Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to make a Twitter tamagotchi bot with PHP.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to set up SSH tunneling to securely transmit HTTP traffic.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to session hijack with a pineapple.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to boot Windows from a USB flash key.
Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to configure Cisco and iptables firewalls with a utility.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to map networks with Spiceworks.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to break down IP and TCP header with Wireshark.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to turn any Windows application into a service.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to organize your desktop with Microsoft Scalable Fabrics.

Beat the Level 2-3 Boss in Resident Evil 5 via this walkthrough and gameplay. Resident Evil 5 (RE 5) is the sequel to 2005's Resident Evil 4. This game guide shows you BSAA emblem locations, treasures, and includes strategies for all 6 missions and boss fights.

In today's time of rampant information crimes, including identity theft, security is more important to the average computer user than ever. This tutorial from Linux Journal Online shows how you can use GnuPG to secure and verify data on your Linux box. (This video was created using only free and open source software tools: TightVNC, pyvnc2swf, ardour2, audacity, jackd, LAME, kolourpaint, cinelerra-cv, mjpegtools, and ffmpeg.)

Check out this video tutorial to see how to construct an alarm system, that's based on the principle of motion detectors, which work by touch. It's very useful to catch unpleasant visitors red-handed. So make sure your chocolate bar never gets snagged again, catch the bandits with a motion detector alarm! Or just keep you kids away from the birthday present closet where peeping is not allowed.

This is a tutorial that shows you how to view and control your computer screen from your iPhone/iPod Touch. But this method is for people who have a jailbroken iPhone/iPod Touch. This works on Edge and Wifi. If you are having problems connecting try going to control panel then security center then turn your firewall off. Also try turning off anything like virus protection.

See how to make an X10 wireless security camera into a nice helmet cam on the cheap in this three-part video. All it takes is an X10 camera, ten bucks in parts, and two hours of your time.

In this episode, Brandon Jackson shows how to merge two images with the Photoshop gradient tool to create a banner montage. Doug Grammar joins D.Lee Beard again, this time to explain spyware, adware, and keylogging. They explain what these threats to your privacy & computer speed are as well as how to prevent and get rid of them. Speaking of security, Jason Rybicki shows one way to tell if your privacy is being compromised on a Mac using a free widget.

This weekend, hackers broke into the servers of the popular shoe shopping site Zappos, giving them access to the personal information of 24 million Zappos customers. The user data taken included names, email addresses, billing and shipping addresses, phone numbers, the last four digits of credit card numbers, and encrypted passwords. However, full credit card data was not lifted, and passwords were cryptographically scrambled.

While most iOS updates will only improve the experience on your iPhone, some can cause more havoc than good. If an update unexpectedly breaks or degrades certain functions on your iPhone, you may be able to roll it back to the previous software.

The gold standard in any business is reaching the front page of Google. You need to get your brand in front of audiences. While it can seem daunting, it's not impossible when you master SEO best practices.

Confused by TikTok? Trying to grow your Instagram fanbase? Aiming to create the perfect Facebook ad? Growing an audience might be challenging, but with the right strategies, it is possible — and fun.

People use browsers for all types of things, and in general, we trust a lot of personal information to them. That's why browsers are a perfect attack surface for a hacker, because the target may not even know they are infected and feed you all of the information you could want.

If there's any silver lining to being stuck at home right now, it's the fact that many of us have way more time to take care of those things that have been sitting on our back burner for ages, like beefing up our resumes.

The coronavirus pandemic has ushered in an unprecedented time in modern history where terms like "social distancing" and "self-quarantine" have pushed their way into the zeitgeist.

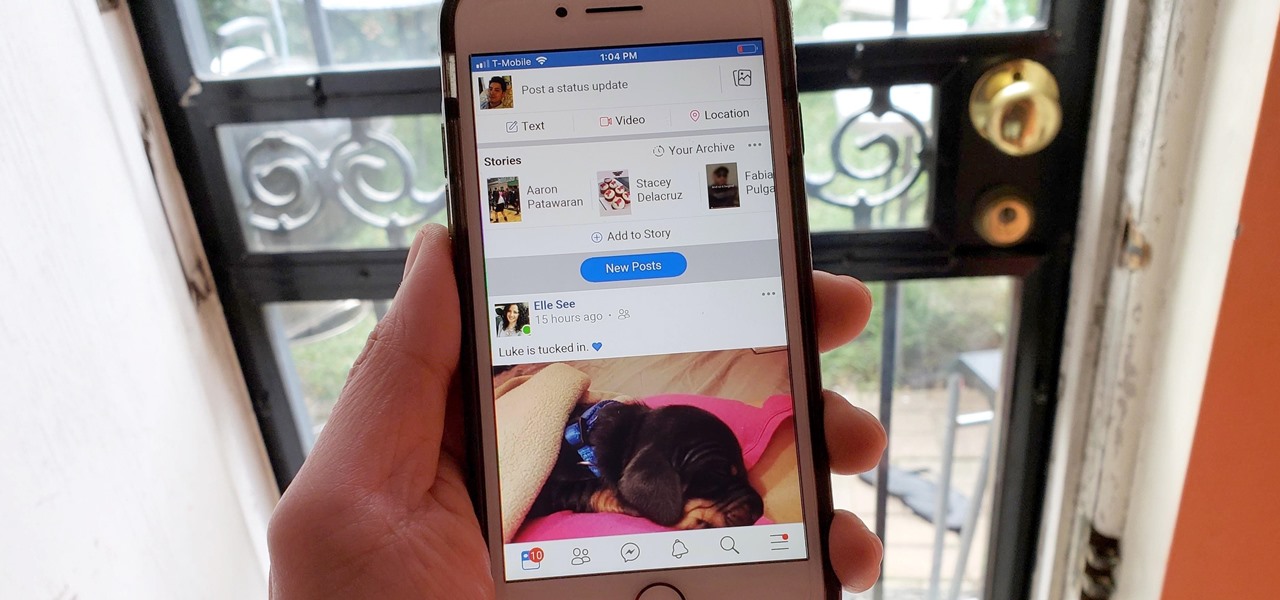
Group chats in Facebook Messenger can devolve into outright noise pollution as people chit chat randomly and bombard you with distracting notifications. Unfortunately, leaving the group outright alerts everyone inside, so if you want to get out of the thread unnoticed, what exactly can you do?

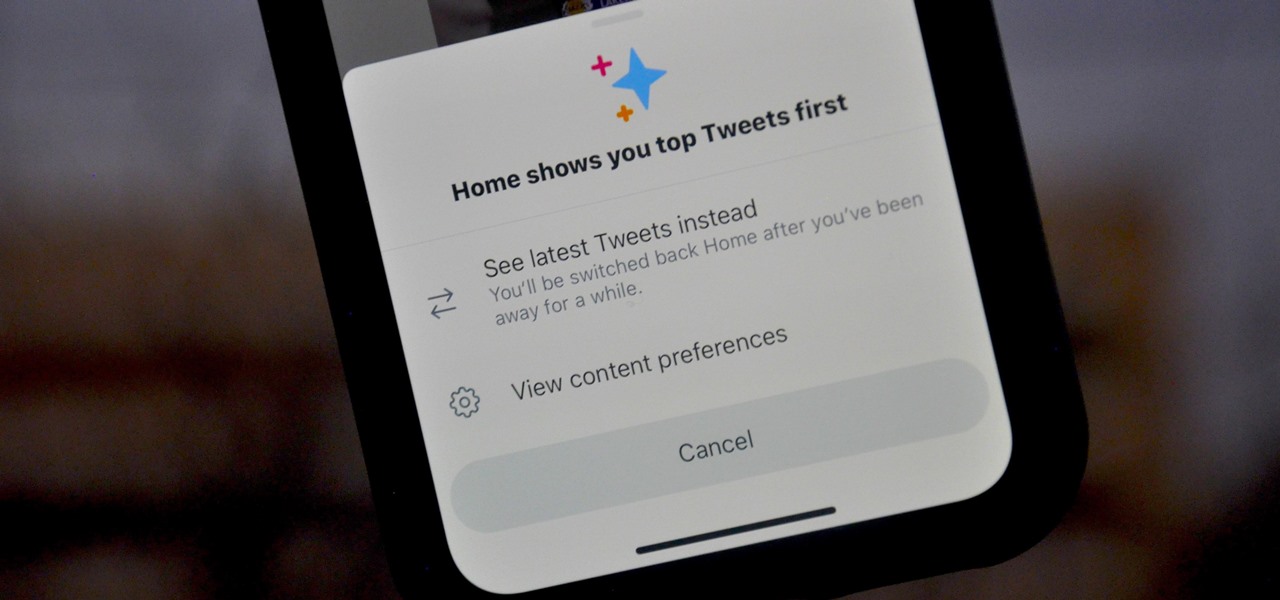
If you're tired of the so-called "top" tweets appearing first in your Twitter timeline instead of only the latest from the people, companies, and bots you follow, there's a way to get rid of them.

Lego has shipped several apps and products that add an augmented reality dimension to their playsets. But it has taken a reality TV show from Fox to allow brick fans to build with virtual bricks in augmented reality.

Augmented reality seems to come into its own in museums, where audiences are ready and willing to try out new immersive tech. Now, that tech-powered palette is about to get a little larger.

Despite the fact that over 600,000 Snap Lens filters have been created since Lens Studio debuted in 2017, and Facebook is reporting that more than a billion users have interacted with its Spark AR filters across Facebook properties, social augmented reality filters get a bad rap in the AR industry.

It takes confidence and guts to pull off attractive and yet adequately frightening Halloween makeup as an adult.

Augmented reality can be more than simply a way to enhance navigation, or superimpose virtual sunglasses onto your face. It can also be a platform for shining a light on important social issues.

Imagine sitting on your patio, scrolling through your phone's photos, reminiscing about the past. Now imagine being able to see those photos floating in the air, at the exact vantage point from where they were taken a year ago.

Phishing is the easiest way to get your password stolen, as it only takes one mistake to log in to the wrong website. A convincing phishing site is key to a successful attempt, and tools to create them have become intuitive and more sophisticated. SocialFish allows a hacker to create a persuasive phishing page for nearly any website, offering a web interface with an Android app for remote control.

Every summer for the last 26 years, hoards of hackers have descended on the Las Vegas Strip for DEFCON, the biggest hacker conference in the US. There's a wealth of talks every season (DEFCON 27 has at least 95 scheduled), and there have been some essential topics to learn from in past discussions. We've dug through the last ten years and found the 15 most popular talks you should watch.

For me, there's nothing better than popping on a favorite show or new movie after a long day at the office — except when there's a friend or two I can talk to about that crazy ending. Netflix doesn't double as a social media app, so you can't chat about what you're watching there. What you can do is share your latest obsession to your Instagram story, to get the discussion going with all your followers.

One of the best things about Android is the ability to customize every aspect of your device to make it your own. However, unless you have prior knowledge or experience with every single setting available to you, you might have missed a few critical features without even knowing it. Some settings are easy to find, while others might be tucked away in another menu of their own.

For lack of a better word, a missing iPhone sucks. Not only do you lose a physical device that cost you a small fortune, but there's also the probability you'll never see your precious data again. Hackers and thieves might, just not you. To keep this from ever happening, there are preventative measures you should take, and the sooner you do them the better.

The latest film addition in the American-produced Millennium series, The Girl in the Spider's Web, was just released on Blu-ray a few days ago. As you could expect, the movie has many hacking scenes throughout, just like the previous English and Swedish language movies centered around hacker Lisbeth Salander. Of course, with the quick pace of some scenes, the hacks can be hard to follow.

Many apps, including Facebook, Twitter, and Facebook, do not let you download videos, even if they are living on your own account. Saving these videos usually requires a third-party app or screen recorder, which is inconvenient and can result in loss of quality. However, TikTok, the newish popular short-form video platform, makes it easy to download videos — even if they're not yours.

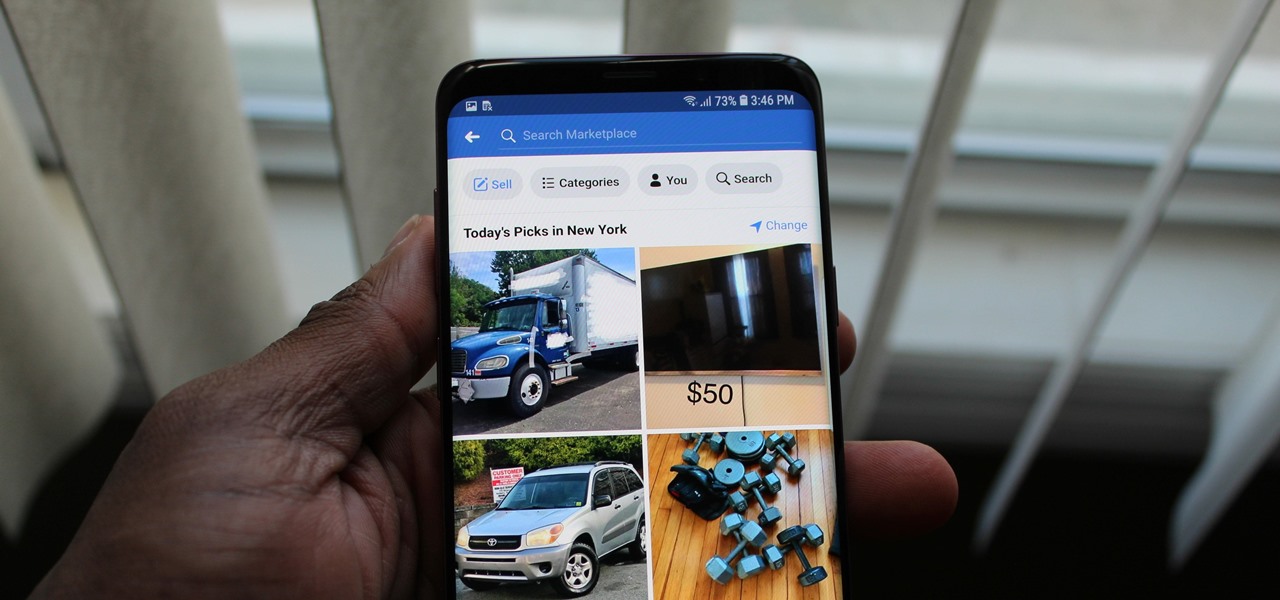
While many of Facebook's tools are well received as they enhance the experience, one which is often complained about is the Marketplace. The Craigslist-like feature which offers a way to facilitate transactions between users can be a little overbearing with its alerts. However, you can change that.

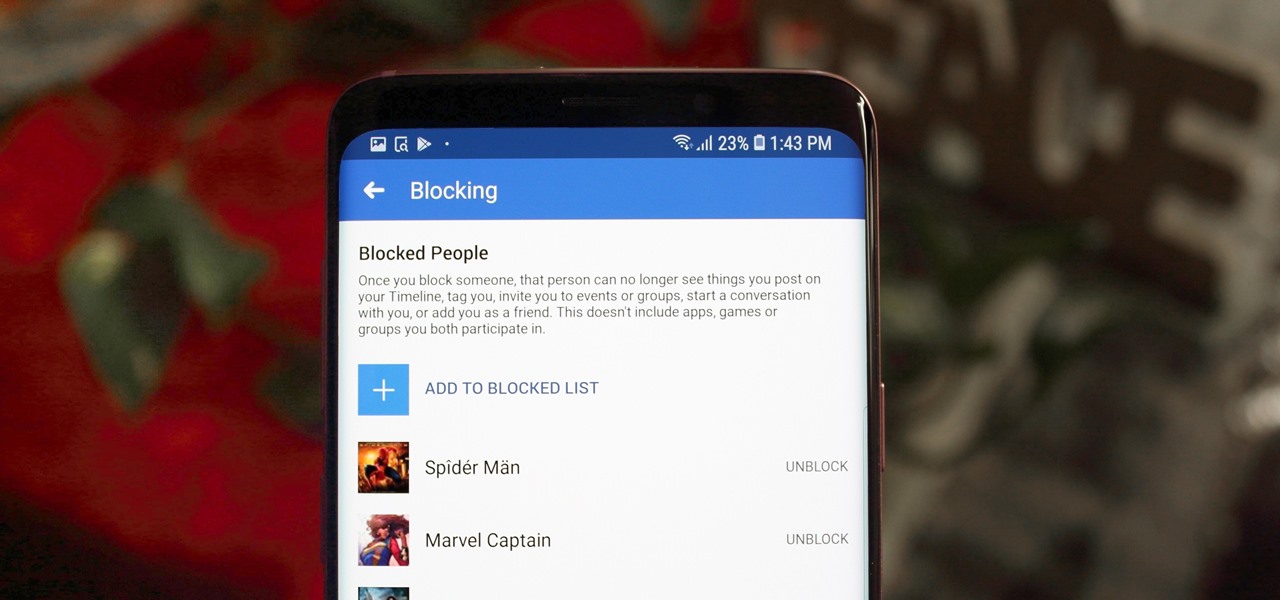
Whether it's an ex you can't stand, that annoyingly political friend of a friend, or good old fashioned trolls, the block feature on Facebook can be a great way to de-stress your feed. It will keep people from contacting you, and it will also prevent them from viewing your profile altogether. It's not just a tool for the full desktop website — in fact, the blocked list is easy to manage right from your phone.

In an ongoing effort to improve its services and become more accessible to users from all regions, Facebook has released a streamlined version of its social media app. Though the leaner Facebook Lite is only officially available in Turkey for now, there's a simple workaround you can use to get the app in any country.