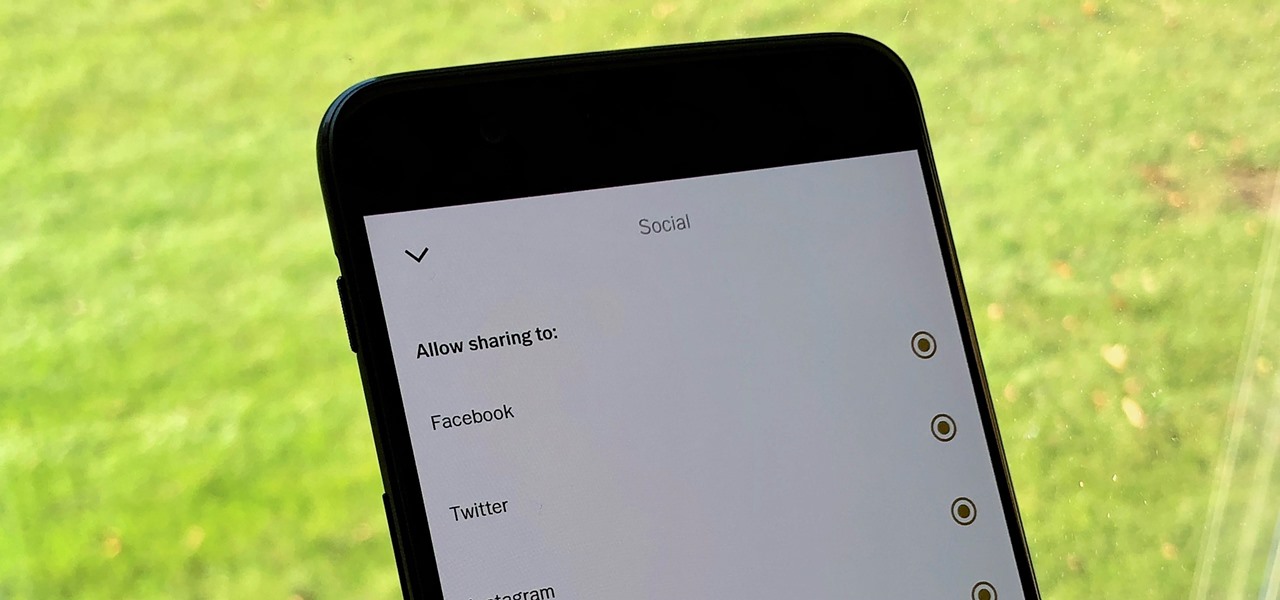
As with most social media platforms, Instagram can be a double-edged sword. On one hand, it's a great way to share and express yourself — but on the other, it can be just as effective at compromising your privacy. Thankfully, there are a few things you can do to protect yourself.

Welcome back, my future hackers! After my first tutorial about doxing, I decided I would dive a little bit deeper into the world of social engineering. In this tutorial we will learn some basic social engineering techniques to get into a company building, find out more information about the company's security, and maybe even exploit the company's computers if you get the chance.

In February of this year, the Higher Court of Berlin ruled that Facebook must follow strict German data protection laws, which Facebook's terms of services and privacy policies circumvent.

What's your Twitter handle worth? If it's considered "desirable" (aka short and simple), it'll get you around 100 bucks, or, if you prefer, the affections of a teenage girl.
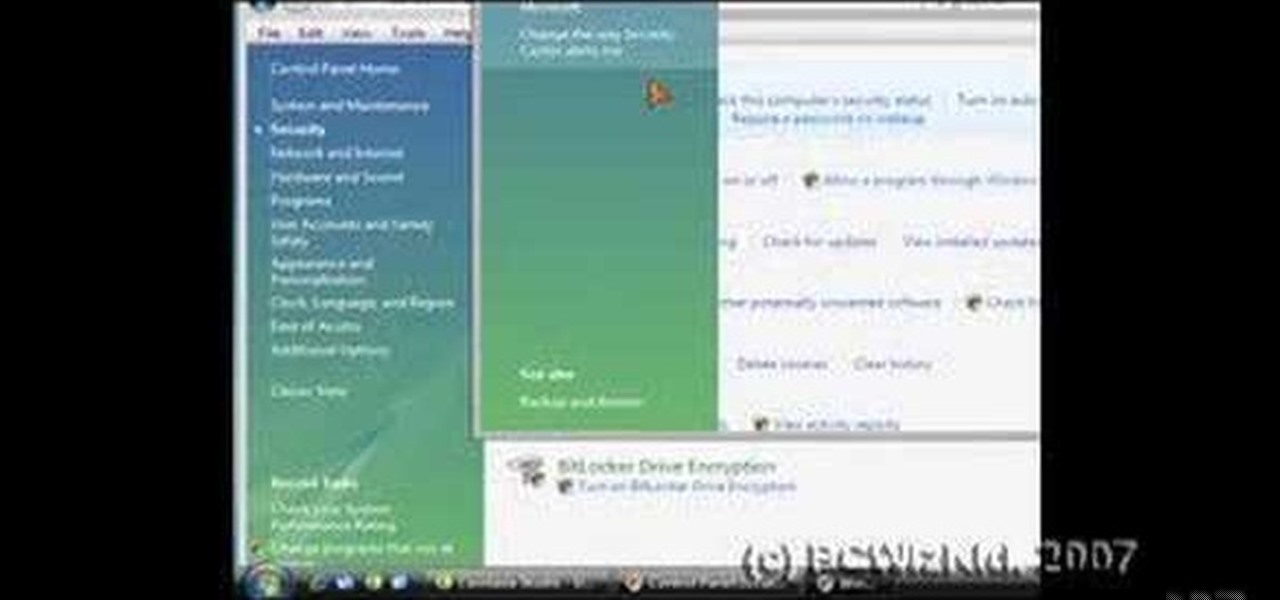
Windows Vista is jam-packed full of new security features, which could be a good thing, but they're just so obtrusive it's not really worth it. If you want to learn how to stop all of the annoying security alerts, this video will walk you through the process of disabling these security notifications in Windows Vista.

So you're at a club and want to show off your Bachata dance moves, but not sure how? In this video, learn how to do "social Bachata dancing" in which you're in an environment, such as a dance club, that requires a dance partner. Learn about the ins and outs of social Bachata dancing with help from this video.

Check out this instructional video to learn how to introduce yourself in English in a business situation. "Social English" is a series of four short videos that deal with common face-to-face English situations at Fujikin. This is the first video in the series and will show you how to introduce yourself to an English speaker.

Greeting someone in English is very simple. Check out this instructional video to learn how to greet someone in English. "Social English" is a series of four short videos that deal with common face-to-face English situations at Fujikin. This is the second video in the series and will show you how to exchange greetings in English.

Social contact is important in establishing yourself as the "alpha" in your dog's eyes. Don't forget to learn this important dog training step. Watch this video pet training tutorial and learn how to use social contact to establish leadership over a pet dog.

When Google introduced the Pixel 3 on October 9th, one of new additions they briefly mentioned was the Titan M security chip. While they did talk about how it will improve overall security, they didn't expand on the number of changes it brings to the Pixel 3's security. Well, they finally shared more, and it's a pretty big deal.

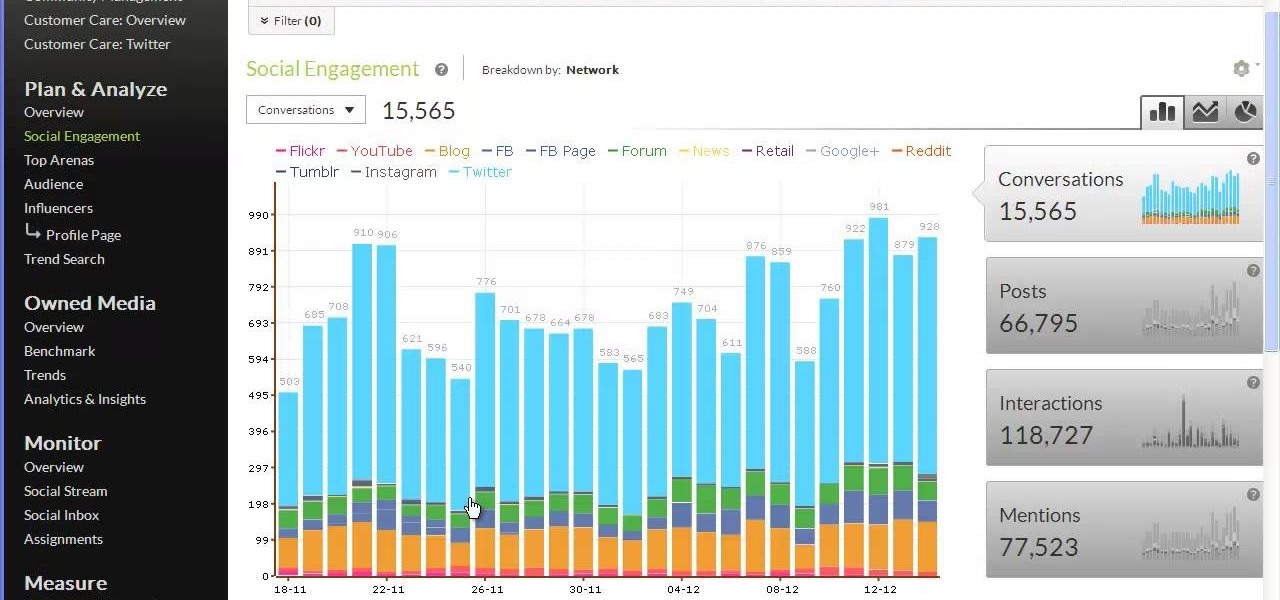
Tracx is a social intelligence software platform that allows enterprises to manage, share and extract actionable insights, threats and opportunities from the social web —in real time.

Installing security lights outside of your home can make for a great addition, but they also create new problems with regards to maintenance and cleaning. Having lights outside exposes them to all of the elements that mother nature can throw at them. This video will show not only how to install security lights, it will also show the proper measures to take so they will keep working with minimal maintenance and care.

This is a lock picking video which demonstrates how to pick a tumbler lock. Of course the only way to really open locks is to practice. But this is the basic info to picking locks. This lock picking tutorial also covers security pins and clear instructional animations to demonstrate. Learn how to pick a lock and use this video to understand lockpicking, security pins, skill tension, and bump keys. See all about how to pick a tumble lock & understand lock security pins.

This video is your guide to all of the armor sets in Terraria. Whether you want the hero look, the plumber style, the archaeologist armor, or the tuxedo gear, this video will show you how to get it. Learn where and how to get every social and vanity item in Terraria.

Most everyone has a fear of public speaking. Even the most seasoned politicians can't get through a speech without sweaty palms, butterflies in his/her stomach, or general nervousness. But for those who are shy, these symptoms occur every time they're in a social situation.

In this video, we learn how to improve your social skills. First, you should have a positive attitude and try to change how people think. You want to never tell people that they are wrong, just help guide people through life. Communicate with people and really listen to what they have to say to you. Make sure that you offer you opinion but give it with a positive attitude. People will listen to what you have to say and when you are passionate it will make then believe you more. Good social sk...

Need more self-confidence! Listen up! Tired of not getting a raise, a date or more social invites? Self confidence plays a major impact on our social standing and our job performance. Work on these six suggestions from Daily Idea and you'll be amazed at the increase in how you feel about yourself.

The fresh feeling of excitement in a relationship may fade over time. Learn ways to keep things fresh in your relationship from a licensed clinical social worker in this video tutorial. Take action: make intimacy and romance are priority, allow spontaneity, and don't stop learning about your partner. Carolyn McIntyre, the instructor in this how-to video from Live Strong, is a licensed clinical social worker, a certified employee assistance professional, and has training in Life Coaching.

Lock picking can be difficult with some security features. This instructional video shows you what happens when you encounter them and what to do. Break into a lock when you've forgotten your keys, but please don't sneak in anywhere you don't belong. Watch this video lock-picking tutorial and learn how to detect security pins.

Veronica Belmont imparts her wisdom on how to be safe within social networks. Learn how to adjust the settings on your Facebook, MySpace, and/or LinkedIn profile to help protect your privacy.

With the new screening protocols and their full body x-ray scanners, the TSA is taking constant criticism from unhappy travelers. Between the nude images the scanner produces and the awkward pat downs, air travel will never be the same. That's why it's important to make sure you're prepared for your flight and the TSA security checkpoints.

The Google Pixel's camera is a status symbol of sorts. When someone sees you with one, you become the photographer of choice for social events. And where do those photos end up? Social media, of course. It's how we share our lives now, and the smartphone camera defines how we approach that.

Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself from cyberstalkers, advertisers, and hackers in a time when digital lives are a high commodity.

Unless you're completely new to Instagram, it's likely that you've linked your account with a third-party service at some point and forgotten about it. Those services still have access to data such as your media and profile information, so it's important that you not only know how to find these "authorized" apps, but that you know how to revoke their permissions.

When it comes to social media, Google has had it a bit rough. But its next big app in this category is apparently steps away from completion, with a platform that allows small groups of users to edit and organize photos in unison.

Gender standards are entirely pervasive. We raise our sons to be masculine and our daughters to be feminine, which perpetuates the gender role formula when they grow up to be parents and raise their own children. Part of this whole equation is that boys are supposed to remain stoic and project an air of strength, and girls are expected to be amiable while being held to unrealistic standards of outward beauty.

Welcome back, my rookie hackers! Many newbie hackers focus upon the technical aspects of hacking and fail to give enough attention to social engineering. In fact, I would say that technical hacks should ONLY be attempted if social engineering attacks fail. Why bother spending hours or days trying to hack a password if someone will simply give it to you?

We all want to put our best face forwards on our social networking profiles. Facebook, MySpace, Twitter and all the rest are the best places to show great photos of yourself. You never know who might be looking. Employers, potential suitors, ex-high school classmates.. they are all snooping to see what you're doing and how you look these days.

In this clip, you'll learn how to quickly set a security pattern on an LG Droid Ally Google Android smartphone. For more information, including a complete demonstration and detailed, step-by-step instructions, and to get started setting up your own security secreen, watch this helpful video guide.

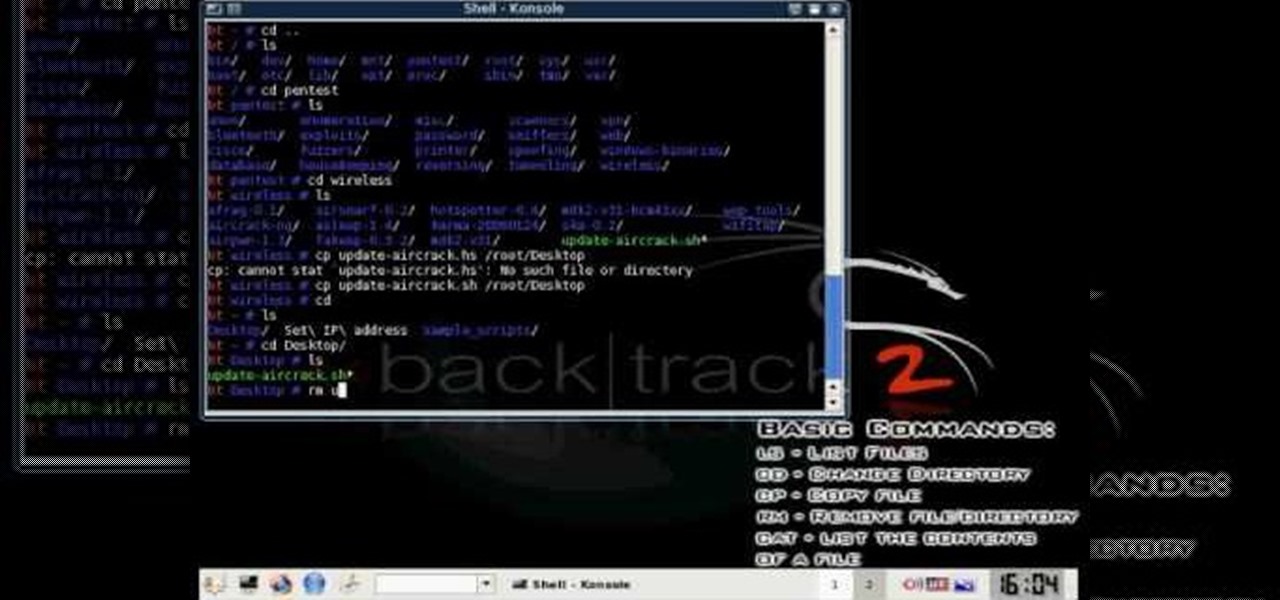
Want to test the security of your WEP WiFi wireless network? In this clip, you'll learn how to use the Backtrack Linux distro and the Aircrack-ng WiFi security app to crack a WEP key. The process is simple. For more information, including step-by-step instructions, and to get started testing the security of your own WiFi networks, watch this hacker's how-to.

Learn how to configure the features in F5's FirePass v7 SSL VPN Endpoint Security. Peter Silva shows some of the new Endpoint Security features in the recent FirePass v7 release. Watch how to create policies, enforce host checks and other protective measures for your Remote Access deployments. For more information, and to get started configuring your own installation of FirePass v7, take a look.

If you live in a hurricane prone area, it is a good idea to protect your windows with security film. This video will teach you how to install hurricane security window film on your own and protect your home and assets.

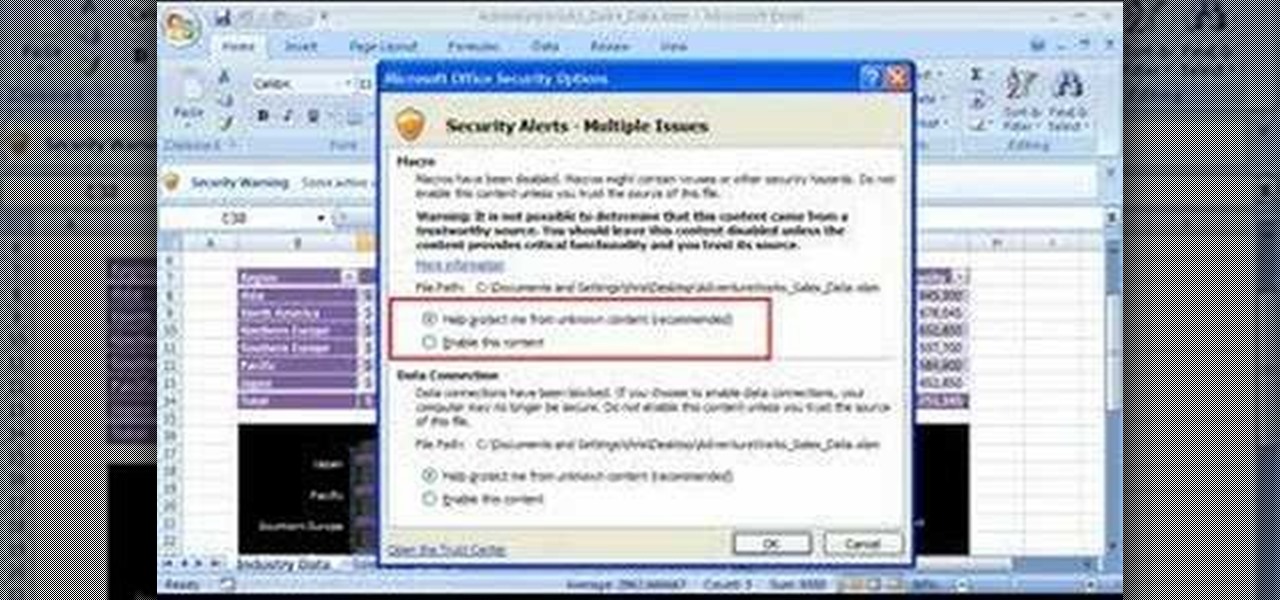
Not sure what to do when you get a security warning about a macro? What are macro security settings, the Trust Center, and Trusted Locations anyway? Watch this instructional video to learn how to enable macros and make informed security decisions that can help you keep your computer safer while you work in Microsoft Office Excel, Outlook, Word, Publisher, PowerPoint, and Visio 2007.

Ever wanted to learn how to pick a lock? Well, there's no better time than now to start learning the craft of so many locksmiths out there... lock picking. Just watch this video tutorial to see how to bypass security wafers when lock picking.

A basic tutorial from InfinityExists.com on using Backtrack - the Linux-based security software package. This tutorial covers: Where to get Backtrack 2, How to burn an .ISO file, How to boot Backtrack 2, How to login, and start the GUI interface. It also illustrates basic Linux commands, and how to set up your Network Interfaces.

One of the earliest players in the social virtual reality space, vTime, has just landed $7.6 million in new funding, which the company says is partially earmarked for developing and releasing an augmented reality version of its platform later this year.

In this day and age, publishing content to one social media account just doesn't cut it. VSCO, Facebook, Twitter, Instagram ... you need to be active on all. And if you prefer editing and posting all of your photos on VSCO, you need a way to share those images with your other accounts.

Equifax reported on Sept. 7 that it discovered a breach on July 29 which affects roughly half of Americans, many of whom don't realize they have dealings with the company. Hackers got away with social security numbers, addresses, and driver's license numbers, foreshadowing a "nuclear explosion of identity theft." Let's explore what really happened and what you and those around you can do to protect yourselves.

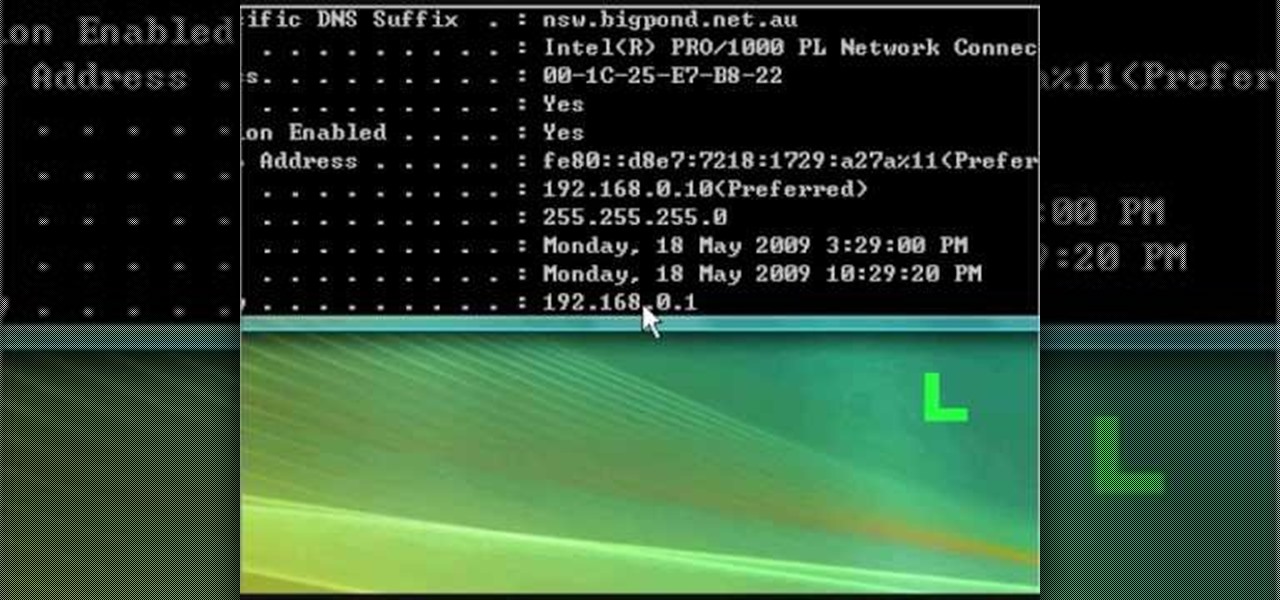
In this tutorial, we learn how to fix security mode for nds Wi-Fi. First, open the command prompt in Windows. Next, type in "ipconfig/all" in the black window that appears. After this, copy your default IP the screen just gave you, then type it into your address bar online. After this, you will be able to log into your security account and make default changes you prefer. Change different station accesses and any other security preferences you want to change. After this, you can change your p...

Having security setting on your web browser is a pretty important tool. It keeps you safe from potential hackers and makes sure you don't visit unsafe sites that could lead to a virus. But sometimes the security settings on a web browser can be a pain and the best choice would be to turn it off. So in this tutorial, you will learn how to easily change the security settings to INternet Explorer 8. So sit back and enjoy!