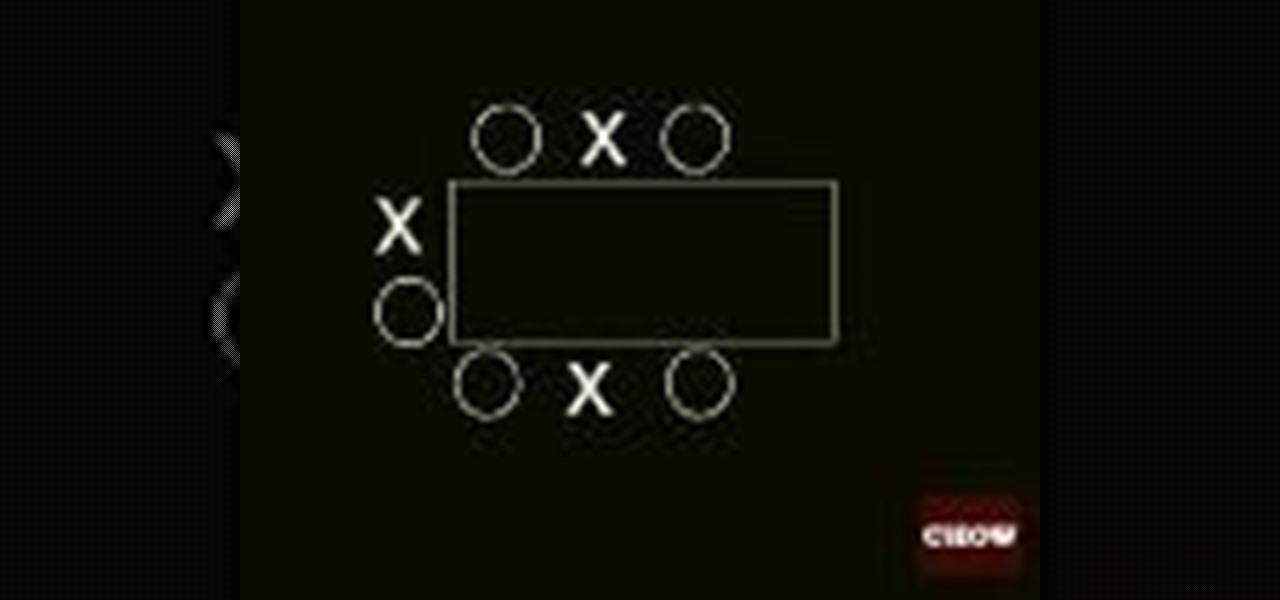
How To: Seat your dinner guests
Seating people willy-nilly may work for prison cafeterias and campus dining halls, but when it comes to guests at your dinner party, put some thought into it. Follow these rules for optimal social interaction.


Seating people willy-nilly may work for prison cafeterias and campus dining halls, but when it comes to guests at your dinner party, put some thought into it. Follow these rules for optimal social interaction.

As many as 6 in every 1,000 children have at least one Autism Spectrum Disorder. People with ASDs tend to have problems with social and communication skills, and have unusual ways of learning and reacting to different sensations. It is important to note that Autism is not just one disorder, but a series of disorders. Learn how to tell if your child is showing symptoms of Autism with this tutorial video.

Whatever it is you're into, Facebook Groups are a great way to connect with others that share your interests. And beyond matching you up with like-minded people, Groups also give you access to deals on items, help you organize play dates with families in the same area, and so much more.

Most of today's mobile augmented reality apps focus on individual experiences, but a new entrant into the space wants to make things a bit more social.

Because it takes two to tango, your dancing Bitmoji World Lens on Snapchat is getting a dance partner.

Augmented reality has given companies worldwide great powers for innovating business practices and engaging customers, but on Monday, Honda demonstrated that with great power, also comes great social responsibility.

Lately, any subject in the realm of politics is a figurative powderkeg primed to explode on the nearest social media channel. Now, one app wants to use your iPhone and AR to strike a match.

On Wednesday, Snap, Inc. unveiled a revamp of its Snapchat app that draws a hard line between content from your friends and content from professional media organizations.

DownToDash, an app from an NYC-based startup, connects students to other students who want to hang out the same way they do. The social networking app has gained increasing popularity since its launch in October 2016 and looks ready to become even more available. The app was founded by Sama Jashnani and Anuja Shah, both recent students themselves.

Microsoft, even being Apple's fierce competitor, is no stranger to producing iOS apps—in fact, they've made 94 of them. But their latest iOS app may be their silliest yet: a goofy photo editor named Sprinkles.
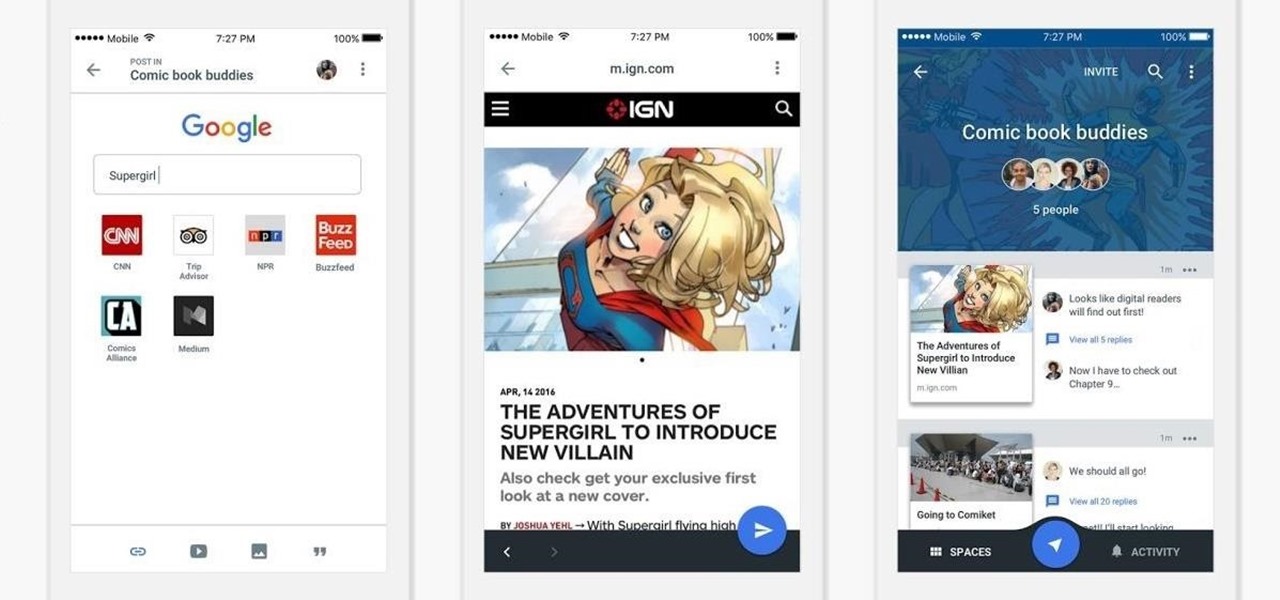
Google is launching a new app called Spaces that lets you share things from the web with small groups of people. The aim of Spaces appears to be granting you a forum with like-minded people to help cut down on off-topic comments that can steer a conversation off the rails. Spaces comes with Google Search, Chrome, and YouTube built in, so you won't need to switch apps to go hunting for interesting content to share. You can invite people to your groups—or "spaces" as they're called in the app—b...

When performing something such as a mass mailer attack on a company, sending executables usually isn't the best option. That's why, in this tutorial, I'll be teaching you how to code a VBA script macro into a Word document in order to compromise a system. Combined with a little social engineering, this can be a very effective technique.
Serving as the primary tool of distribution for many websites, social media is how most of us catch up what's going on around the world. While there is a bunch of clickbait going around on Facebook and Twitter, there are plenty of genuinely interesting articles being shared.

Unless you're a business executive or movie star, most of us aren't afforded the luxury of having a personal assistant. Wouldn't it be nice to wake up in the morning and just have everything taken care of?
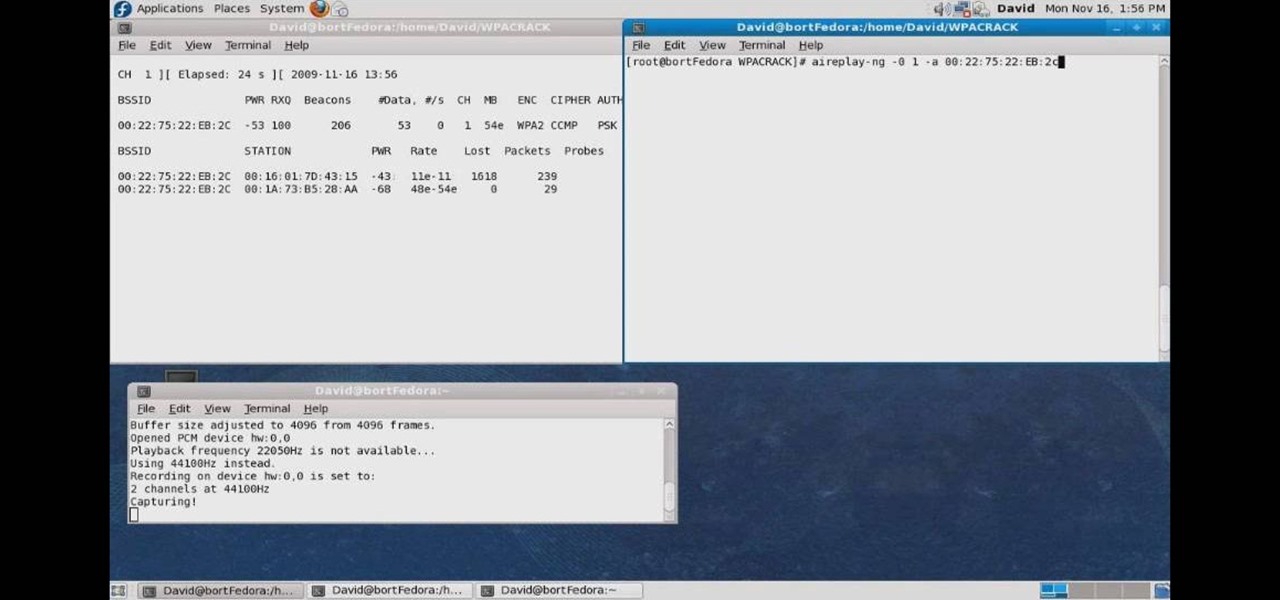
In this how to video, you will learn how to crack a WPA encrypted wireless network. To do this, you will need the Air Crack package for Linux. First, disable the wireless adapter and enable monitor mode. Next, identify the channel in the wireless network and Mac address. Once you have this, you can listen to the traffic coming to and from this point. Wait for the handshake or disconnect something in order to force it to reconnect. From here, you are ready to perform the attack. With any encry...
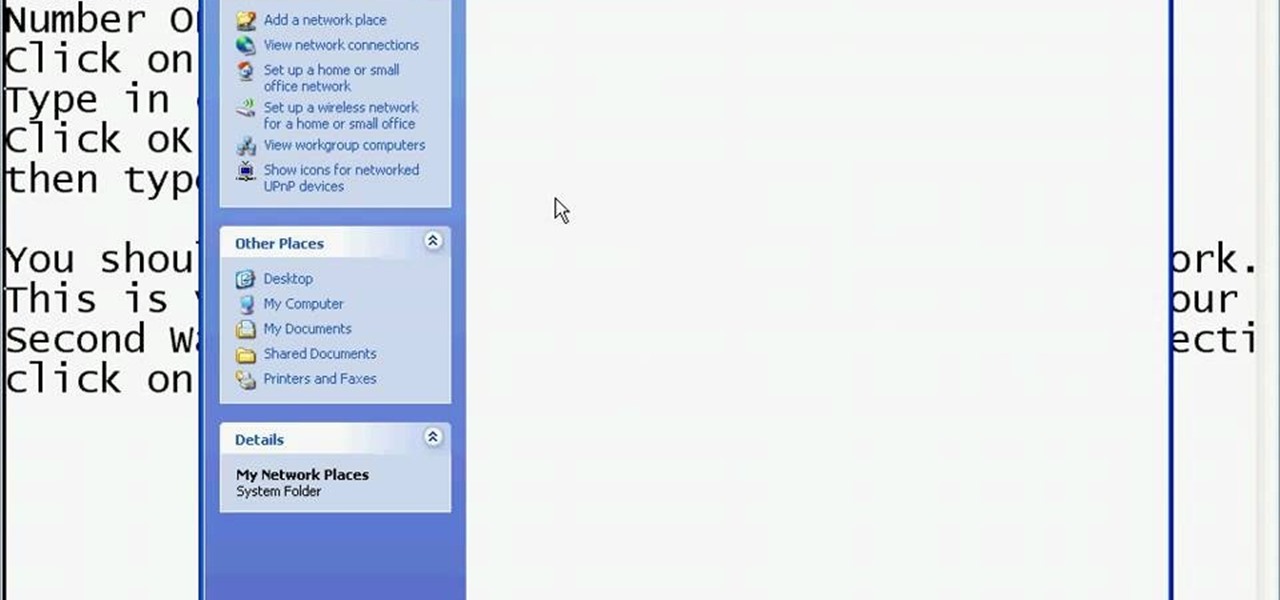
This video shows you the method to find if someone else is using your Internet connection. There are two methods for this. The first method involves opening the start menu and click on 'Run'. Type cmd in the text box which opens as a result of clicking on 'Run'. Type NET VIEW at the command prompt. This will show all people using your network. The second method involves going to Start menu. Go to Connect to and Show all connections. Click on My network places. Click on 'View workgroup compute...

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to map networks with Spiceworks.
Nmap ("Network Mapper") is a free and open source (license) utility for network exploration or security auditing. Many systems and network administrators also find it useful for tasks such as network inventory, managing service upgrade schedules, and monitoring host or service uptime. Nmap uses raw IP packets in novel ways to determine what hosts are available on the network, what services (application name and version) those hosts are offering, what operating systems (and OS versions) they a...

This video will show you how to subnet using CIDR notation. If you're curious about how to determine networks, subnet masks, broadcast addresses and what makes a host range valid. A great video for anyone currently studying computer networking technology.
This video will teach you how to hack a WEP wifi network on a Mac. You'll need to follow the link, grab the prog and follow the steps. It's not too hard, so give it a try. Remember, stealing is illegal!

Want to see whether your PC is being accessed by hackers? Netstat (network statistics) is a command-line tool that displays network connections (both incoming and outgoing), routing tables, and a number of network interface statistics. It is available on Unix, Unix-like, and Windows NT-based operating systems. This video tutorial presents a basic introduction to working with the netstat tool. Determine whether you've been hacked with this how-to.

Anyone can set up their own wireless network. All you need is a little know-how. You will need a computer with wireless capability, a high-speed modem, a wireless router, and a broadband internet connection. Don't get tied to the wall; a wireless connection will allow you to move the computer freely around your home and still get an internet connection. Watch this video tutorial and learn how to hook up a wireless network at home.

Tekzilla shows you how to troubleshoot network woes with ping and traceroute.
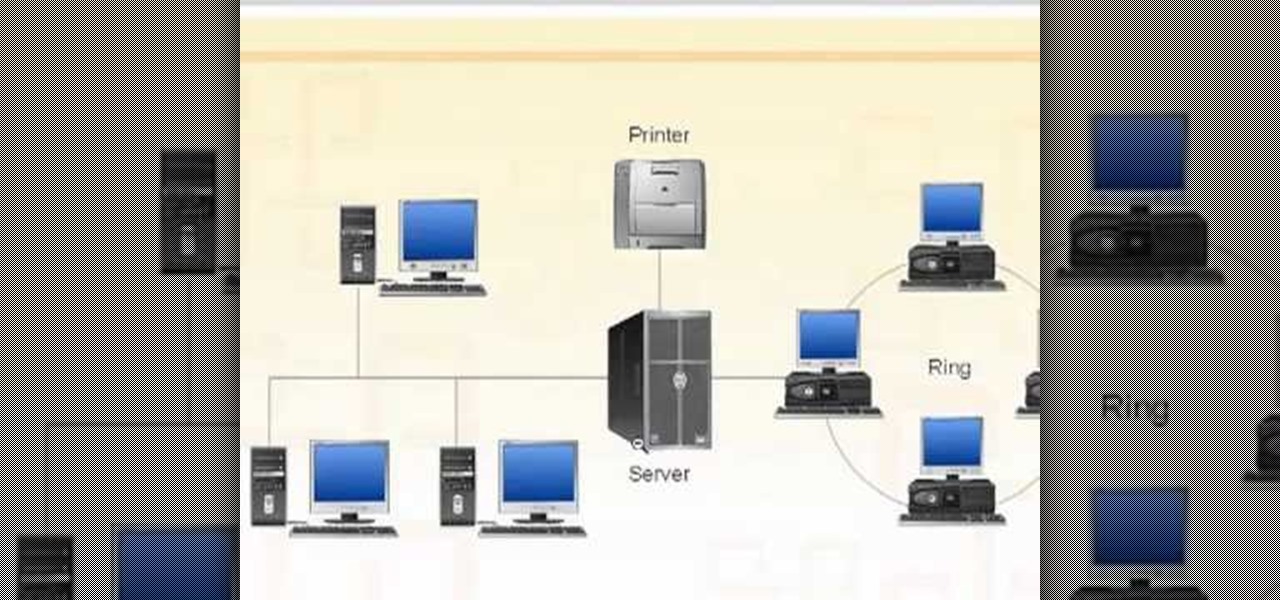
Need some help figuring out the ins and outs of LAN networks? They're easy enough to understand. And this brief video tutorial from the folks at Butterscotch will teach you everything you need to know. For more information, and to learn more about LAN networks yourself, watch this helpful video guide.
Meez is the social entertainment leader combining avatars, web games and virtual worlds. Get help with all of your Meez avatar needs with these Meez tips and tricks! Watch this video tutorial to learn how to remove the head off your Meez avatar.

The first of a two part series on setting up your linux server and network for external access through your cable modem or DSL. Covers modifying the Linux servers network setting to a static IP address.

MIT artificial intelligence researcher Lex Fridman recently asked SpaceX and Tesla founder Elon Musk possibly the best question he's ever been asked: What would he ask a hypothetical AGI system (an AI system with human-level intelligence and understanding) if he only had one question?

Augmented reality seems to come into its own in museums, where audiences are ready and willing to try out new immersive tech. Now, that tech-powered palette is about to get a little larger.

There's nothing wrong with indulging in guilty pleasures on Spotify every once in a while — we all need a little Coldplay and Creed in our lives. The only problem is, all of your friends and family might be watching. Anyone that is following your Spotify account can potentially see what you're listening to, but there are several ways to hide this shameful and embarrassing activity from the world.

Microsoft.com is one of the most extensive domains on the internet with thousands of registered subdomains. Windows 10 will ping these subdomains hundreds of times an hour, making it challenging to firewall and monitor all of the requests made by the operating system. An attacker can use these subdomains to serve payloads to evade network firewalls.

If you find yourself with a roommate hogging limited data bandwidth with video games or discover a neighbor has invited themselves into your Wi-Fi network, you can easily take back control of your internet access. Evil Limiter does this by letting you control the bit rate of any device on the same network as you, allowing you to slow or even stop data transfer speeds for them completely.

While AT&T is gradually showing off the powers of its 5G technology in the US via the Magic Leap One, another major wireless company is doing the same in the UK using the world of fashion.

While Wi-Fi networks can be set up by smart IT people, that doesn't mean the users of the system are similarly tech-savvy. We'll demonstrate how an evil twin attack can steal Wi-Fi passwords by kicking a user off their trusted network while creating a nearly identical fake one. This forces the victim to connect to the fake network and supply the Wi-Fi password to regain internet access.

With its recent acquisition of 3D gaming engine PlayCanvas, Snapchat parent Snap, Inc. appears to be preparing a challenge to the existing players in the world of game development, particularly in terms of augmented and virtual reality gaming.

Now that we have our payload hosted on our VPS, as well as Metasploit installed, we can begin developing the webpage which will trick our "John Smith" target into opening our malicious file. Once he has, we can take over his computer.

One of the more meme-able characters from the animated series Rick & Morty will be able to beckon iPhone owners to "show them me what you got" thanks to ARKit.

More video content is making its way to Facebook as the social network relentlessly tries to get its video platform up to par with YouTube. Now, they seem to be making more of an effort to improve their video tab, as new features have started to appear on some Android phones.

You might notice that there's been a few changes around here. All of us here at WonderHowTo have been working hard to create fun new spaces and topic areas to dig our heels into. We've created a few brand new websites, spiffied up our design, and today we're launching the WonderHowTo network.

before I move on to more exciting areas in this series, I want to also point out some things to protect your information & how to not get DoXed.

If a tree falls in the woods and nobody is there to hear it, does it make a sound? If a person makes calls but doesn't have a Facebook account, are they even really a person? Yes, of course they are, but it just makes life easier when you're part of the world's biggest social network, as proven with Facebook's latest application, Hello - Caller ID & Blocking.