If you're like me, then your perfect Friday night has your friends over for some group-YouTube streaming. If you're not like me, you're probably cool. But for the rest of us, YouTube is meant to be a shared experience. I think YouTube has caught on to that trend, since it has developed Uptime, an app that lets you watch YouTube with other people wherever you all are.

Facebook, you either love it or you hate it ... or maybe you're indifferent. The point is, Facebook is everywhere, and the debate is still raging over whether or not it's actually, well, good. That debate may not exist for the various personalities of Facebook much longer, however, as Facebook announced a new app geared directly towards improving how they broadcast their content to their audiences.

There is now another way for doctors to use augmented reality in operations. This time, it's for plastic surgery — Specifically facial surgery.

If you're on Instagram, you may start to see Babadook all dressed up this month. This beautiful monster is taking Instagram by storm by #babashooking it's way all around the world in its brand new Pride attire.

Online lives could be made easier now that Facebook, Instagram, and Messenger are testing merged app notifications. 'Could' being the operative word!

Now, you can prevent Donald Trump from building that idiotic wall from the comfort of your smartphone. Well, in theory, you can, thanks to a hilarious new gaming app called — wait for it — Trump's Great Wall.

The producers of FX's animated series Archer have devised a plan to introduce augmented reality hijinks into its eighth and penultimate season with a new app for iOS and Android devices.

Selfies' reign on social media and pop culture has not really lost any steam since it was declared the word of the year back in 2013. We've had the much-mocked selfie stick, and even an ill-fated TV show named after the term. So what's next? Well, if you're phone maker Oppo, you're banking on the next big selfie-thing being the dual selfie camera.

Joyce Kuo of Nijie Technology released a video showing a group fighting it out Dragon Ball Z-style in a restaurant, but instead of Goku, Piccolo or Vegeta, we have two horse-headed young ladies shooting fire and other elements at each other.

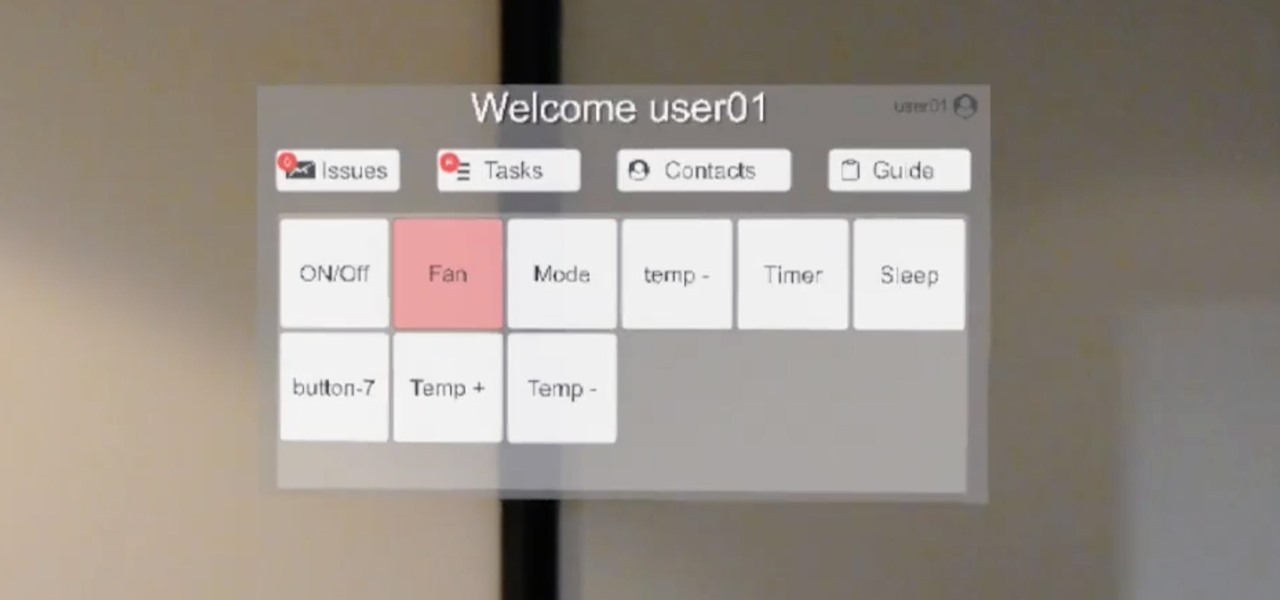
Empea Berlin, a Germany-based company specializing in augmented, mixed, and virtual reality software, released a Facebook video a few months back showing off their experiments in smart home technology. Using a Raspberry Pi and a HoloLens unit, they were able to make a virtual remote control for an air conditioning unit. The remote is complete with various modes, temperature controls, timers, and other features. There have been no updates on this project since they first showed it off, but hop...

In response to the flurry of doubtful headlines about Magic Leap today, set off by an unflattering article from The Information, Magic Leap CEO Rony Abovitz released a short blog post quickly detailing what to expect from the company over the next year. The gist comes down to this: big things are happening in 2017.

It seems like a new, dangerous Android exploit is uncovered every month or two. The latest headliners are NightMonkey and Chronos from the list of CIA hacks reported by Wikileaks, which have been billed as gaping security holes in the world's biggest mobile operating system.

Want to go to Seattle and meet the Actiongram team?

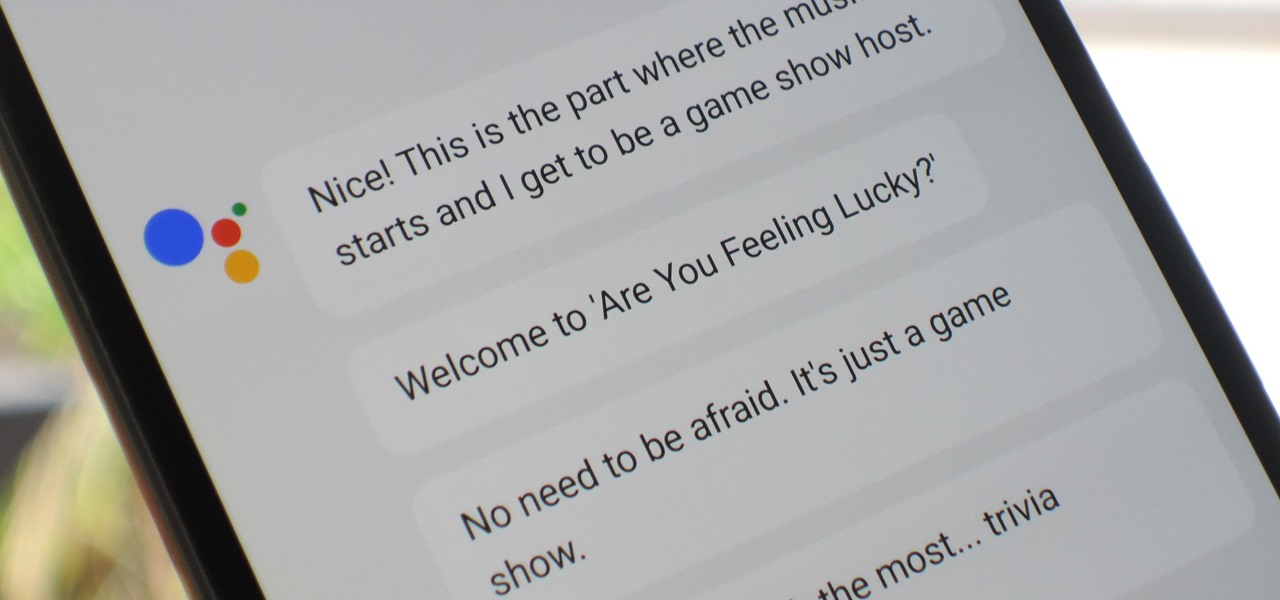
If you took your favorite search engine, gave it a witty personality, and bundled it together with a messenger-style interface, you'd have the new Google Assistant. It's great for getting fast answers—even on your follow-up questions—but its flair for fun might just be the standout feature.

This is the very first article in my series on setting up a Mac for hacking. In this series, I will be operating under the assumption that you have a clean install of macOS (previously OS X). If you aren't starting with a clean installation, there may be a few differences, but nothing we can't help you out with.

Considering how much smartphones cost in the first place, we're understandably reluctant to throw them out when we've bought a newer model. And this is probably the best practice, too, as there are many great uses for an old Android device.

One of the major criticisms of virtual reality, and much modern technology in general, is the antisocial nature it creates. But vTime wants to overcome the isolating nature of VR headsets with a virtual hangout space for you and your friends.

Instagram is the world's biggest photo-sharing site, narrowly edging out competitors like Imgur and Flickr. But unlike the competition, Instagram doesn't make it easy for users to download a full-resolution copy of any of the images hosted on their servers, as the site's main intention is to keep folks coming back and using the social media aspect of it all.

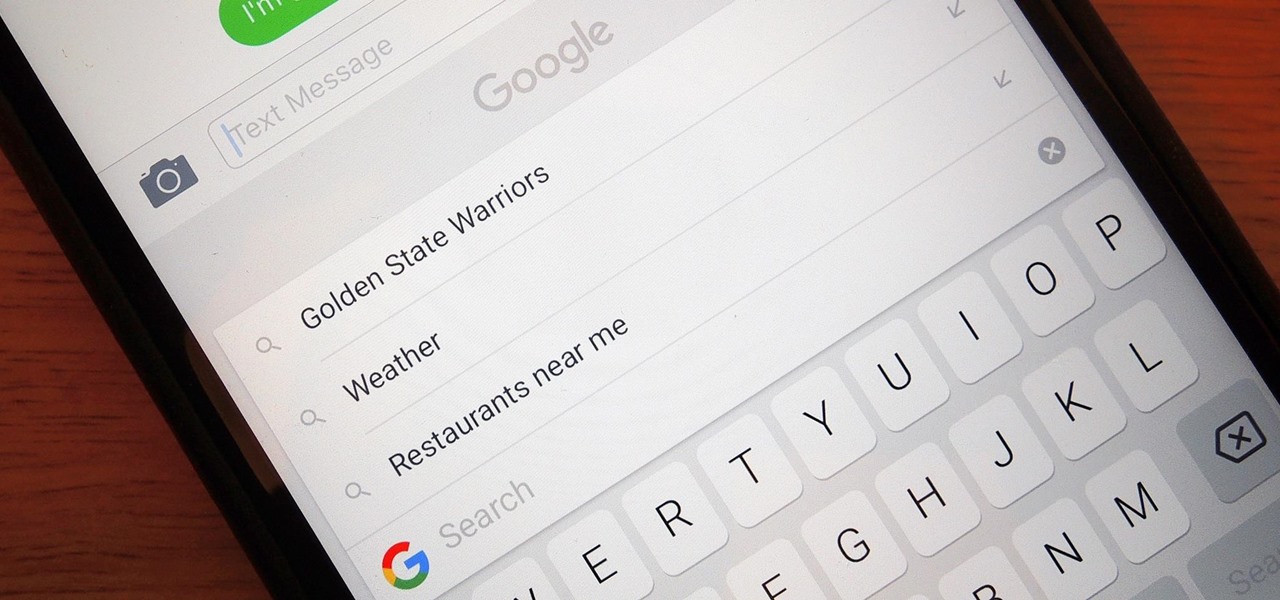
Google just made searching the web on your iPhone a whole lot easier with its new GBoard keyboard for iOS. It has a built-in Google icon so that you can search directly from whatever app you're in, making it a cinch to add images, GIFs, directions, videos, and more.

When it comes to security, Android generally takes an all-or-nothing approach—once someone has your PIN, they're free to do just about anything, up to and including wiping your device. This is why you have to be extra careful to ensure that neither strangers nor friends are looking over your shoulder while you're entering your PIN.

If you've been keeping tabs on the rumor mill for the iPhone 7, one of the most discussed elements of Apple's upcoming device is the possible elimination of the headphone jack in favor of a Lightning connection.

Welcome back, my novice hackers! As many of you know, recon is crucial to a successful hack/pentest. In most cases, hackers spend more time doing good reconnaissance than actually hacking. Without proper recon, you are simply guessing at what type of approach or exploit is going to work and, as a result, your time is wasted without any useful outcomes.

Live streaming has emerged as a major part of the way people share information. With celebrities and news/media personalities utilizing mobile live streaming effectively to reach thousands, the appeal has bolstered the fortunes of Twitter's Periscope and Facebook's Live. Now, Google is ready to join the fray, and it's backed by its enormous YouTube property. According to initial reports, Google is at work on a brand new application for YouTube simply called "Connect," which will take its curr...

3D printers have been surging in popularity for both professional and personal applications, and now OLO is on the verge of making 3D printing practical wherever you go. Their eponymous 3D printer is battery-powered and uses the light from your smartphone's screen to create 3D objects out of special "daylight" resins.

Welcome back, my tenderfoot hackers! One key area on the minds of all hackers is how to evade security devices such as an intrusion detection system (IDS) or antivirus (AV) software. This is not an issue if you create your own zero-day exploit, or capture someone else's zero-day. However, if you are using someone else's exploit or payload, such as one from Metasploit or Exploit-DB, the security devices are likely to detect it and spoil all your fun.

Welcome back, my tenderfoot hackers! Web apps are often the best vector to an organization's server/database, an entry point to their entire internal network. By definition, the web app is designed to take an input from the user and send that input back to the server or database. In this way, the attacker can send their malicious input back to the servers and network if the web app is not properly secured.

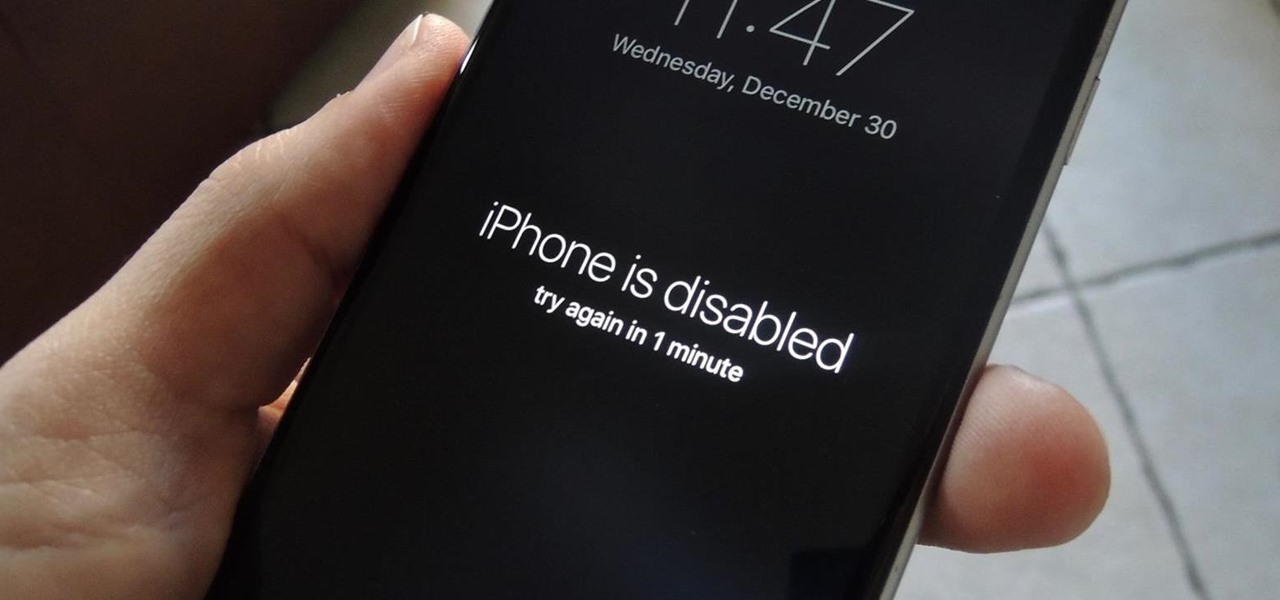
With Touch ID on iOS devices, it's a little more difficult to lock yourself out. However, it can still happen if you don't use it, have a busted fingerprint scanner, or use an older device that doesn't have Touch ID, which means you're passcode dependent (unless you have zero lock screen security).

I recently posted a Tutorial about setting up Dendroid: http://null-byte.wonderhowto.com/how-to/setup-dendroid-android-rat-0167299/. I have worked the last 5 days on getting the Dendroid Binder, given with the Dendroid Source, working. This solution only works on Windows systems!

Hey there, reader! In this tutorial we are going to explain how values are stored in variables as either signed or unsigned. Try to not get lost!

INTRODUCTION Hello dear null_byters here we go again with our third part of this serie.

Technology can move really fast. Just consider the format for which we consume videos and movies, which has transformed from film reels to VHS to DVD to Blu-ray to steaming with nothing physical at all. But for some odd reason—maybe because it strikes a nostalgic chord or it's just the new hipster trend—VHS is in again. Yes, shaky, grainy, low-quality videos with timestamps are cool again, and I dig it.
I see many people posting the same thing on the internet. "How do I become a hacker? Where do I commence?"

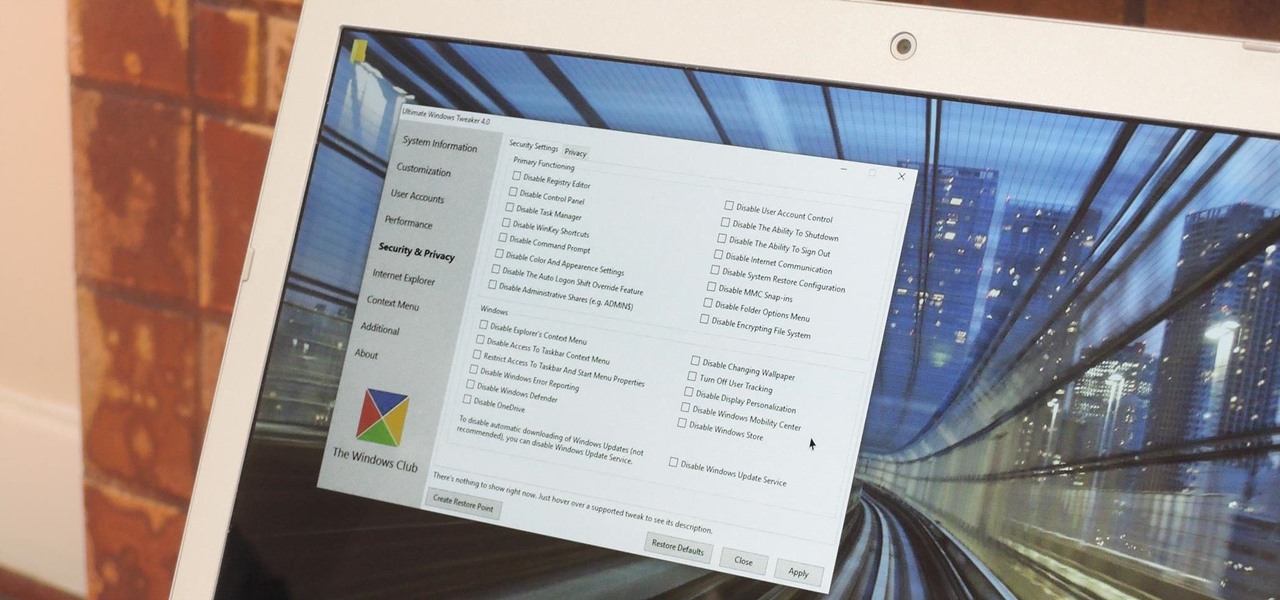
Every time Windows gets a significant update, the vast majority of existing tweaking utilities become obsolete. For every option that you fine-tuned with one of these tools on Windows 7 or 8, there's a change in the registry or system settings that cause your tweaks to now point to a dead end. This was definitely the case with Windows 10, since there were so many sweeping changes that very few existing options carried over.

Due to recent conflicts, I feel the urge to post this, in hopes that some of you will feel less hatred towards newbies, or a more respectable name, beginners.

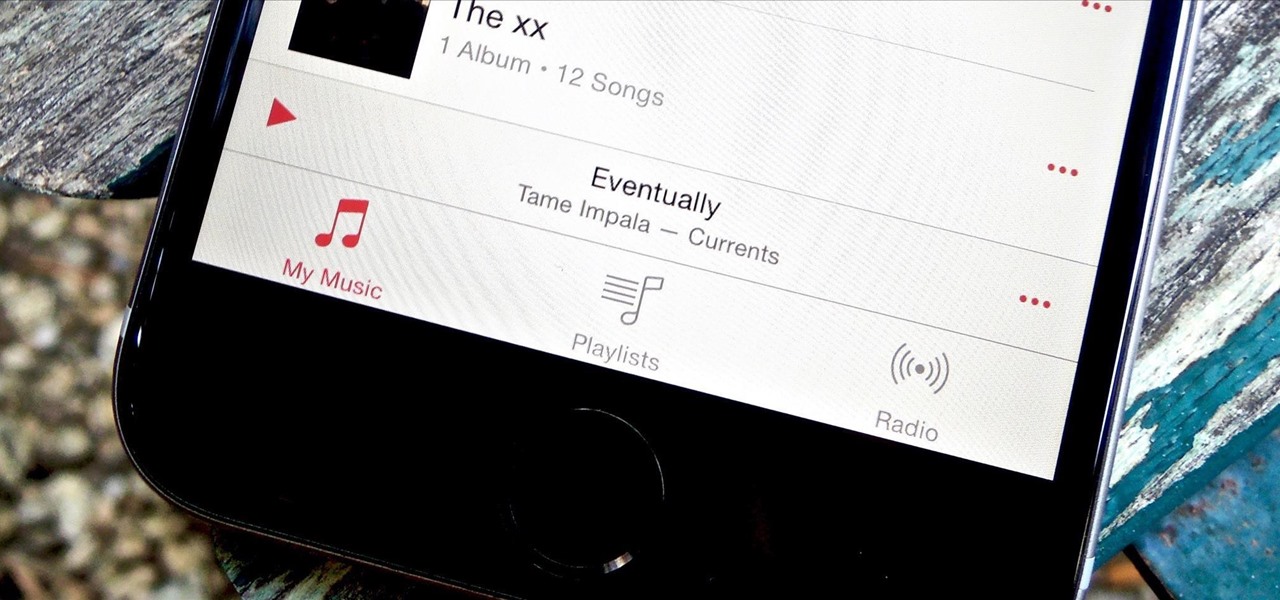
In an attempt to get more people to subscribe to Apple Music, the Music app was completely revamped in the iOS 8.4 update for iPad and iPhone to include new tabs for New, For You, and Connect.

Hi all, Pro Hackers/Crackers, Let's see how we can use batch for our own Protection instead of exploiting someone with it.

In an attempt to remain a mobile-exclusive app, Instagram doesn't let users upload photos or videos from their computer. On the Instagram web app, you can pretty much only like and comment on items in your feed, but what about all of those photos on your computer that scream #tbt?

As many of you know, I firmly believe that hacking is THE skill of the future. Although the term "hacking" often conjures up the image of a pimple-faced script kiddie in their mother's basement transfixed by a computer screen, the modern image of the hacker in 2015 is that of a professional in a modern, well-lit office, hacking and attempting to development exploits for national security purposes. As the world becomes more and more digitally-dependent and controlled, those that can find their...

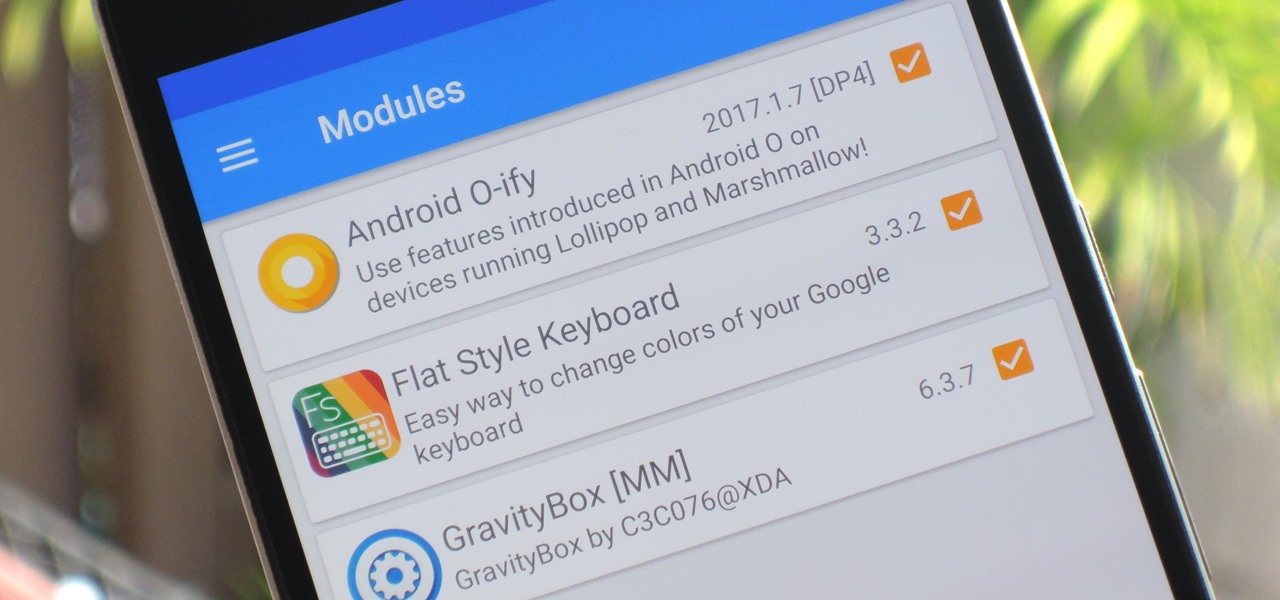
The Xposed Framework is a very powerful platform on top of which smaller modules can run to make changes to the Android system and various other apps. Installing modules is just as easy as sideloading any Android app, but afterwards, you'll need to activate the module and reboot your device.

For a number of years, I have had a vortex cannon on the top of my list of projects to attempt. Creating a sturdy cone for the barrel has always been a hurdle in the design, one I finally found a solution for in this video.