when compared to Snapchat and Facebook's new Messenger Day feature. But like all social media, keeping the account secure is an essential aspect, as it restricts unwanted viewers from seeing your content and can prevent unauthorized users from accessing your account. Instagram has several methods for locking down the account including a new two-factor authentication (2FA) mechanism.

If bObsweep Pethair is behaving differently, there is a check-up test you can do from home. Perform this diagnostic test to make sure bOb is functional or find the cause of anything that challenges his cleaning ability.