Hacking Wi-Fi is a lot easier than most people think, but the ways of doing so are clustered around a few common techniques most hackers use. With a few simple actions, the average user can go a long way toward defending against the five most common methods of Wi-Fi hacking, which include password cracking, social engineering, WPS attacks, remote access, and rogue access points.

Apple knows their products can be addicting, and with iOS 12, they are doing something about it. With the help of Screen Time and few other new tools, it should now be a lot easier to get off your phone and enjoy life in the real world.

Google Calendar is a cornerstone of the Google Suite, perhaps second only to Gmail itself. Whereas email is constantly plagued by phishing attacks, as of yet, the calendar is a relatively untapped social engineering attack vector. But it's relatively easy for an attacker to inject a meeting or event into a target's Google Calendar and use it to exploit them.

As with most social media platforms, Instagram can be a double-edged sword. On one hand, it's a great way to share and express yourself — but on the other, it can be just as effective at compromising your privacy. Thankfully, there are a few things you can do to protect yourself.

Introduced along with the iPhone X, Animoji are animated characters, mostly animals, that are rendered from the user's facial expressions using the device's TrueDepth camera system to track the user's facial movements.

Paying for street parking in New York City just got so much easier. Instead of searching for loose change or hoping you didn't forget your wallet, you can use a device you always have with you: your phone.

Apple Maps. For years now, its reputation has been that of a punchline. Although Apple and Google battle for supremacy in most hardware and software categories, in the map game there's no question who has the superior app. But the news of the day shows Apple expanding the cities it plans on collecting street data from, opening up speculation that they're not ready to throw in the towel on Apple Maps.

Some studies have shown that vitamin D supplements help fight respiratory infections, but some haven't. A new study published in The BMJ clarified the confusion, and identified a group of people that might be better able to fight off colds and flu with vitamin D supplements.

What's the best part of the holidays, other than gorging yourself on food until you're physically able to hibernate? Imbibing delicious, hot drinks that are spiked to the gills with liquor.

With all of the bare-bones setup out of the way in our Mac for Hackers series, your Apple machine should be ready to run a significant amount of pentesting tools. We can pull tools from GitHub and compile them, we can pull dependencies or tools from Homebrew, we have both Python and Ruby. Everything is ready to go and now it's time to start building a toolbox on our local host.

If you've ever found yourself staring at intricately woven pastries at your local bakery and wondered how they do it, you'd be surprised to know it's not all that difficult. Those pastries with differing shapes and lovely lattice work may scream endless preparation and meticulous attention to detail, but they're actually quite easy to make at home.
Welcome back Hackers\Newbies!

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

Perhaps the best part about Easter is the fact that, even after the day is over, there's usually still a lot of candy left. Jelly beans, gummy bears, Cadbury eggs, peanut butter cups, marshmallow peeps — there's no end to the sugary goodness in your awesome Easter basket. Yet as much as I love stuffing my face with brightly colored candies, it's easy to get sick of them halfway through the basket.

Here is a tutorial to show you how you can easily make this much loved Frozen character with Play-Doh. Using some simple techniques and clever tricks, you can make your very own Olaf.

Shark jumps Steampunk, experts unsure of the meaning. Cape Town -- In an unprecedented move today, a Shark have jumped a steampunk couple as they were attempting to work on their hobby steamboat.

Sherlock Holmes is one of the most famous characters in modern history, and has appeared in film more often than any other character. No less than 78 different actors have taken their turn at portraying the enigmatic deduction machine in various mediums, and each has brought their own foibles to the role. Some of the names may even surprise you: Tom Baker, John Cleese, Peter Cushing, Charlton Heston, Christopher Lee, Roger Moore, and even Leonard Nimoy.

Will the predicted apocalyptic date—December 21st, 2012—really be the end of the world? In this ongoing five-part series, we examine what would happen if zombies, nuclear weapons, cyber wars, earthquakes, or aliens actually destroyed our planet—and how you might survive.

In this video, a man performs a French, Baroque-era (17th Century) style dance, the minuet. A minuet is a social dance of French origin for two people. This video gives a demonstration of minuet combinations.

Learn how to follow proper netiquette rules. You may be a model of decorum in person, but a bonehead online. Check out how much you know about Internet manners.

Having a boring Facebook profile is lame! Impress your friends and flaunt your social networking skills by sprucing up your Facebook profile.

Thanks to modern "smart phones" and the internet, media by the people, for the people is finally a reality. Here's how to use your phone to be a mobile journalist.

Everybody knows it really shouldn’t matter, but sometimes entering a school cafeteria without a lunch mate can seem like walking the plank. Here’s how to survive the stroll.

Why waste your vacation dollars on pricey hotel rooms when there are cheaper – and sometimes free – alternatives? Watch this video to learn how to find cheap (or free) places to crash on vacation.

Learn how to mingle. If the idea of walking into a room full of strangers strikes fear into your heart… welcome to the club. But there are ways to overcome this common social phobia.

This weekend, hackers broke into the servers of the popular shoe shopping site Zappos, giving them access to the personal information of 24 million Zappos customers. The user data taken included names, email addresses, billing and shipping addresses, phone numbers, the last four digits of credit card numbers, and encrypted passwords. However, full credit card data was not lifted, and passwords were cryptographically scrambled.

The frustration of searching for the perfect image can be overwhelming. Then there's the issue of copyrights: Can you use it? Do you have to give credit? Are you allowed to manipulate the image?

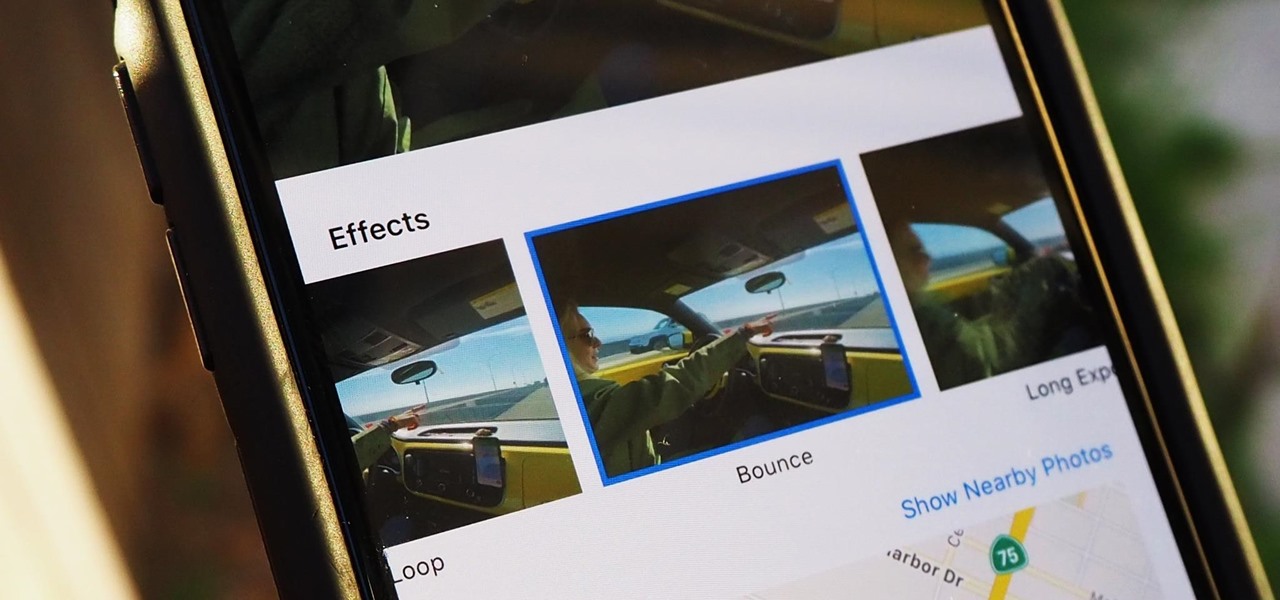
Live Photos haven't caught on as much as Apple probably would like, but they're far from the gimmick that critics initially claimed they were — and things are only getting better as time moves on. Some aspects of the feature are somewhat hidden, however, and you need to find them to unlock Live Photos' full potential.

You need a break from gloomy coronavirus updates. We all do. The unrelenting stream of doom and negative news is both helpful in terms of keeping ourselves and our families safe, but it also has the unfortunate effect of increasing our anxiety. When will this end? How bad will it get? Is there reason to be hopeful?

Following someone on Twitter is an investment. You virtually agree to have their opinions, tirades, and hot takes spewed across your timeline. It can get annoying real quick if they're known to post controversial comments periodically. However, there are other ways to stay updated on someone's tweets without you having to hit the follow button and go all in.

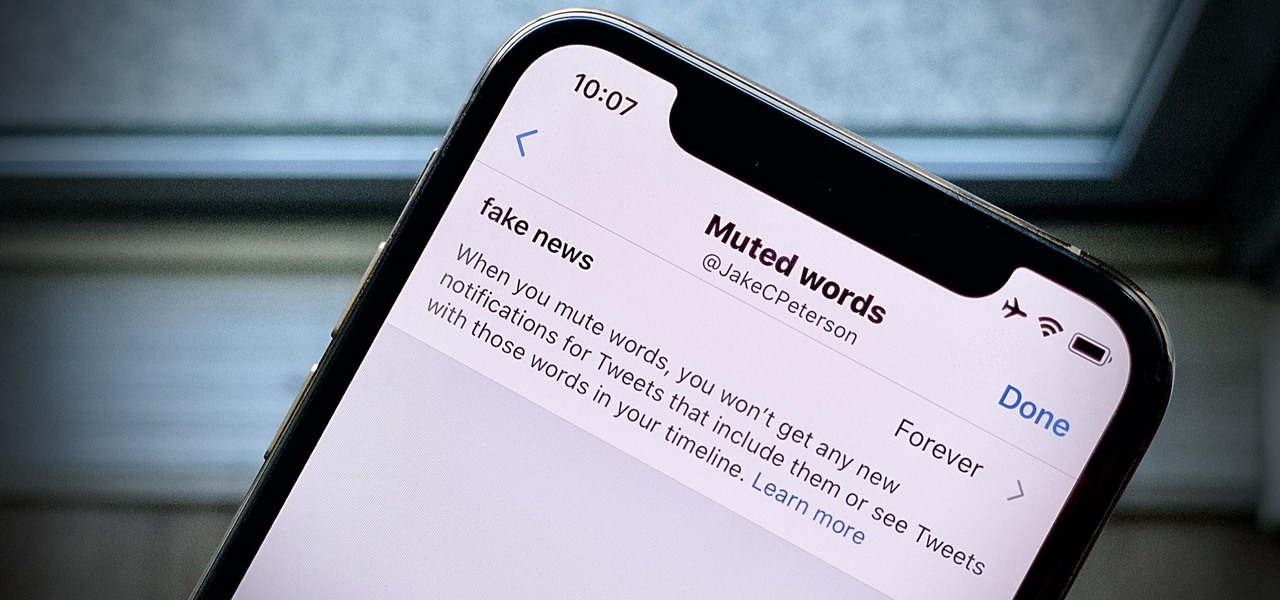
Twitter can be a wonderful place for people to express their emotions and chat with each other in brief. However, it can also be a breeding ground for hateful comments, foul language, and a whole lot of political talk.

If you don't want to be found on Twitter, there are several ways to do that without making your account private. For instance, you can choose an obscure username, omit your real name, or pick a random avatar. But there are lesser-known features deep in your settings that can also protect your privacy online, including preventing photo tags.

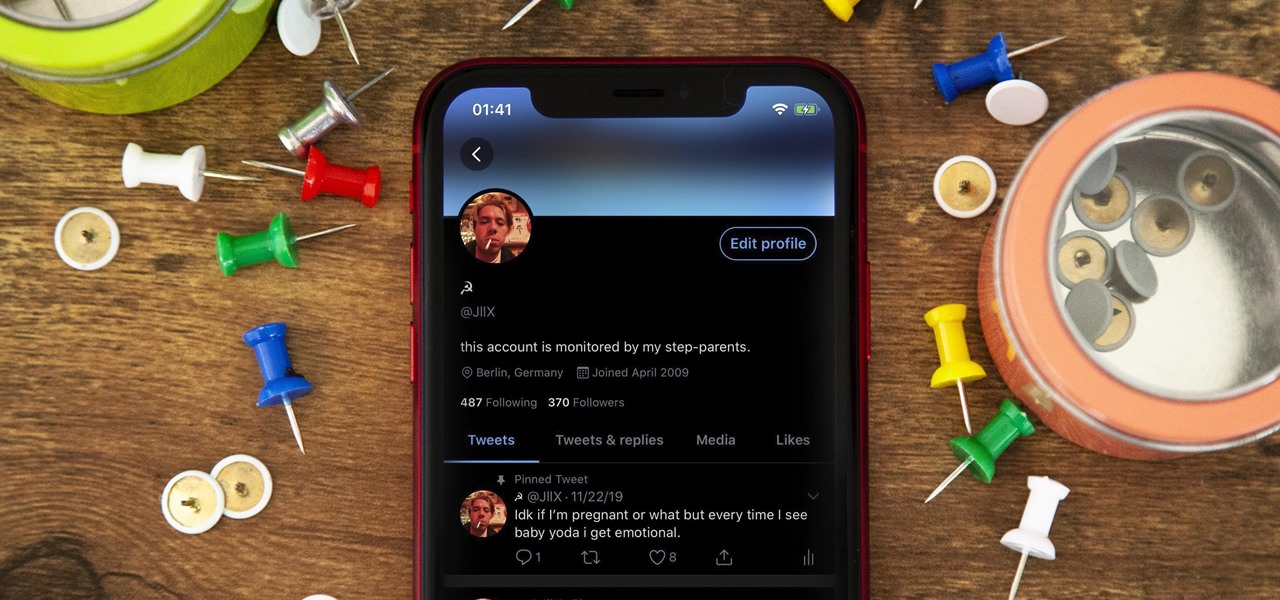
Pinning a tweet is a great way to get the point across because it's the first post people see when they visit your Twitter profile. When you pin a tweet, reply, or retweet, it sticks to the top of your profile, whether you create new tweets or not. It's the perfect spot to place one of your more popular tweets, a fantastic blog you wrote, or even just a joke that shows your personality.

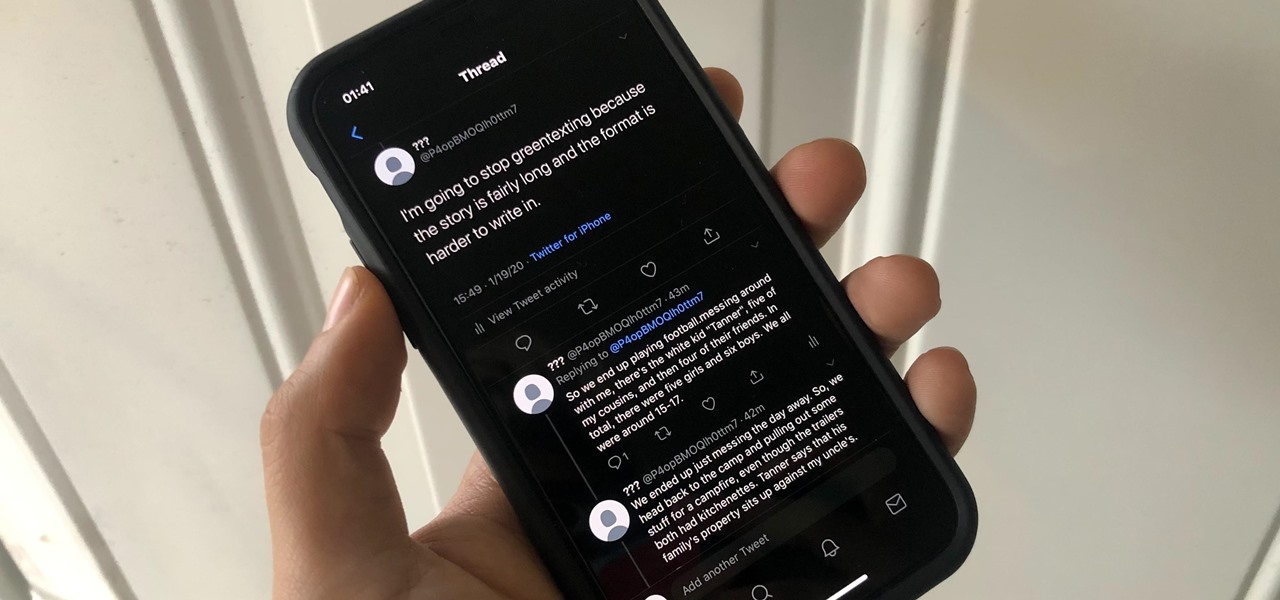
The 280-character limit for tweets on Twitter is double what it used to be back in the day, but it's still not enough to express in-depth thoughts, ideas, commentary, rants, blogs, stories, and the like. These tweetstorms, as they're called, are the reason why Twitter created its threads feature.

While the long-awaited HoloLens 2 officially arrived this week, details leaked about another, arguably longer-awaited AR headset, the fabled wearable from Apple, and a previously undisclosed partner assisting the Cupertino-based company with the hardware.

Social media accounts are a favorite target for hackers, and the most effective tactics for attacking accounts on websites like Facebook, Instagram, and Twitter are often based on phishing. These password-stealing attacks rely on tricking users into entering their passwords into a convincing fake webpage, and they have become increasingly easy to make thanks to tools like BlackEye.

Augmented reality gaming startup Tilt Five is ready to reinvent old school Dungeons & Dragons-style games for the modern age with its augmented reality headset and tabletop game system.

My autistic son loves music. One afternoon, when he was nine, I downloaded GarageBand to his iPhone to help with the boredom of a long wait at a doctor's office. Instead of pacing or escalating into a meltdown, he spent the entire hour and a half practicing, learning, and composing. When we finally left that day, the rest of us exhausted and irritated, he shared his first composition with a big smile.

Microsoft.com is one of the most extensive domains on the internet with thousands of registered subdomains. Windows 10 will ping these subdomains hundreds of times an hour, making it challenging to firewall and monitor all of the requests made by the operating system. An attacker can use these subdomains to serve payloads to evade network firewalls.

Unless you're completely new to Instagram, it's likely that you've linked your account with a third-party service at some point and forgotten about it. Those services still have access to data such as your media and profile information, so it's important that you not only know how to find these "authorized" apps, but that you know how to revoke their permissions.