Many of us were left scratching our heads when the iOS 7 update removed the Twitter and Facebook options from the Notification Center. Allowing you to quickly tweet and post Facebook updates, these were features used, and missed, by many—including me.

Ladies and gentleman, it's official—"Selfie" has been named Word of the Year by Oxford Dictionaries.

Checking notifications from all of your social media accounts is half the fun of the Internet, but can become quite tedious—hopping from site to site can take up hours of your time, especially when you're running away from something (in my case, it was always homework/studying).

Offensive pictures, depressing tweets, political statuses, and just plain old dumb comments are only a few of the reasons why people unfriend or unfollow others on social media sites. Sometimes it's just social spring cleaning, other times there's no reason at all.

Many social networks have become a part of our daily routine. Checking Facebook or sending out a Tweet are things millions of people do every single day. So, one would think that having a great app offering for Windows 8 would be a no-brainer. But, and this is a huge but, there are still no official Twitter or Facebook apps for Windows 8.

If the number of apps designed to make getting out of bed easier tells us one thing, it's that people hate waking up. Whether it's because you're dreading going to work or school, or just stayed out a little too late the night before, it's almost never fun.

As enjoyable as Facebook can be at times, it can also be a great distraction and even better deterrent of getting work done. A quick "Oh, let me check my notifications" can turn into hours and hours of Facebooking, and before you know it, you're already on your 7th Wikipedia page, all thanks to that status your friend posted. The reason I mention this is because Firefox's new 17.0 update includes many features, but the one that's been making the rounds online is the integration of Facebook Me...

I noticed the neon yellow sign at the new location of Pho Bar in Chinatown right away. The sweeping cursive yellow letters spell out "Crazy Rich Broth"; the same phrase printed on the back of servers' shirts. It's the kind of minimalist but colorful design feature that is especially popular on Instagram at the moment — shots of patrons in front of a glowing sign.

Apple revealed three new iPhone models on Wednesday, Sept. 12, at its "Gather Round" event in Cupertino, as well as announced the official release date of iOS 12, its newest mobile operating system. If you missed it and want to watch the full event, here's how to do it on your computer, smartphone, or Apple TV.

Code execution in Microsoft Word is easier than ever, thanks to recent research done by Etienne Stalmans and Saif El-Sherei. Executing code in MS Word can be complicated, in some cases requiring the use of Macros or memory corruption. Fortunately, Microsoft has a built in a feature that we can abuse to have the same effect. The best part, it does so without raising any User Account Control security warnings. Let's look at how it's done.

DownToDash, an app from an NYC-based startup, connects students to other students who want to hang out the same way they do. The social networking app has gained increasing popularity since its launch in October 2016 and looks ready to become even more available. The app was founded by Sama Jashnani and Anuja Shah, both recent students themselves.

To keep fungal pathogens at bay in their crowded homes, wood ants mix potions to create powerful protection for their nest and their young.

Greetings comrades! Great leader has ordered that we gain intel on a website owned by the opposition. For all general purposes we will be scanning nmap.org because they really don't care if Big Brother decides to perform a whois on their IP. We will be using Dmitry for the scanning.
If your company has already released some popular and addictive game and you're thinking about creation a sequel, this article is just what you need. We gathered the main tips and advices that will be useful for the building a strategy and a sequel itself. Check out the following instructions and recommendations that can lend you a hand in making a sequel for your game.

When performing something such as a mass mailer attack on a company, sending executables usually isn't the best option. That's why, in this tutorial, I'll be teaching you how to code a VBA script macro into a Word document in order to compromise a system. Combined with a little social engineering, this can be a very effective technique.

Since I first announced the new Null Byte recognition for excellence a few weeks ago, several of you have written me asking, "How can I study for this certification exam, and what material will be covered on the exam?" Now I have an answer for you. The White Hat Hacker Associate (CWA) will cover 14 domains or areas. Everything you need to know is here on Null Byte. There will be no questions that are not covered here on this site, guaranteed.
Welcome back Hackers\Newbies!

Welcome back, my nascent Hackers! In my last blog, we looked at a passive way to gather information necessary for a hack. The advantage of using passive recon is that it's totally undetectable, meaning that the target never knows you're scouting them and you leave no tracks. The disadvantage, of course, is that it's limited to only some websites and not entirely reliable.

Keith Ferrazzi teaches you how to be outgoing. Although it is difficult to talk to people you don`t know, you might miss out on opportunities if you don`t. Only by reaching out to people, you will meet them and they may get to know you enough to perhaps be of help to you in your carreer. You have to learn how to speak up. One way is to pick a role model in your social circle who is outgoing and watch how they behave and listen to what they say. Joining a Toastmasters group is also recommended...

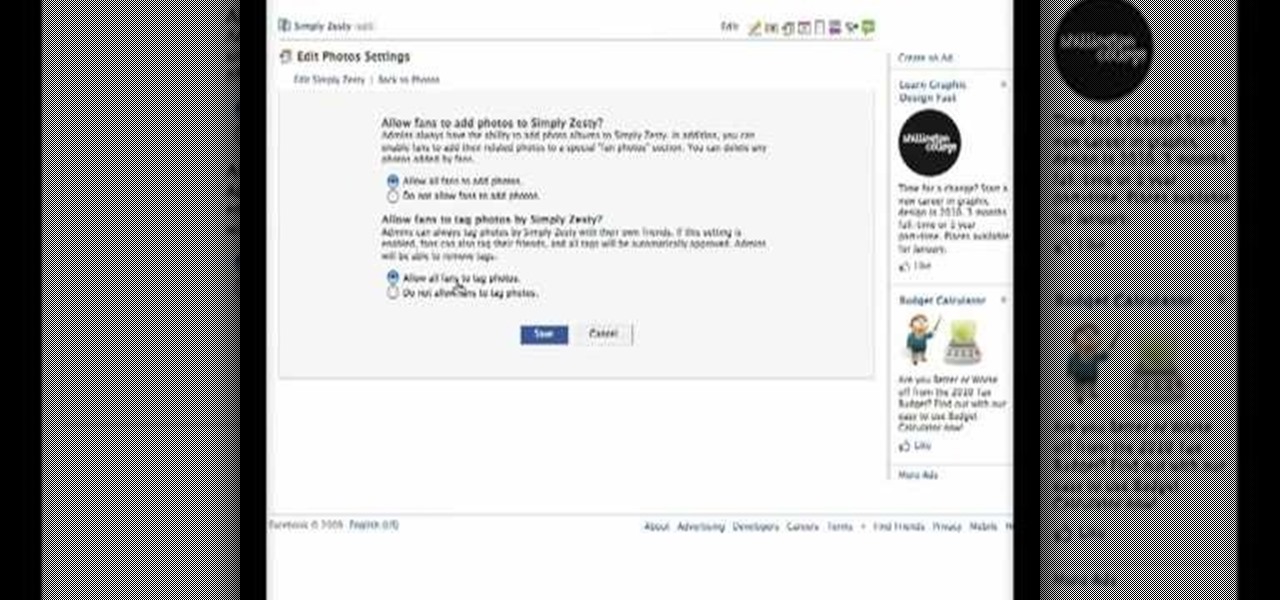
Facebook is the most popular social networking websites that can be used to stay in touch with friends and family. Using facebook you can look up your friends and even see the photos they have uploaded. You can also tag photos in the application. To do this go to your editor page and scroll down to photos. Now click edit settings inside it. At the bottom select 'Allow all fans to tag photos' option and save it. Now when you go to your home page and open the photos section you can tag them and...

In this how-to video, you will learn how to embed a social or fund raising widget on to your Facebook page. Look for static fbml on the Facebook search function. Click on it and add to page. Next, press add static fbml. Now you are finished. Go to edit page and click edit on the application. Now you can embed whichever code you need to paste into your Facebook page. Do not worry about what the code does, as you do not need to know it in order for it to work. Save the changes and go back to th...

Your mother used to remind you to wash behind your ears now make sure you keep your dog in tip top health and clean their ears too. Dogs depend a lot on their hearing but can build dirt and wax in and around their ears which can be irritating or lead to infection.

CreativeIceDesigns shows you how to make a "Polaroid"-style image on Photoshop CS3. Open a new 400 x 500 pixel image, and create a new layer, and drag underneath the original background layer. On the original "Layer 0" (the top-most layer), take the marquee tool and cut out (delete) a square, so that what you have in front of you looks like a Polaroid picture. Drag the the picture you want in, transform it into the right shape (ctrl + T) and drag it underneath "Layer 0." You can add effects (...

"Facebook is a social utility that connects people with friends and others who work, study and live around them. People use Facebook to keep up with friends, to share links, to share photos and videos of themselves and their friends, and to learn more about the people they meet." -- Facebook

Sorority Life hacks, cheats, glitches. How to hack Sorority Life. Watch this video tutorial to learn how to hack unlimited invites in Sorority Girls (08/16/09).

An American Ballroom Companion presents this social dance demonstration from the Library of Congress. Watch this demonstration traditional dance video on the Ragtime Dance: The Maxixe (1st Step). Not for beginners - this is not an instructional, step by step video. It is an authentic, professional demonstration of the Ragtime Dance: The Maxixe (1st Step). The Maxixe is an Africanized polka or two-step dance, an Afro-Brazilian styling of the polka which was brought to Brazil by European immigr...

An American Ballroom Companion presents this social dance demonstration from the Library of Congress. Watch this demonstration traditional dance video on the Ragtime Dance: The Maxixe. Not for beginners - this is not an instructional, step by step video. It is an authentic, professional demonstration of the Ragtime Dance: The Maxixe. The Maxixe is an Africanized polka or two-step dance, an Afro-Brazilian styling of the polka which was brought to Brazil by European immigrants.

An American Ballroom Companion presents this social dance demonstration from the Library of Congress. Watch this demonstration traditional dance video on the Ragtime Dance: Argentine Tango. Not for beginners - this is not an instructional, step by step video. It is an authentic, professional demonstration of the Ragtime Dance: Argentine Tango. Argentine Tango is a dance which originated in Argentina and then move to Uruguay. In the US it is known as Ballroom Tango.

An American Ballroom Companion presents this social dance demonstration from the Library of Congress. Watch this demonstration traditional dance video on the Ragtime Dance: Argentine Tango (1st figure-feet only). Not for beginners - this is not an instructional, step by step video. It is an authentic, professional demonstration of the Ragtime Dance: Argentine Tango (1st figure-feet only). Argentine Tango is a dance which originated in Argentina and then move to Uruguay. In the US it is known ...

In today's world of social media, there's really only two powerhouses—Facebook and Twitter. And those of you with Twitter accounts know the power of a Tweet. Getting more followers means reaching more people, but the vast majority of Tweeters are following only a handful of Twitterers themselves. Do you ever wonder why them? What's so special about these selected followed users? Is it worth it to follow them, too? That's up to you, but if you're searching for more people to follow, then it's ...

There's a seemingly endless list of downsides that come with the coronavirus pandemic — ranging from canceled trips abroad and sunny days spent inside to limited communication with friends and family. But one of the undeniable upsides is that there's simply never been a better time to start your own online business since most people will be working from home for the foreseeable future.

It is a scary time to be alive. As states start to ease back shelter-in-place restrictions, the new world you're entering is still unsafe. With a vaccine months away, your best bet is to follow CDC guidelines and use the tools at your disposal.

Attacks against databases have become one of the most popular and lucrative activities for hackers recently. New data breaches seem to be popping up every week, but even with all of that attention, databases continue to be a prime target. All of these attacks have to start somewhere, and we'll be exploring a variety of methods to gather information on PostgreSQL databases with Metasploit.

When you think about your Apple Watch, what comes to mind? Fitness tracking? Replying to texts? There are a lot of things Apple Watch is good for, but social media doesn't appear to be one of them based on the App Store. If that's your perception, however, it's time for a reality check because you can start browsing Twitter and Reddit on your Apple Watch right now.

Google Calendar is a cornerstone of the Google Suite, perhaps second only to Gmail itself. Whereas email is constantly plagued by phishing attacks, as of yet, the calendar is a relatively untapped social engineering attack vector. But it's relatively easy for an attacker to inject a meeting or event into a target's Google Calendar and use it to exploit them.

Modern "mad men" are buying into augmented reality for marketing, with the two latest examples being trendy burger maker Bareburger and department store chain Zara.

Considered by many (perhaps unfairly) to be a very public failure, Google Glass can add another plot point to its comeback story, this time as a tool to teach social skills to children and adults with autism.

After exploiting a vulnerable target, scooping up a victim's credentials is a high priority for hackers, since most people reuse passwords. Those credentials can get hackers deeper into a network or other accounts, but digging through the system by hand to find them is difficult. A missed stored password could mean missing a big opportunity. But the process can largely be automated with LaZagne.

The Chinese government's tight restrictions on gathering data by foreign firms for 3D mapping, the lifeblood of machine-taught driverless systems, could at least slow down access to the market by Waymo, Tesla, General Motors (GM), Ford, and other players hoping to make inroads there.

Google, the company that rules the internet, is now testing a method to leverage its machine learning with its ubiquitous presence on mobile devices. The new model they're employing is called Federated Learning, and it hopes to apply artificial intelligence to Google's services on Android without compromising user privacy.