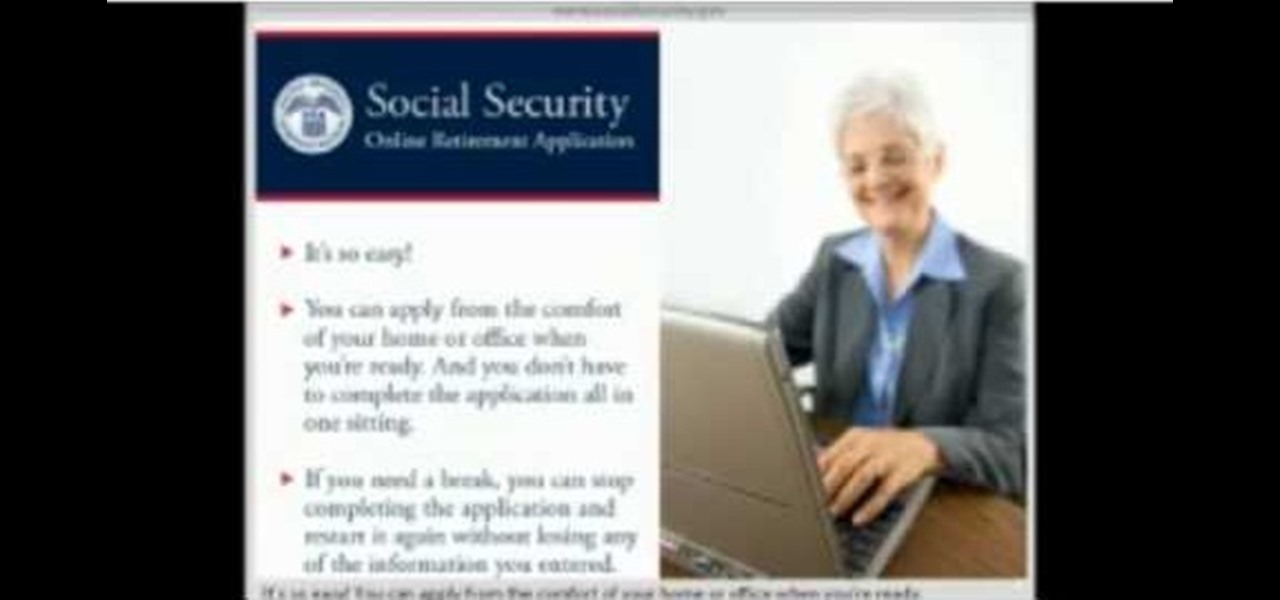
When you decide its time to retire, you will most likely need to cash in your Social Security benefits. In this official two part tutorial, presented by the American Social Secuity Administration, learn exactly how to use their website and apply online. Applying online is very easy, and takes a lot less time than applying in person. By applying online for social security, you will bypass all of the long lines and waiting that usually happens in one of the offices. Plus, you won't ever have to...

As long as you're on the internet, you can be hacked. With an estimated 2.65 billion social media users, these apps are prime targets for hackers.

Have you ever thought of building your own social networking site? Before you get to making websites like Facebook, you need to start off smaller, and this 29-part video series is where to begin with developing a social networking community website . Before you start with these lessons though, make sure you have all the following:

If you have children who are still your dependents and have been living in your household for at least half of the year, and have their own social security number, you can actually get a major tax credit with a simple worksheet. In this video you will learn the requirements for the tax credit and also how to fill out the worksheet and calculate your credit.

Take a folder and organize documents based on the actions required. Actions:

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to packet sniff networks with the fundamentals.

Identity theft typically occurs when someone uses your personal information such as social security numbers, credit card numbers or account information to perform various misdeeds, and you are left to clean up the mess.

T-Mobile's credit-checking system was recently hacked, and this one is about as bad as it gets. The names of 15 million customers, their date of birth and social security number, as well as driver's license numbers and additional information was illegally accessed, meaning the potential for identity theft here is huge.

In this tutorial, we learn how to sign up and set up a Twitter account. Twitter is a social networking site where you have 140 characters to tell your friends how you are feeling, what you are doing, or talk to them! You can follow people and other people can follow you. You can choose who follows you, which will create and strengthen online relationships. You can even get business referrals from this! Just by getting yourself out there, this is a great tool. To sign up, you will simply go to...

Greetings, hackers and friends! I know it has been a while since I posted a tutorial, and hopefully I can make up for that by posting a series.

Hello, hackers and engineers! Today we are going to dive a tiny bit deeper into the secrets of psychology, and how we can use them with hacking and social engineering attacks.

The video shows us how to use a proxy to bypass the Internet Filters. Most of the times in our schools and colleges most of the websites including the social networking ones will be blocked for security reasons and makes us unable to log into those websites. In such cases even the ones from the YouTube, several videos will be blocked. So in this video, we will be shown how to bypass those filters and log into those sites. Firstly go to the website Proxapp and over there you will be asked the ...

Gigafide explains that with so many different social networking sites, it is hard to keep information up to date on all of them. He first introduces TweetDeck, an amazing desktop application that allows a user to update information for their Twitter, Facebook, MySpace, and LinkedIn accounts. If you don't want to go through the hassle of installing TweetDeck on your computer, there is HootSuite, a web application that allows you to do this and if you're interested in keeping track of much more...

There are 10 major ways to protect your PC. Disable Autorun, in Windows. Make sure that your system is up to date, by setting automatic updates. Always use a log on for your computer that does not have administrative privileges. Use different passwords, and change your passwords on a regular basis. Don't use simple passwords. Be careful of using links sent to you via email. Never disclose your sensitive information in public forums: e.g. social networks. Encrypt sensitive data on your compute...

In this tutorial, we learn how to apply for unemployment in New York. You can do this either by phone or by going online. You will need personal information to file, including: social security number, drivers license number, mailing address, phone number, and W-2 form. Even if you don't have every item on the list, you can still file a claim. You will get a four digit pin number, then have an agent gather all of your information. If you do call to file, there are people who work there that sp...

Code execution in Microsoft Word is easier than ever, thanks to recent research done by Etienne Stalmans and Saif El-Sherei. Executing code in MS Word can be complicated, in some cases requiring the use of Macros or memory corruption. Fortunately, Microsoft has a built in a feature that we can abuse to have the same effect. The best part, it does so without raising any User Account Control security warnings. Let's look at how it's done.

With more people joining the internet scene each day it's important that it's security is.. well it has to be good. Of course everything can be hacked and that's the way hackers work. They know there IS a vulnerability but they don't don't know the rest. in this article i'll try to explain the big difference between HTTP and HTTPS

The Nokia Social hub is a fairly useful piece of software available to owners of the Nokia Booklet 3G netbook. From the Social hub, you can connect to facebook and access several of the social network's functions, including posting an update. If you have a SIM card inserted with an active 3G connection, you can even send a text message from the netbook.

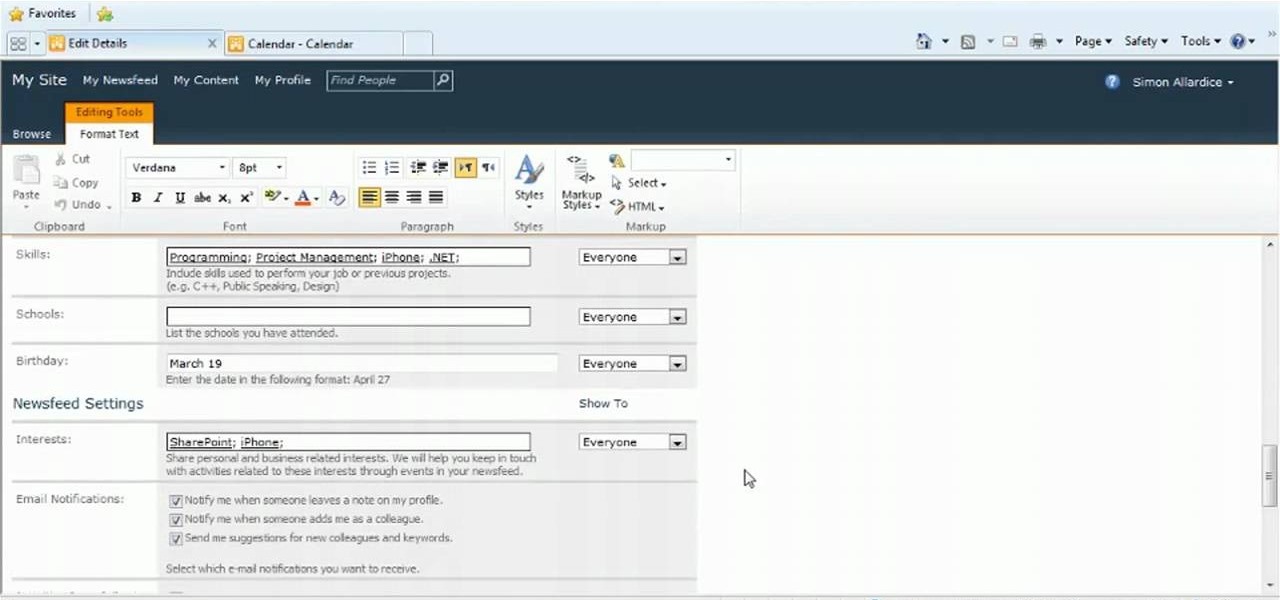
Learn how to take advantage of Microsoft SharePoint 2010's new social computing tools. Whether you're new to Microsoft's popular content management system (CMS) or a seasoned MS Office professional just looking to better acquaint yourself with the SharePoint 2010 workflow, you're sure to be well served by this video tutorial. For more information, and to get started taking advantage of SharePoint's social computing features yourself, watch this free video guide.

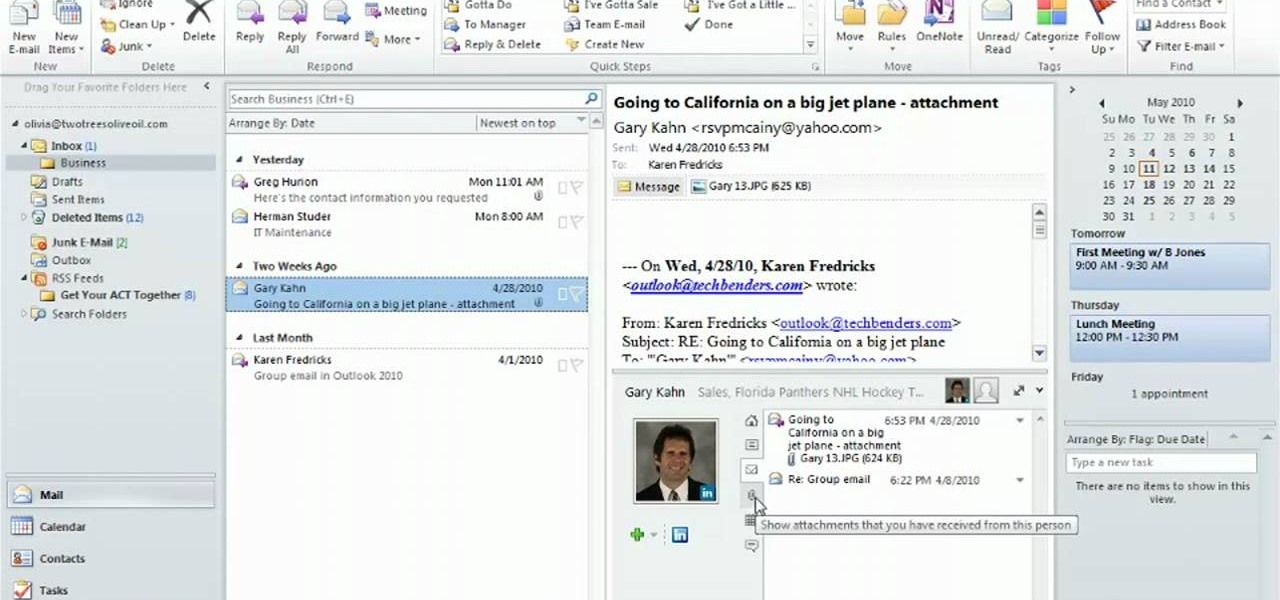
Use the Microsoft Office 2010 Social Connector tool to reach out to friends in your favorite social networks. Whether you're new to Microsoft's popular email and scheduling application or a seasoned MS Office professional just looking to better acquaint yourself with the Outlook 2010 workflow, you're sure to be well served by this video tutorial. For more information, and to get started using the Outlook 2010 tool for yourself, watch this free video guide.

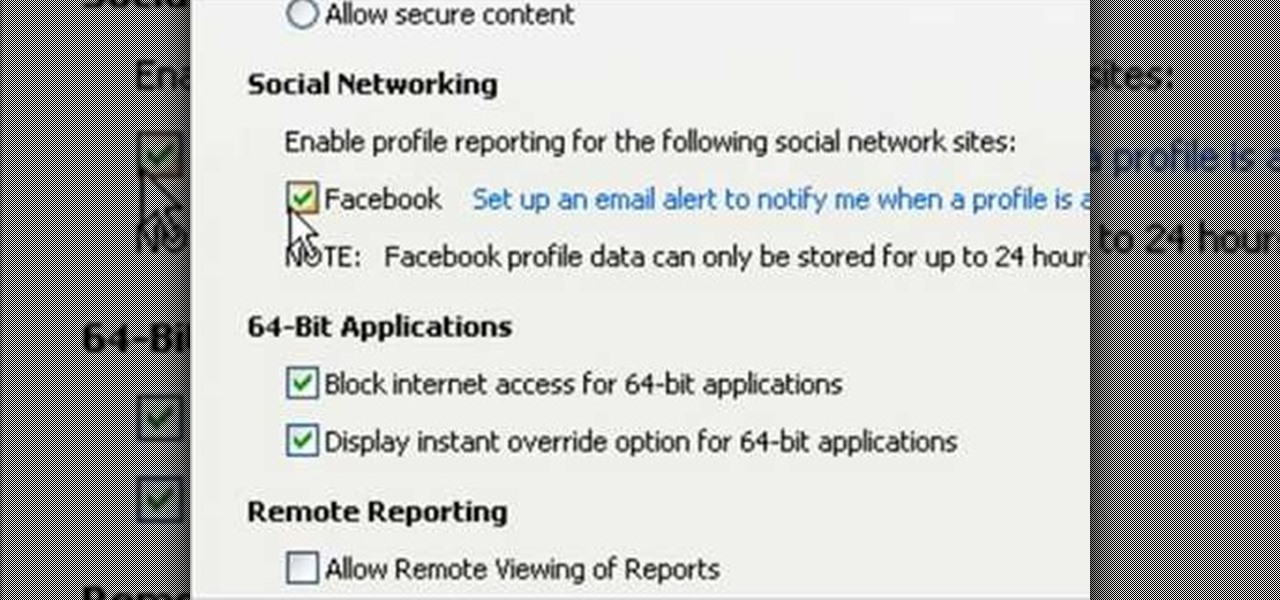
Danny with Top Ten Reviews will show you how to monitor social network activity with the Net Natty program. This will be helpful for monitoring social networking accounts on websites such as Facebook and MySpace. First, open Net Nanny. Go to the dashboard and select Additional Settings under Filtering. With this section, social networking sites that have been used on the computer will be listed. You can check whichever account you want to monitor. Under the dashboard, go to Reports and select...

Check out this instructional video to learn how to ask and answer simple questions in a social conversation. "Social English" is a series of four short videos that deal with common face-to-face English situations at Fujikin. This is the third video in the series and will show you how to ask and answer questions naturally in an English conversation.

Among the younger generation, Roblox rivals major titles like Minecraft as one of the most popular online games out there. In fact, it's common to hear children tell new playmates to "friend me in Roblox!" so they can play together online. There's nothing inherently sinister here, but with all the online interaction, kids' safety becomes a factor.

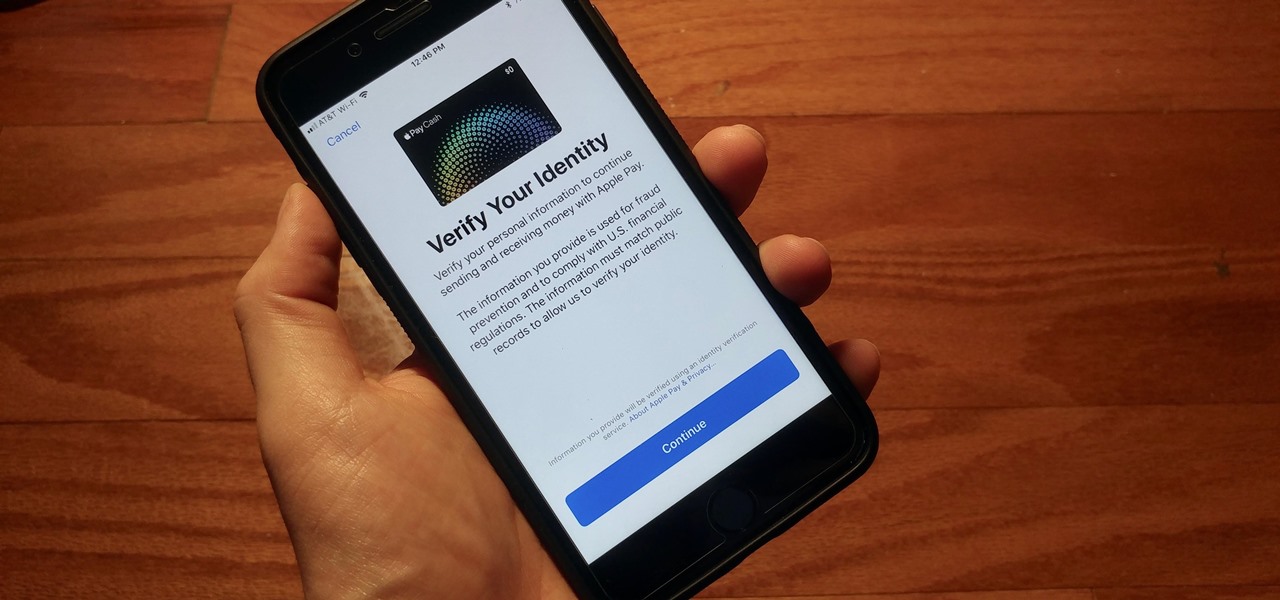
With iOS 11.2's introduction of Apple Pay Cash, you can send and receive money to others directly through iMessage, using the convenience and security Apple Pay is known for. However, if you want to make sure your efforts go uninterrupted, you'll want to make sure you verify your identity with Apple.

For an easy way to lookup and connect with people and companies across the web (and all of its many social media outlets) check out the Firefox extension Tabble. Tabble provides you with access to all of an individual's relevant online information and can even show you relevant e-mails in your Gmail account if applicable.

Learn to take back control if social anxiety is getting in the way of your life. The first step is to take control of conversations at social functions by asking questions. This will help you to direct the conversation more and not feel like you have no control. Next, learn to always have an exit plan for any social function you might attend. Planning an exit strategy beforehand will help you to relax. Finally, be kind and loving to yourself. Don't beat yourself up and take the time to be mor...

In the realm of internet security, it's becoming clear that augmented reality is not immune to the increasing wave data breaches plaguing users.

One of the best ways to increase traffic to your web site is to participate in social media. This video will show you how to optimize your social media posts so that they generate the most interest in your site and attract the most visitors.

This video tutorial is in the Motivation & Self Help category which will show you how to deal with social anxiety and improve your social skills. In this video Momo answers some questions on social skills and gives a few suggestions on what to do when the panic sets in. The panic sets in either because you have nothing to say or you have expectations. Usually it is expectations. You got expectations from your teachers, your parents, your friends or your peers. When you have expectations when ...

Want to know how to use social plugins on Facebook? This clip will show you how it's done. Whether you're completely new to the Facebook's popular social networking site or simply require a small amount of clarification on how to perform a particular task on Facebook, you're sure to benefit from this helpful video guide. For more information, including detailed, step-by-step instructions, take a look.

Social engineering makes headlines because human behavior is often the weakest link of even well-defended targets. Automated social engineering tools can help reclusive hackers touch these techniques, but the study of how to hack human interactions in person is often ignored. Today, we will examine how to use subtle, hard to detect persuasion techniques to compromise a human target.

For a photo- and video-sharing app based around privacy, Snapchat sure has a lot of security holes floating around. At one time, you were able to take screenshots of Snapchats in iOS 7 without the sender knowing, which is something that you can still do on rooted Android devices.

Airport security lines are one of the biggest hassles involved in air travel. Navigating them quickly and successfully can be the difference between making your flight and not. This video offers some tips for how to get through security quickly, including buying airport-security-friendly luggage and packing said luggage in an easy-to-inspect way. Also, don't wrap any gift, as security may want to unwrap them!

Thanks to the Freedom of Information and Privacy acts, we’re all entitled to see what the FBI has on us. Learn how to get your hands on your FBI file.

Home security is as important as having a job. You have to protect your family and your valuables. If you can't afford a high tech security system, then maybe a fake security camera will do the trick. This security camera dud is also a cheap alternative for a film prop. Watch this video tutorial to learn how to build a fake cardboard security camera.

Airport security keeps getting stricter and more time-consuming. Shorten your time in the security line with these tips. Watch this video travel tutorial and learn how to get through airport security.

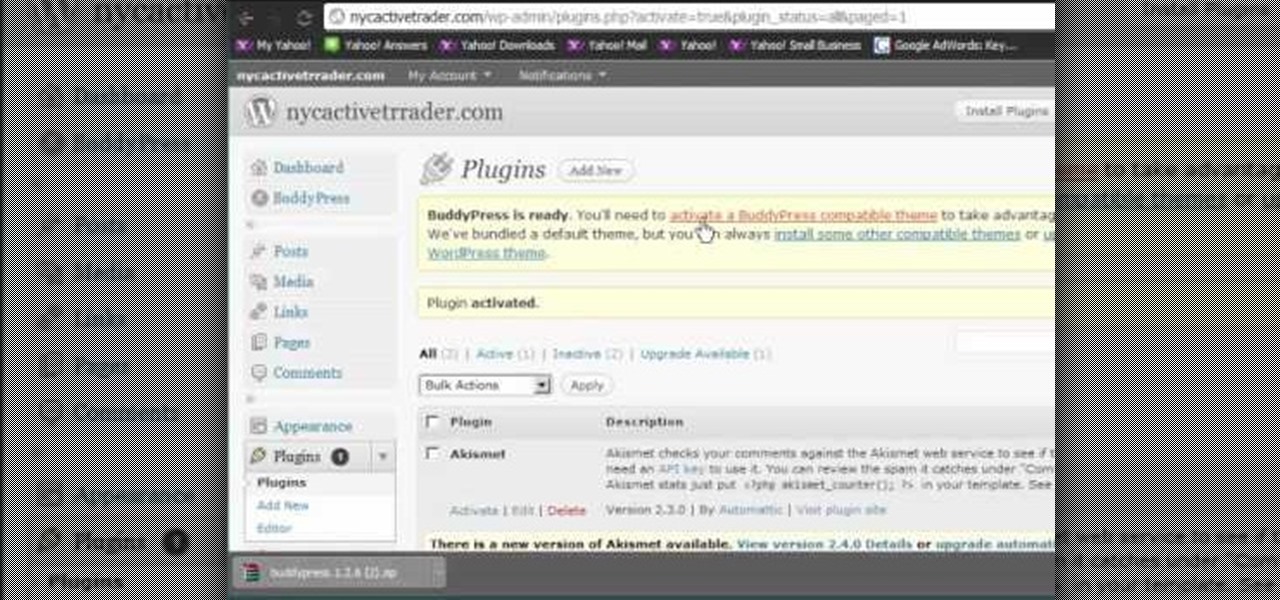
Like Facebook so much that you want to make your own version of a social network, just for you and your friends? It's totally possible, thanks to BuddyPress, a DIY social network for a tight community with the power of WordPress. This video will show you the steps to installing it and setting up your own social network.

If you haven't been on any sort of social media all day — which I seriously doubt — then you might not have heard that today, June 30, is Social Media Day. It's been trending on Twitter, but has also been making appearances on Instagram and Facebook. While major influencers are talking up a storm about this, most people are simply asking "what is social media day?"

The photo-centric Instagram app is a great way to share "evergreen" pictures and videos when compared to Snapchat and Facebook's new Messenger Day feature. But like all social media, keeping the account secure is an essential aspect, as it restricts unwanted viewers from seeing your content and can prevent unauthorized users from accessing your account. Instagram has several methods for locking down the account including a new two-factor authentication (2FA) mechanism.

Just because the internet renders you virtually anonymous does not mean social customs should be ignored. Just like in the outside world, there is etiquette that should be obeyed if you want to be treated as a friend rather than an annoyance online. In this how to video, Proper Ollie teaches you how you can have proper internet etiquette in social networking forums.