Snapchat developers insist that the app stay true to what its always been: a service for snapping and sharing self-destructing images. This belief is further hit home with their strict 31-character text limit, which some people refuse to abide by. Namely, Snapchatter Shayne Skellett.

Whether it's for handling your business's social media account or just for personal reasons, like trolling an ex-girlfriend's page (not that I've ever done that) or posting on behalf of your pup, there are instances where having two different Facebook accounts on one device is simply easier than switching back and forth.

Yesterday, April 7th, it was revealed that the United States White House had been hacked by allegedly Russian hackers. According to reports, the Russian hackers used social engineering/phishing to get a foothold in the U.S. State Department and then pivoted from that system/network to the White House. Although the White House said no confidential information was compromised, the President's appointment calendar and other information were. Attribution or "blame" for the hack was made more diff...

While you may not have loads of secret files hiding on your computer, there might be one or two items that need a little extra security, like a file of website logins or a folder of risqué photos.
If you've had your Gmail account for awhile, it's probably a cluttered mess thanks to unread messages, out-of-control newsletters, and never-ending email threads. This is one of the main reasons for the creation of Google's streamlined Inbox service, but the adoption rate for it hasn't indicated a huge shift over for most of us yet (partly because it's invite-only still).
Technology allows us to communicate with others like never before, providing us with the ability to stay connected with past and current coworkers, classmates from high school, and even relatives in far-away countries.

Welcome back, my hacker novitiates! Eluding and evading antivirus software and intrusion detection systems is one of the most critical tasks of the hacker. As soon as a new exploit is developed and discovered, the AV and IDS developers build a signature for the attack, which is then likely to be detected and prevented.

With over 1.5 billion people on this planet without electricity, it's hard for those of us in developed nations to even fathom how anyone can read, write, repair, or do anything else that we take for granted without any lights. While some of our First World problems pale in comparison, they remain issues nonetheless, one of the biggest being constant battery drain from portable electronics.

If there was anything missing from the notorious YO app, it was Aaron Paul's character from Breaking Bad, Jesse Pinkman, calling me by his signature catch phrase—you know the one.

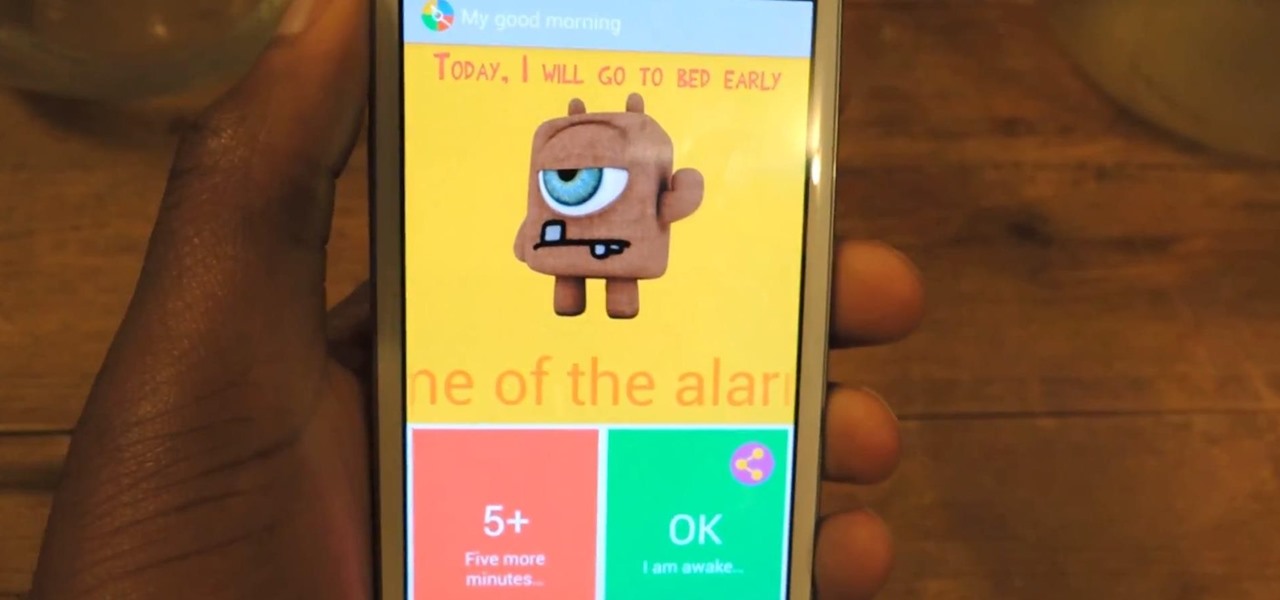
Lock screen notifications can sometimes be overwhelming and difficult to manage, especially in the morning when I receive a massive influx of emails, texts, reminders, and social media alerts. At some point it's not even worth scrolling through all of them on your lock screen when you can get a better grasp of everything by just checking out the Notification Center instead.

Welcome back, my tenderfoot hackers! Those of you who have been reading my posts here for awhile know how much I emphasize good reconnaissance. Novice hackers often jump into a hack/exploit without doing proper recon and either fail or get caught. Experienced and expert hackers know that 70-80 percent of a good and successful hack is dependent upon successful and accurate reconnaissance.

As competition for Spotify and Pandora, Samsung released Milk Music earlier in 2014, a free music streaming service for their Android devices. While Milk was unique to Galaxy owners only, it was popular enough that we showed you ways to get it on non-Galaxy devices as well.

When it comes to subscription-based music streaming services, the conversation doesn't go much further than Spotify and Google Play Music (previously called "All Access"). Both services are essentially the same aside from slightly different catalogues and social options, and they both run ten bucks a month for unlimited music streaming and offline track saving (although Spotify does have a free, ad-supported service).

Welcome back, my novice hackers! New hackers often ask me the same question: "What is the easiest platform to hack?" My response is always the same—it is not a platform, but rather a particular piece of software that is easiest to hack, which is on nearly every client-side system. That software is Adobe Flash Player.

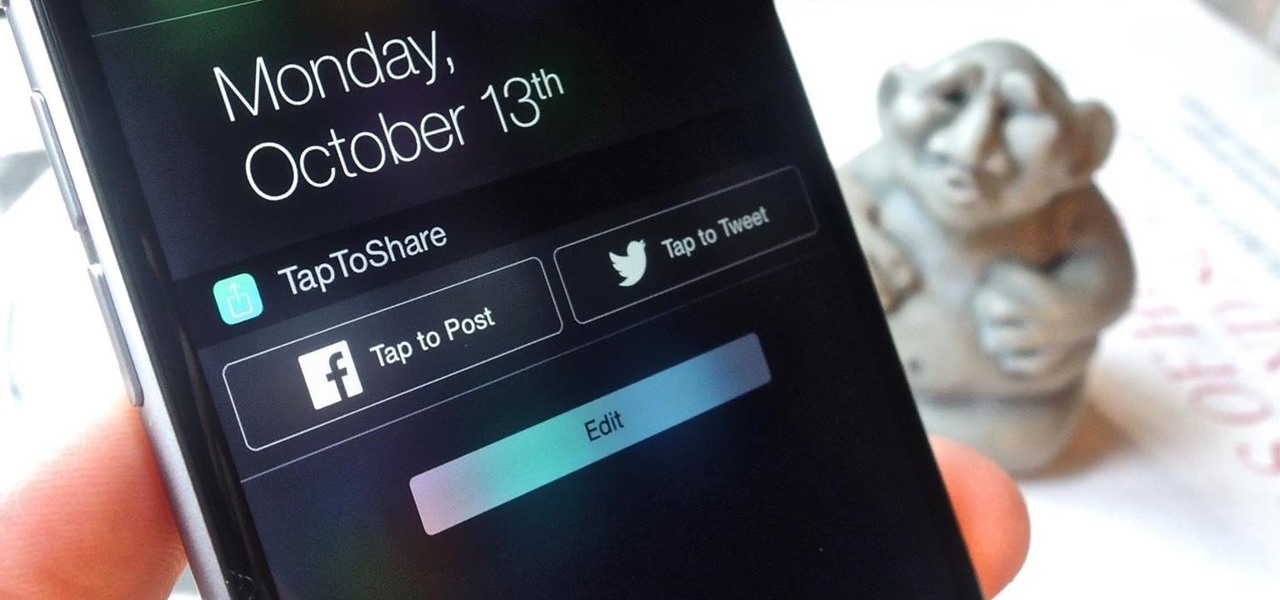
Back in the days of iOS 6, iPhone users were able to send a quick tweet from their notification center, but that has long since been removed. This convenient feature was missed enough on iOS 7 for devs to create a jailbreak tweak in its absence. Thankfully, due to the new widget capabilities of iOS 8, we can have Twitter back in the Notification Center along with Facebook.

Welcome back, my hacker novitiates! Every so often, a MAJOR vulnerability appears that makes millions of systems vulnerable to attack. The most recent, named Shellshock, basically leaves every Mac OS X, Linux, and UNIX system on the planet vulnerable. As nearly two-thirds of all web servers on planet Earth run one of these operating systems (primarily Linux), that's a whole lot of systems out there waiting to be harvested.

Welcome back, my amateur hackers! Many of you here are new to hacking. If so, I strongly recommend that each of you set up a "laboratory" to practice your hacks. Just like any discipline, you need to practice, practice, and practice some more before you take it out to the real world.

There are a gazillion app switchers on the market, and some are really awesome, like Edge, GloveBox, Loopr, and Switchr, to name just a few. However, these can all be a little bit more complicated and cumbersome than necessary when I just want to switch back to the last app I was in.

There will always be a time when you're not entirely sure what you're doing with a certain subject. But the days of weighing the pros and cons yourself are coming to an end. Whether it's a common quandary like "Where should we eat?", or a more specific question along the lines of "Should I buy this shirt or not?", you can now simply AskInternets.

Security is a priority for many when they first set up their mobile devices. Nobody wants to have a stranger or nosey friend go through their phone and discover risqué photos or embarrassing text messages. These days, the closet is gone—everyone keeps their skeletons in their phones.

Aside from the most basic functions, most of us are pretty useless when it comes to Photoshop. Yes, we can all add filters, but who wants to see everything in black-and-white or sepia? Why not change a sunflower blue, your hair pink, or your lips purple—without having to spend hours with editing software.

Welcome back, my novice hackers! In a recent tutorial, I showed you how to use shikata_ga_nai to change the signature of a payload to evade detection by security devices (firewalls, IDS, etc.) and AV software.

Welcome back, my rookie hackers! Most often, the professional hacker is seeking protected information from the target system or network. This might be credit card numbers, personally identifiable information, or intellectual property (formulas, plans, blueprints, designs, etc.). Most of my Null Byte guides have been focused on getting into the system, but this only begs the question—"what do I do when I get there?"

Gaining major consumer support and the ire of Big Cable, Aereo today announced support for the Chromecast through it's Android app. A revolution for cord-cutters, Aereo lets you record and stream live broadcast TV on your computer, smartphone, tablet, or media streaming player (Apple TV, Roku, and now Chromecast).

LG's arsenal of screen-off and screen-on tap gestures recently expanded into lock screen territory. Dubbed "Knock Code", this feature allows owners of various LG phones, like the G2 and upcoming G3 to unlock their phone with a series of taps on the screen. The most impressive part is that the screen doesn't even need to be on!

Twitter found a sweet spot with its 160-character limit, but Snapchat sports a social media low of 31 characters, forcing us to condense our ideas into a few short words when typing in picture captions because of their ephemeral nature. While this severely limited amount of words is Snapchat etiquette, I've got so much more to say than 31 characters!

Once you unlock your bootloader and root, you're left with one more hurdle to overcome, and that's getting S-Off.

If you are using the the AT&T variant of the HTC One, you are well aware that the carrier opted not have the HTC Backup app pre-installed on the device. Luckily for us, HTC said "screw it" and put the app on Google Play, allowing anyone with an HTC One, regardless of carrier, to be able to download and use the app—if you're an AT&T customer, grab the app and let's take a quick walkthrough (again, the rest of us on other carriers should have the app already).

The movie Her is getting a lot of love from viewers and critics alike. While I find it kind of creepy to fall in love with a computer program, if Scarlett Johansson talked to me every day, I'd probably fall in love too.

This is how I made my smartphone camera stand using everyday items laying around in my garage. This is also a great rainy day project for anyone who uses a smartphone for their youtube or social media videos. It cost me almost nothing to build since I already had most of the items. This is a great project for anyone looking to start out on since it is really simple. It literally took me only 10 minutes to build.

Air New Zealand is looking for a spokesperson for the Antarctica: No Ordinary Place, No Ordinary Assignment project, a two-week adventure in Antarctica, where the chosen candidate will join National Geographic photographer Jason Edwards to document environmental issues and important research being conducted by research teams sponsored by Air New Zealand and Antarctica New Zealand.

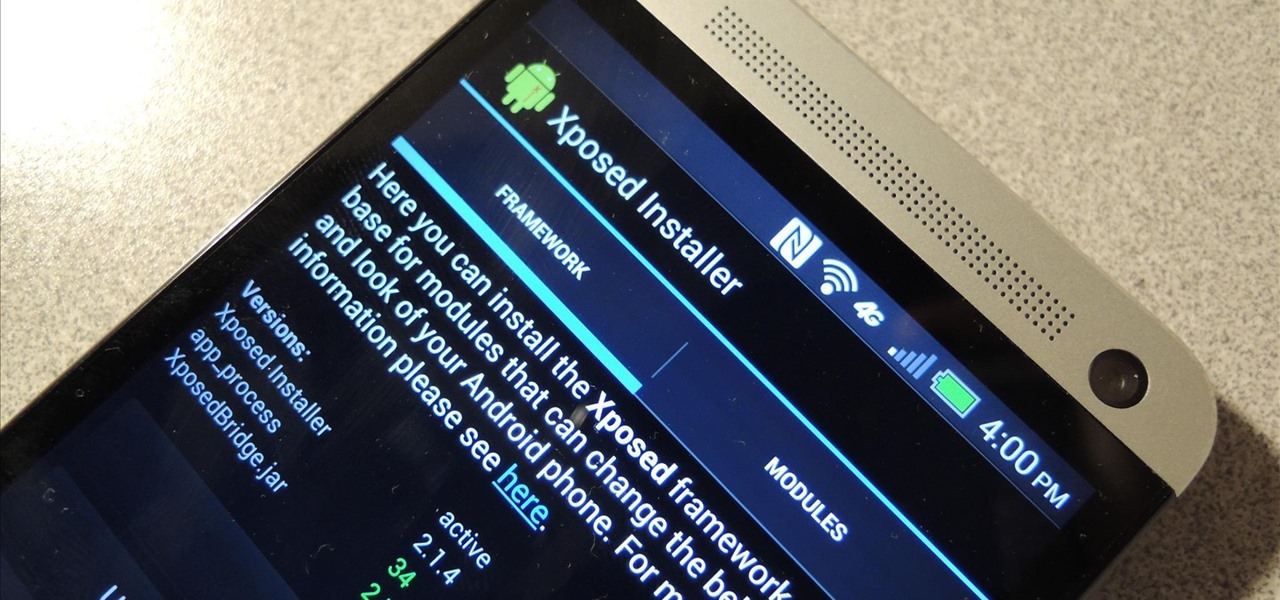
Update: The installation process for Xposed Installer is now dead simple—check out our updated guide!

Nine times out of ten, when you pick up your Samsung Galaxy Note 2, you already know what app you're going to be using. If you only have Swipe to unlock enabled, finding that app is as easy as swiping and locating the app on your Home screen or in the app drawer.

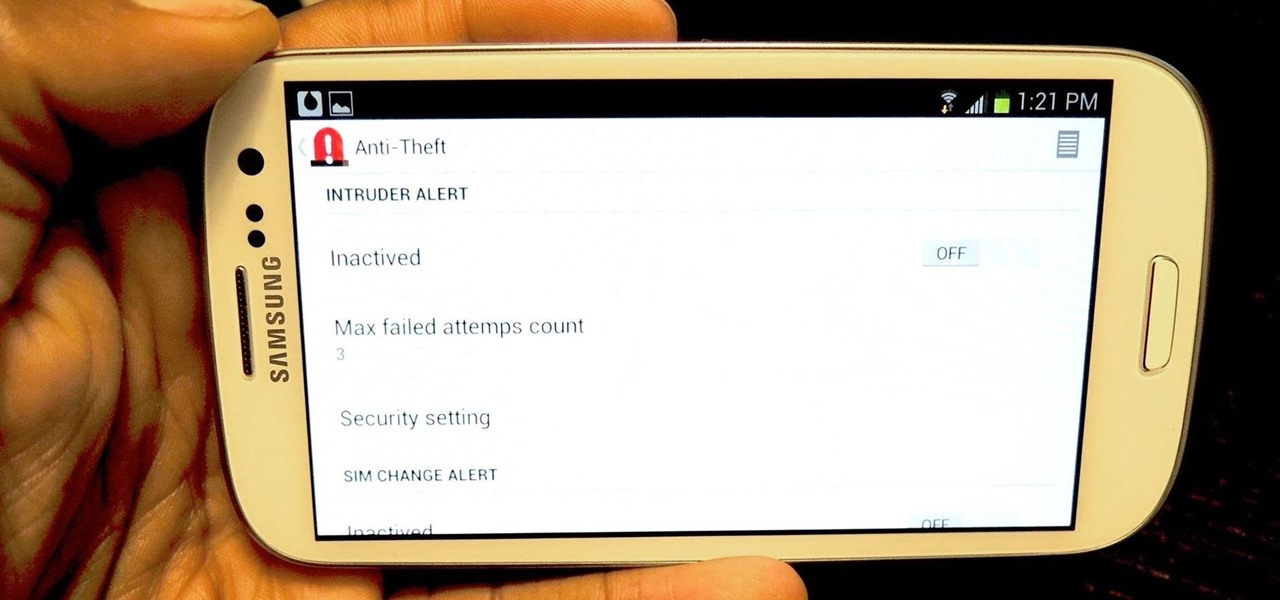
I love surprises. Surprise parties, surprise visits, surprise Patrick... But there are times when a surprise is the last thing you want, like reaching into your pocket to find that your Samsung Galaxy S3 is not where it should be.

Welcome back, my nascent Hackers! In my last blog, we looked at a passive way to gather information necessary for a hack. The advantage of using passive recon is that it's totally undetectable, meaning that the target never knows you're scouting them and you leave no tracks. The disadvantage, of course, is that it's limited to only some websites and not entirely reliable.

Welcome back, my hacker novitiates! Many of you have written me that you're having difficulty installing and running Metasploit on a variety of platforms. No matter if you're using Mac, Linux, or Windows, I strongly recommend you install BackTrack as your secondary OS, a virtaulization system, or on an external drive. This particular Linux distribution has many hacking and security tools integrated—including Metasploit.

While the phenomena of viral videos and internet celebrities are relatively new, it seems like there's a new one every other day. Sometimes they're funny, other times they have a social mission, like Kony 2012, and sometimes they're just videos of cats jumping in boxes.

Legal Services A group of lawyers refused to provide legal services to needy AARP members for $30 per hour, but when asked to do it for free, they readily agreed.

Having to read a bunch of articles and tweets everyday can be tiresome, but if you can have a sweet-ass personal assistant read them for you, you're pretty golden.

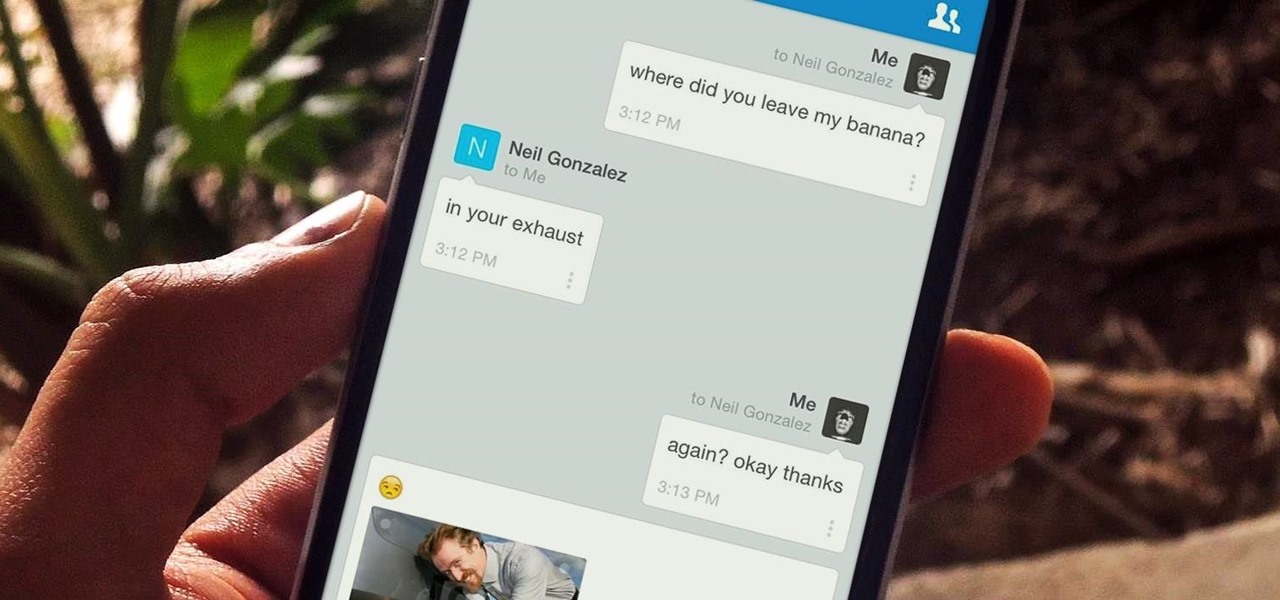
Who doesn't hate Auto Correct? There's nothing worse than hitting 'Send' only to realize that your phone betrayed you by changing a word so that your message doesn't even mean the same thing anymore—especially when it's going to someone like your boss or parents.