On Wednesday, the tech world woke up to fairly shocking news with the announcement that AT&T would be the exclusive wireless carrier for the forthcoming Magic Leap One, as well as an investor in Magic Leap.

A new study published by American University demonstrates how Pokémon GO and other augmented reality games can help city governments bring communities closer together.

In its latest feature with an assist from augmented reality in storytelling, the New York Times shows readers the virtual crime scene it constructed to prove that the Syrian military conducted chemical warfare against its citizens.

Usually, the camera adds 10 pounds, but with a new augmented reality effect in Like's mobile app, the camera can actually make you look slimmer.
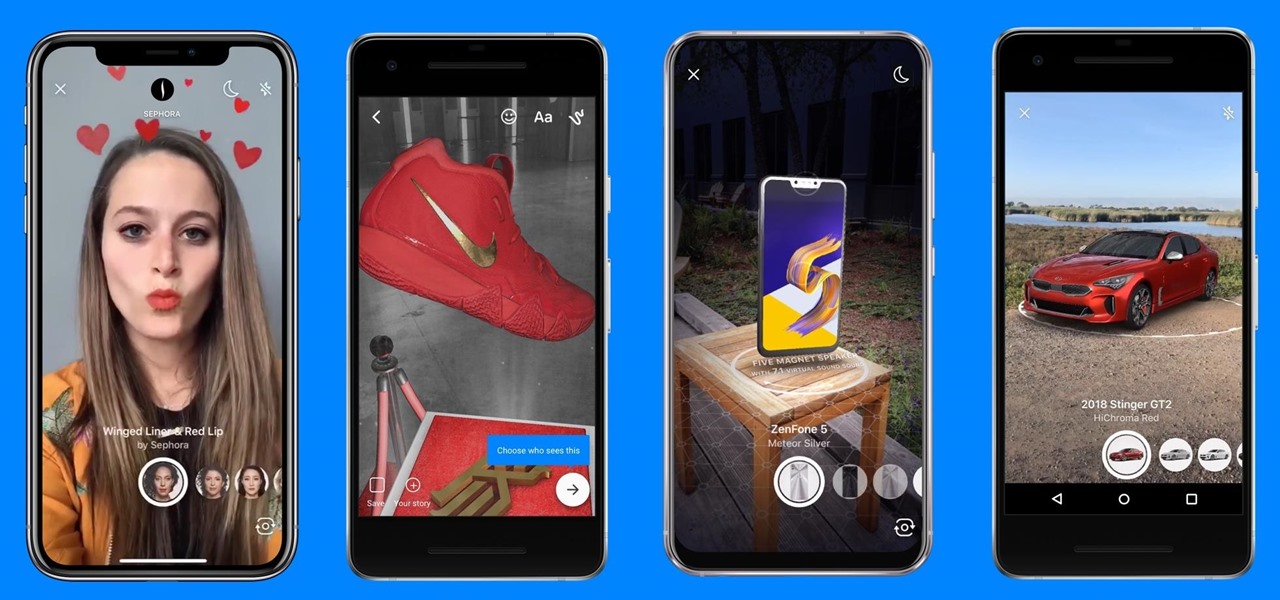
On Tuesday, on the one-year anniversary of the announcement of its AR Camera platform, Facebook founder and CEO Mark Zuckerburg revealed at the company's F8 developers conference that the platform will be extended to the company's Instagram and Messenger apps.

Taking photos that are actually printed and hung on a real wall, versus being shot and shared via a social wall, is a seemingly lost art, but PhotoBloom AR wants to change that with augmented reality.

What's black and white, sounds like actress Kristen Bell, and is standing in your living room talking to your kids right now? Don't worry, that's just Genius the Panda, an augmented reality character from the Yakables app for iPhones and iPads.

With the Google Maps API giving entertainment brands the means to build their own location-based AR games, Niantic is raising the bar for the genre with new updates to Pokémon GO.

What many thought was inevitable, based on recent hints, has been revealed to be in the planning stages: Snapchat is working on smartglasses. The surprising information came out on March 2 in a report that also claims Snap Inc. is planning to release version two of its Spectacles product in the third quarter of 2018.

Soon, Pokémon GO allies attacking a raid boss at a gym will be able to do so together in augmented reality.

Proxies can be quicker to use than a VPN for specific applications, like web browsers or torrent clients. Both services will hide your true IP address, but a VPN is slowed down because it encrypts all data through a VPN network, while a proxy just acts as a middleman for fetching and returning requests from a server on your behalf. When speed is needed, go proxy.

Exotic sports cars are the province of the ridiculously wealthy but, thanks to augmented reality, you can now get closer than ever to a Bugatti Chiron.

The next frontier for AR hardware is the consumer headset, and tech companies of varying size and tenure are working hard to strike the right mix between comfort, cool factor, and cost. How these companies handle the hype and flow of information vary wildly.

Lowe's Home Improvement has been an early adopter of augmented and virtual reality in their business practices, so it was a bit of surprise that their name was absent from the ranks of companies launching ARKit apps last week.

In most cases, when you create a movie project in iMovie for iPhone, you're starting with just a few media clips. There's no reason to select every photo or video at once, and that's likely a hard task anyway. Adding additional media footage to your movie project couldn't be any easier, especially when it comes to photos.

More prescriptions for antibiotics are written for ear infections than any other type of infection. A new study comparing the incidence and causes of ear infections in children between the ages of six months and three years found that the incidence of ear infections over the last decade has dropped significantly since the 1980s.

Drones are a fairly new craze to hit the nation. While they are accessible to the general population, good drones still typically cost a ton of money and despite all the fun they are, it's sometimes not worth it to actually buy one. If you're one of those people who would love to play around with drones — but don't want to have to buy one — Arcane Reality is developing the app for you thanks to Apple's ARKit.

How can something get more free than free? Well, in the case of Twitter, Virgin Mobile found a way with its newest promotion. If you have a 4G plan with Virgin Mobile, you can now access Twitter from your smartphone without it counting towards your monthly data allowance.

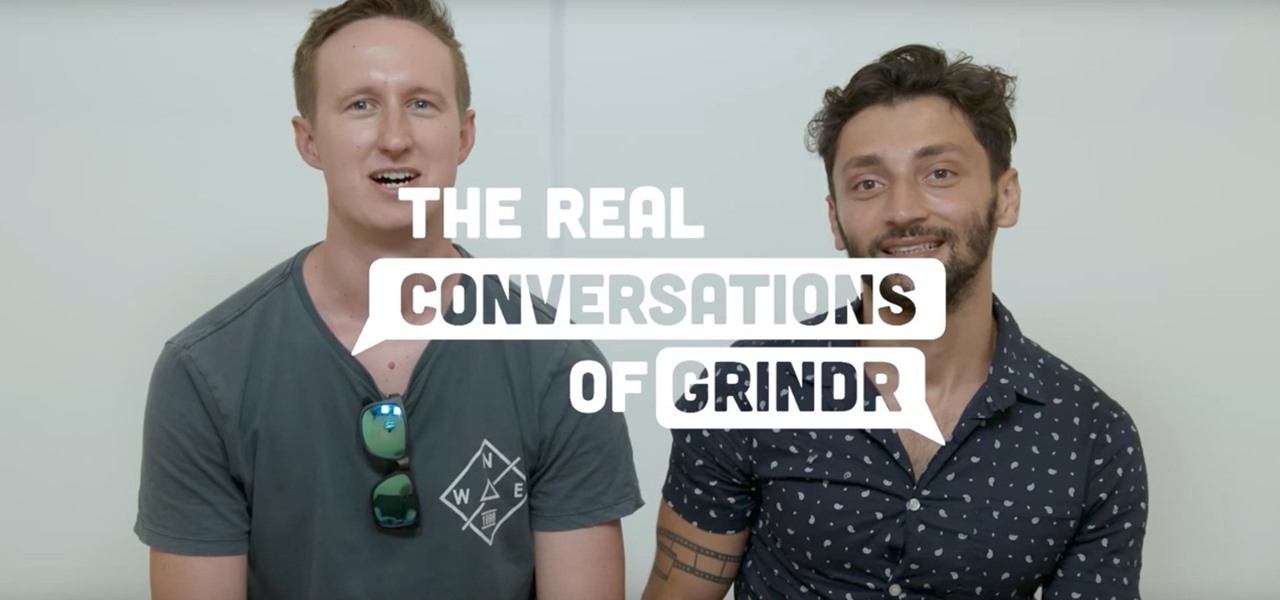
With significant advancements in the treatment and prevention of HIV, you'd think the stigma surrounding the deadly virus and AIDS, the syndrome the infection causes in the body, would have lessened. Unfortunately, a new project looking at conversations on Grindr — a social networking app for gay, bi, curious, and queer men — has shown that this stigma is very much present.

There's a general belief that augmented and mixed reality is going tied to enterprise solutions for the foreseeable future, and most developers in the field are focused on business use-cases. Without a dramatic breakthrough in the next couple of years that will likely be the case, making that decision the sensible one.

So, according to Sprout Social, mentioning an Instagram handle in the caption of your posts increases audience engagement by up to 56 percent. If true, that's pretty impressive.

According to a source at TechCrunch, a new version of Snap's 'Spectacles' could include augmented reality.

Delphi Automotive PLC has announced it is partnering with Transdev Group to develop on-demand driverless transportation systems, a deal that shows promise for autonomous development on a global scale.

Snapchat is attempting to take over the world via augmented reality technology. Well, it's more of a virtual makeover than a takeover, but still ...

When building anything of a social nature, be it a local roller derby or softball team, a club dance night for chiptune, or building new technology markets, the community around those ideas are an important factor in helping these things not only come into existence but to grow into something that enlightens everyone involved. The community around an idea can actually make or break these new ventures — and this applies to augmented and mixed reality as well.

One thing you don't see often in the driverless industry are partnerships. When automakers are in the news together, it usually means drama. However, an important partnership between Nissan and Mobileye was announced today. One that has the potential to make driverless cars on the road better and safer.

Apple staff will be put through their paces now that the company's "Automated System" for driverless cars is in motion.

Snap Inc. is no stranger to augmented reality. In fact, AR has been the Snapchat app's most popular feature, as face filters continue to update and change the way we communicate with each other. But in a new move, Snap Inc. is showing its commitment to improving AR and its real-world integration with its updated world lenses.

To keep fungal pathogens at bay in their crowded homes, wood ants mix potions to create powerful protection for their nest and their young.

As Alfred monologued in The Dark Knight, "Some men aren't looking for anything logical, like money. They can't be bought, bullied, reasoned, or negotiated with. Some men just want to watch the world burn."

If you follow tech, you're probably familiar with Siri, Apple's personal voice assistant, which has been integrated heavily into iOS ever since iOS 5. But you might not have known that Siri is capable of performing some tasks when the iPhone is in a locked state. The default state of iOS is to allow access to Siri from the lock screen, most likely for the convenience of hands-free access to the phone.

Snapchat has already found a compelling way to create advertisements in augmented reality with their branded filters, but they continue to experiment with new ways to monetize the bridging of the real and digital worlds. Their latest idea, which requires users to "snap" an image to unlock content, could succeed where QR codes haven't.

You might not think a mixed reality headset could help kids eat their vegetables, but that's the exact premise behind Habit.at—the app that won the "Social Good" category at the 2016 HoloHacks competition in Los Angeles.

If you have any group chats going, you're surely familiar with this scenario: One person sends a picture, then, within 30 seconds or so, all other participants chime in with one-word responses like "Cute," or "Awesome." It's a social nicety, so you have to expect this behavior, but that doesn't make it any less annoying when your phone randomly beeps and vibrates ten times in a row because of it.

Apple is planning to completely overhaul its Apple Music streaming service this summer, and is expected to unveil the changes at its Worldwide Developers Conference in June, according to reports from Bloomberg and 9to5Mac.

Nintendo rolls out its first smartphone-specific game in the U.S. on March 21st, and the main protagonist is... you. Well, your Mii, and it's not a game, but a social app.

Facebook's Messenger apps for Android and iOS make it easy to navigate between conversations, helps you keep in touch with your friends or heckle your enemies, and even lets you tag yourself or others in the conversation with hilarious nicknames to keep things interesting.

In this article I will show you how to obtain victim's credentials without cracking any hashes. There are a couple of ways to perform this task (for example dumping the SAM file and cracking the NTLM hashes), but here I will explain how to do it using PowerShell and a bit of social engineering. We are going to create a fake login popup.

In this video, I'm gonna show you how to fold a paper jet fighter call F-18 Hornet. This model is designed by Thay Yang.