Whether it's for handling your business's social media account or just for personal reasons, like trolling an ex-girlfriend's page (not that I've ever done that) or posting on behalf of your pup, there are instances where having two different Facebook accounts on one device is simply easier than switching back and forth.
Technology allows us to communicate with others like never before, providing us with the ability to stay connected with past and current coworkers, classmates from high school, and even relatives in far-away countries.

If there was anything missing from the notorious YO app, it was Aaron Paul's character from Breaking Bad, Jesse Pinkman, calling me by his signature catch phrase—you know the one.
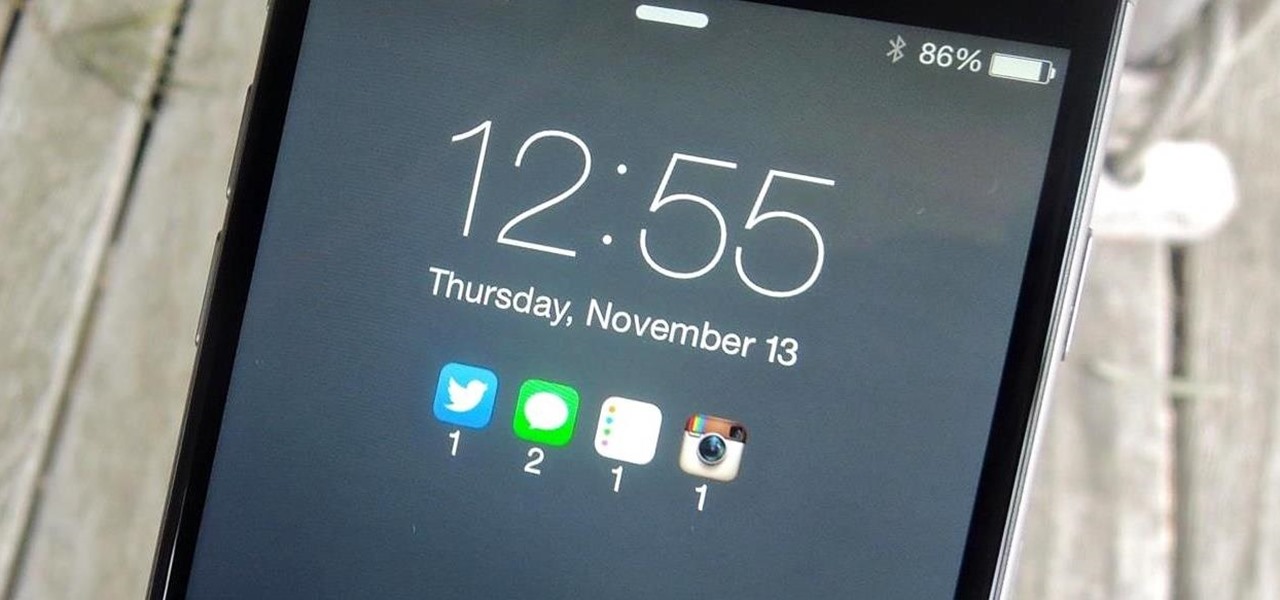
Lock screen notifications can sometimes be overwhelming and difficult to manage, especially in the morning when I receive a massive influx of emails, texts, reminders, and social media alerts. At some point it's not even worth scrolling through all of them on your lock screen when you can get a better grasp of everything by just checking out the Notification Center instead.

Aside from the most basic functions, most of us are pretty useless when it comes to Photoshop. Yes, we can all add filters, but who wants to see everything in black-and-white or sepia? Why not change a sunflower blue, your hair pink, or your lips purple—without having to spend hours with editing software.

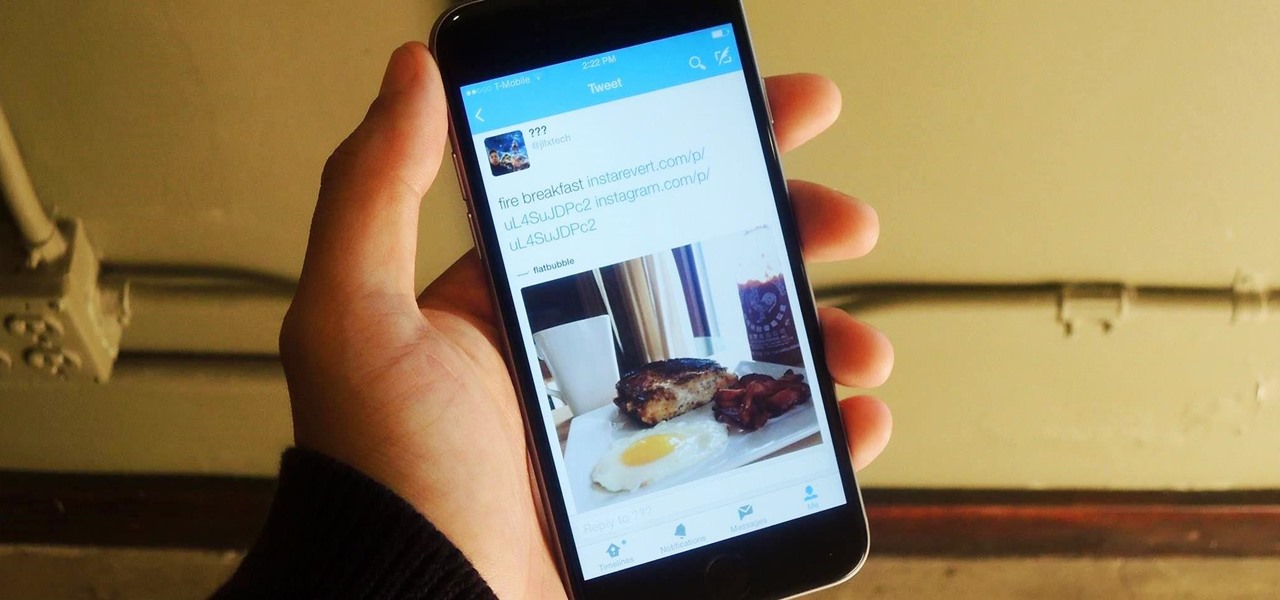
Twitter found a sweet spot with its 160-character limit, but Snapchat sports a social media low of 31 characters, forcing us to condense our ideas into a few short words when typing in picture captions because of their ephemeral nature. While this severely limited amount of words is Snapchat etiquette, I've got so much more to say than 31 characters!

This is how I made my smartphone camera stand using everyday items laying around in my garage. This is also a great rainy day project for anyone who uses a smartphone for their youtube or social media videos. It cost me almost nothing to build since I already had most of the items. This is a great project for anyone looking to start out on since it is really simple. It literally took me only 10 minutes to build.

Air New Zealand is looking for a spokesperson for the Antarctica: No Ordinary Place, No Ordinary Assignment project, a two-week adventure in Antarctica, where the chosen candidate will join National Geographic photographer Jason Edwards to document environmental issues and important research being conducted by research teams sponsored by Air New Zealand and Antarctica New Zealand.

With more people joining the internet scene each day it's important that it's security is.. well it has to be good. Of course everything can be hacked and that's the way hackers work. They know there IS a vulnerability but they don't don't know the rest. in this article i'll try to explain the big difference between HTTP and HTTPS

We've all had that awful, sinking feeling when something you've been typing away at is suddenly gone. Maybe you accidentally hit the Back button, lost your internet connection, or your computer crashed, but whatever the reason, losing your work totally sucks. A lot of word processing programs have a built-in auto-save feature to prevent you from losing everything, but most websites and blogs haven't gotten there yet. An extension for Chrome and Firefox called Lazarus: Form Recovery can help y...

Who doesn't hate Auto Correct? There's nothing worse than hitting 'Send' only to realize that your phone betrayed you by changing a word so that your message doesn't even mean the same thing anymore—especially when it's going to someone like your boss or parents.

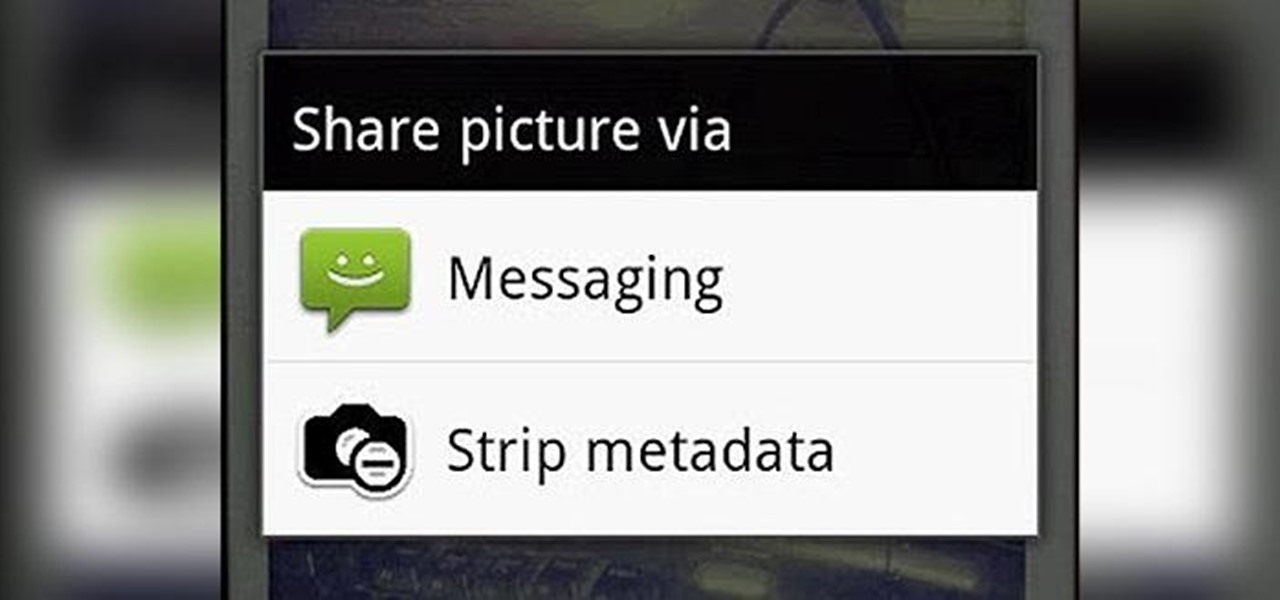
We've talked before about EXIF data—or metadata—attached to photos and how it can expose information about your location, what type of device you're using, and even the device or camera's unique identification number.

I can certainly say that I don't like be ignored, and you're probably right there with me on that. Also, if you're like me, you don't like being blocked on an instant messenger, either. There's something about being shafted like that that can really cramp your style.

Many social networks have become a part of our daily routine. Checking Facebook or sending out a Tweet are things millions of people do every single day. So, one would think that having a great app offering for Windows 8 would be a no-brainer. But, and this is a huge but, there are still no official Twitter or Facebook apps for Windows 8.

If the number of apps designed to make getting out of bed easier tells us one thing, it's that people hate waking up. Whether it's because you're dreading going to work or school, or just stayed out a little too late the night before, it's almost never fun.

Apps are now very much integrated with social media, especially with your Facebook profile. Pretty much every app these days lets you log in using Facebook, while some actually force you to, giving you no other option. But, the most annoying part is that these apps leave notifications all over your Facebook timeline, cluttering the hell out of it. So, how can you completely banish all of these apps from being able to access your Facebook?

So you've learned all of the dance moves to Gangnam Style and made your very own papercraft version of PSY that dances whenever you want him to. Now it's time to take your obsession a step further—by making yourself the star of the Gangnam Style music video. JibJab, the custom e-card site, has created a free tool that lets you use any photo to replace PSY's face with yours (or whoever you choose), then share the video with your friends.

As enjoyable as Facebook can be at times, it can also be a great distraction and even better deterrent of getting work done. A quick "Oh, let me check my notifications" can turn into hours and hours of Facebooking, and before you know it, you're already on your 7th Wikipedia page, all thanks to that status your friend posted. The reason I mention this is because Firefox's new 17.0 update includes many features, but the one that's been making the rounds online is the integration of Facebook Me...

With the Samsung Galaxy S III being a hot commodity, it's no surprise that your friends might try unlocking your fancy password-protected phone. While some friends have good intentions when using your phone, there are those certain friends who get into the phone to do this... The worst scenario might be that you leave the phone around a group of friends, come back and find that all of your social media accounts have been hacked. When you yell out to your friends asking who did it, no one make...

Ever been halfway to work or school and suddenly remembered you forgot to log off your computer? A lot of people are constantly logged in to email and social media accounts, so if you have a mischievous roommate or sibling, this situation could be disastrous. That's where TweetMyPC comes in—it's a free Windows application that lets you send commands to your computer just by tweeting. Image by Twittermania

Mike Agerbo explains the benefits from listening to one's music through AppleTV, however it seems that one cannot listen to any music or other audio files unless he/she is using iTunes media. Agerbo explains how you can use Apple TV with other types of media, using a program called ATV Flash. Agerbo believes ATV Flash to be an easy and inexpensive tool to upgrade one's Apple Television so it can use the USB port and download and use other media content. One can also create a Boxee account to ...

Here's a fast lesson in hosting video on your own Drupal website using the FileField and jQuery Media modules. The Filefield and jQuery Media modules are a one-two knock out combination for allowing users to upload media files to fields in your custom content types and then playing back the media files in their matching player or handler. It represents a positive direction for treating fields containing files and is a great starting point for researching your own implementation of this recipe.

Is you media center in chaos? Watch this video tutorial by Better TV for ten tips on how to organize and down-size your media center.

Before you do any shooting on the Red One Camera, you must set up your project settings and format your media with the settings you plan on shooting with. 2K, 3K, or 4K and your FPS must be set or face bad consequences when you go to edit this footage.

People use browsers for all types of things, and in general, we trust a lot of personal information to them. That's why browsers are a perfect attack surface for a hacker, because the target may not even know they are infected and feed you all of the information you could want.

In a way, Twitter is the town square of our era, where people can share and discuss ideas on a wide variety of topics. While the tech giant has its own app for Android, it's pretty bare-bones when it comes to features. This has paved the way for third-party clients that are rich with customization options.

Riding the coattails of one of the biggest movies this year, the first edition of the new Moviebill augmented reality magazine will be available at Regal Cinema theaters nationwide this weekend alongside the release Avengers: Infinity War.

Augmented reality device maker Vuzix has filed a defamation lawsuit asking for $80 million in punitive damages, money damages, and interest against a short seller who has publicly claimed that the Amazon Alexa functionality of the company's Blade smartglasses is fraudulent.

A recent update to Facebook's News Feed could significantly broaden its reach when it comes to delivering augmented reality content.

After devoting a number of resources toward developing VR content to modernize the delivery of its news content in recent years, The New York Times is expanding its capabilities to include augmented reality as well, a mission outlined in a manifesto published on Thursday.

This week, Samsung officially kicked off the Oreo Beta Program for the Galaxy S8 and S8+ in North America and several other markets. The full list of changes is quite substantial, so we'll be running through them in a series of posts detailing what's new. First up, the Galaxy phones inherit notification channels from Android 8.0.

Code execution in Microsoft Word is easier than ever, thanks to recent research done by Etienne Stalmans and Saif El-Sherei. Executing code in MS Word can be complicated, in some cases requiring the use of Macros or memory corruption. Fortunately, Microsoft has a built in a feature that we can abuse to have the same effect. The best part, it does so without raising any User Account Control security warnings. Let's look at how it's done.

A Jedi does not seek adventure or excitement, but Star Wars fans can seek Jedi with the Find the Force augmented reality scavenger hunt promoting the launch of merchandise for Star Wars: The Last Jedi.

DownToDash, an app from an NYC-based startup, connects students to other students who want to hang out the same way they do. The social networking app has gained increasing popularity since its launch in October 2016 and looks ready to become even more available. The app was founded by Sama Jashnani and Anuja Shah, both recent students themselves.

Say goodbye to boring video chats over Messenger. Now the app is rolling out new features that can make any chat interesting and fun.

If imitation truly is the sincerest form of flattery, then Snapchat must be blushing profusely as Instagram continues to shamelessly copy its features and dig into its wallet. Instagram has also managed to copy some of the security aspects — or lack thereof — of one of Snapchat's hottest characteristics.

With tools such as Reaver becoming less viable options for pen-testers as ISPs replace vulnerable routers, there become fewer certainties about which tools will work against a particular target. If you don't have time to crack the WPA password or it's unusually strong, it can be hard to figure out your next step. Luckily, nearly all systems have one common vulnerability you can count on — users!

When performing something such as a mass mailer attack on a company, sending executables usually isn't the best option. That's why, in this tutorial, I'll be teaching you how to code a VBA script macro into a Word document in order to compromise a system. Combined with a little social engineering, this can be a very effective technique.

Since I first announced the new Null Byte recognition for excellence a few weeks ago, several of you have written me asking, "How can I study for this certification exam, and what material will be covered on the exam?" Now I have an answer for you. The White Hat Hacker Associate (CWA) will cover 14 domains or areas. Everything you need to know is here on Null Byte. There will be no questions that are not covered here on this site, guaranteed.

In late 2012, Instagram CEO Kevin Systrom made a sudden and controversial change to his social media service when he removed Twitter Card support.