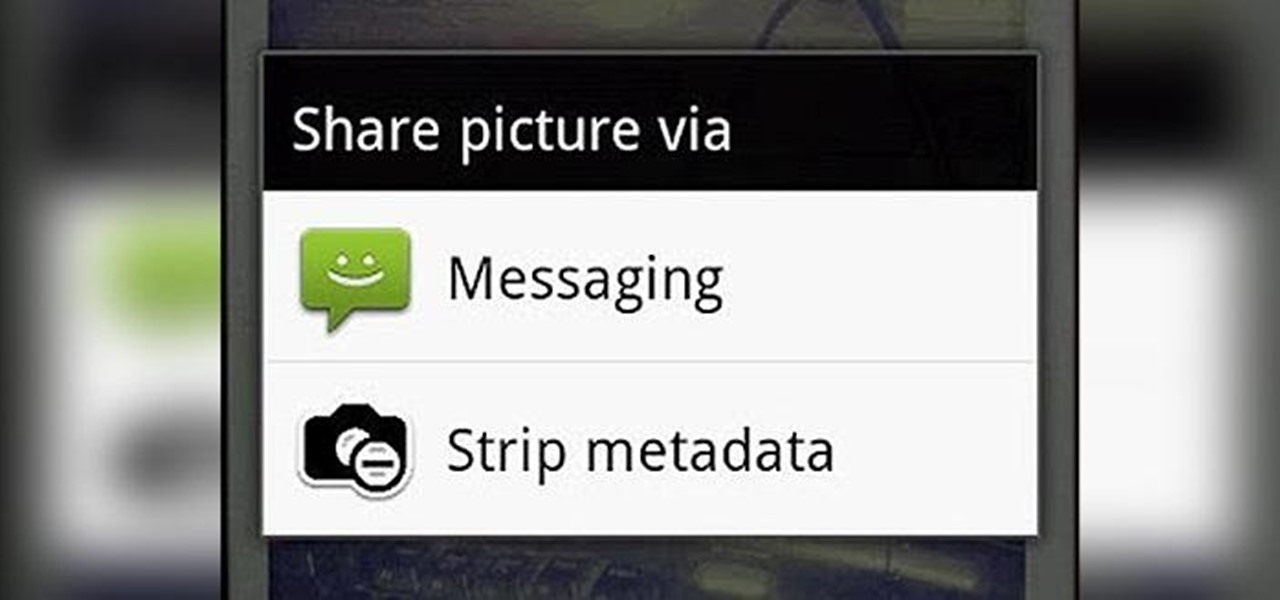
We've talked before about EXIF data—or metadata—attached to photos and how it can expose information about your location, what type of device you're using, and even the device or camera's unique identification number.

I can certainly say that I don't like be ignored, and you're probably right there with me on that. Also, if you're like me, you don't like being blocked on an instant messenger, either. There's something about being shafted like that that can really cramp your style.
Playlists are a great way to organize and share groups of videos on YouTube. Playlists can consist of your videos, someone else's videos, or a combination of the two.
Instagram's controversial terms of service update this past month has spurred an onslaught of dismay and anger from users of the popular photo-sharing social network. The specific set of the new terms that set off this firestorm basically said that businesses could use your uploaded photos for advertisement, without you receiving any of the profit.

Before lead was removed from gasoline, lead from car exhaust got into the air, was breathed in by kids, lowered their IQs, and increased crime rates (there is a very strong correlation between IQ and criminal behavior).

It's been a rough week for Instagram. First they came out with a new terms of service that suggested the right to let companies use people's photos for advertisements without the user's permission. Then everyone started freaking out and debating whether or not to leave the online photo-sharing and social networking service. Now, they've changed the controversial wording saying that the selling of user photos "is not true and it is our mistake that this language is confusing".

Apps are now very much integrated with social media, especially with your Facebook profile. Pretty much every app these days lets you log in using Facebook, while some actually force you to, giving you no other option. But, the most annoying part is that these apps leave notifications all over your Facebook timeline, cluttering the hell out of it. So, how can you completely banish all of these apps from being able to access your Facebook?

Last week, Instagram stopped supporting media Cards on Twitter, meaning that in order to view a full photo shared in a tweet, you have to click through to Instagram rather than seeing it on your Twitter feed. Otherwise, the photo will appear to be cropped.

So you've learned all of the dance moves to Gangnam Style and made your very own papercraft version of PSY that dances whenever you want him to. Now it's time to take your obsession a step further—by making yourself the star of the Gangnam Style music video. JibJab, the custom e-card site, has created a free tool that lets you use any photo to replace PSY's face with yours (or whoever you choose), then share the video with your friends.

With the Samsung Galaxy S III being a hot commodity, it's no surprise that your friends might try unlocking your fancy password-protected phone. While some friends have good intentions when using your phone, there are those certain friends who get into the phone to do this... The worst scenario might be that you leave the phone around a group of friends, come back and find that all of your social media accounts have been hacked. When you yell out to your friends asking who did it, no one make...

When subjects are asked to watch a movie and not display emotions (say, a comedy without laughing, or a tearjerker without crying), they evidently use up glucose in particular areas of their brain in a way that subjects who are free to react however they want do not.

Ever been halfway to work or school and suddenly remembered you forgot to log off your computer? A lot of people are constantly logged in to email and social media accounts, so if you have a mischievous roommate or sibling, this situation could be disastrous. That's where TweetMyPC comes in—it's a free Windows application that lets you send commands to your computer just by tweeting. Image by Twittermania

Outdoor lighting is an important part of your landscape. It's serves multiple purposes, but wouldn't you want to make sure you're getting the right lights, for both daytime and nighttime use? Lowe's has the answers to help you plan and install outdoor lighting in your yard.

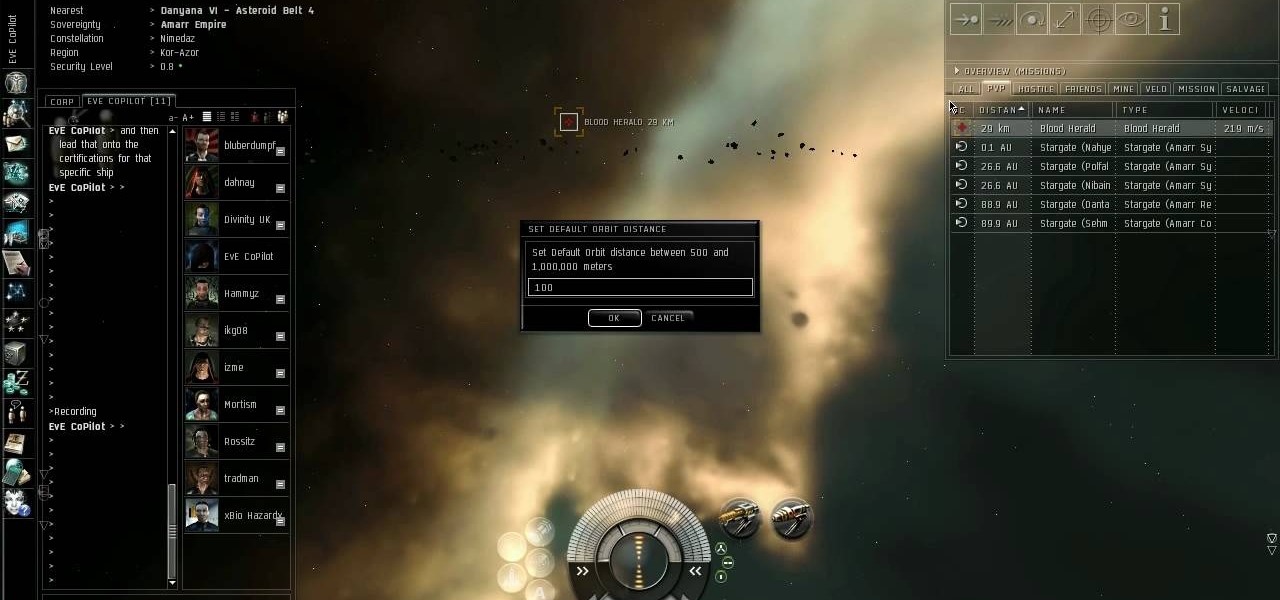
Quickly turn a profit during a combat mission by ratting - killing NPC enemies who spawn in asteroid belts. The difficulty of rats depends on how secure your system is - the lower security, the harder the rats are to kill. This tutorial shows you the best way, as a new player, to earn money by ratting.

In order to set up a secure wireless router, you will need to use the security that is available with your wireless routing. You will need to change the default ID names and password on your computer. Try to make sure that your passwords are difficult. Also, turn on the encryption: e.g. WEP.

You don't want anybody to have access to your cell phone. Nobody. Well, instead of the standard unlock mechanism, the one anybody can unlock your cell phone with, the Motorola DROID, and Android enable mobile device, allows you to create your own unlock pattern, secret to anyone else, which wakes it from sleep mode. Best Buy has answers. The Best Buy Mobile team explains how simple it is to set up a secure lock on a Motorola DROID cell phone.

This video tutorial from agseo presents how to unlock applications in Facebook social internet network. For more detailed information go to www.agseo.blogspot.comTo unblock Farmwille and other applications on Facebook social network login to your Facebook account.From top menu Account drop-down list select Privacy Settings.Then select Applications and Website from the newly opened window.Select Blocked Applications (click on Edit Blocked Applications button).A list of all blocked applications...

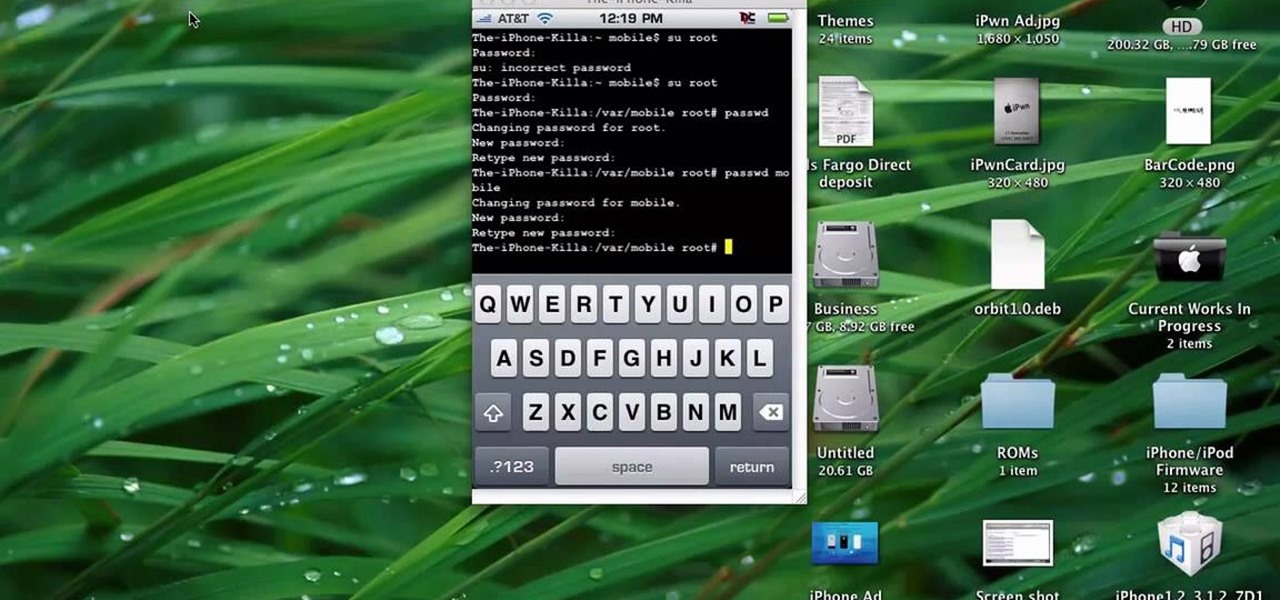
This quick tutorial runs you through a fast and easy way to make your iPhone or iPod Touch more secure. However the best security is abstinence. Just don't run the programs that leave your devices vulnerable unless you need them.

Make your way through The Saboteur for the Xbox 360. In the eighth mission in Act 1: Doppelganger, the ambassador will rendezvous with a German official near the Place des Vosges. Security will be tight around the ground level, but you should be able to find a vantage point among the rooftops. For more info, watch the whole gameplay.

So you want to party with celebrities. Whatever you do, don’t cry. You won’t just look silly—you’ll look unstable. Follow these steps to get you one step closer to hanging with the stars.

New to Windows? No problem... here's a beginner's video tutorial that will teach you how to prevent cut, paste, copy, and delete on Windows files.

Check out this 2 part walkthrough of RE 5 Chapter 2-3 Savanna. This Resident Evil 5 Walkthrough is being played on Veterans Difficulty in Co-Op mode with Chris Redfield being played by Reule and Sheva Alomar being played by RavenVanHelsing.

Resident Evil 5 (RE 5) is the sequel to 2005's Resident Evil 4. This game guide shows you BSAA emblem locations, treasures, and includes strategies for all 6 missions and boss fights.

Check out this walkthrough of Residential Evil 5, Chapter 6-2: Main Deck. Resident Evil 5 (RE 5) is the sequel to 2005's Resident Evil 4. This game guide shows you BSAA emblem locations, treasures, and includes strategies for all 6 missions and boss fights.

Last weekend, some unlucky Gmail users inadvertently had their email accounts wiped out. Actually, it was 0.02 percent of all Gmail users—or roughly 40,000 of the 200 million who use the email service, due to an "unexpected bug" which affected copies of the data. Gmail does make backup files of everything, so eventually everyone will reclaim their email history. In fact, as of yesterday, Google has successfully restored all information from their backup tapes and has started returning everyon...

Breaking into a low-security lock is easy (and thus, why it's the subject of a googolplex number of Youtube tutorials made by mischievous prepubescent boys). But add a combination number to a lock and your lock-picking life gets much harder.

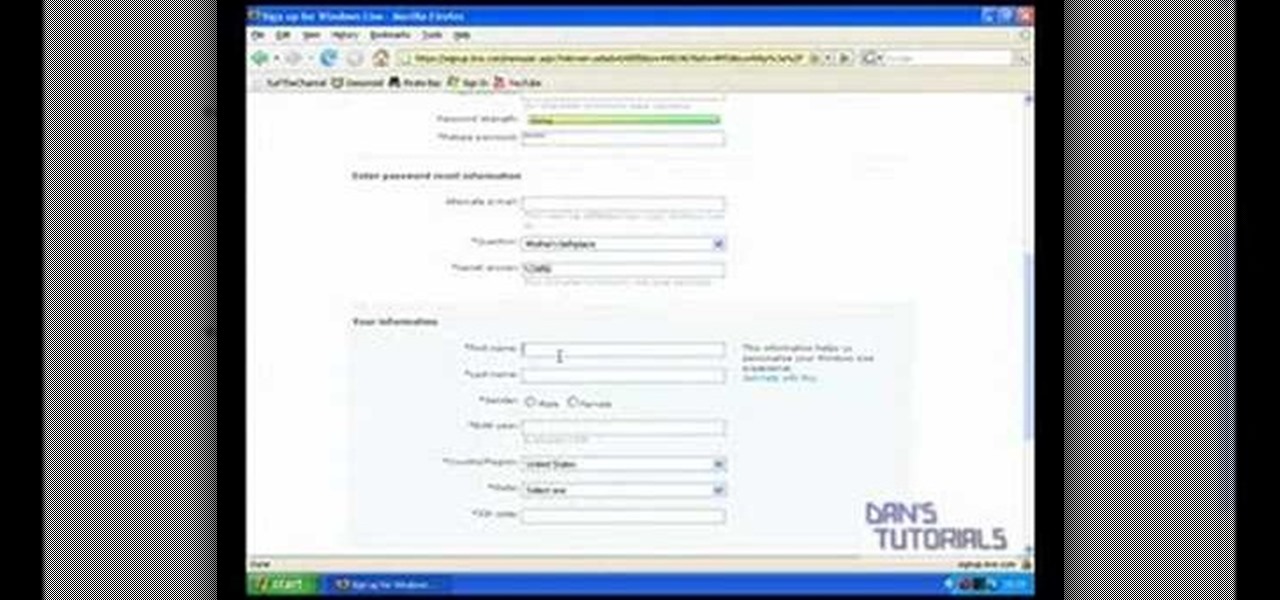
This tutorial shows how to create an email account in Windows Live. Use Google search to find the Windows Live Hotmail page. When you get to that page, click on the button that says, "Get it Free". On the next page, you can choose your email address, ending with either @live.com or @hotmail.com. If the email address is already in use, pick something else or add some numbers. Next, choose a password. There is a bar that shows how strong your password is. You can set a security question that ca...

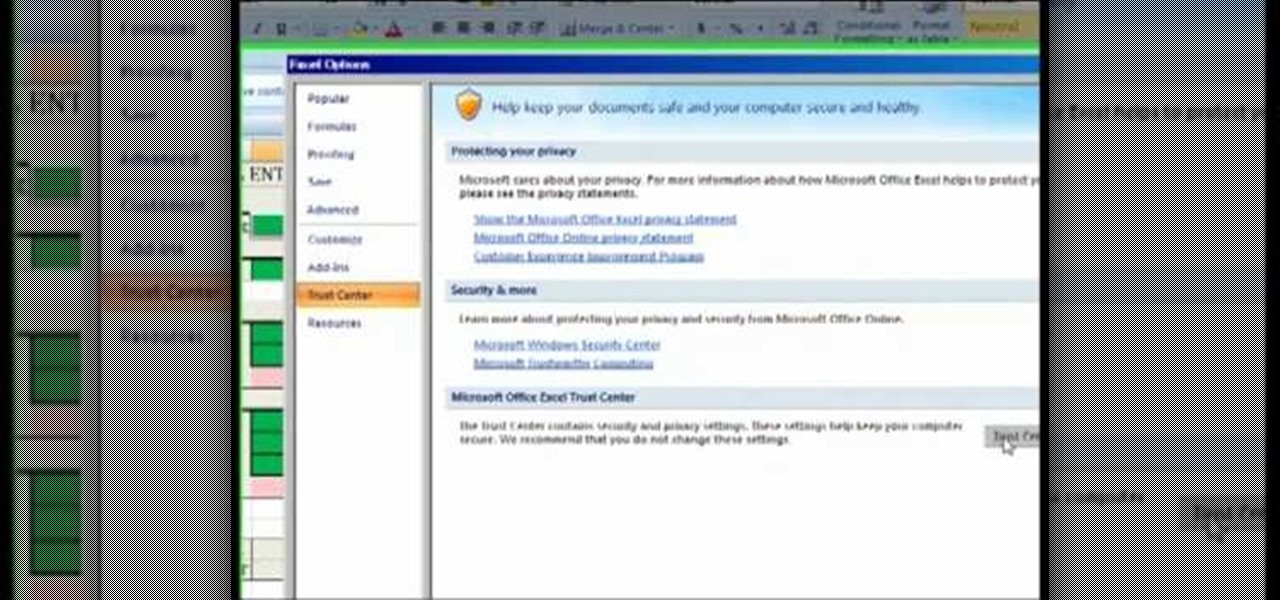
The Costsheet demonstrates how to enable macros in Excel 2007 to run correct spreadsheets. First, open up the spreadsheet. Make sure that the macros are enabled. If they have not, enable the macros by placing them in a trusted source by saving them in a particular folder. You can also choose to recognize the publisher as a trusted source. Click the office button and scroll down to Excel options. Click on the trust center option and go to trust center settings. Then, view the trusted locations...

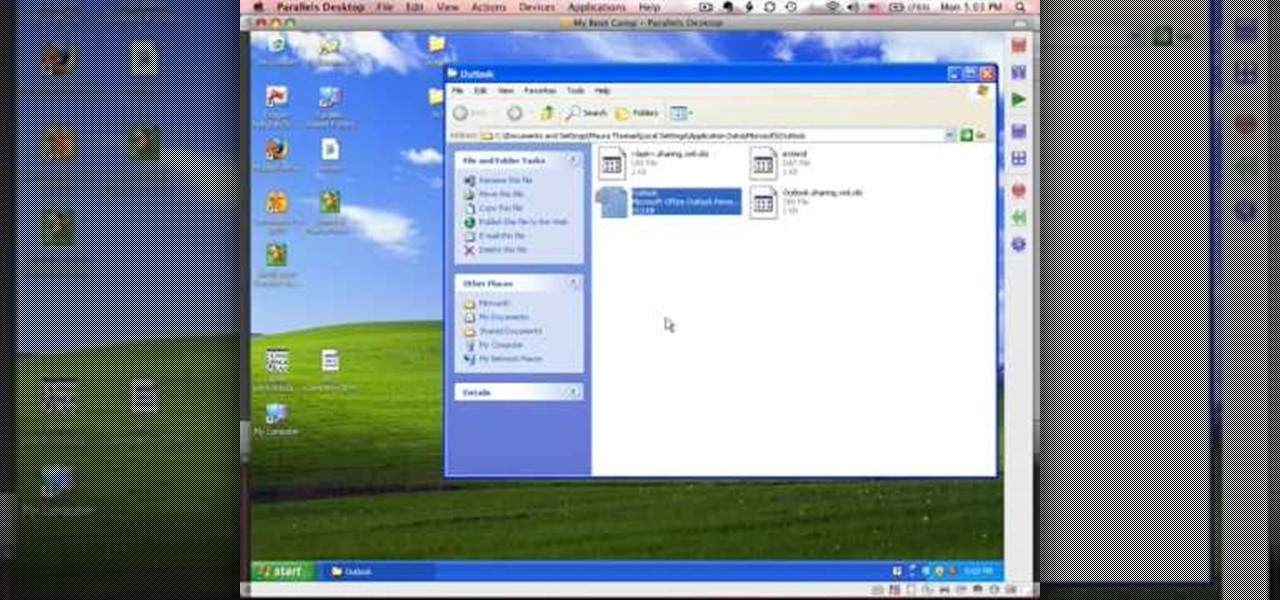
This tutorial describes how to backup the PST file of Outlook.

Whatever your reasons for doing it, if you are trying to hack passwords, it helps to have the right software for getting the job done. With the Cain and Abel program, you will be well on your way to hacking even the toughest personal passwords.

In this video the girls of Sugar Walk Catwalk dot com teach us how to walk in high heels. First you need to find the right heels, and there are three points you want to look for. First the fit of the arch. Second, that the ball of your foot is secured in the bottom. And, thirdly, test the heel balance. If the heels aren't working for you in the store, it's only going to get worse in real life! Once you've got a pair of shoes, we're shown how to make them better with foot petals or gel pads to...

This is a video that teaches you how to connect a Nintendo DSi to the internet. In order to connect a Nintendo DSi to the internet, you have to do this.

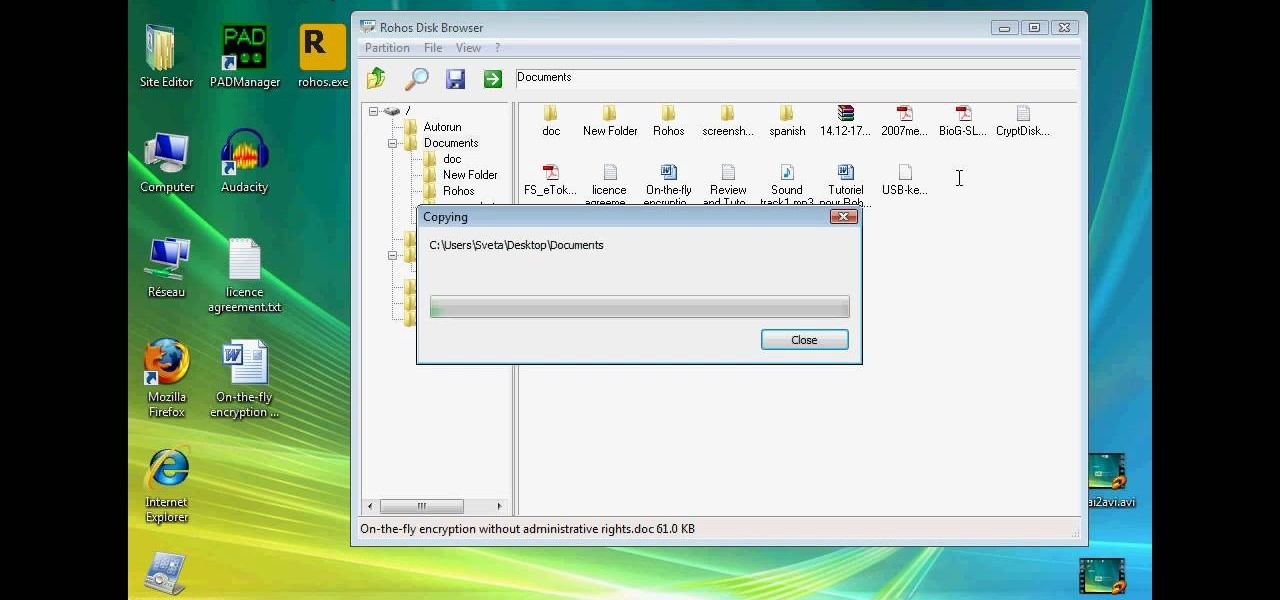
This technical video will show you all about the Rohos Mini Drive. See how you may work with an encrypted partition on a PC without admin rights using this free portable encryption solution. It securely protects your portable data on any USB device. Portable utility Rohos Disk Browser gives you opportunity to work with your sensitive data on a USB drive in the usual way on any PC (even at an internet cafe, where you don’t have admin rights).

A series of videos that help show just how tough it can be to install a remote car starter. Unless your an electrician or a technician, this complex job can result in a variety of electronic failures in your car including prevention of actually getting into your car as well as prevent you from driving home.

Professional truck driver, Yesterday Irmani, teaches us how to tie a time honored, weight sustaining knot, for transportation purposes.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to build a motorcycle camera mount for under five bucks.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to homebrew and hack the PSP.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to analyze packet captures and network taps.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to extract Windows executables from packet captures.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to hide secret data inside a photo.