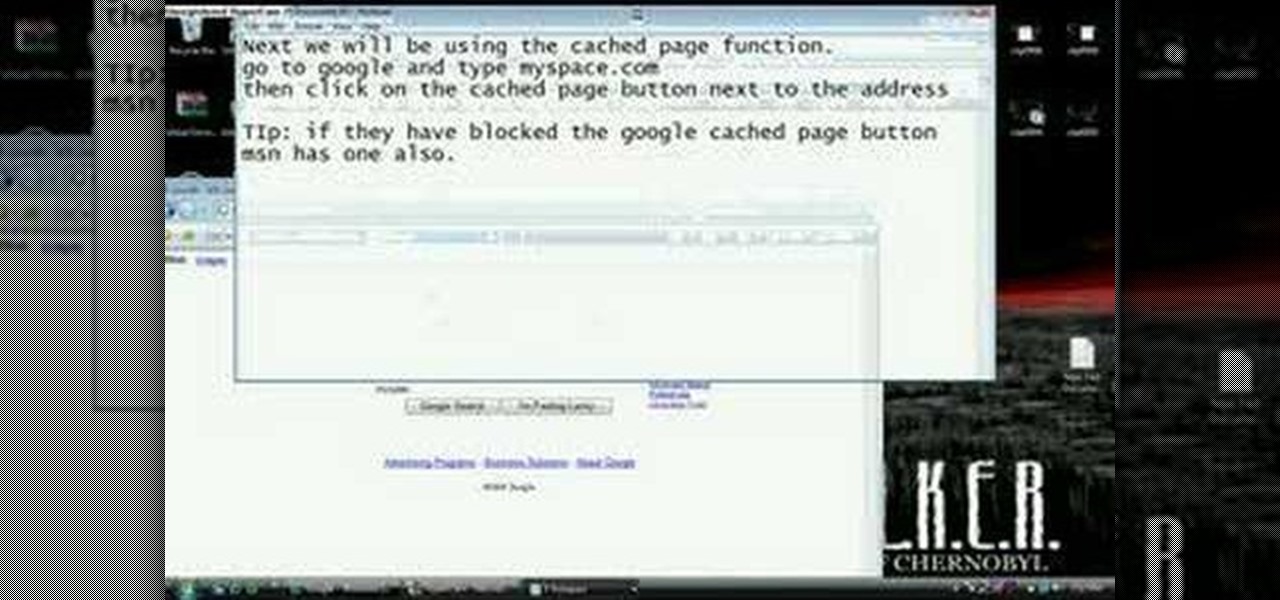
Welcome back, my budding hackers! As I have mentioned many times throughout this series, knowing a bit of digital forensics might keep you out of a lot of trouble. In addition, digital forensics is a burgeoning and high paying career. Some knowledge and certifications in this field will likely help you land a Security Engineer position or put you on the Incident Response Team at your employer.
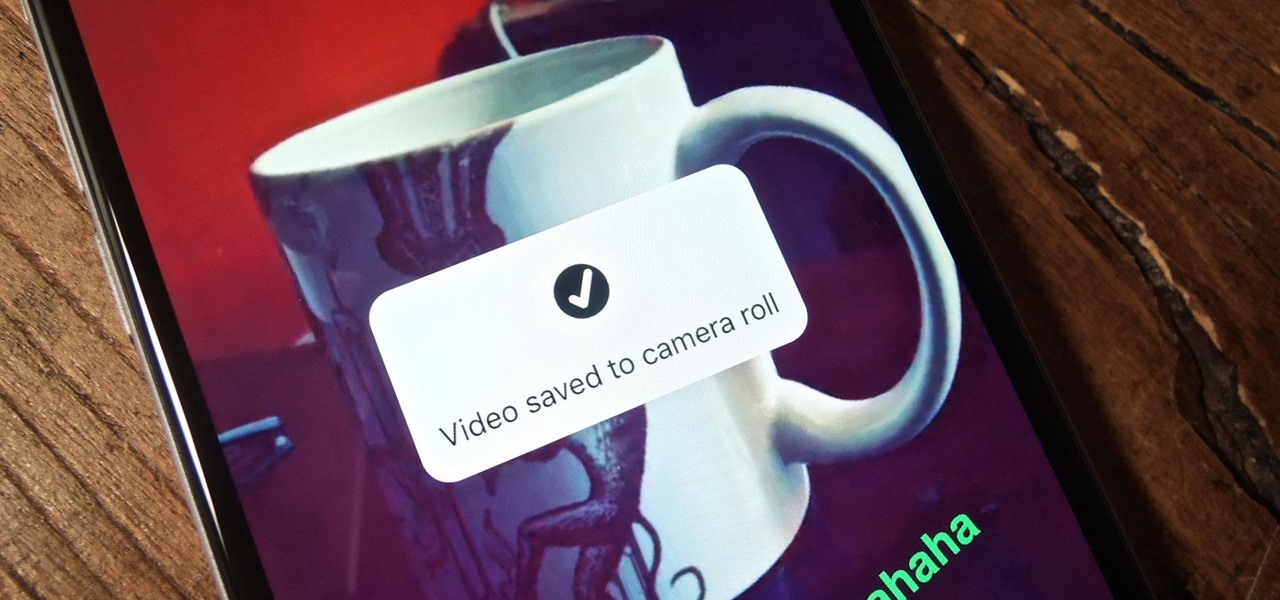
For most of us, the primary reason we capture videos on our iPhones is to post on one of the various social media platforms out there, like Facebook, Instagram, Snapchat, or Twitter, providing instant gratification by receiving a proverbial nod from our followers.

Both the Galaxy S6 and S6 Edge have had root methods available to them before the phones were even released, but the problem with these existing root methods is that they would trip the KNOX counter on your device.

Humans in general are great at keeping things about themselves private, from feelings to personality traits. While smartphones and social networks are making these secrets more open, narcissists have and always will love being out in the open with everyone's attention on them.

Welcome back, my neophyte hackers! Many newbie hackers seem to be confused regarding the process or methodology to employ a successful hack. Most want to simply go straight to the exploit without doing the due diligence to make certain that the hack will work and you won't get caught.

If you've ever searched for a new job online, chances are you've been completely overwhelmed by the process. Clicking through pages and pages of semi-relevant job postings, sending out hundreds of emailed résumés, and filling out applications is tiresome and dull.

If you haven't heard yet, Google made it possible a couple months ago for every Android user running 2.2 or higher to track his or her smartphone or tablet using their Android Device Manager service. It's a super easy way to track, lock, and secure erase your Android device from the web without ever having to download a third-party application, like Droid Finder, since it occurs in the background via Google Services.

Sometimes, doing the right thing is way more difficult than it should be, like trying to return a lost smartphone. Despite having the best intentions, it's often hard to track down the rightful owner, especially if the device is armed with a passcode. On the other hand, there are plenty of people who see an unattended iPhone or Samsung Galaxy S3 as a chance for profit. In 2011 alone, the number of lost and stolen cell phones in America was worth over 30 billion dollars. That's right, billion....

Google Reader is soon to be no more. Yesterday, the company announced that the service will be shutting down as of July 1, 2013, as part of Google's second "Spring Cleaning."

Video: . Optimize your Marketing with a Mobile Website

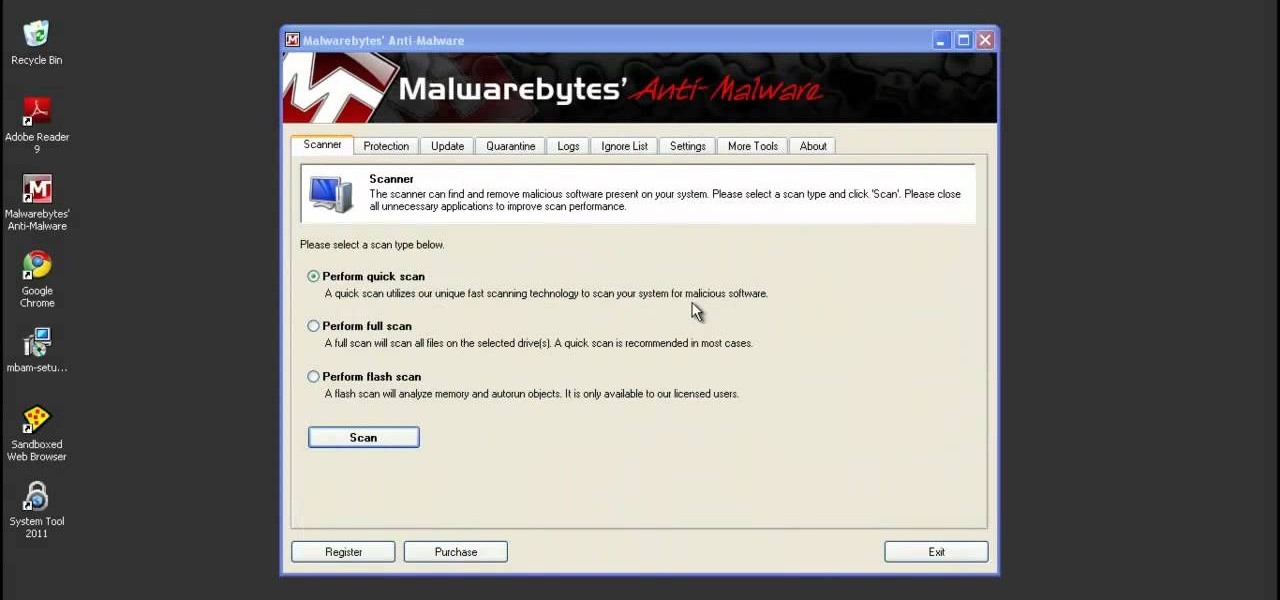
System Tool and System Tool 2011 are the most widespread fake-antivirus rogues on the internet today, infecting countless machines. This video will teach you how to uninstall both warez completely, returning your computer to blessed normalcy.

The iPad's got some stiff competition these days, especially from Android, who plans to invade the tablet market with their high-end mobile operating system. And they're off to a good start with the Samsung Galaxy Tab, available from AT&T, T-Mobile, Vodafone and Verizon Wireless, along with other carriers.

Want to know everything about your new Motorola Droid X from Verizon Wireless? This three-part video review goes through all the features of the Droid X, showing you how to use everything on the Android smartphone. It's got a 4.3-inch touchscreen and HD video capability, something a mobile phone has never had.

Ivy League schools are a students wet dream, but not everyone can get into them. Even fewer get scholarships for them. But in recent years, Ivy League universities have raised the number of scholarships they award to students. More students are seeking awards, making the application process for these scholarships very competitive.

The setting of this video is at a restaurant that was once a Czechoslovakian social club that was turned into an award winning barbecue restaurant called Honky Tonk Barbecue.

This video explains how to handle and take care of a horse. Always approach a horse quietly so that you don’t startle him. Talk to him and pet his neck. Horses are social animals and react well to being spoken to in soft soothing tones.

Jim Reppond of Coldwell Banker Bain demonstrates the way of getting postlets into Facebook. He says that by adding the postlets in your Facebook page, one can click on the link and directly go the postlets page if they are interested. He asks you to then go to the postlets page and log in using your username and password. Once inside, you can click on the 'My Postlets' tab to see your active postlets. Then chose the postlet you want to add to Facebook and click on the respective 'HOST' button...

Nowadays many schools and colleges have blocked the social community sites from accessing them through school computers. The video shows how one can access to these sites using a command prompt.

What's better than one prank? Five pranks! This video from the notorious Kipkay provides five fantastic, funny, and facile pranks to pull off on your friends and family… maybe even your enemies.

Dropping out of high school doesn’t have to mean the end of your educational career. You can earn a General Education Development diploma, also known as a GED. In this video, learn about the process needed, step-by-step, to get your GED.

Have you been noticing a small stench trailing throughout your home? Is you teen going through "changes" and you don't know how to approach them? Follow these tips to keep your home and teen smelling like roses.

We've all seen them. Those guys or girls. Walking down the street with that little flashing blue piece in their ear. Do you love the convenience of your wireless earpiece, but you hate the way it makes you look like "one of them"? Here's how to avoid coming across like a total jackass.

Many of us have had a bad haircut, so don't let it bring you down. Instead, use these tips to help improve your cut!

Steer clear from empty flattery and malicious social engineering with these tips on how to avoid a player.

Do you remember "The Heist" from episode 21? Well, the sequel is even more unfair than the original! Check out this video if you want to stump people with a trick called "The Heist II." For this trick, you need only a few simple supplies: a match, a cup, and a nickel.

There's no exact science to achieving high-school popularity. But you definitely don't have to throw half your class under the bus to get there.

Systm is the Do-It-Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. They will help you avoid pitfalls and get your project up and running fast. In this DIY episode, see how to build a firewall from a junk PC to protect networks.

Look good for your internet friends. Edit photos on social networking sites such as Facebook and Picasa as well as blogs without having to download them to your computer.

Social bookmarking sites is the way to go if you intend to increase traffic to your website or blog. If you don't know about sites like StumbleUpon or Digg, then you should watch this quick tip for information about getting more traffic to your blog via social bookmark sites.

For years, you could only make purchases with your Apple Cash balance on your iPhone using Apple Pay, but a new update gives you the power to set up a virtual card number you can use just like a debit or credit card.

You should feel relatively safe to watch and post videos on TikTok, but like with any online service, you're always at the mercy of hackers.

In the realm of social media, all roads lead to one destination: cracking the code of continuous partial attention dopamine hits. We learned this back in the days of Vine, before Twitter foolishly killed it. And I pointed my lens at the emerging trend back in 2016 when I highlighted Musical.ly for Mashable, just before it was snapped up by China's Bytedance for $1 billion and merged into what is now TikTok.

With protests springing up across America, there's a chance you may have your first interaction with law enforcement. Many demonstrators will have their phones in-hand to film the action, which, sadly, could prompt an officer to demand the device and any self-incriminating data it may contain. Before this happens, you should know there are tools at your disposal to protect your data in such situations.

With Avatar, Facebook's personalized stickers for use on its social and messaging platforms, those who aren't on Facebook or have otherwise dumped the social network may feel left out.

Over the past few months, Google has prioritized the development of its video communications products as the demand for social distancing solutions continues to increase in response to the COVID-19 pandemic.

Spreading your reach to new audiences on Instagram takes time and effort. It's not only about taking unique photos and curating an exciting feed. You should choose the time of day wisely, connect with popular brands, and take advantage of hashtags. Unfortunately, hashtags can make it seem like you're trying too hard, but you can make them invisible — in stories, at least.

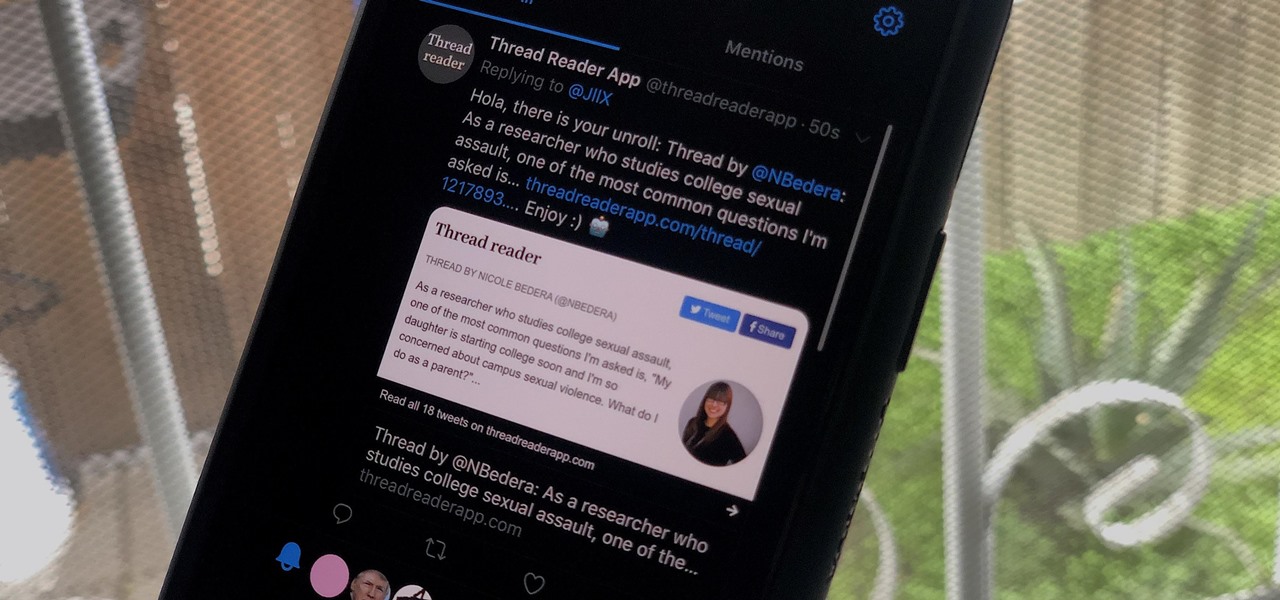
While tweetstorms were a part of Twitter since the beginning, threads, which makes tweetstorms more viable, didn't show up until late-2017. Still, threading multiple tweets at once to create long-form stories, opinions, tirades, and other lengthy Twitter posts, can be hard to digest. However, you can make reading them easier with just a single message.

It's time to make some more room at the augmented reality cosmetics counter. This week, social media giant Pinterest unveiled "Try On," a virtual make-up visualization tool running on its Lens visual search tool.

After dipping its toes into the AR cloud arena last year, Ubiquity6 is now jumping in with both feet this year.